Active Directory Lab
Sections:
- Deploying a Windows File Server
- Joining a Windows Domain
- Active Directory Lab Topology
- (Plain-Text) Active Directory for Sophos Authentication
- (SSL/TLS) Active Directory for Sophos Authentication
- Importing Active Directory Groups
- Set Primary Authentication Method for Sophos Services
Resources:
- Sophos Firewall
- Windows Server VM
- Active Directory
- Network Shares
Overview:
- In this lab demonstration, I will be defining an external Windows server with Active Directory at the Corporate site Sophos Firewall to be used for user authentication for various firewall services
- In the next few sections, I will demonstrate configuring a Windows server virtual machine using Oracle VirtualBox from the ground up and setup services such as Active Directory and Windows file services for network shares across the domain (Corporate and Branch LANs)
Deploying a Windows Server Virtual Machine
Overview
- In this section, I will demonstrate deploying a Windows server virtual machine using the Oracle VirtualBox type-2 hypervisor
- A type-2 hypervisor, also known as a hosted hypervisor, is a type of virtualization software that runs on top of an existing operating system (OS)
- It operates as an application within the host OS and uses the resources of the host machine to create and manage virtual machines (VMs)
- Type-2 hypervisors are great for labs (such as testing, development, or educational environments) because they offer several benefits that make them ideal for non-production or experimental setups
- Other Notable Type-2 Hypervisors
- VMware Workstation (Windows & Linux)
- Parallels Desktop (macOS)
- VMware Fusion (macOS)
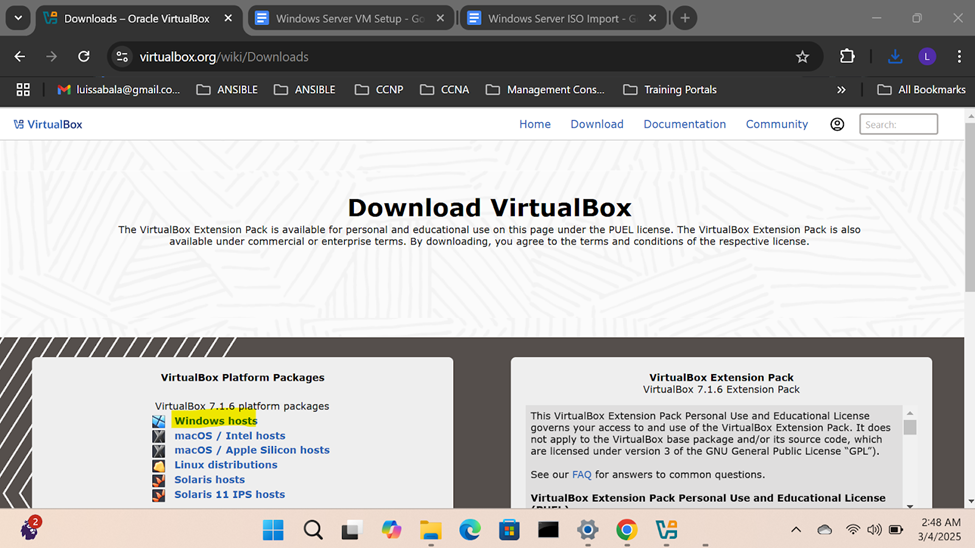
Downloading VirtualBox
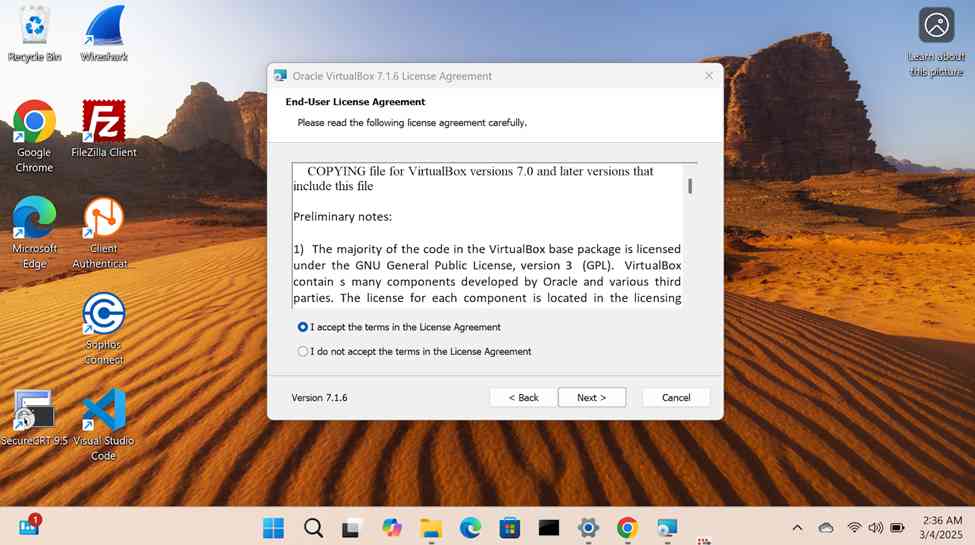
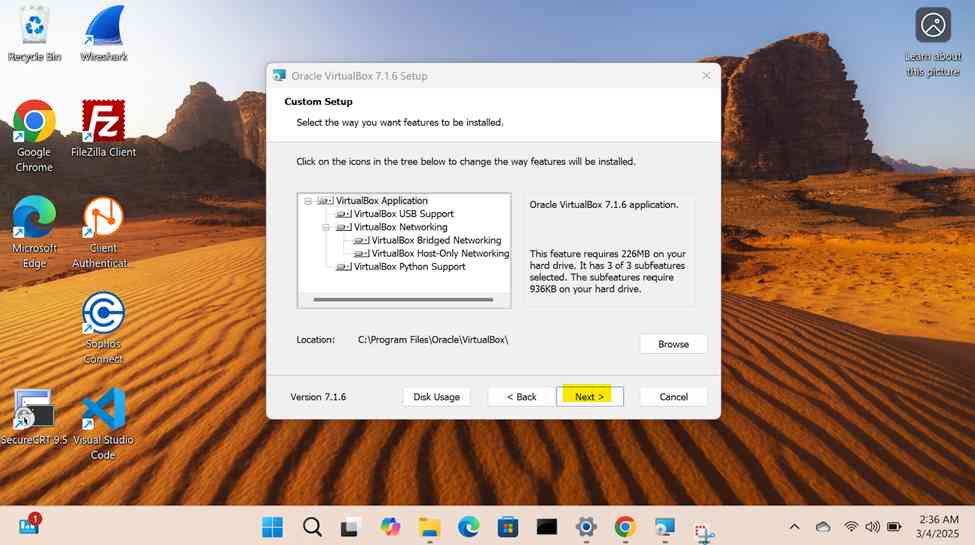
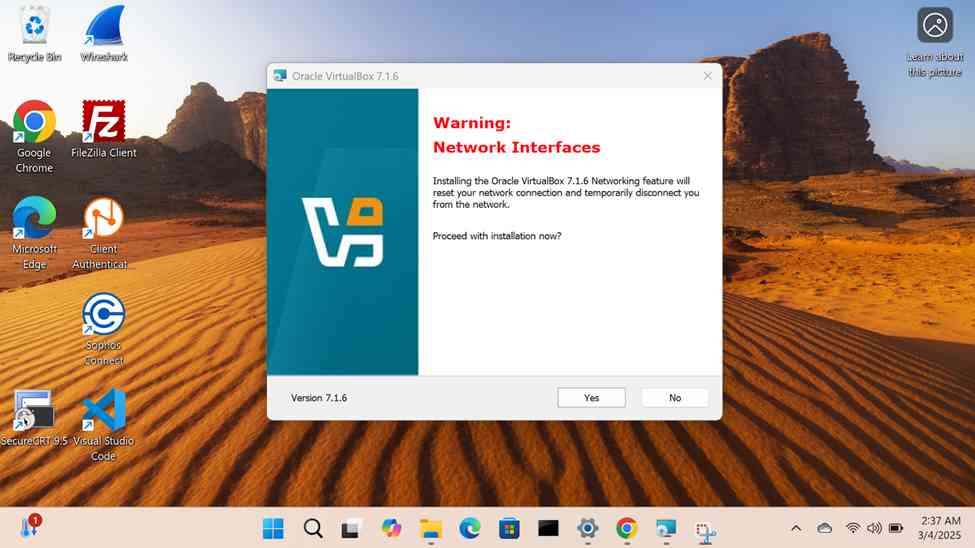
- In this demonstration, I will walk-through installing the Oracle VM VirtualBox hypervisor software on a Windows machine that will be used to run the Windows server virtual machine
- Resource: VirtualBox Download


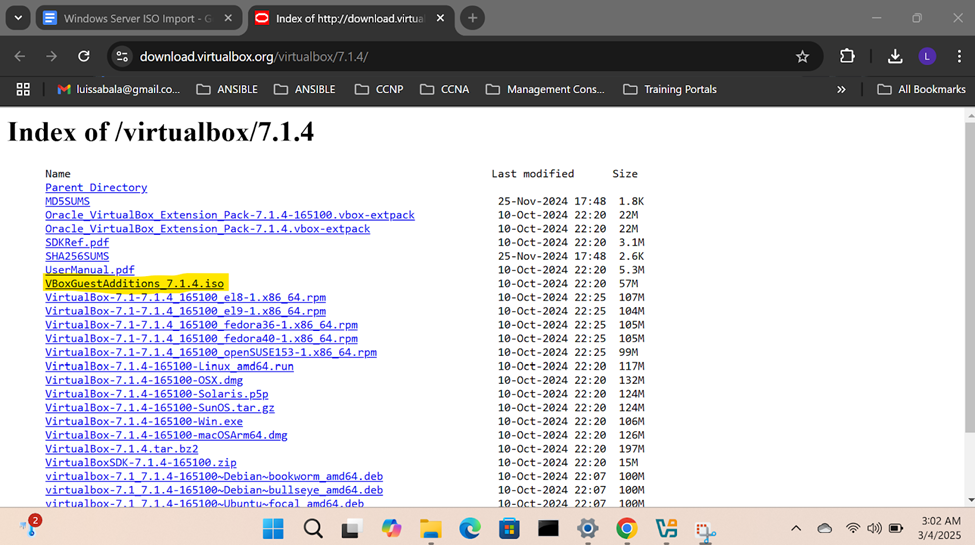
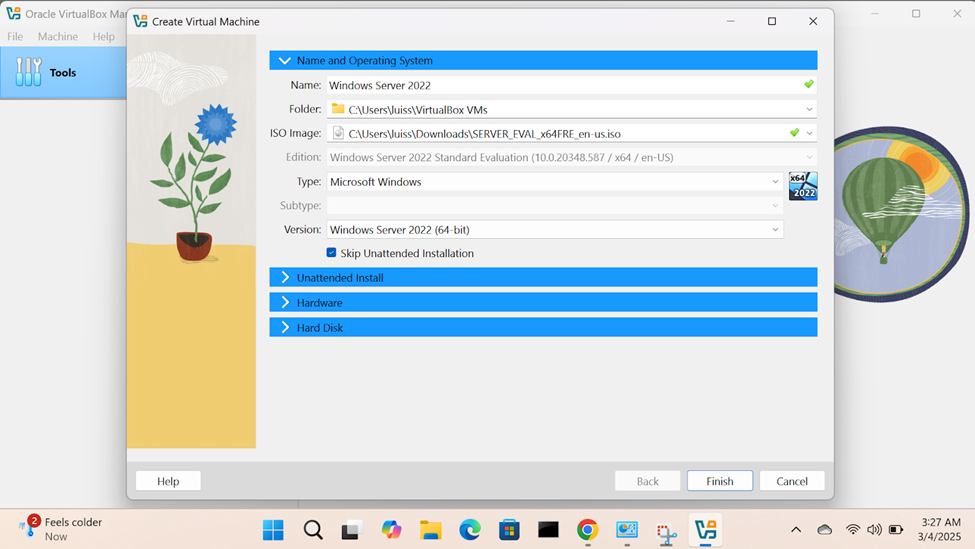
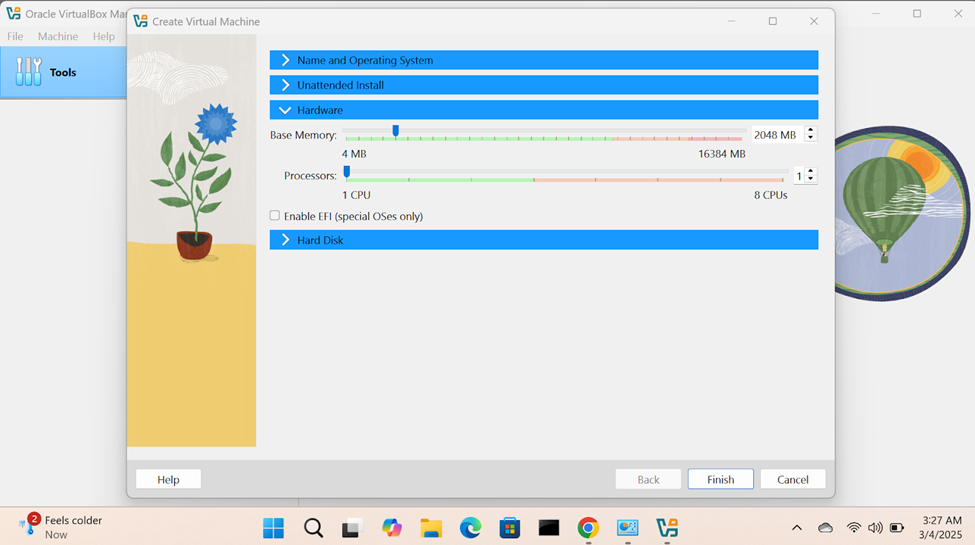
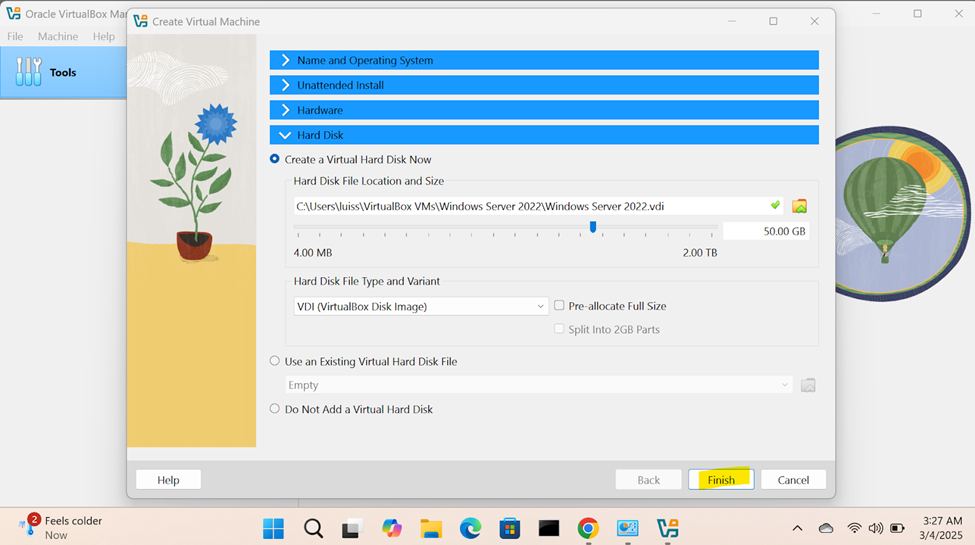
Downloading & Importing Windows Server Image
- In this demonstration, I will walk-through downloading the Windows server trial '.iso' image and the Oracle VirtualBox Guest Additions and then importing those files into the VirtualBox hypervisor
- For virtual machines, ISO files are often used to install operating systems. Instead of using physical disks, the ISO file is 'mounted' virtually within the virtual machine (VM). This allows the virtual machine to boot from the ISO as if it were a real CD/DVD, enabling the installation or loading of software
- Oracle VirtualBox Guest Additions is a set of drivers and utilities that improve the performance and integration of a virtual machine running on VirtualBox, making it more seamless to use
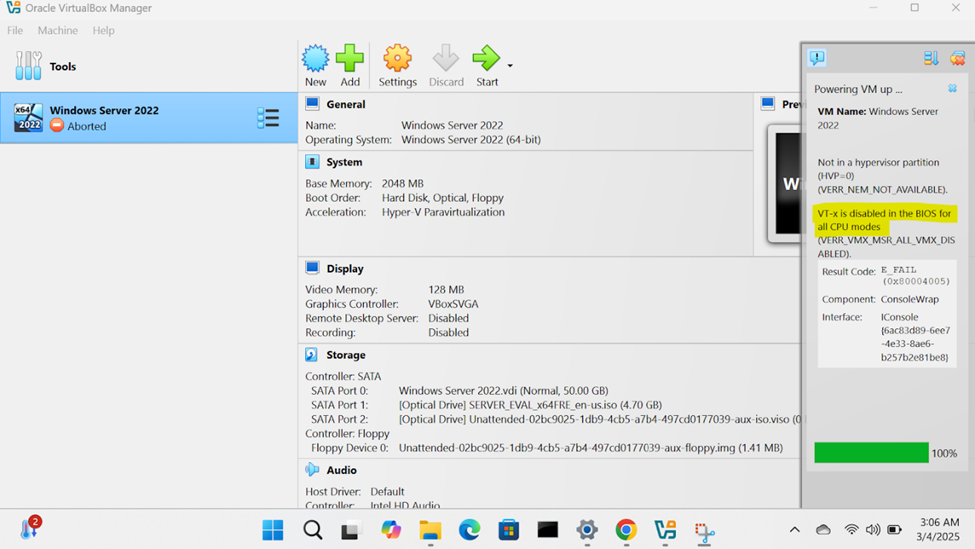
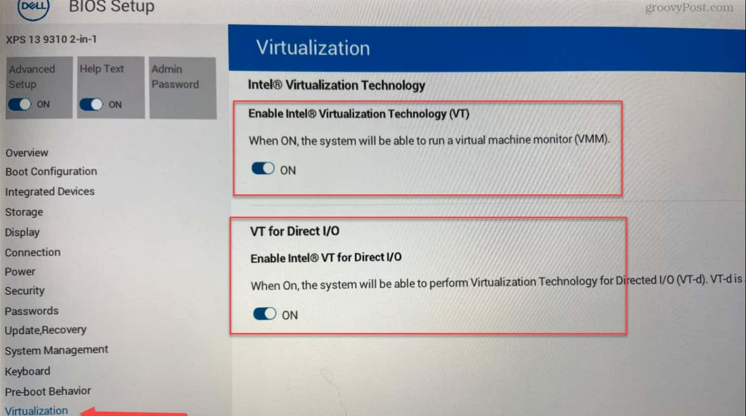
- In order to run virtual machines with optimal performance in VirtualBox, you need to have VT-x (or AMD-V on AMD processors) enabled in your BIOS settings. Different computer vendors often have different BIOS setups and is recommended to do google search for your specific computer type
- Resources

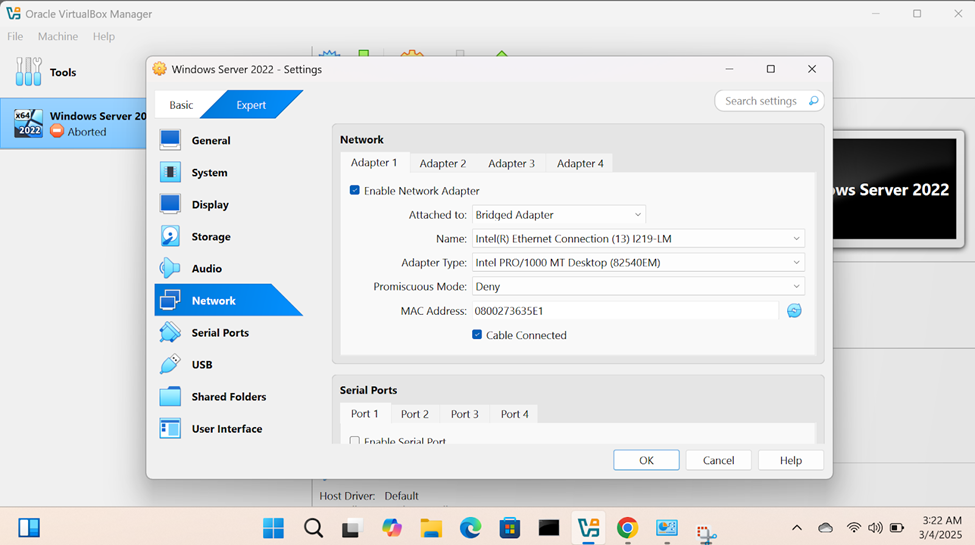
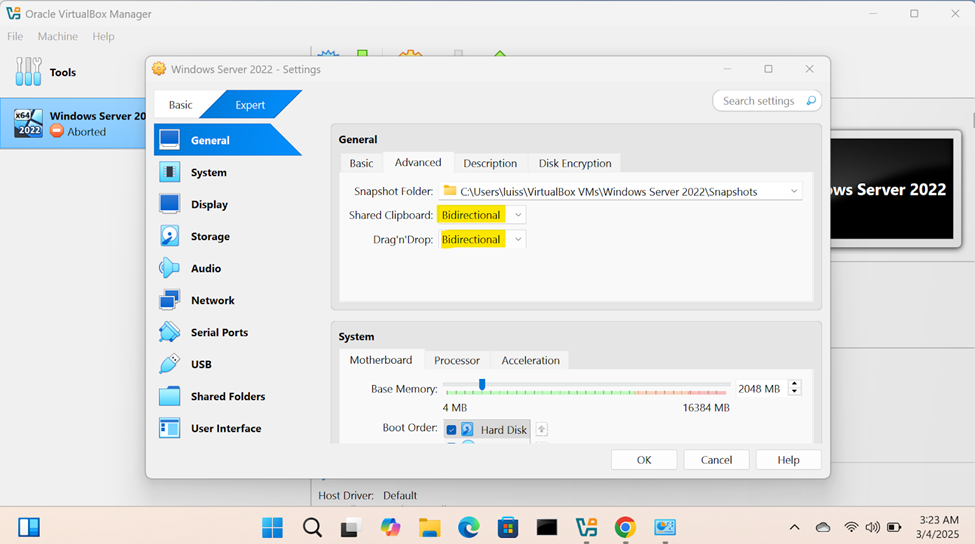
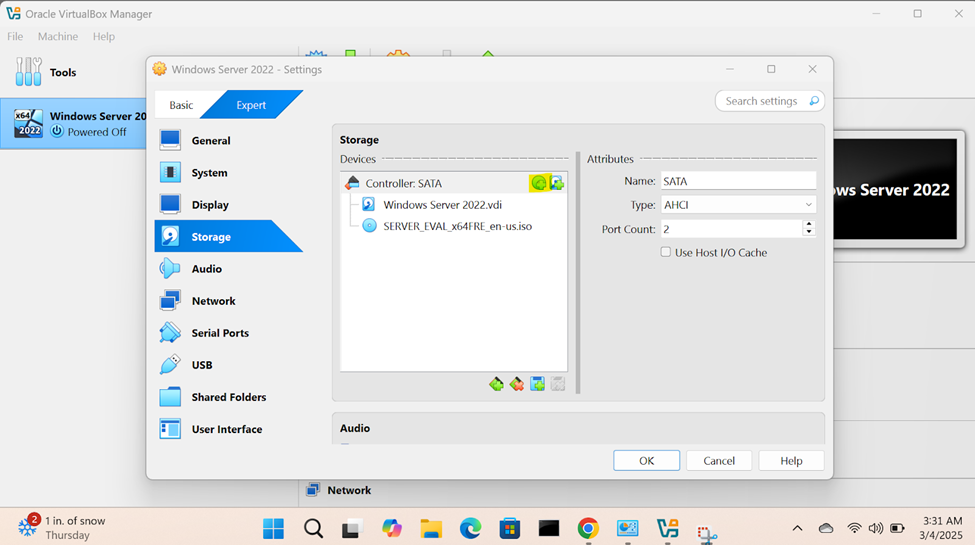
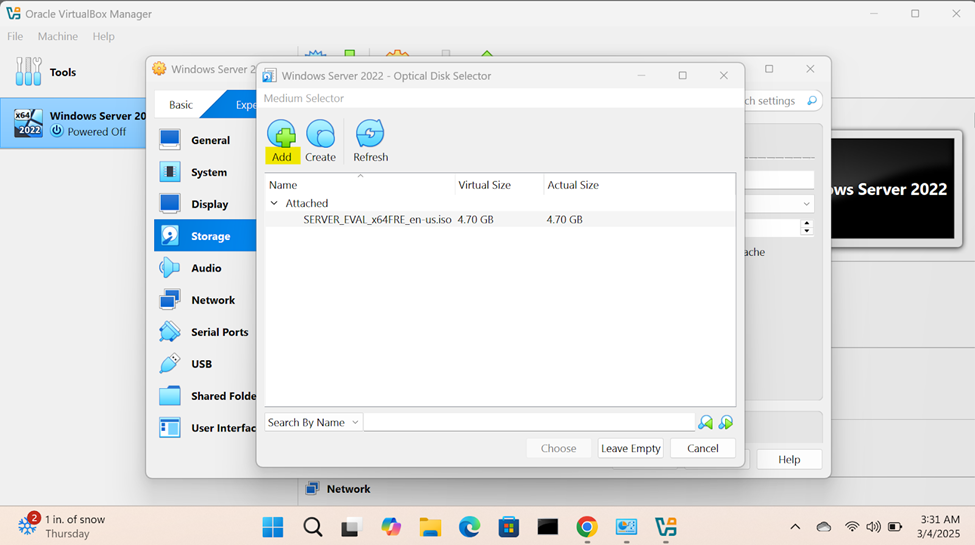
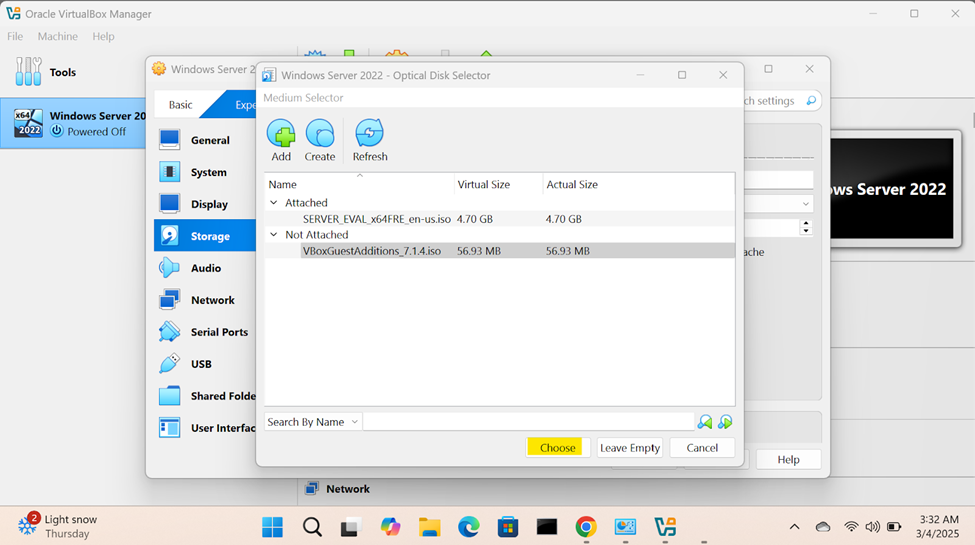
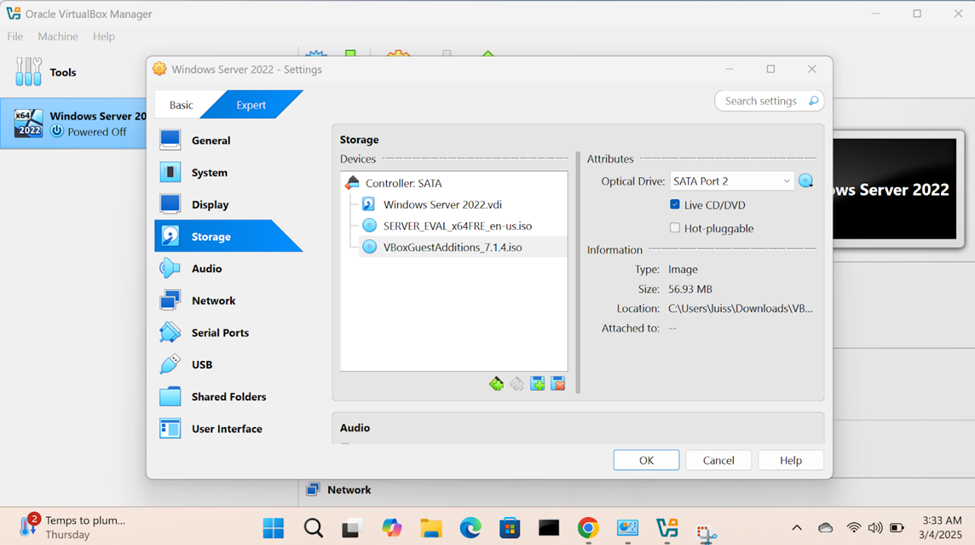
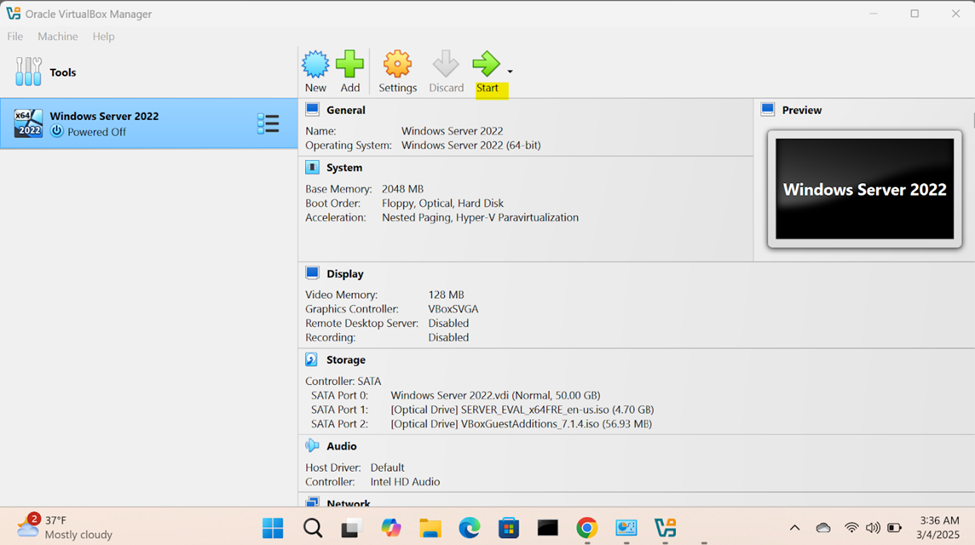
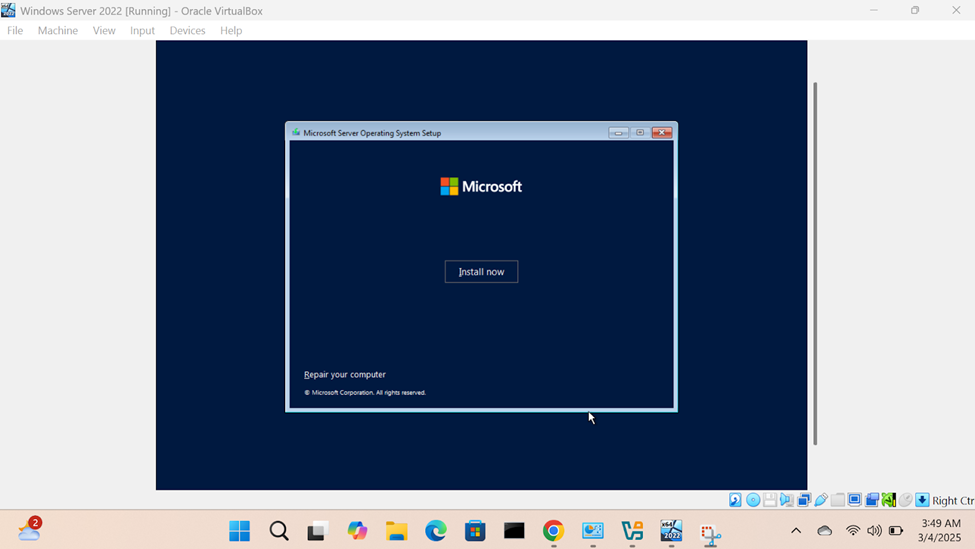
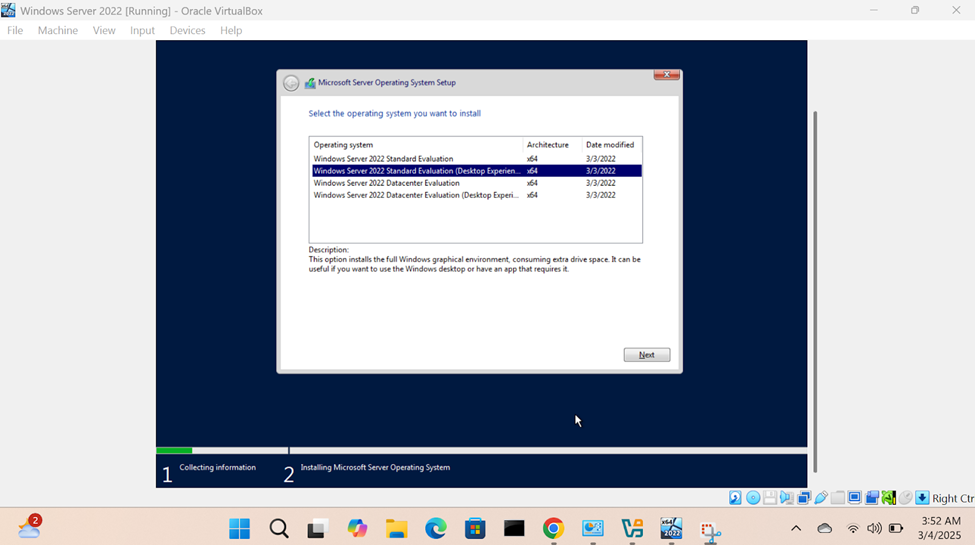
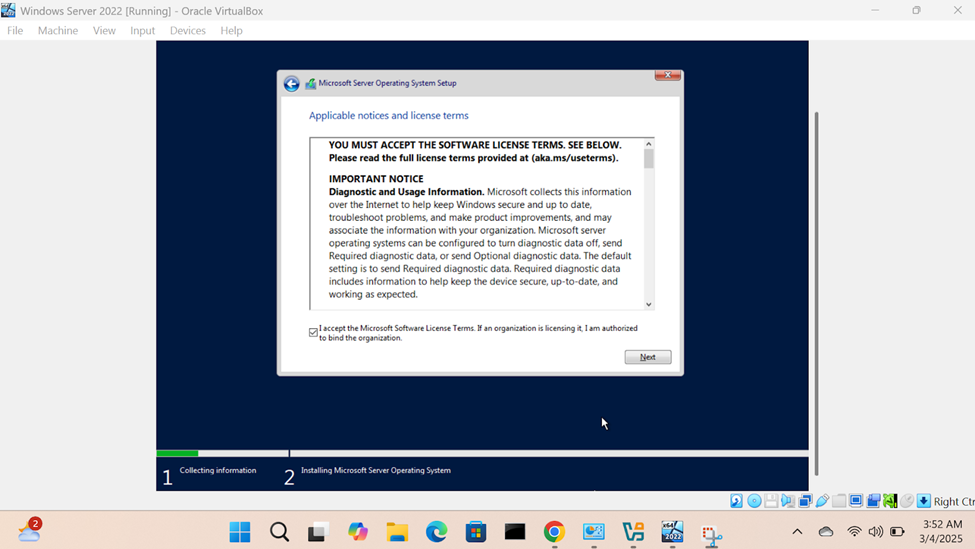
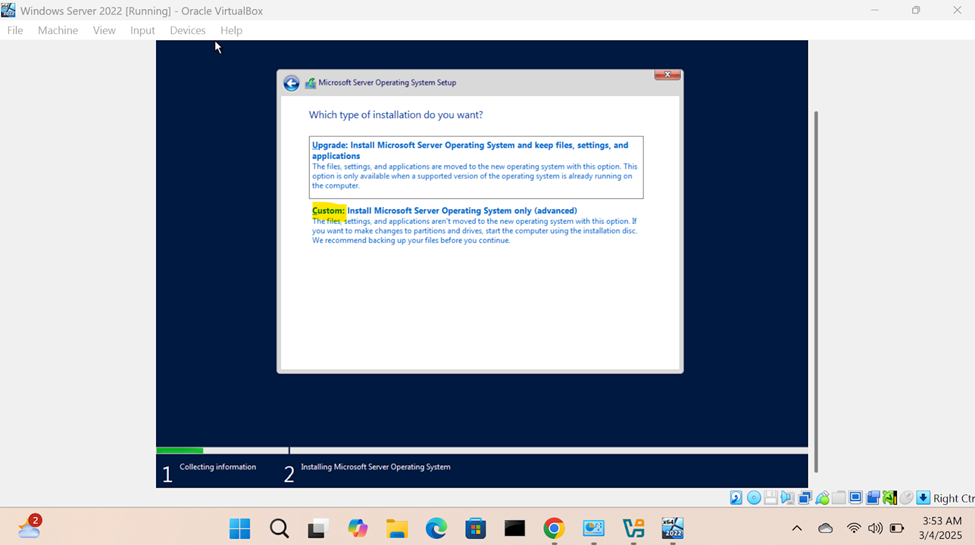
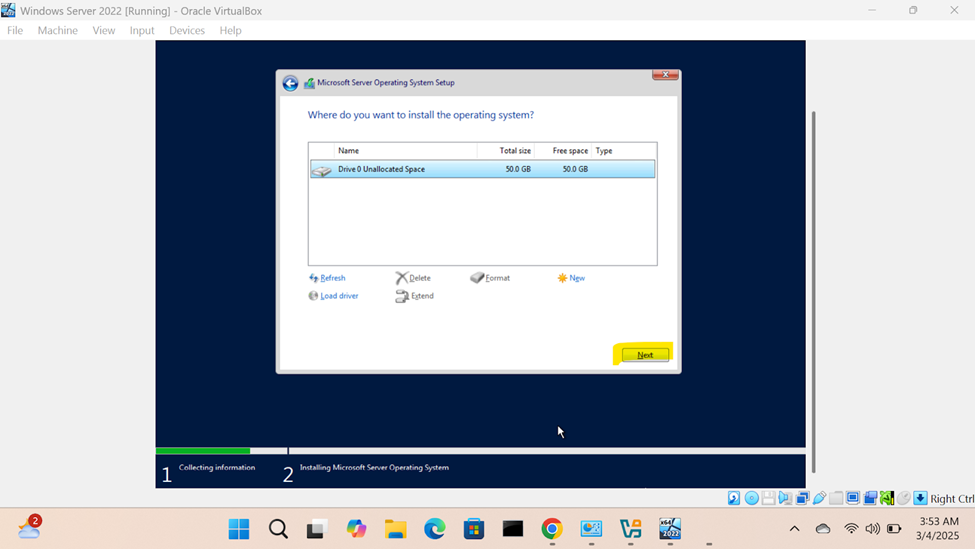
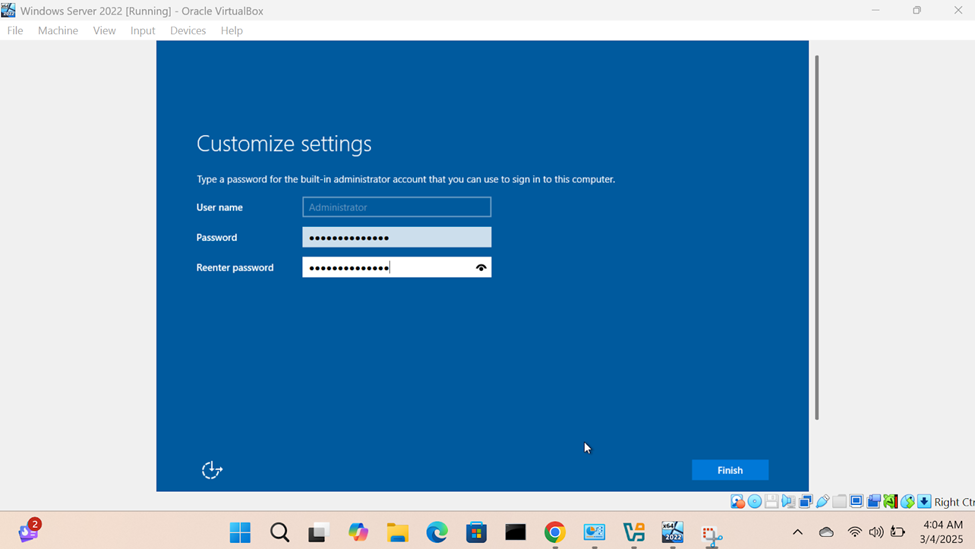
Windows Server Operating System Setup
- In this demonstration, I will walk-through configuring and setting up the Windows server operating system
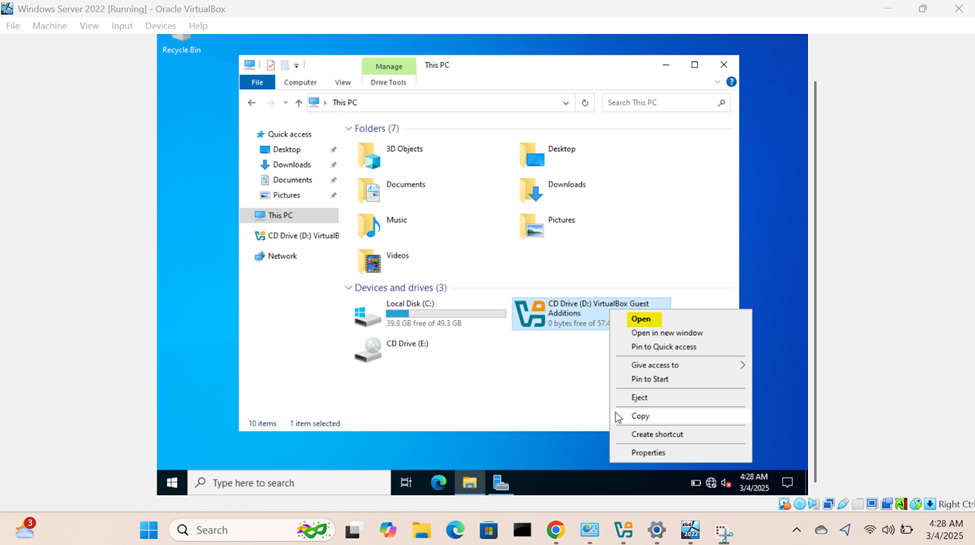
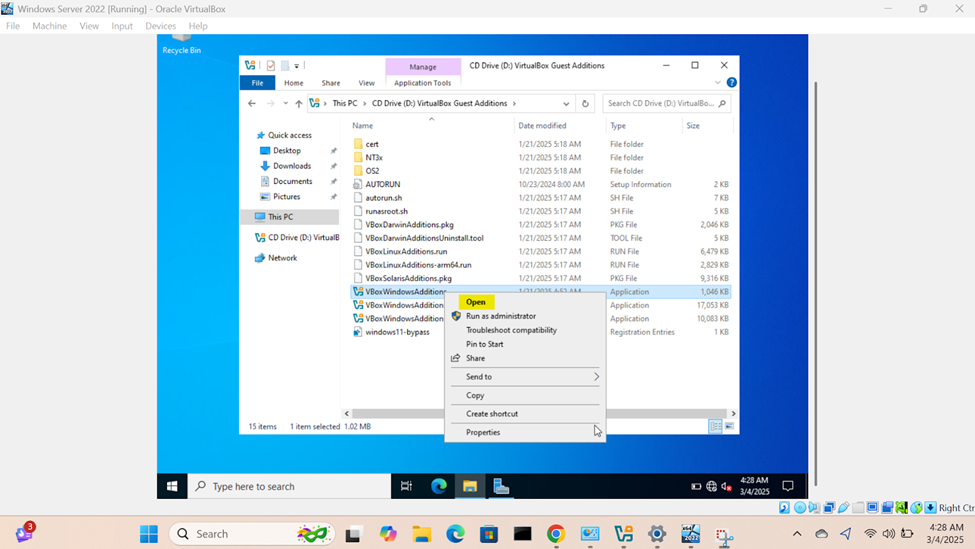
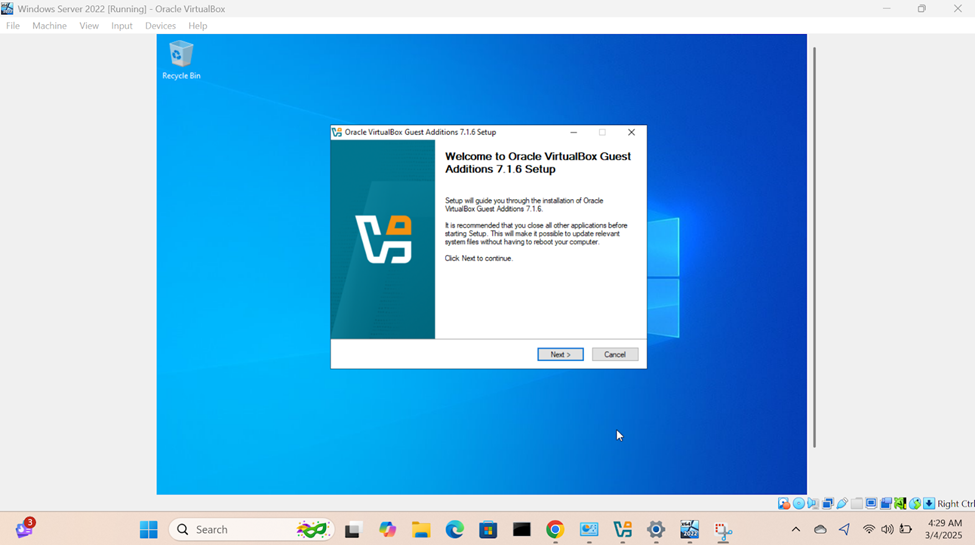
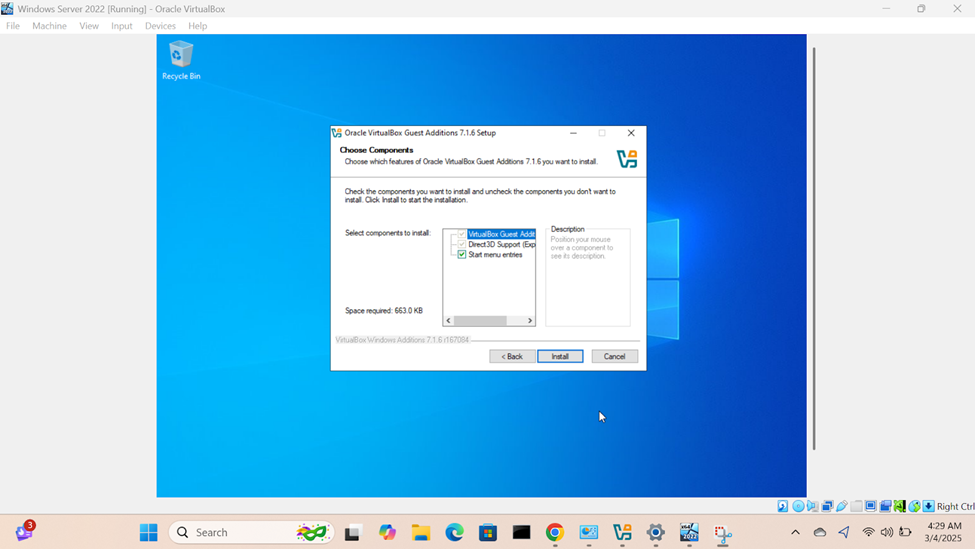
- Upon logging into the Windows server post setup, I will run the Oracle VirtualBox Guest Additions installer from the CD drive (ISO) that was imported when downloading and importing the Windows server ISO image
- When you install the VirtualBox Guest Additions on the VM, it provides several benefits, one of which is dynamically resizing of the VM's display. This feature allows the guest OS to automatically adjust the resolution of the VM's display as you resize the VirtualBox window making labs enjoyable
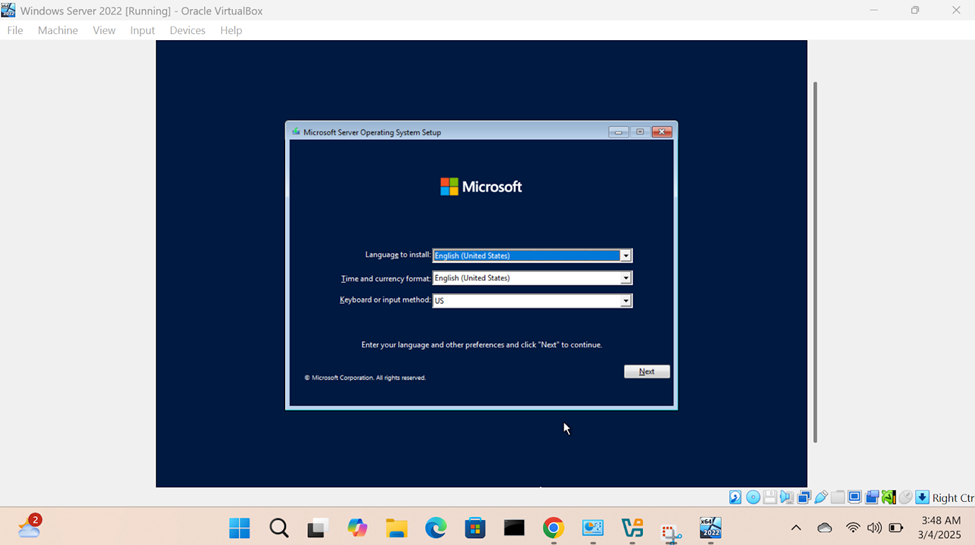
Connecting Windows Server to Lab Network
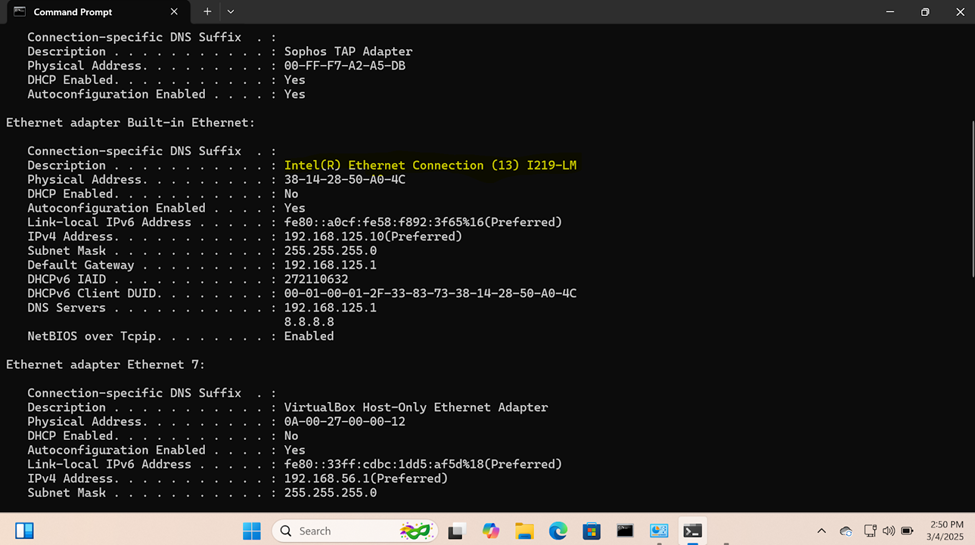
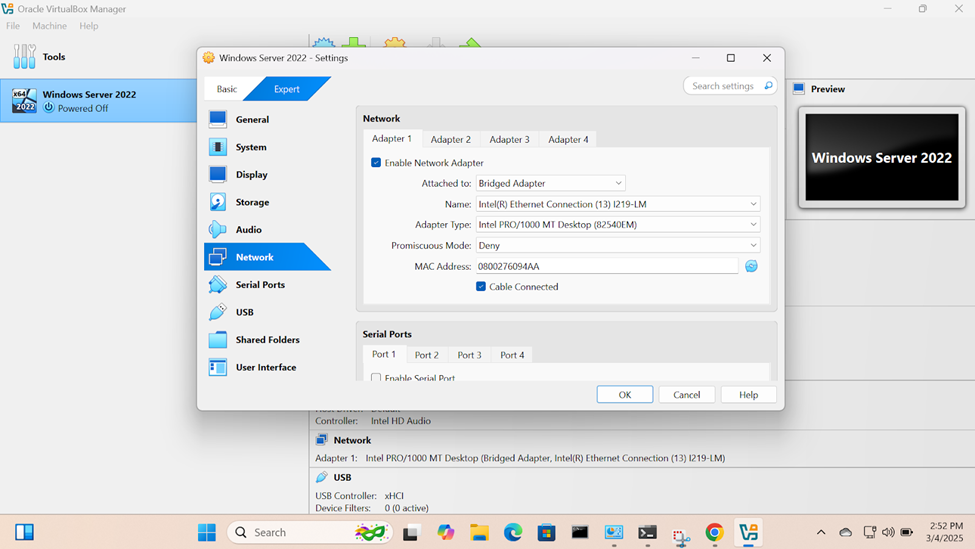
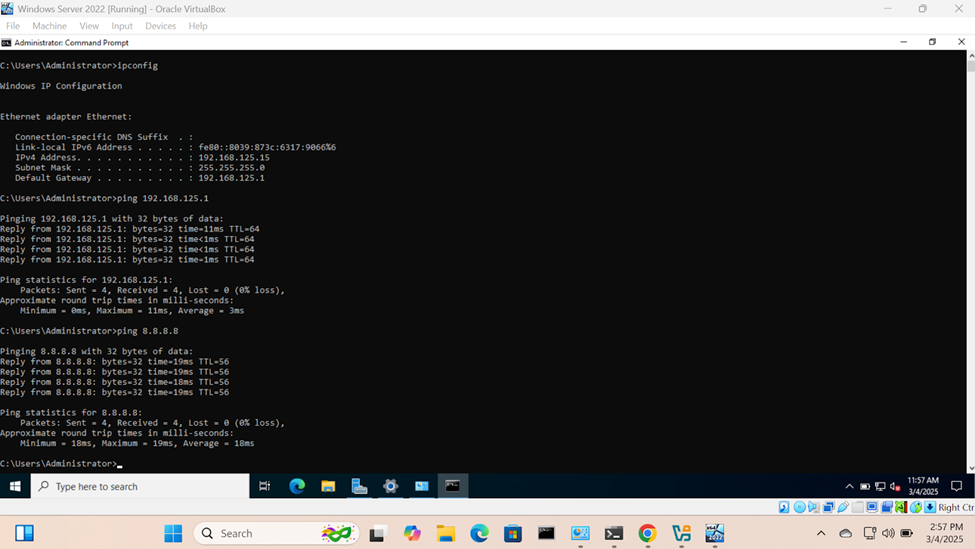
- In this demonstration, I will walk-through connecting the Windows server VM to my lab network
- Setting static IPs on servers is a key step to ensure the server always has the same IP address, making it accessible for various services like websites, databases, email servers, and remote management
- Key points to remember when setting static IPs
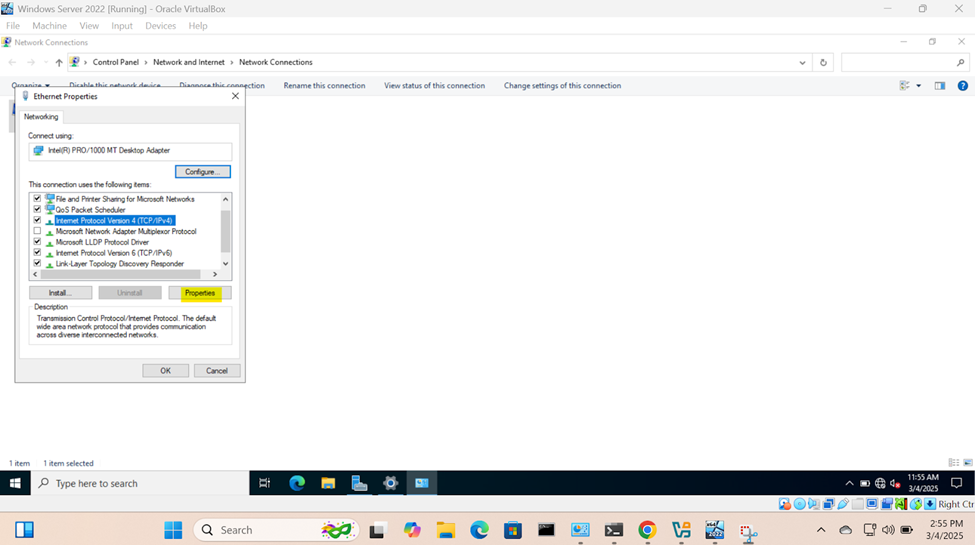
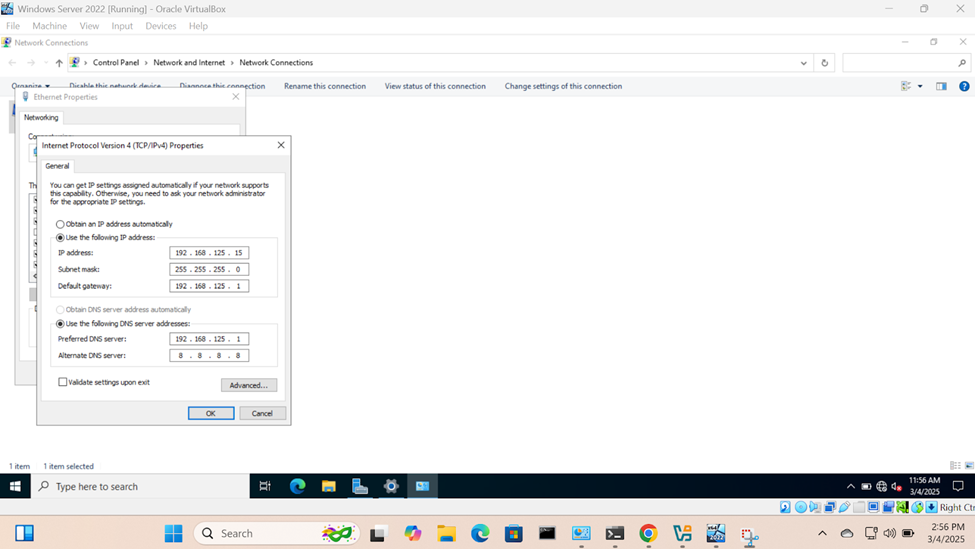
Creating an Active Directory Domain
- Resource: KB Article
- In this demonstration, I will walk-through integrating Active Directory on the Windows server VM post setup
- Below are the summary steps when deploying an Active Directory server
- Configuring a static IP address
- Naming the server (hostname)
- Installing the Active Directory Domain Services Role
- Configure Active Directory in Windows Server 2019/2022
Setting a Hostname for the Server
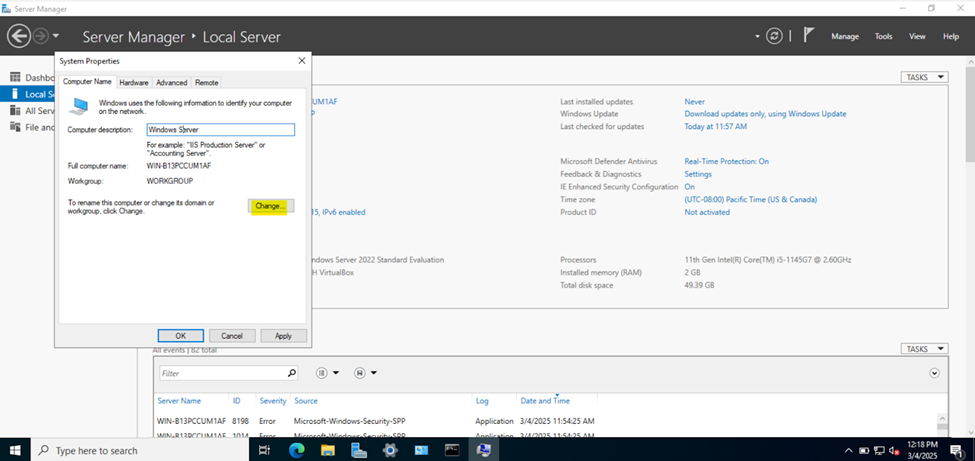
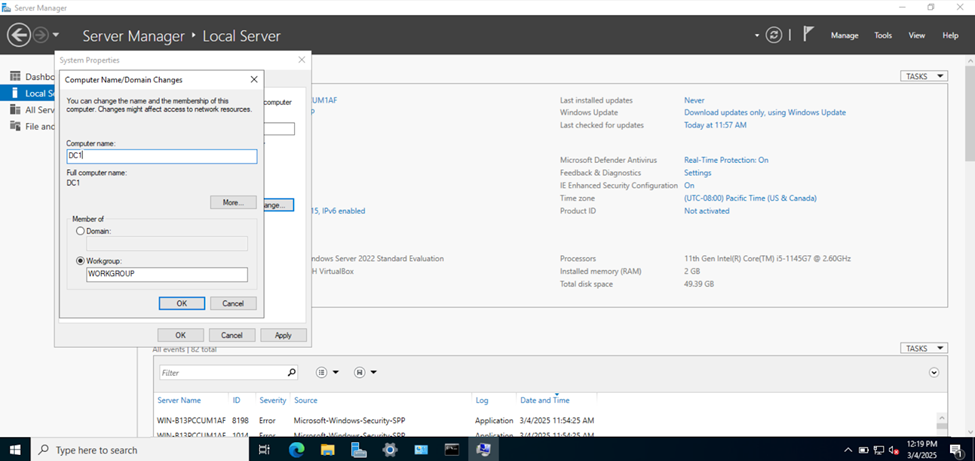
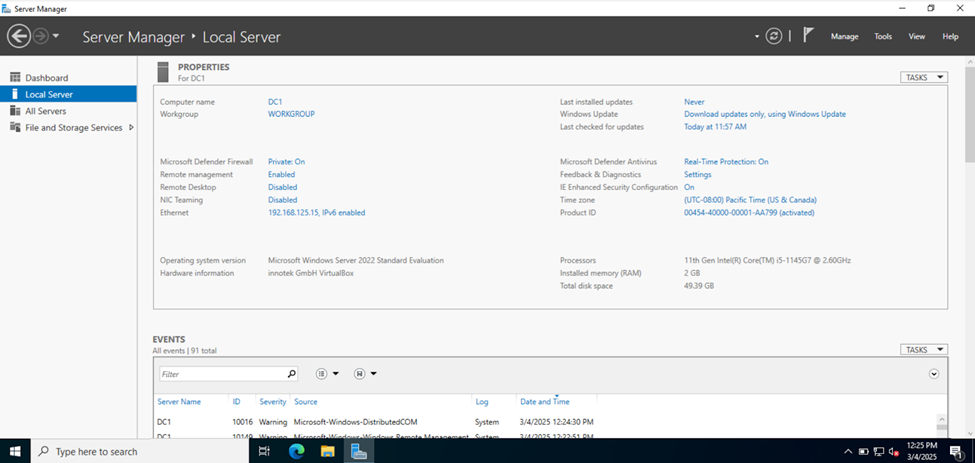
Installing the Active Directory Domain Services Role
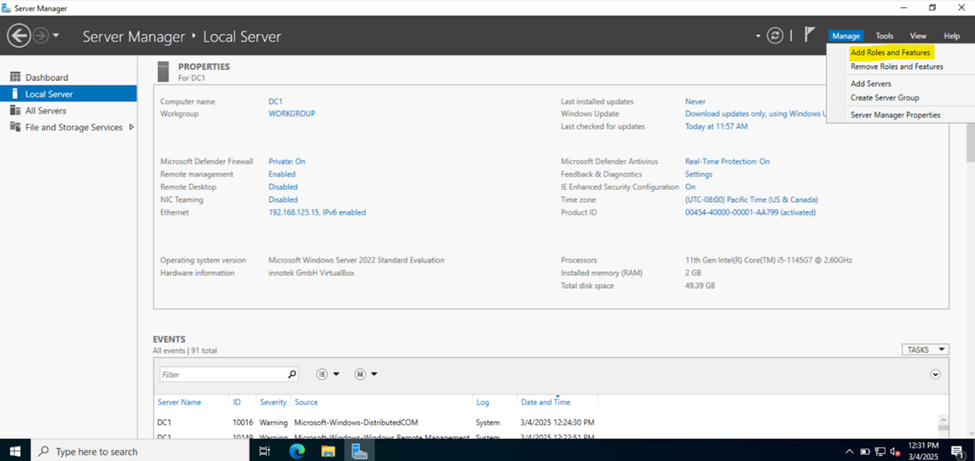
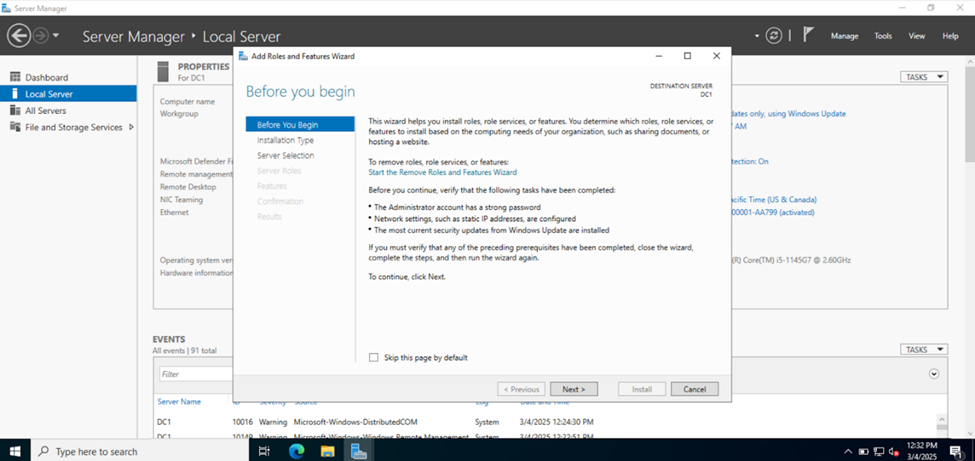
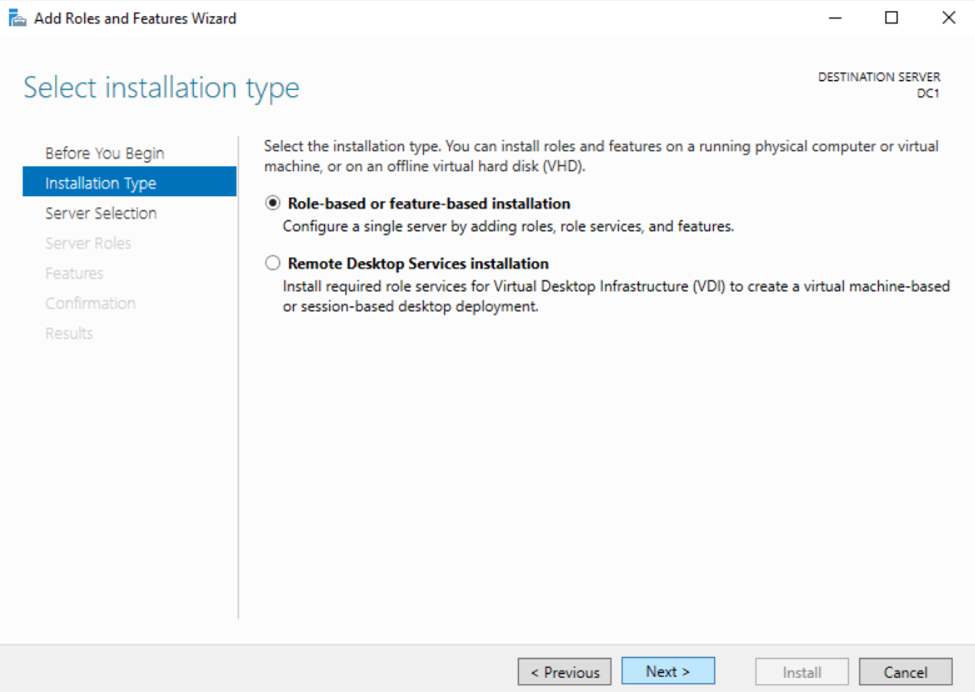
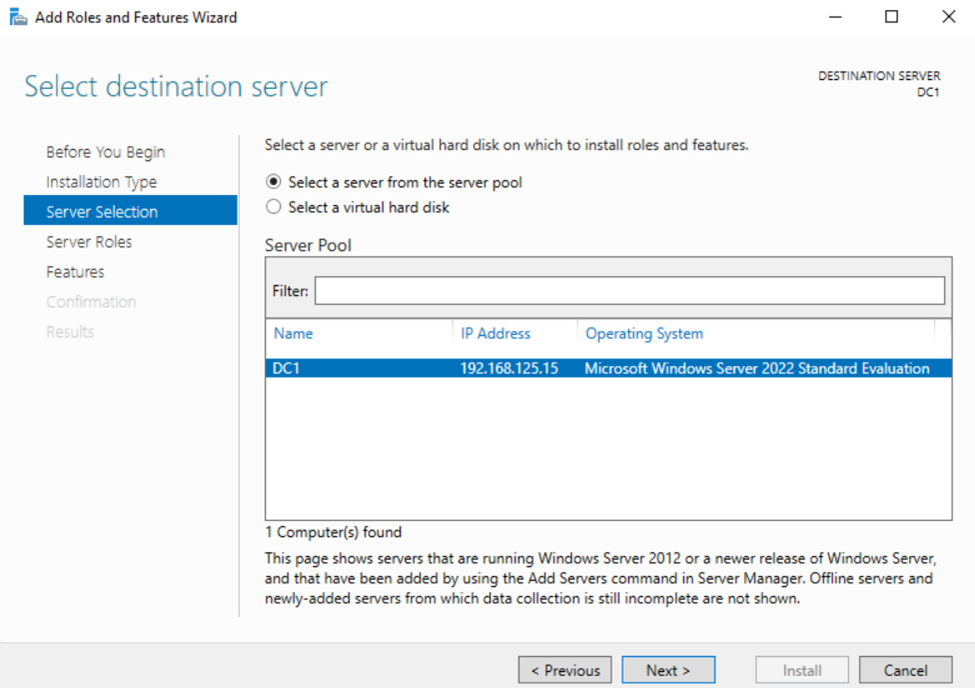
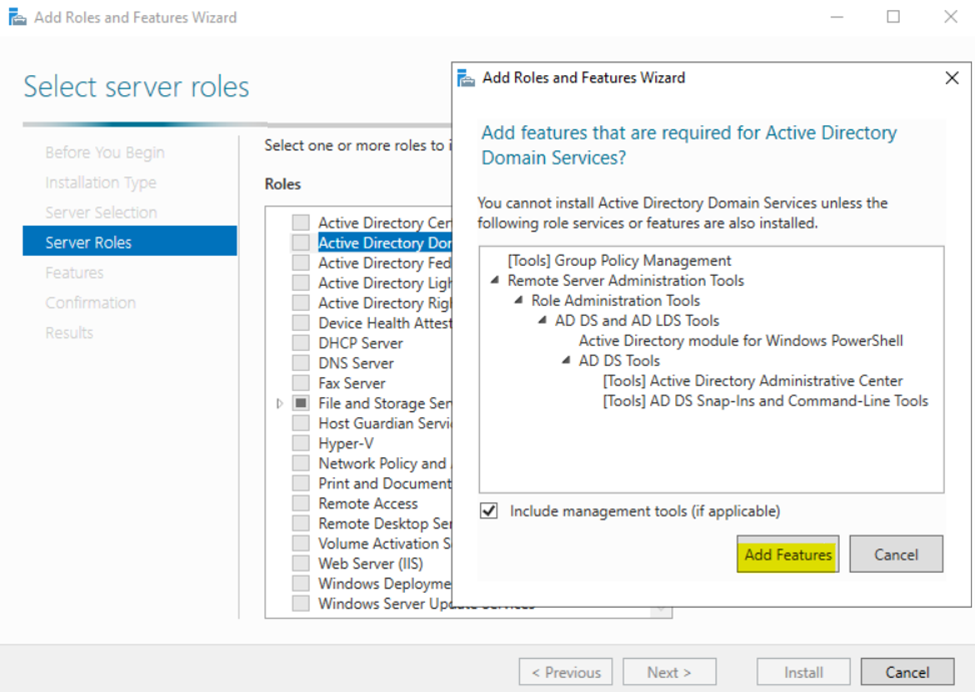
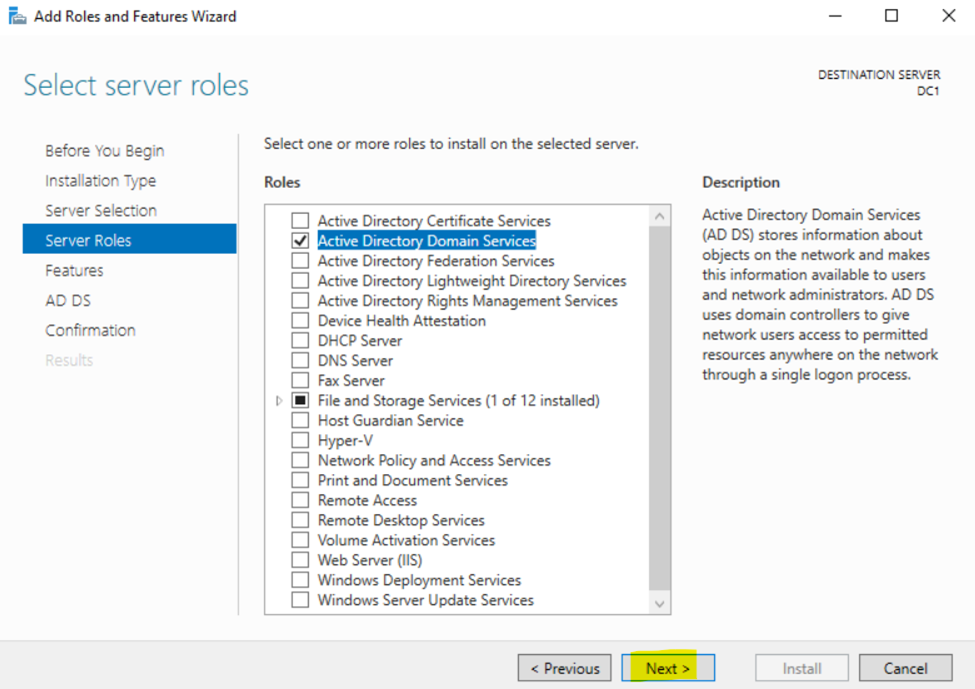
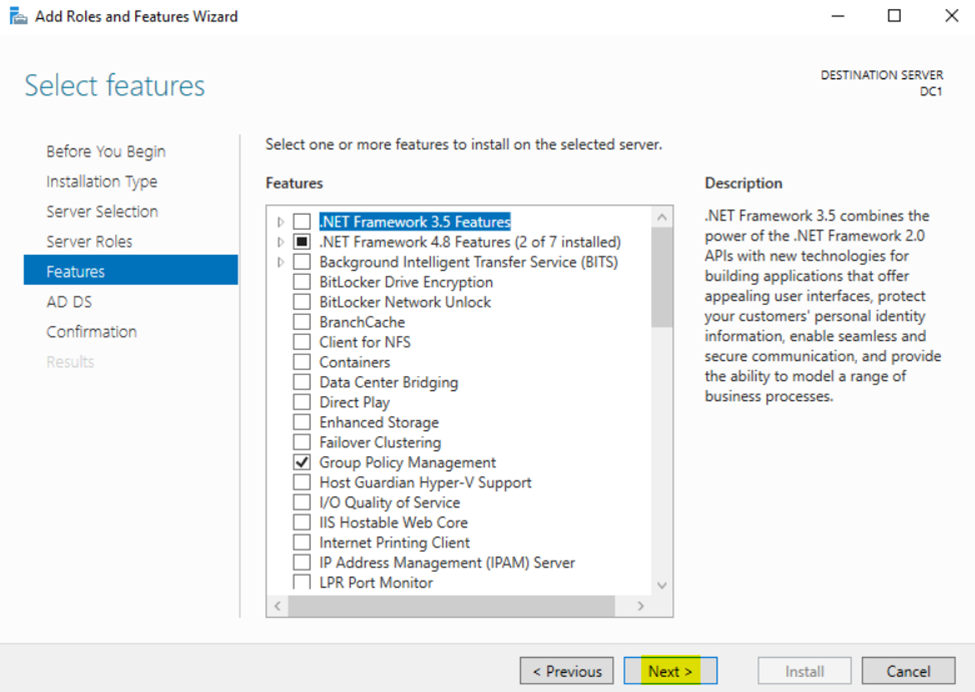
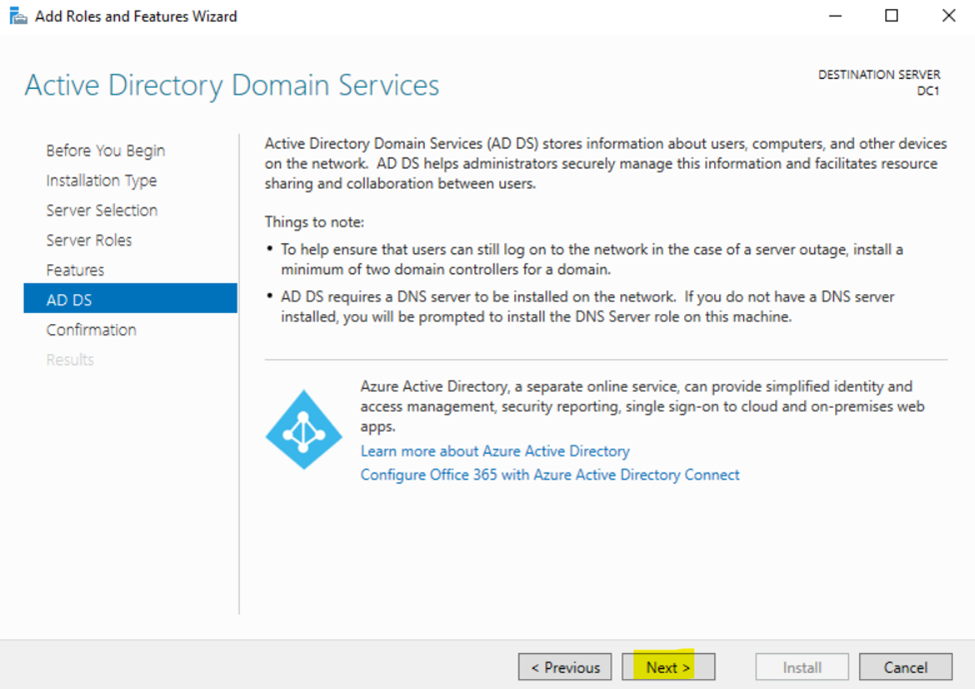
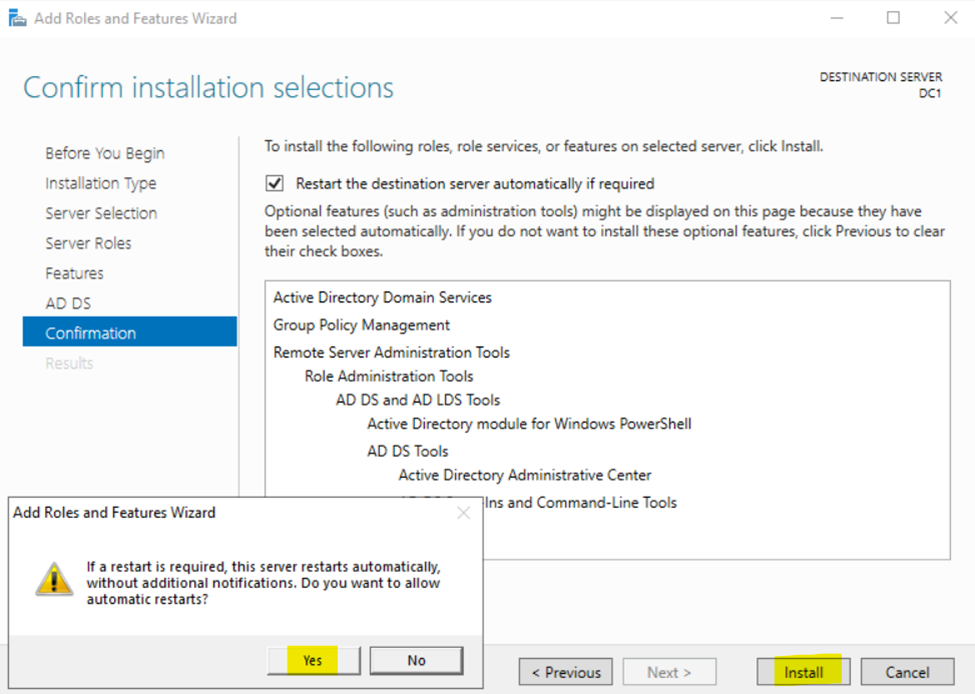
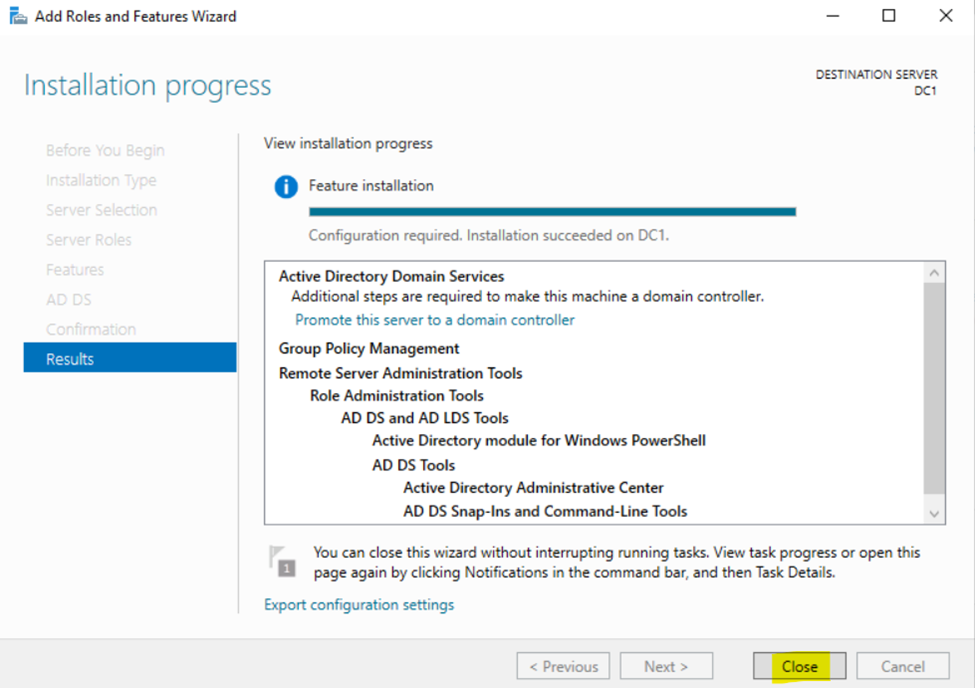
Configuring Active Directory in Windows Server 2022
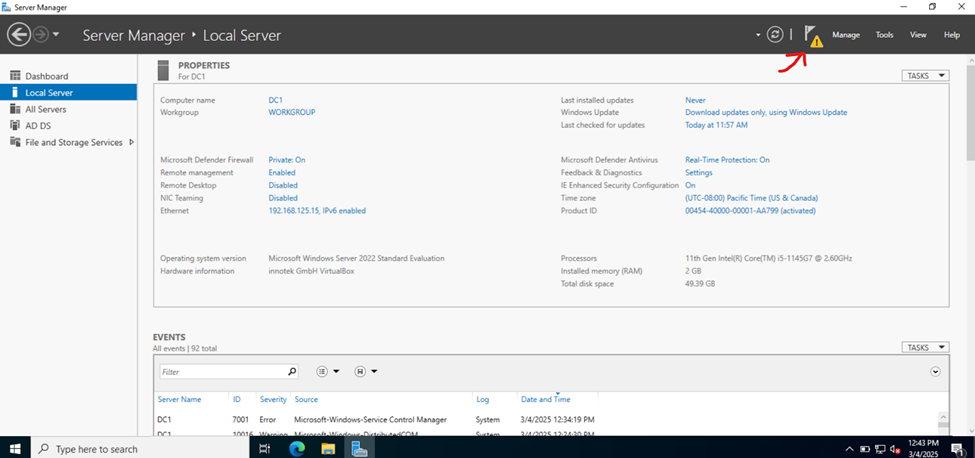
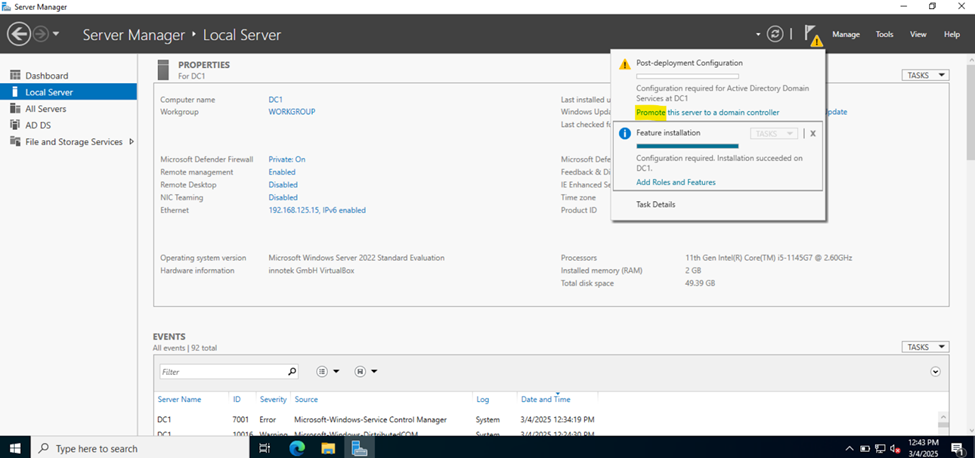
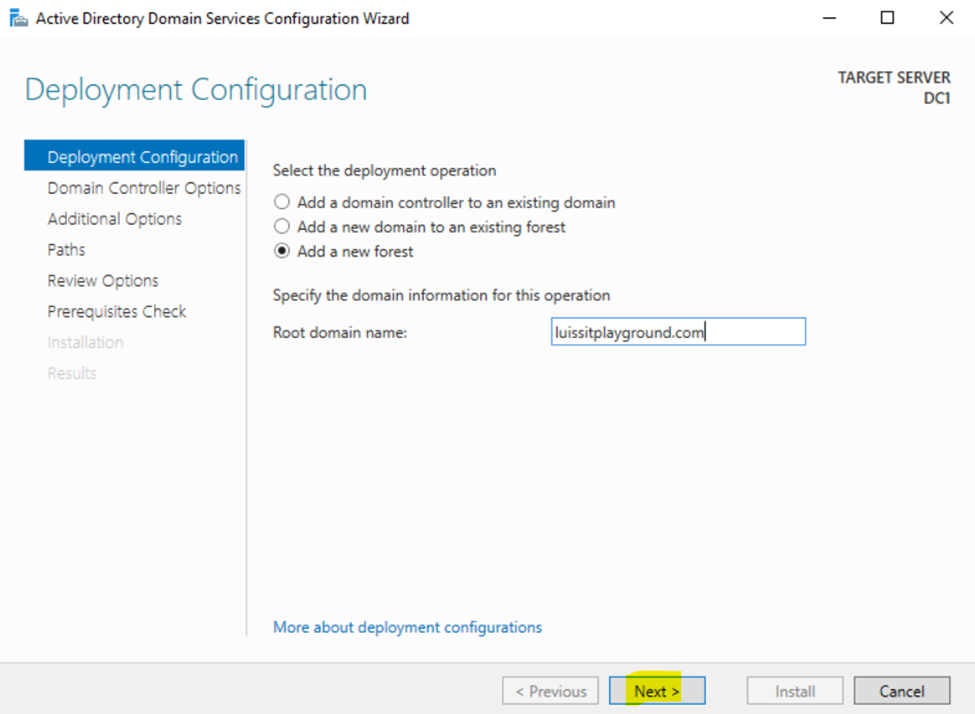
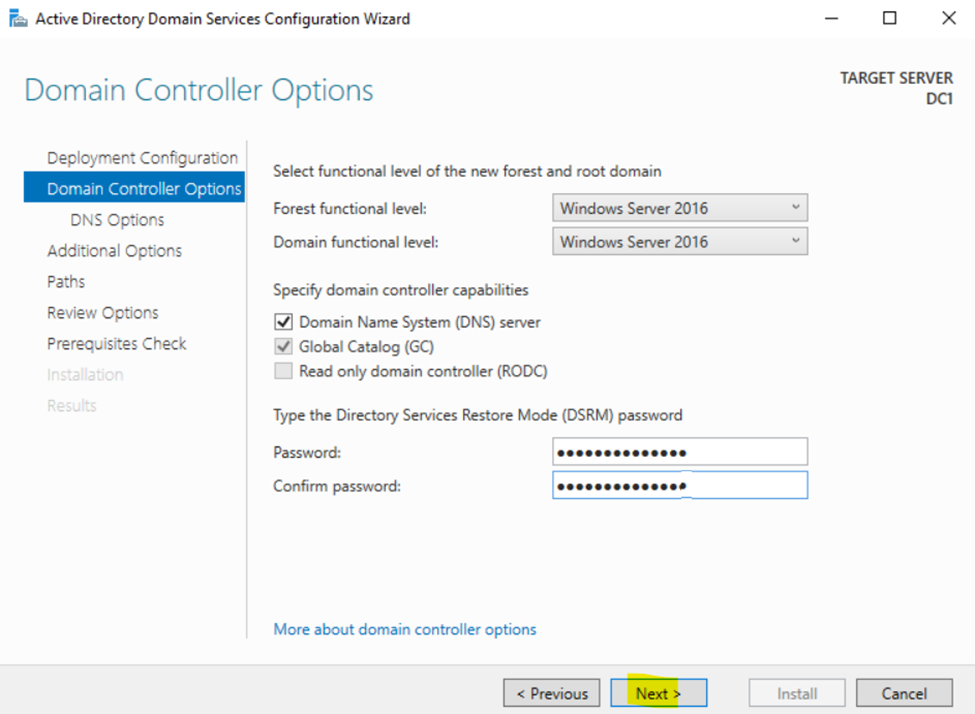
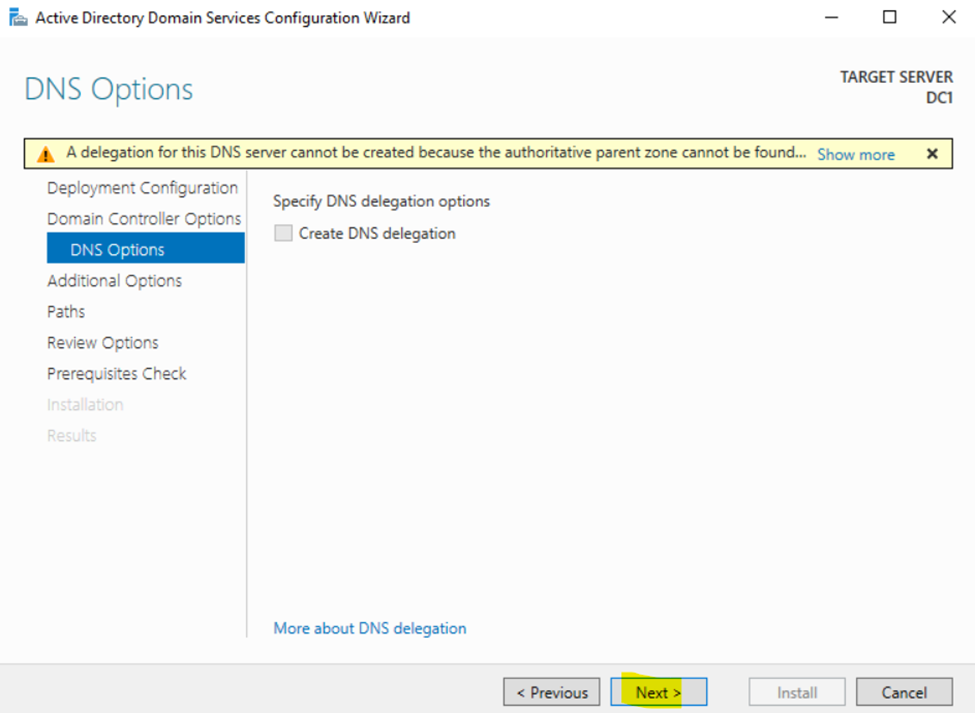
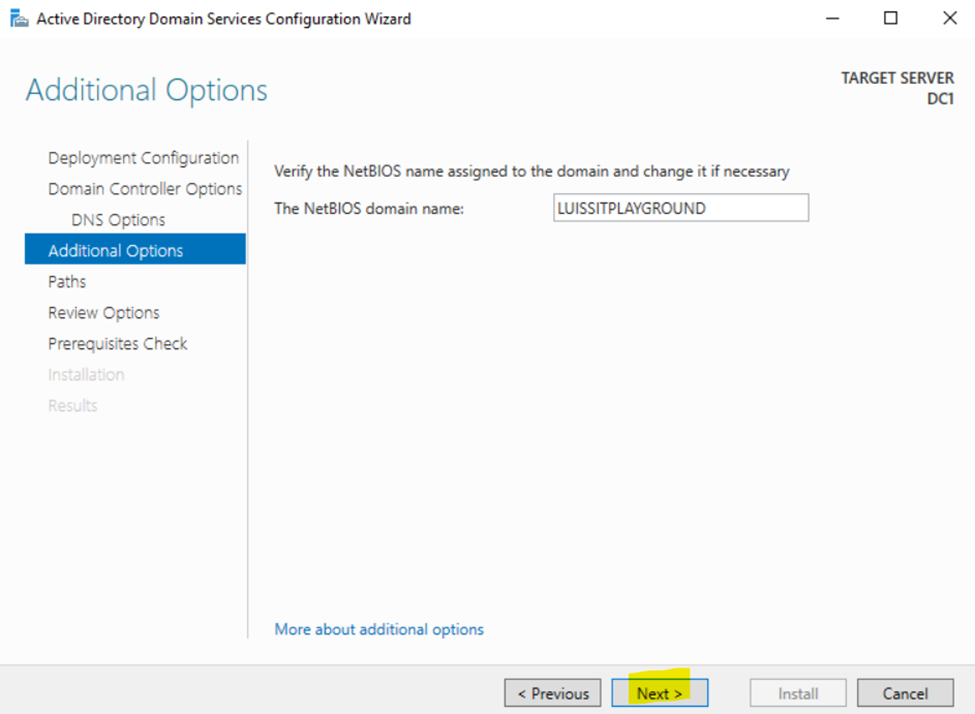
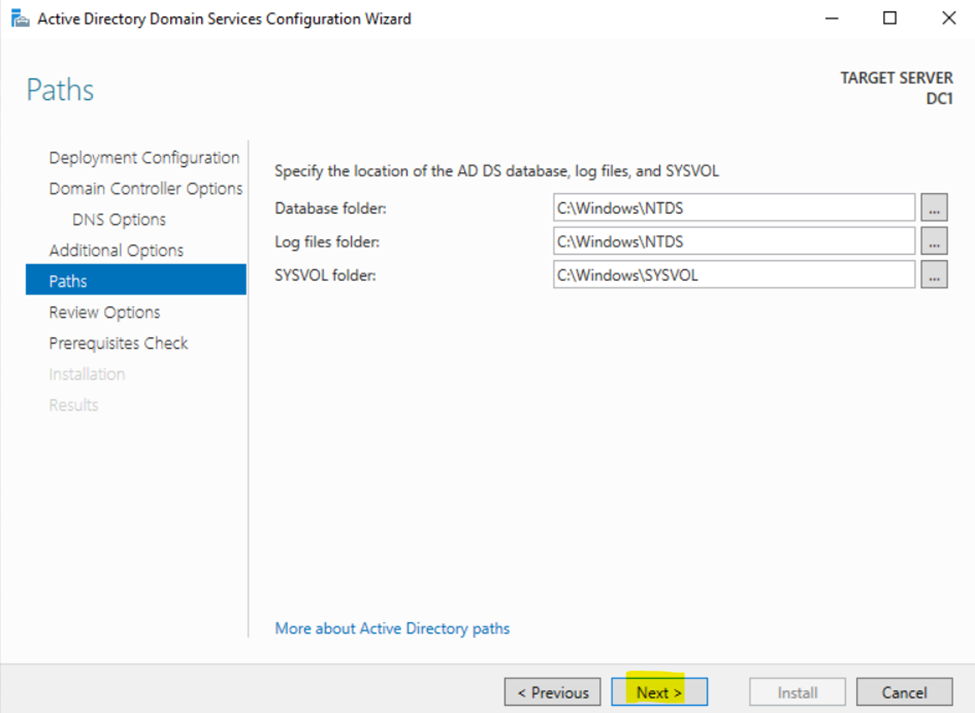
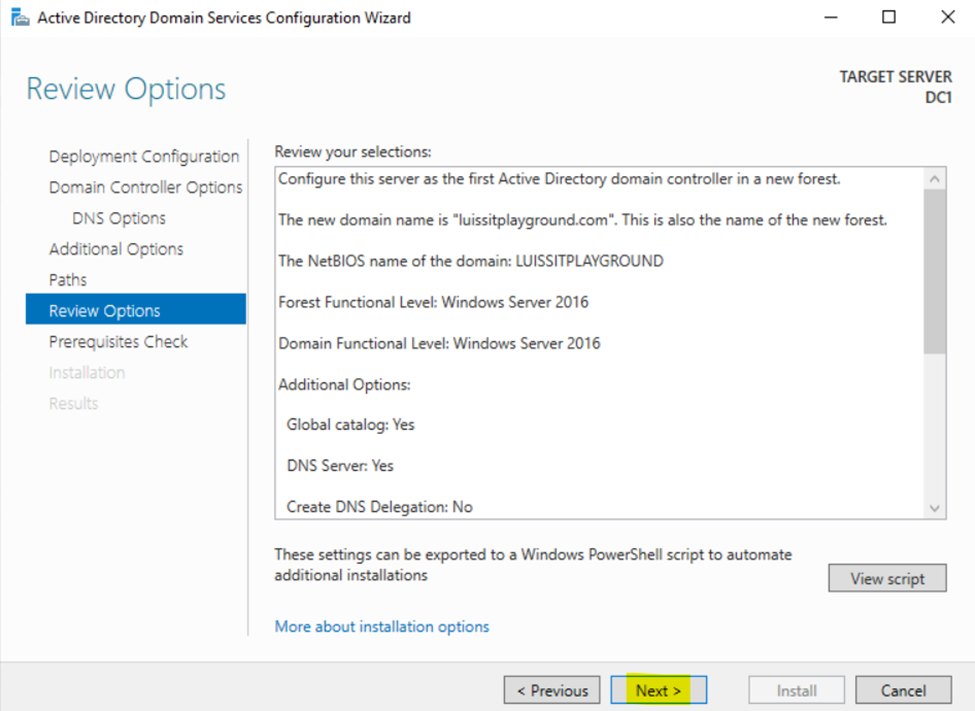
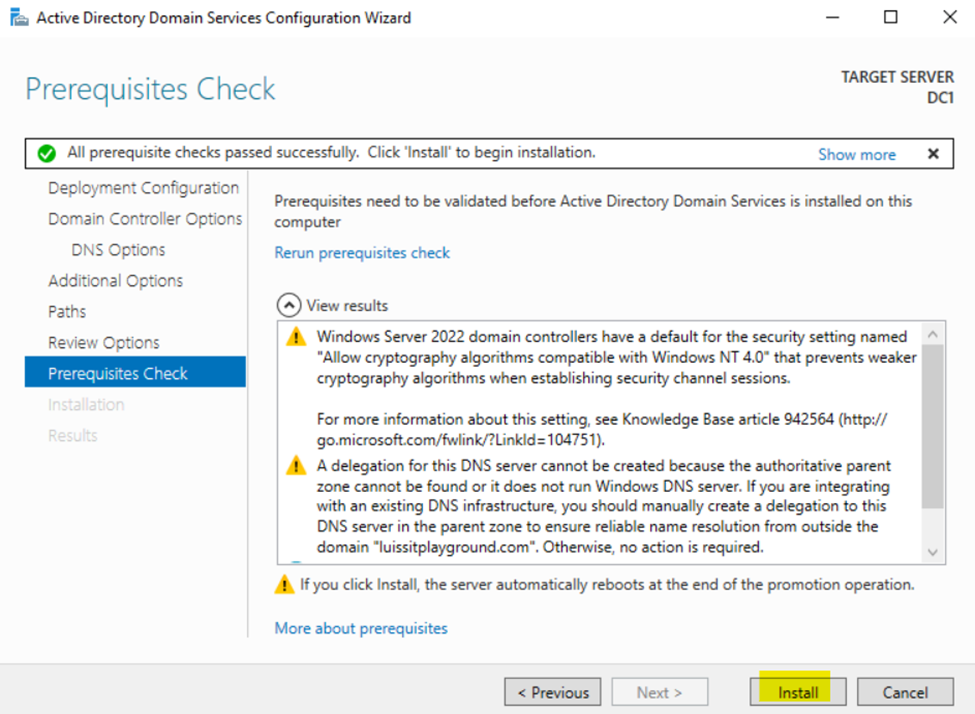
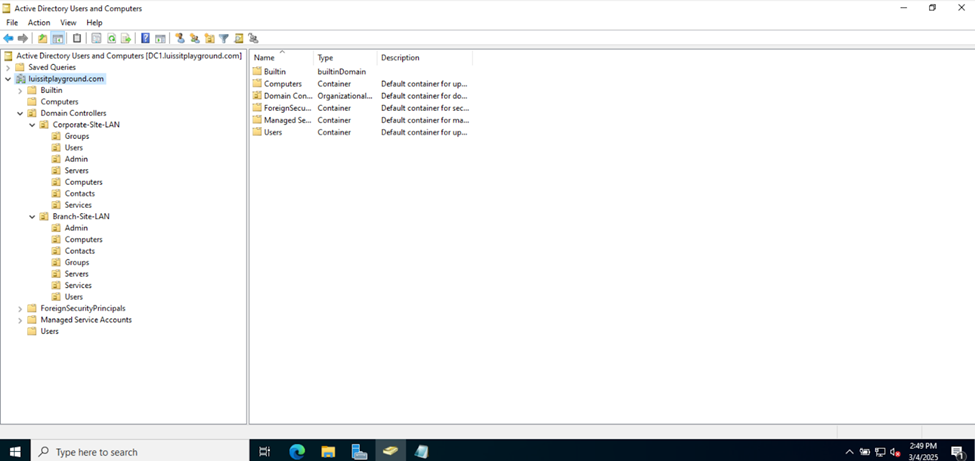
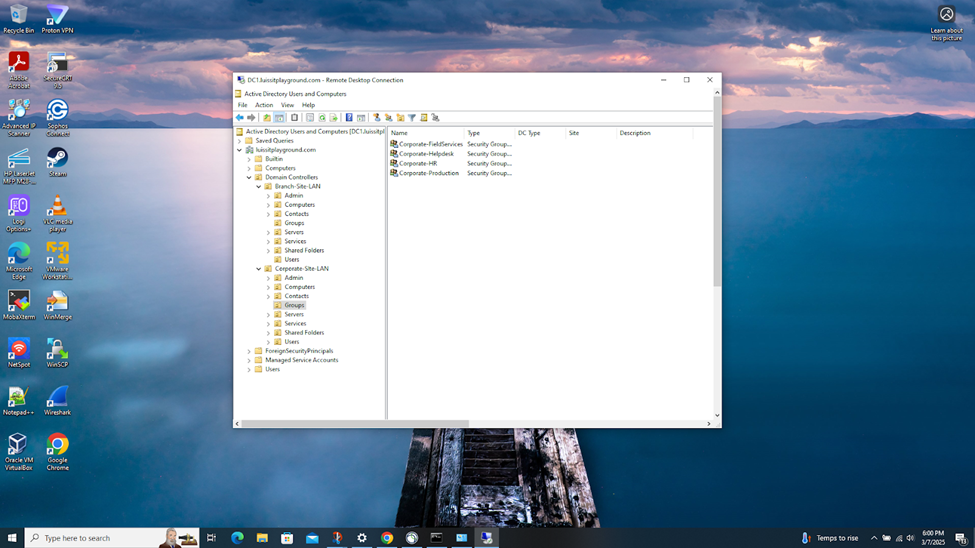
Creating Active Directory Groups & Users
- Resources
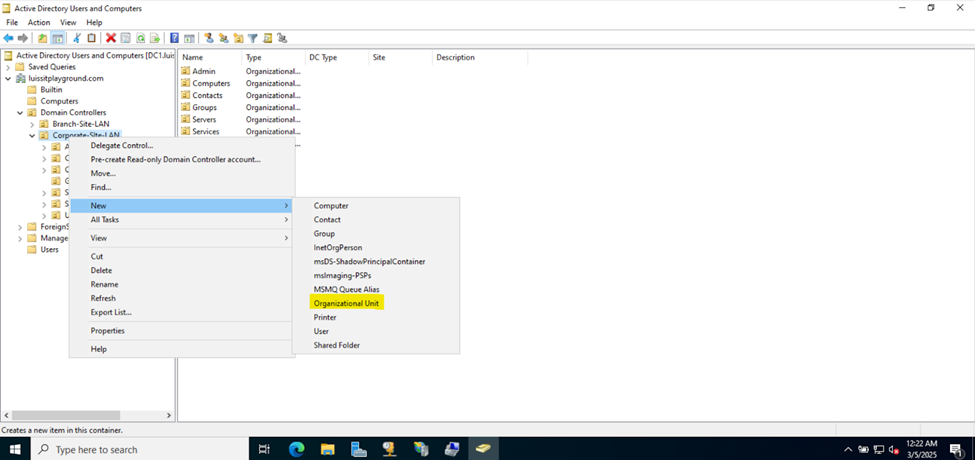
- In this demonstration, I will walk-through setting up Active Directory OUs, groups, and users for the Corporate and Branch site LANs respectively
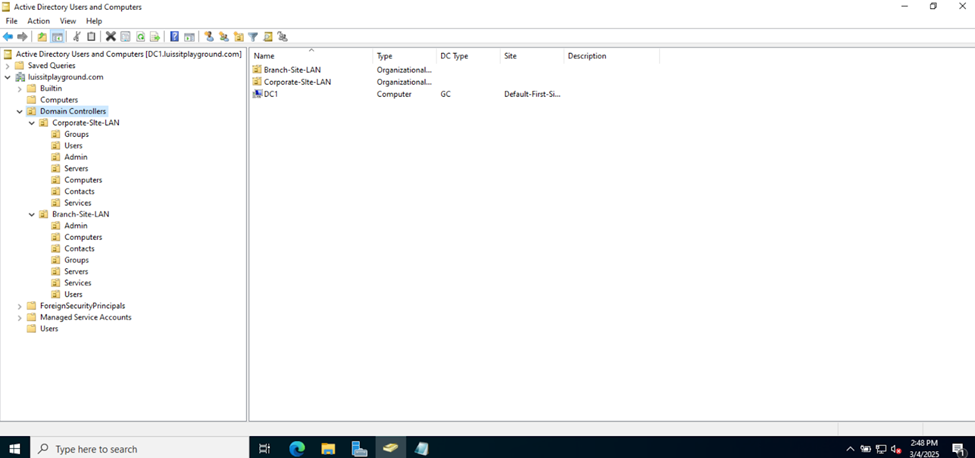
- Active Directory Organizational Units (OUs)
- An OU is a container within AD that helps organize and manage objects like, users, groups, computers, and other resources
- OUs are used to create a hierarchical structure within an AD domain, making it easier for administrators to manage and delegate permissions, apply group policies, and organize resources in a logical manner
- In this demonstration, I will be defining two core OU groups representing the Corporate and Branch site LANs and their respective internal OUs, security groups, and users
- In summary, having multiple objects and groups in Active Directory tailored for different purposes enhances security, simplifies administration as the organization scales, ensures compliance, and makes the overall management of users and resources more efficient
Organizational Units (OUs)
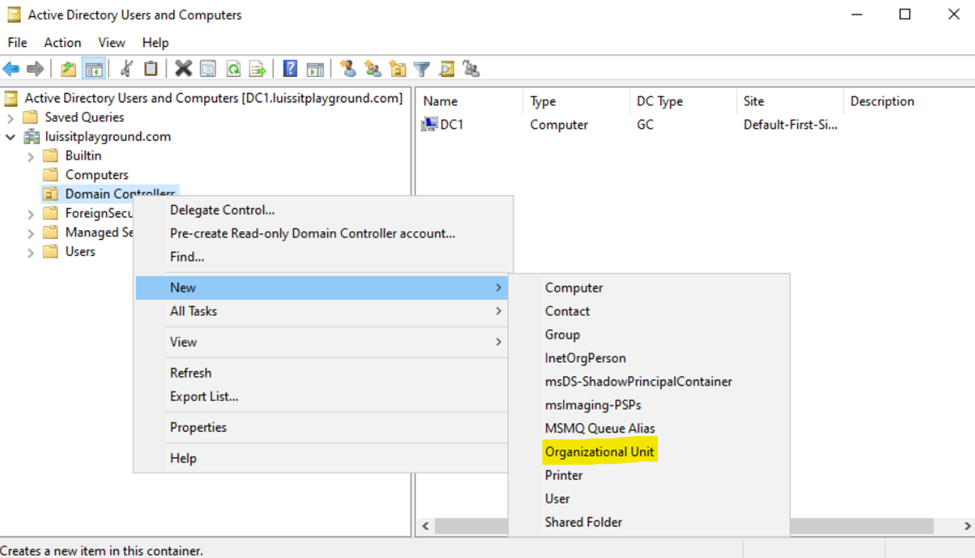
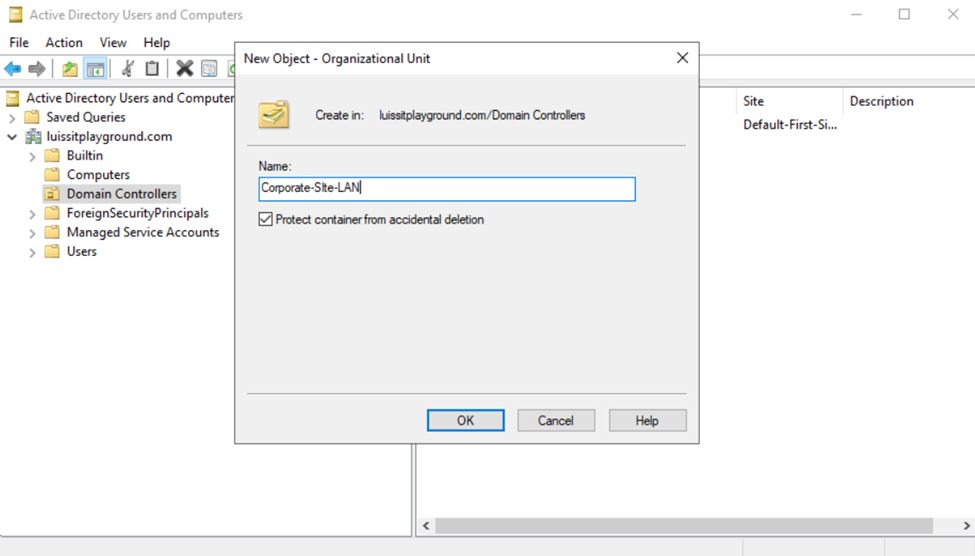
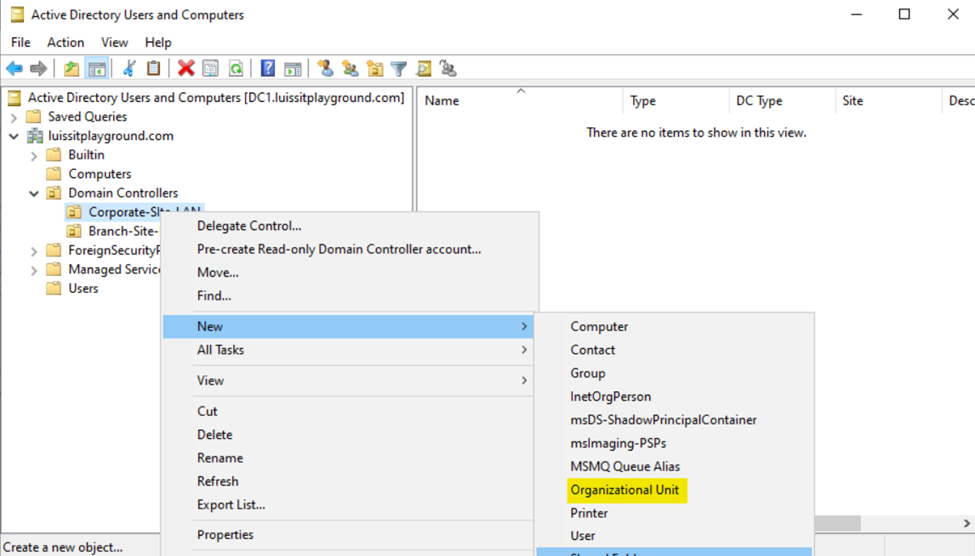
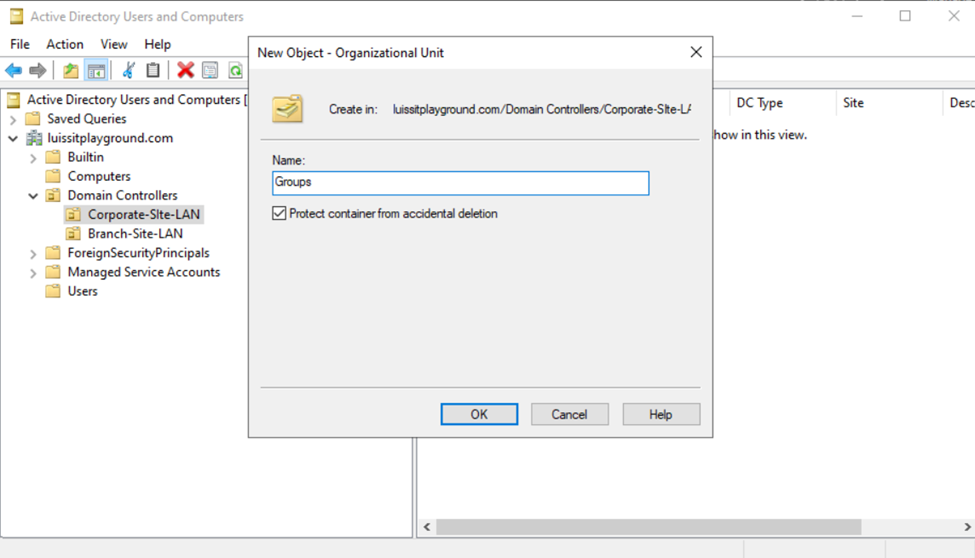
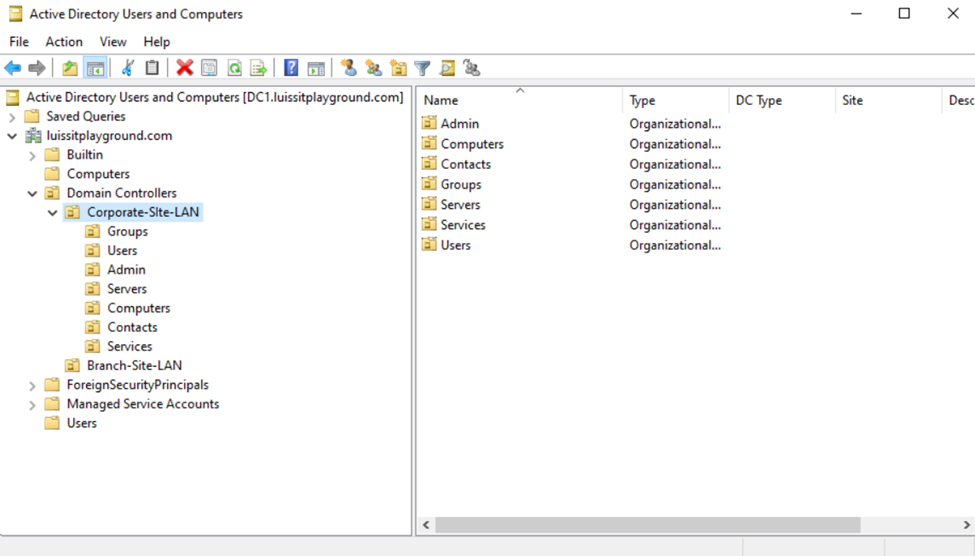
Users (Domain Accounts)
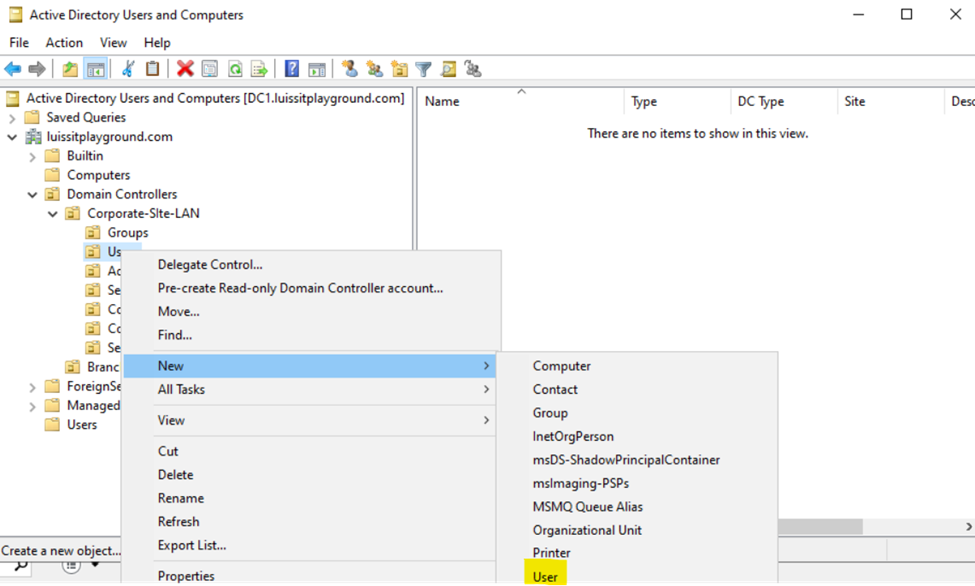
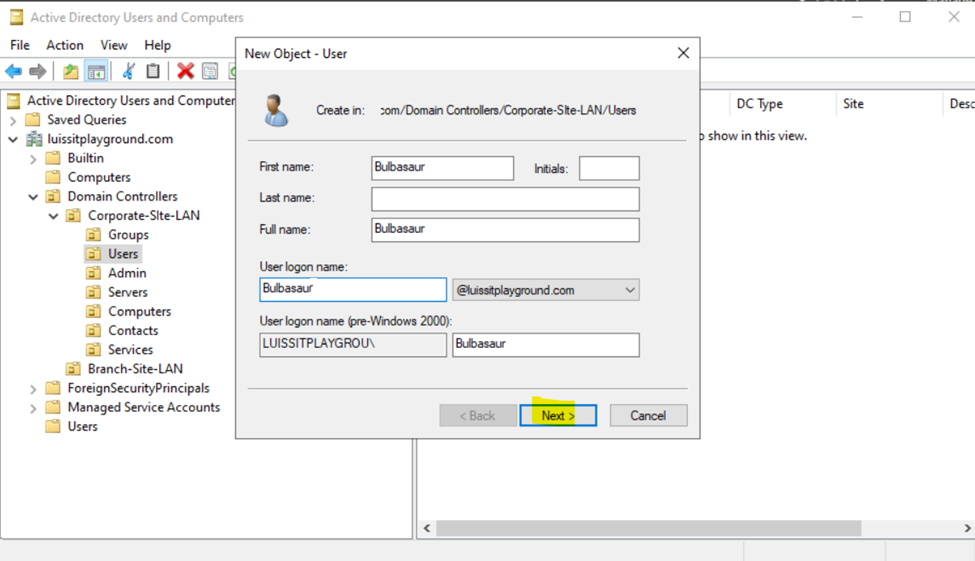
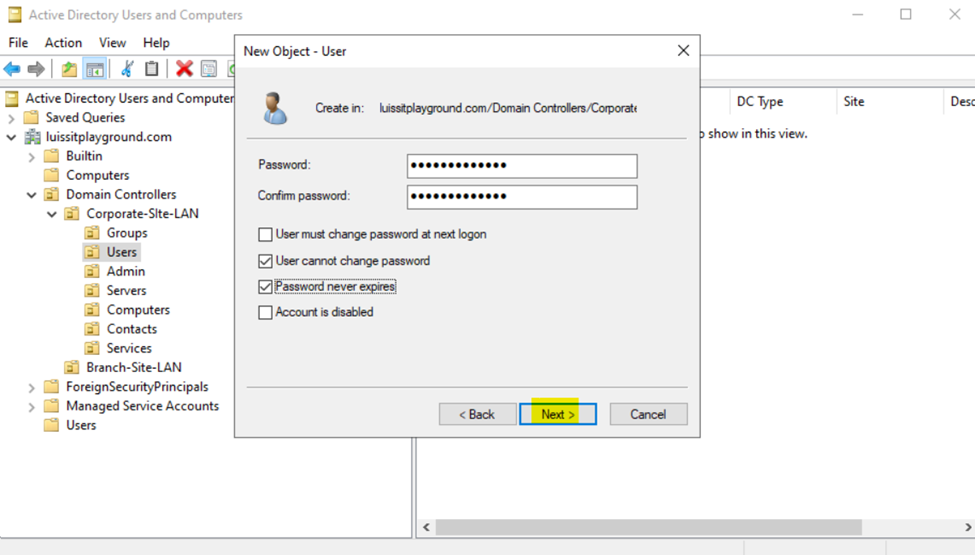
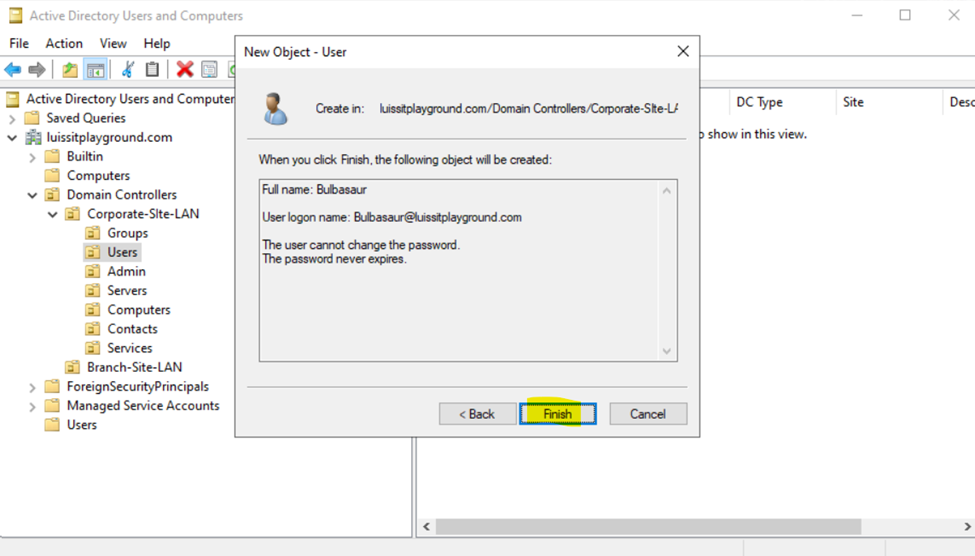
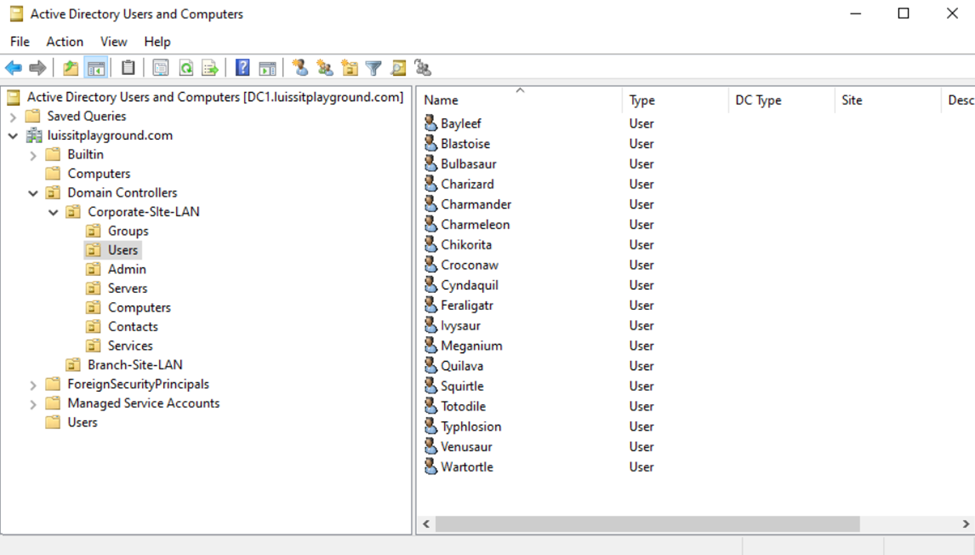
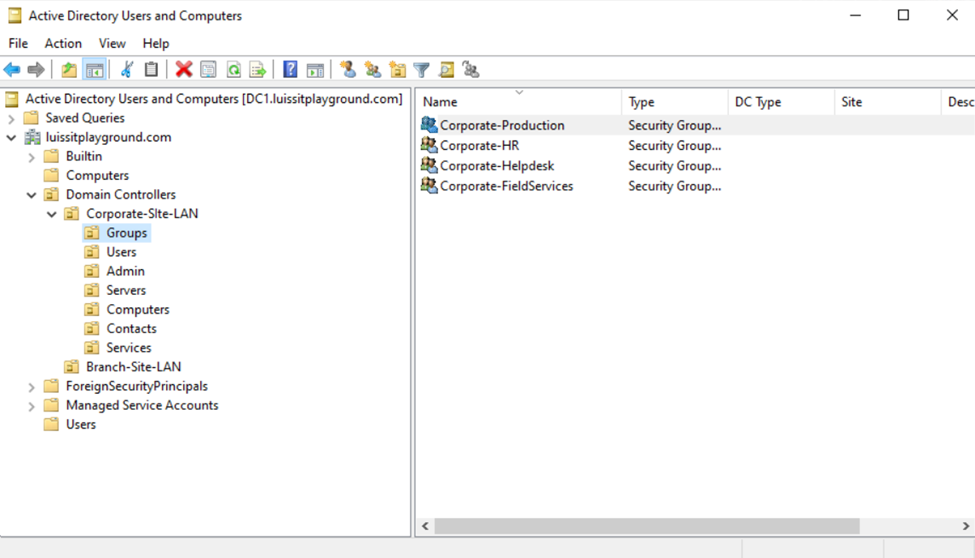
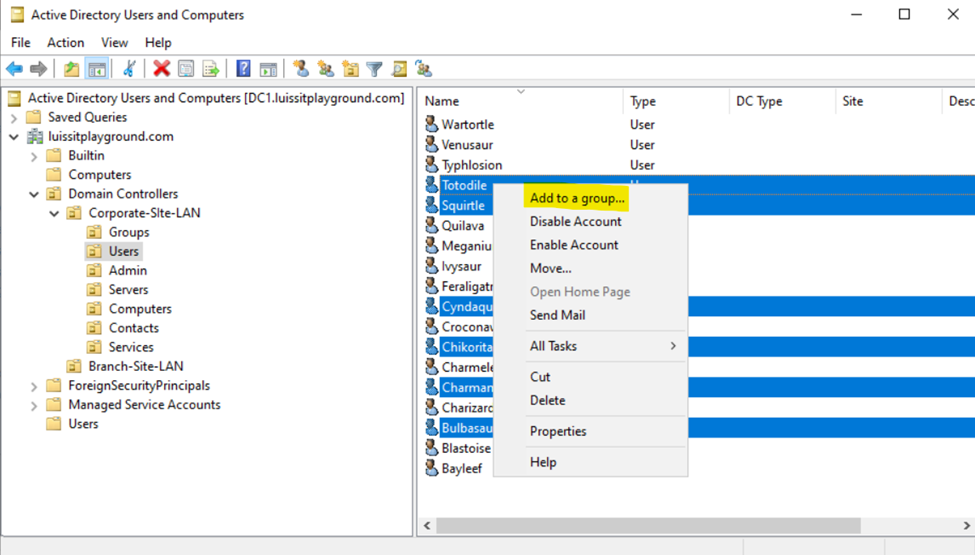
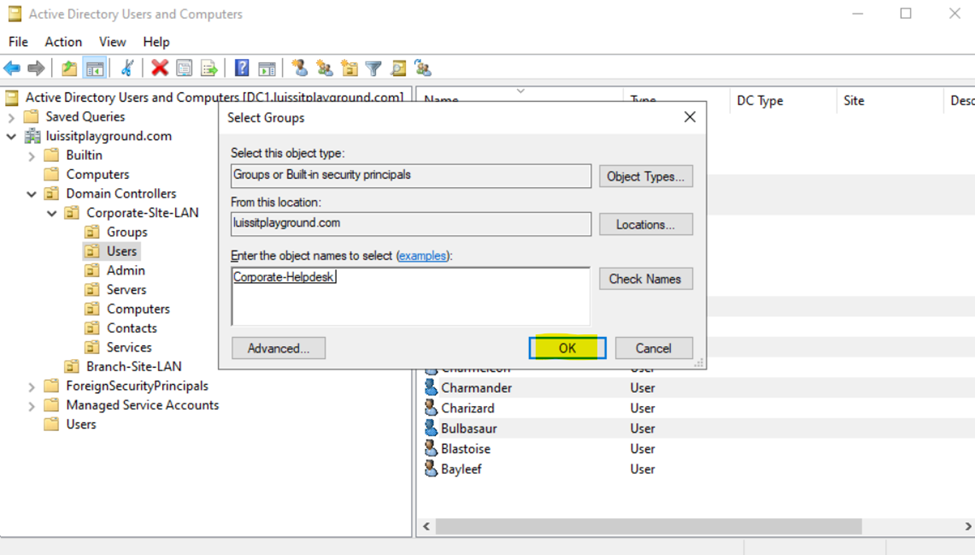
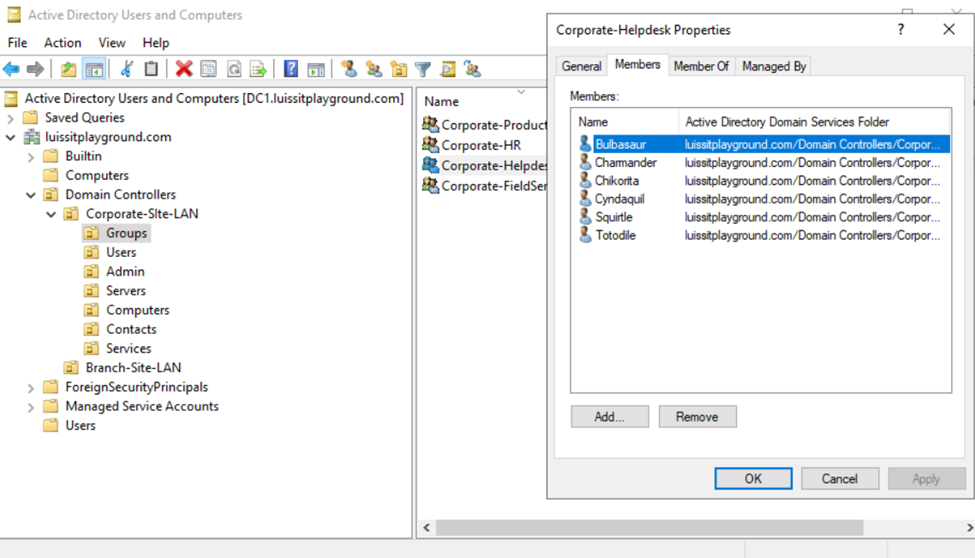
Security Groups
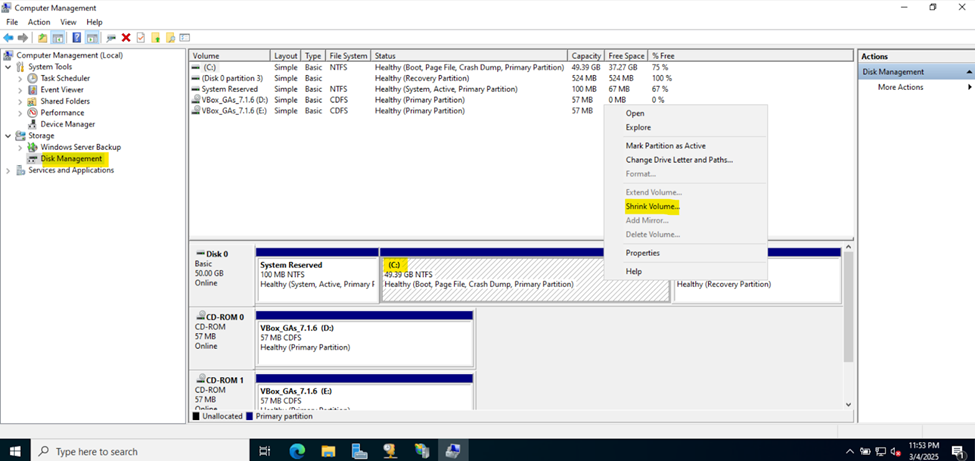
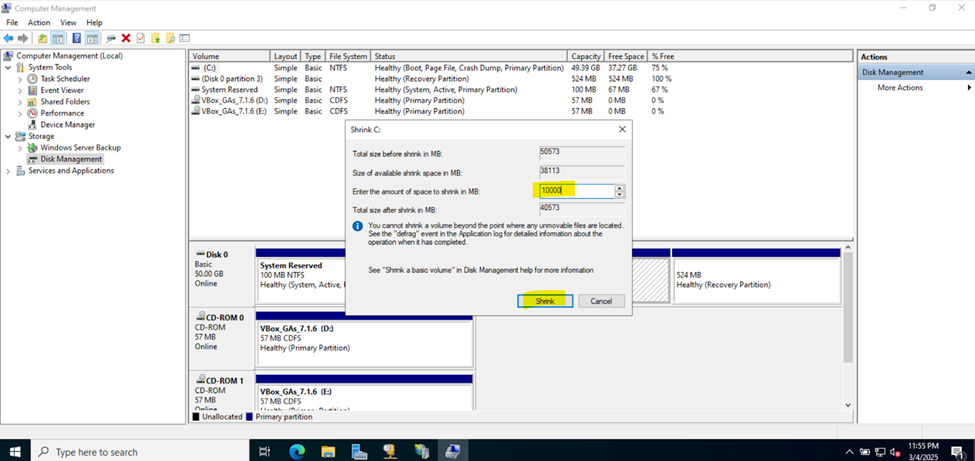
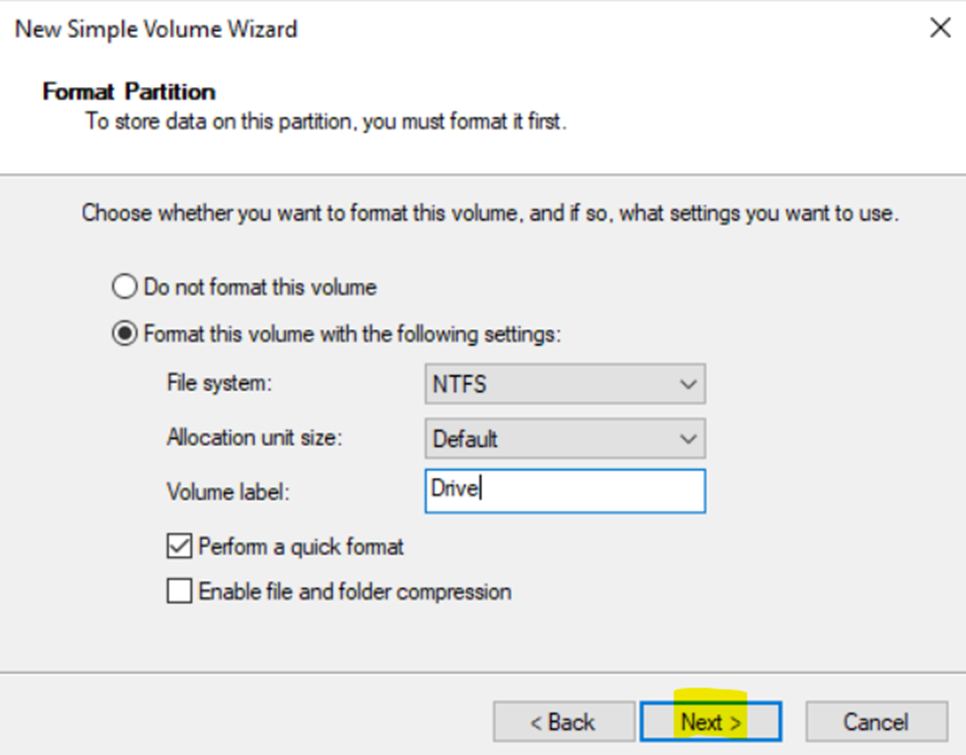
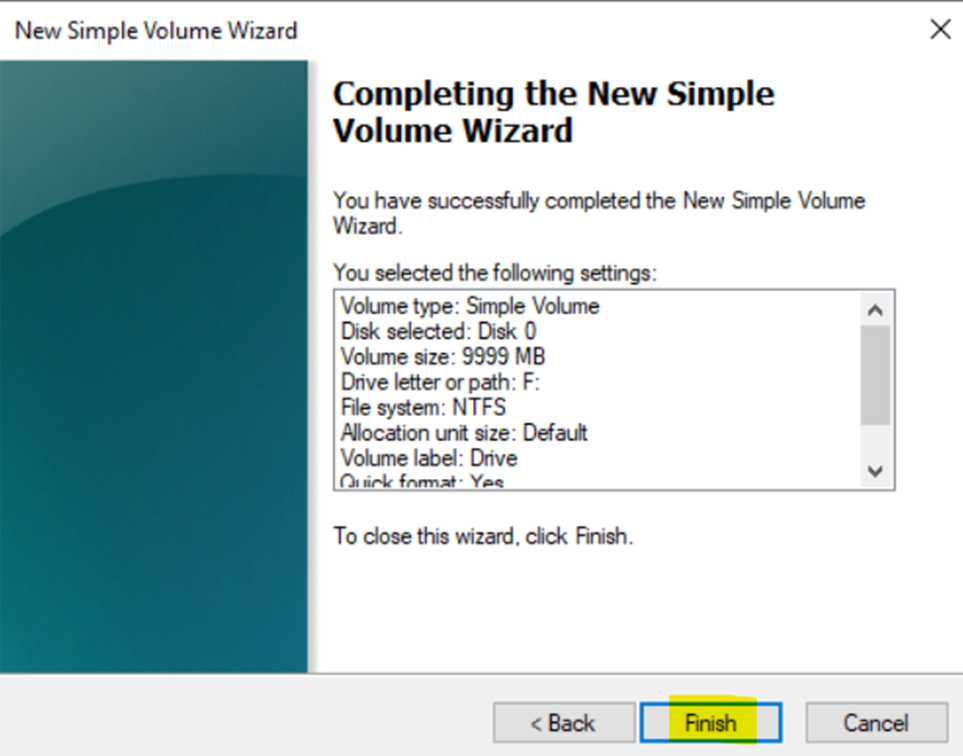
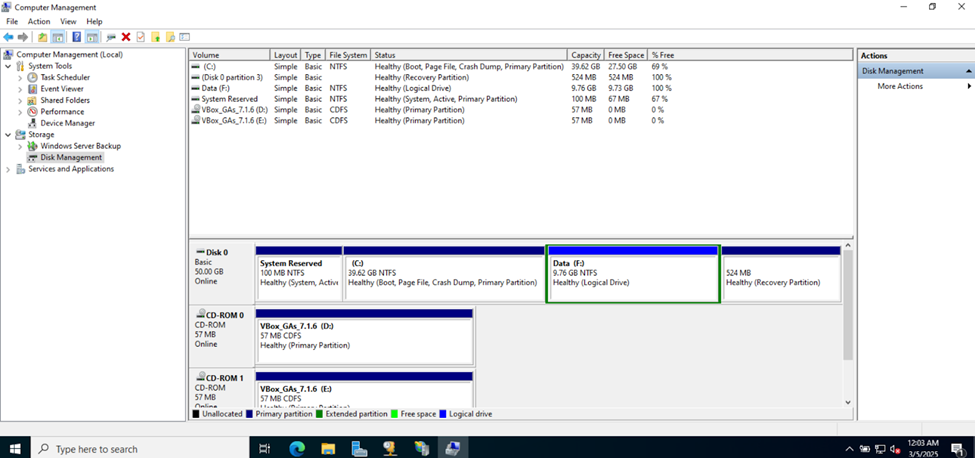
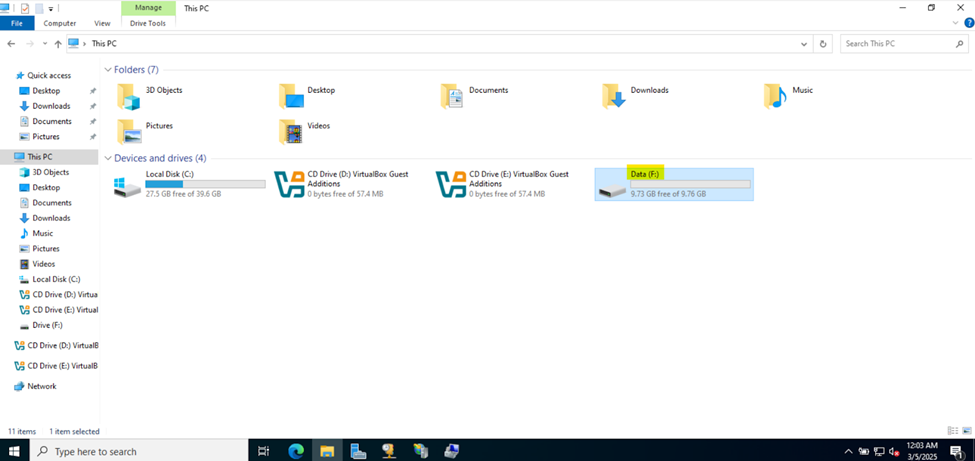
Creating Hard Drive Partition for Network Shares
- Resources
- In this demonstration, I will walk-through creating a new Hard Drive partition dedicated for network shares across the domain
- Although not required, having a dedicated partition for network shares can help separate shared data from the operating system and other application data. This makes the system more organized and easier to manage
- If the partition is separate from other data, it helps in isolating shared resources, reducing the risk of accidental modification or deletion of system or application files
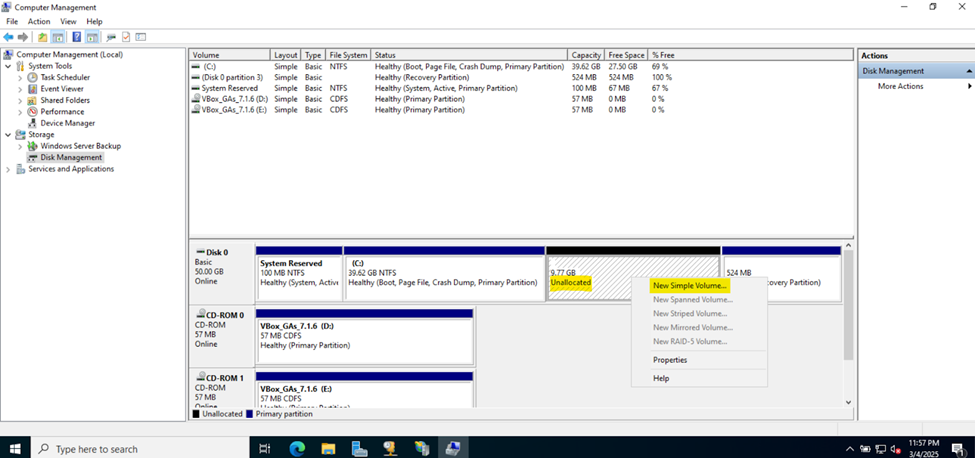
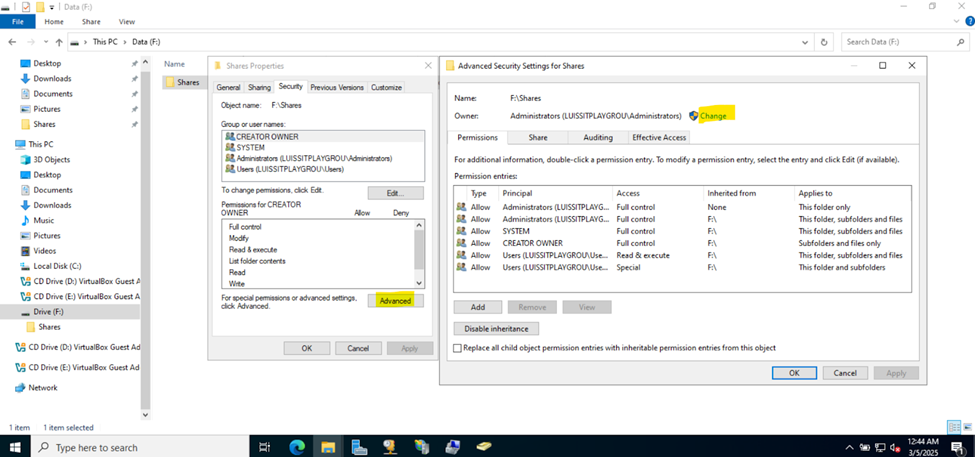
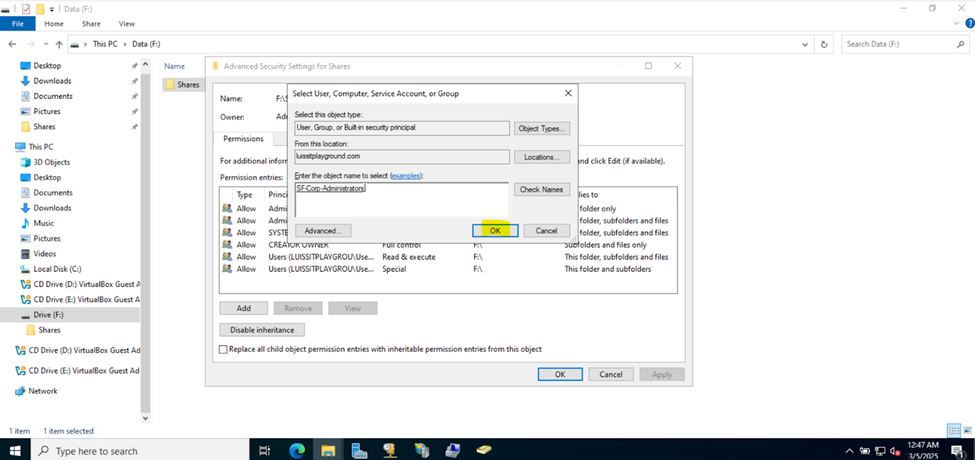
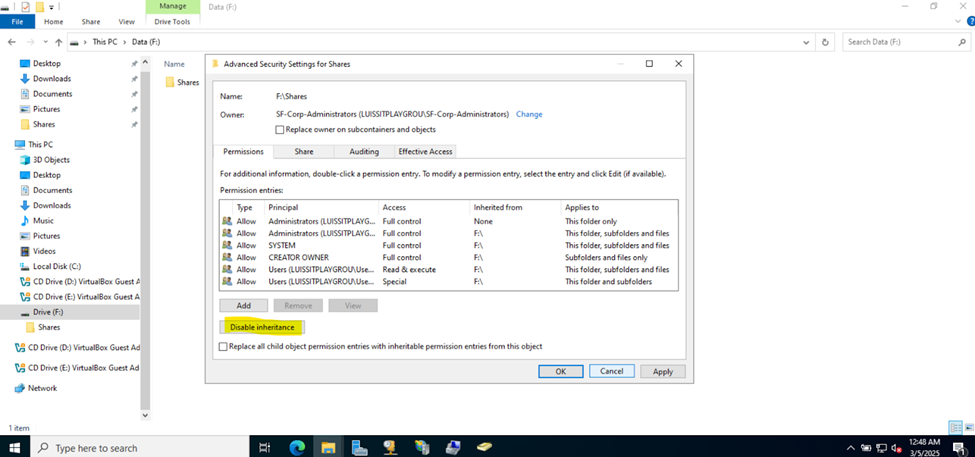
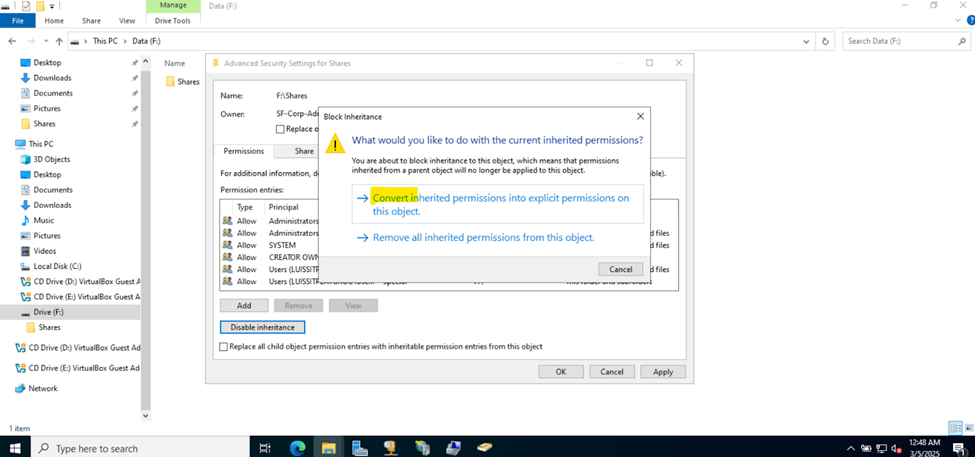
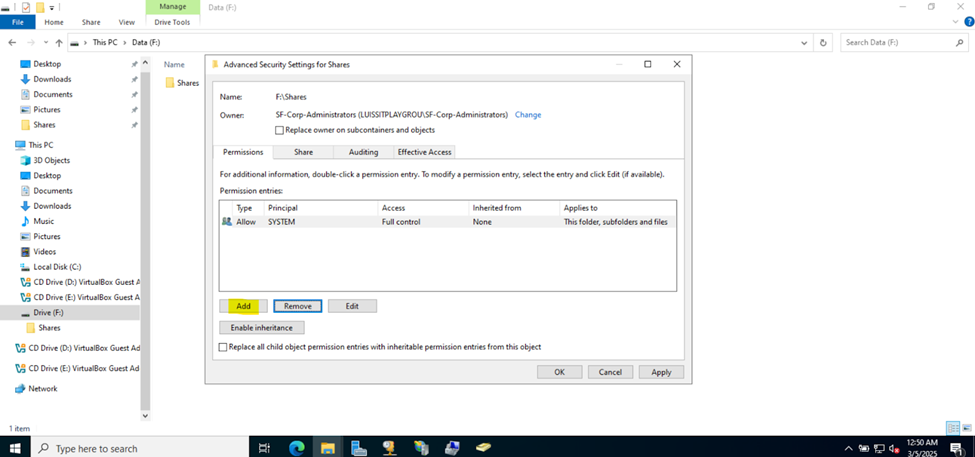
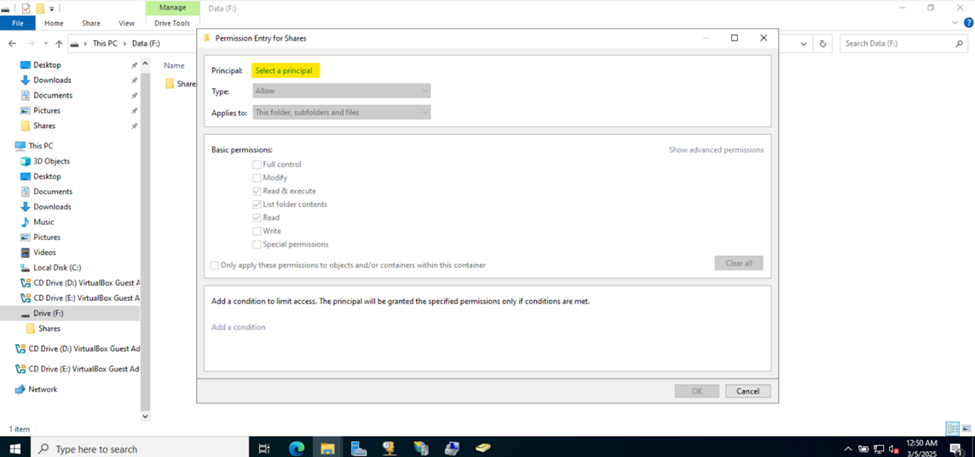
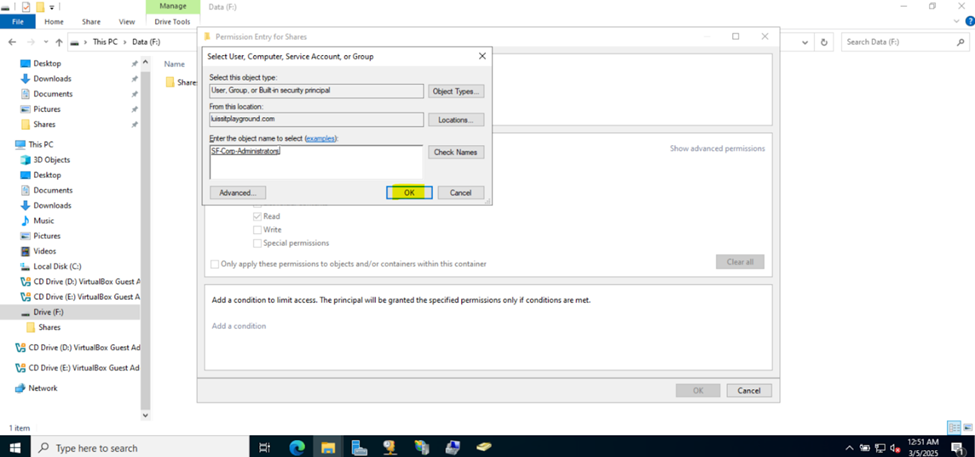
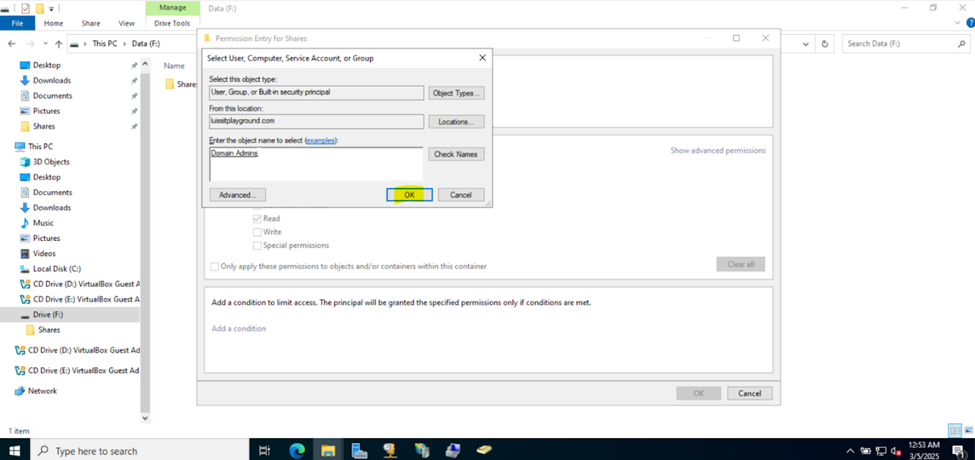
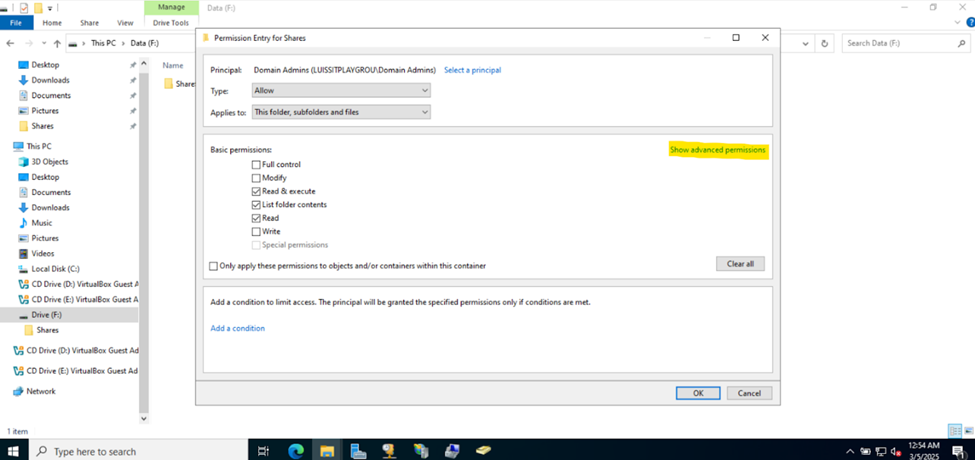
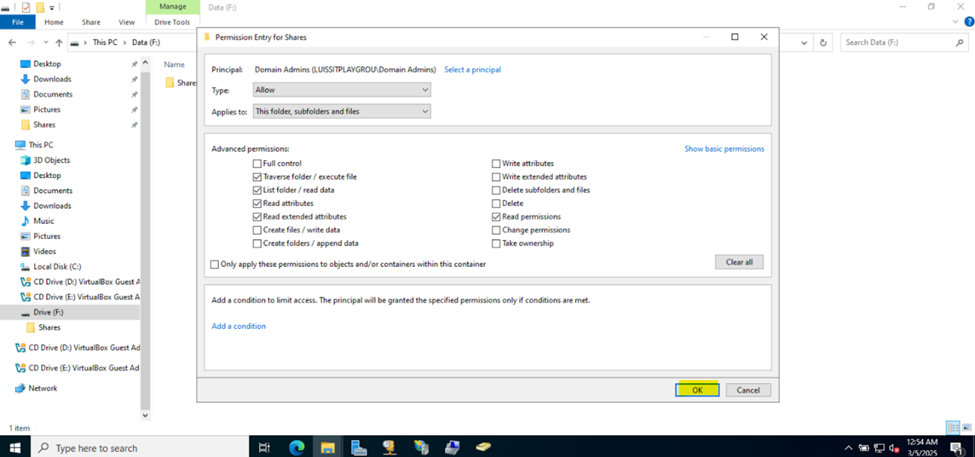
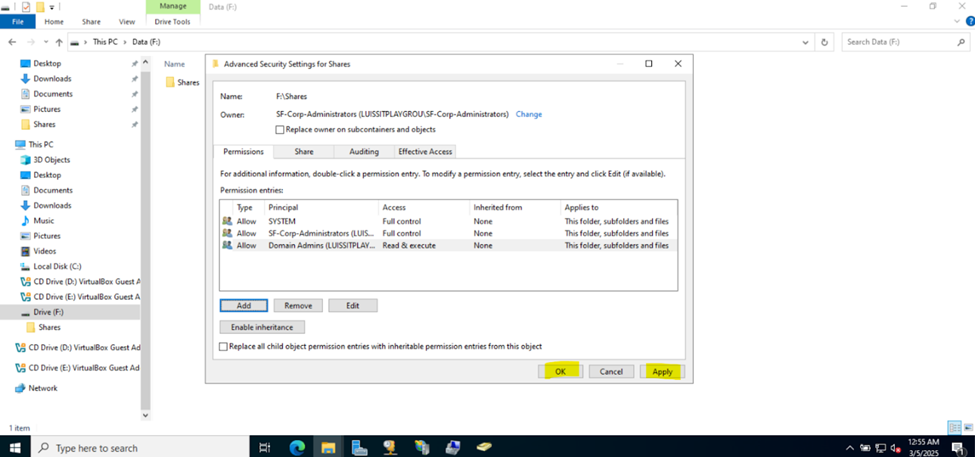
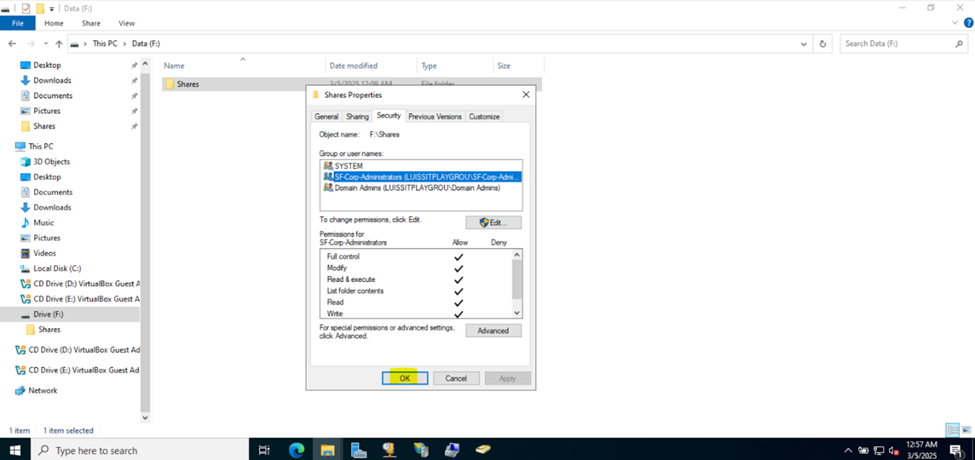
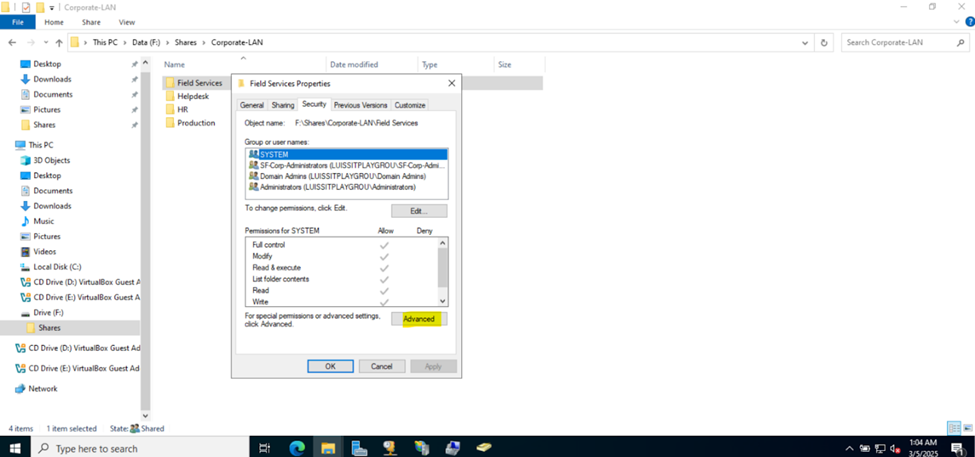
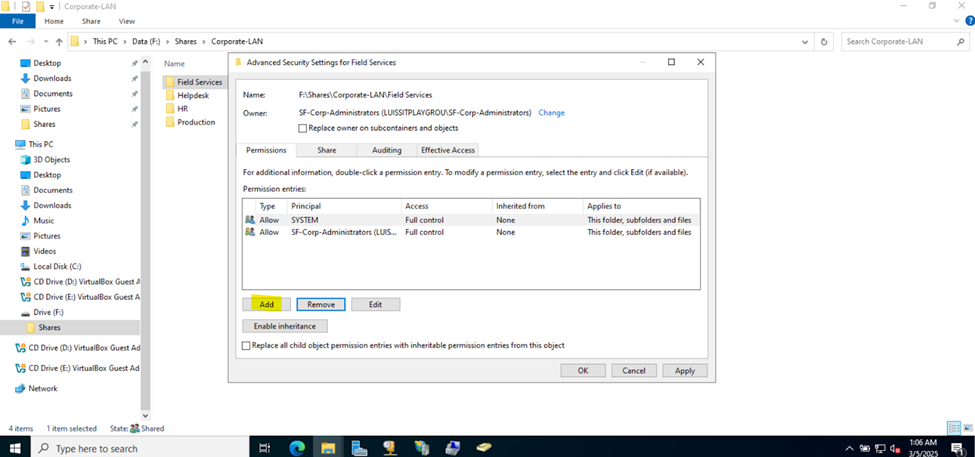
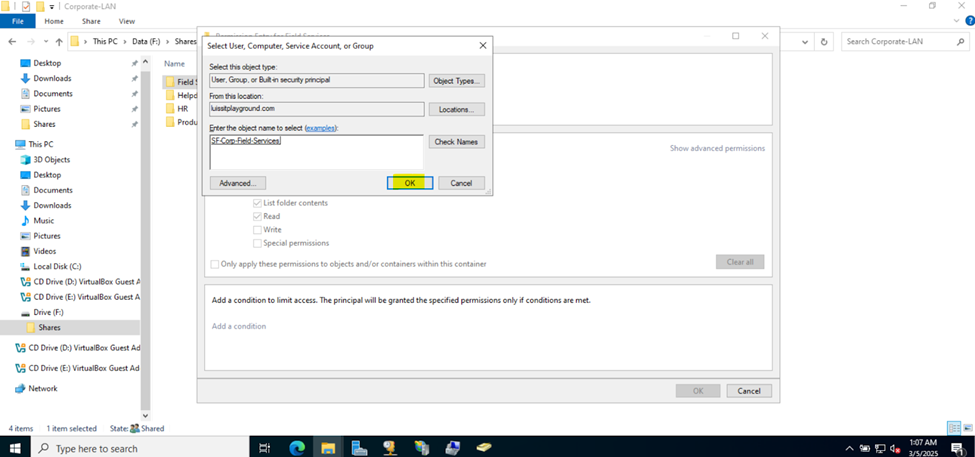
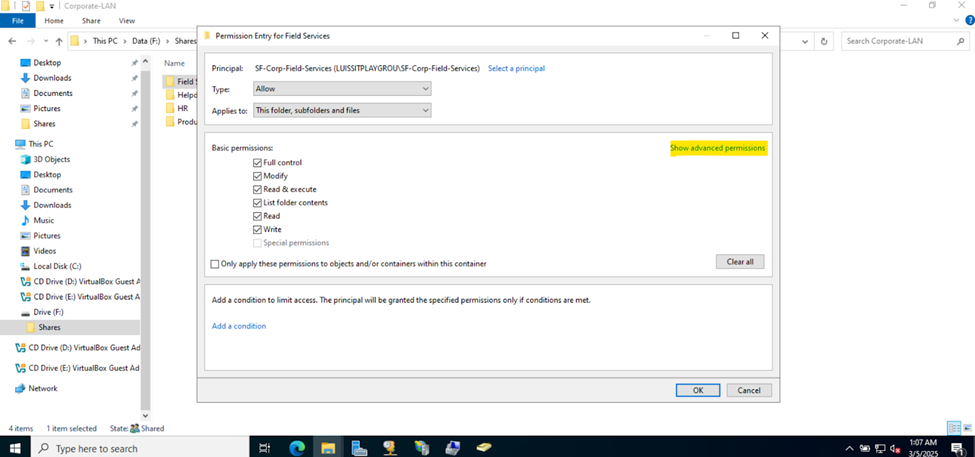
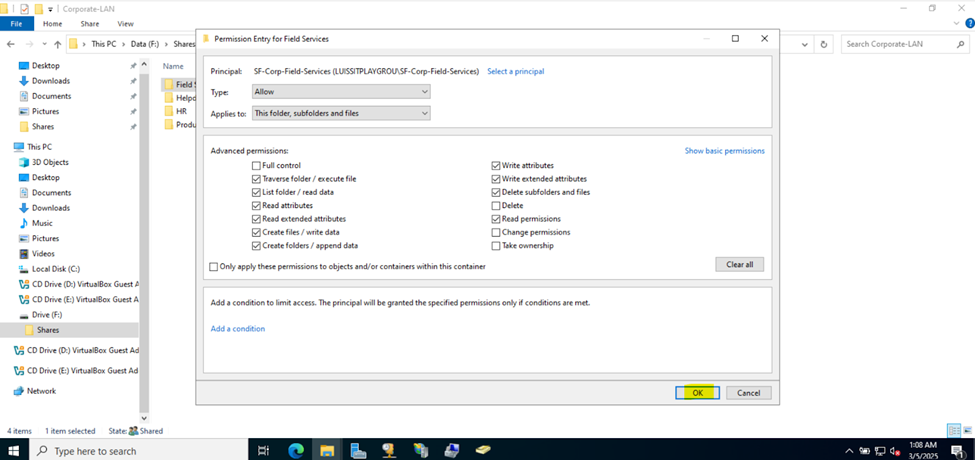
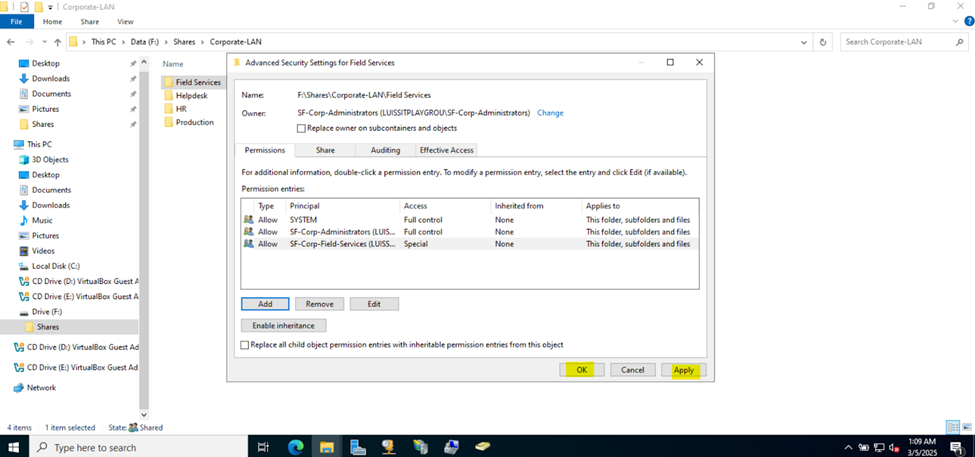
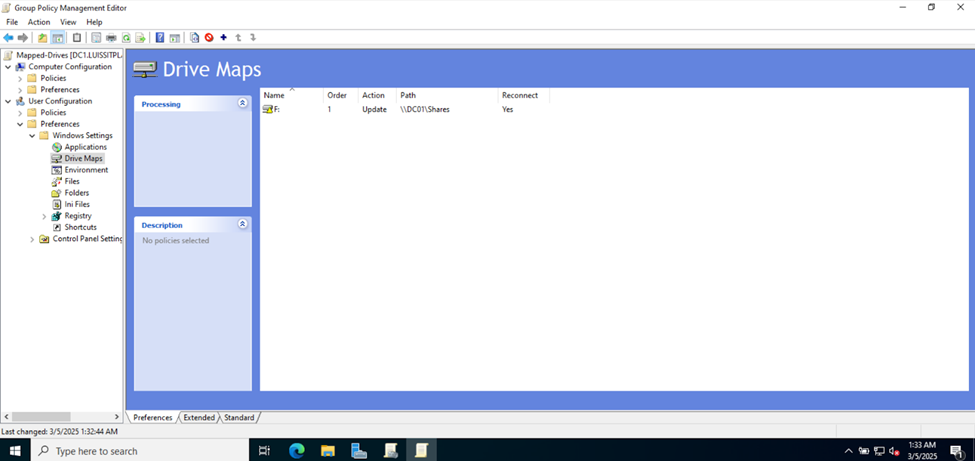
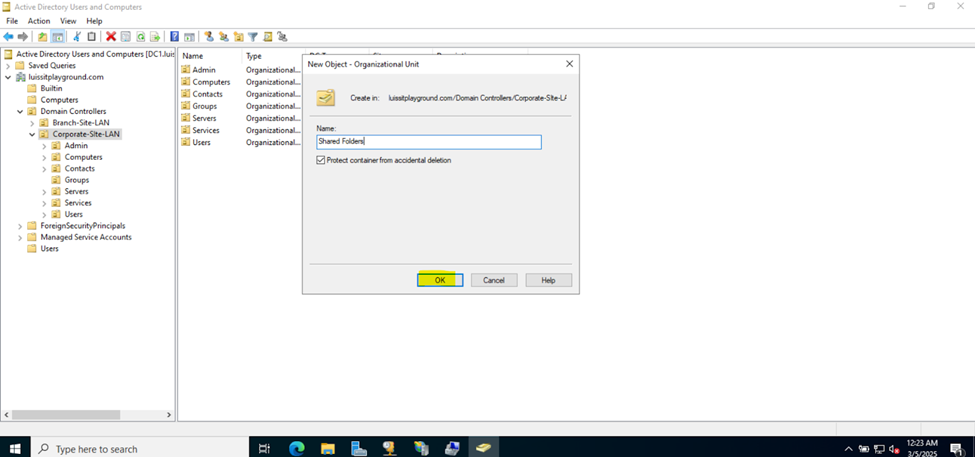
Defining Network Share Folders & Active Directory Groups
- Resources
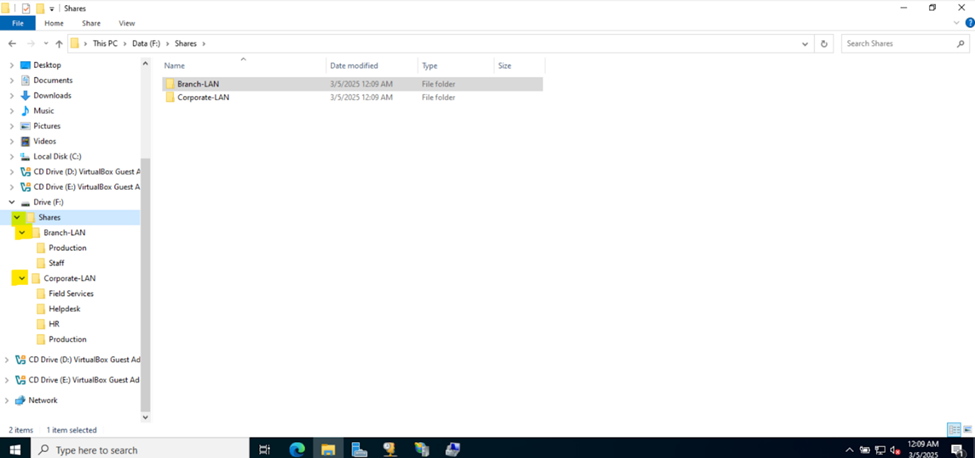
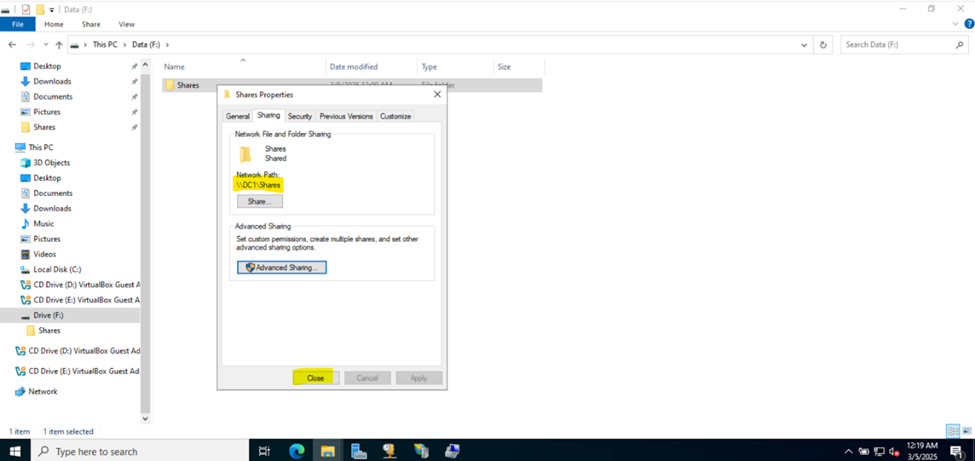
- In this demonstration, I will walk-through defining the network share folders and directories by categorizing them by the networks in my lab environment
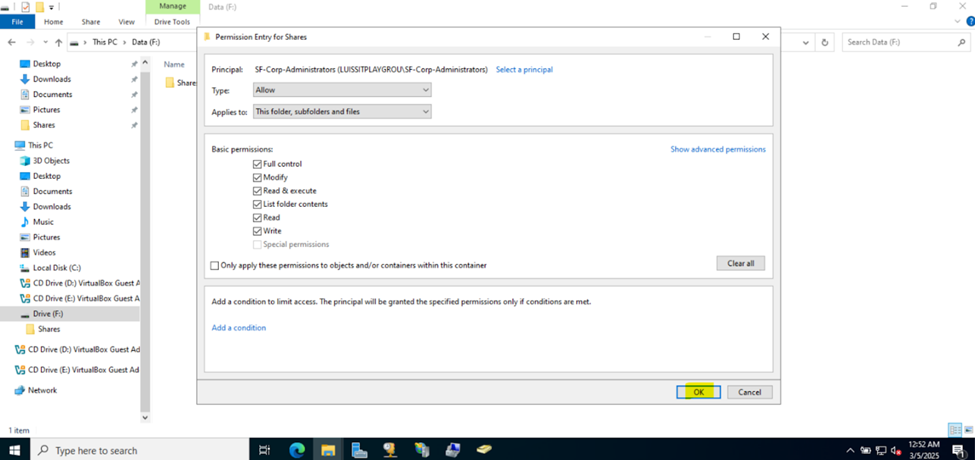
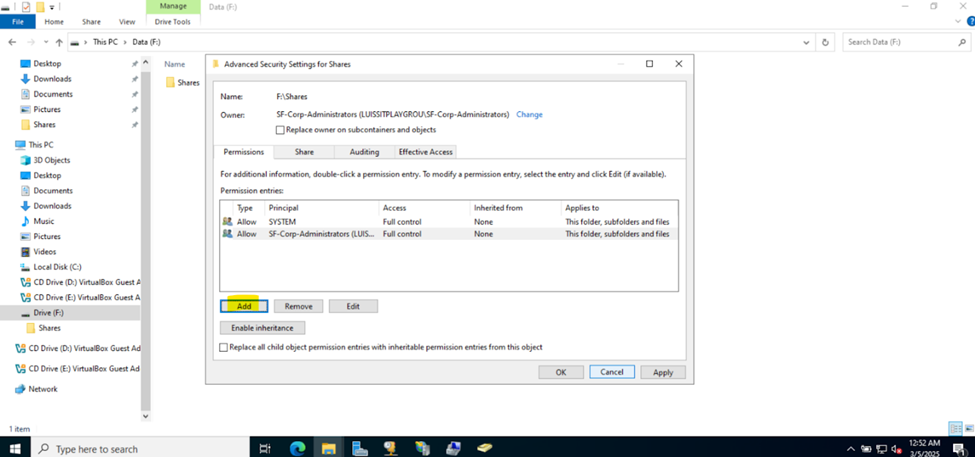
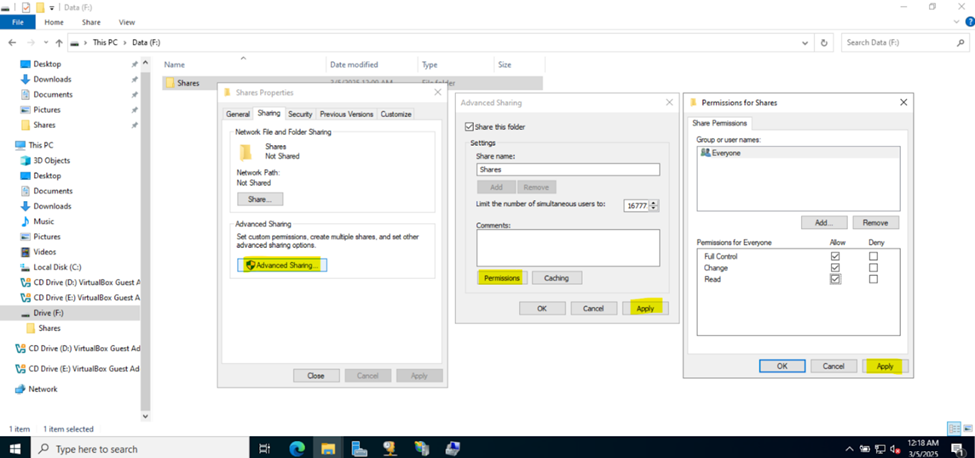
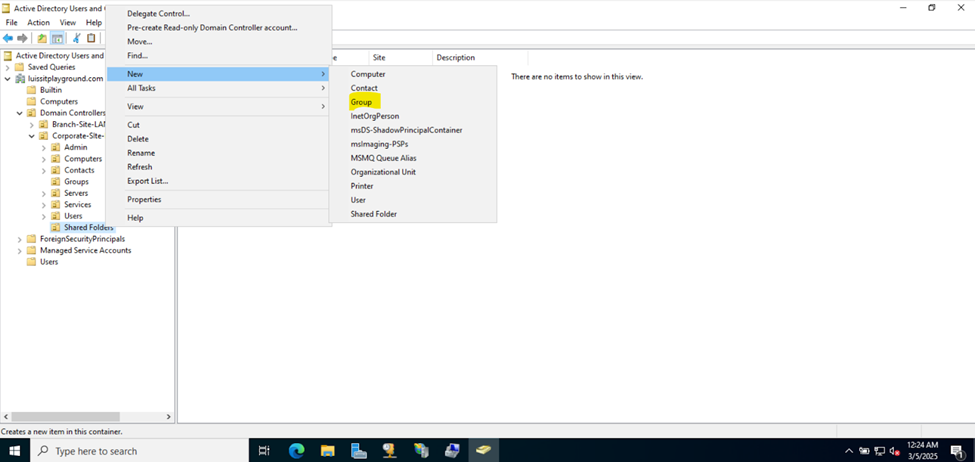
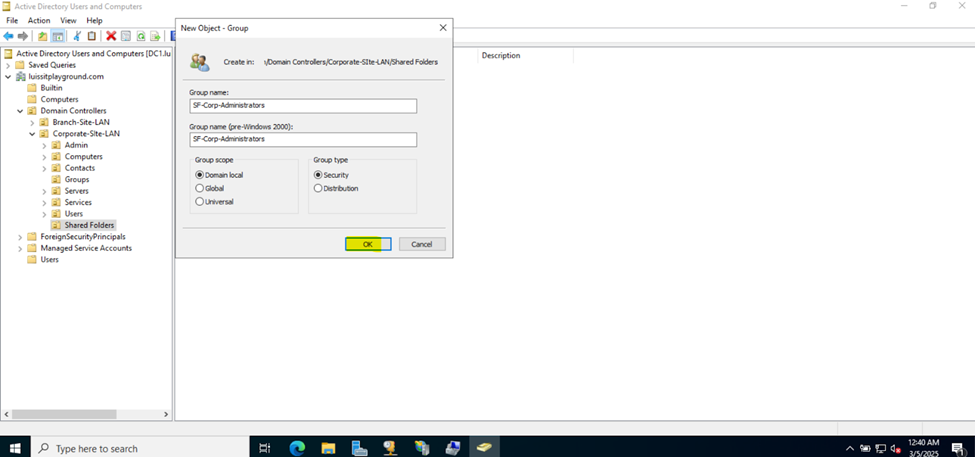
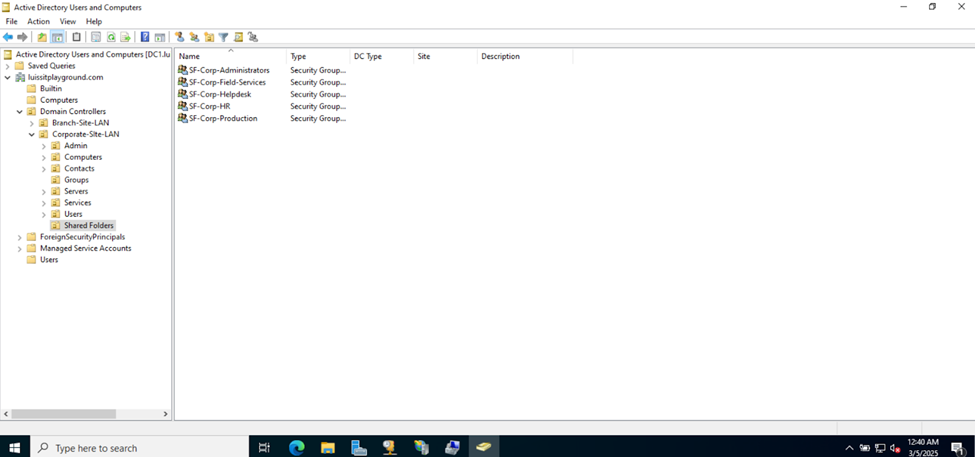
- Upon defining these directories, I will define new Active Directory security groups for the purpose of applying network share permissions
- Instead of applying permissions to individual users, you can apply permissions to groups, simplifying management. For example, instead of adding individual users to a shared folder's security settings, you can add an AD security group (HR Department) to the folder's permissions
- If you need to apply the same set of permissions to multiple users or resources, using AD security groups ensures consistency across all users. This prevents potential errors or inconsistencies in permissions
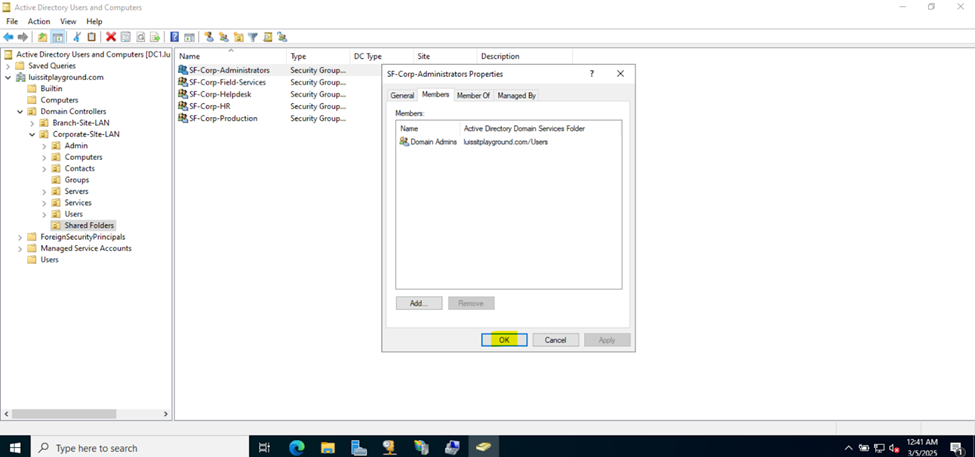
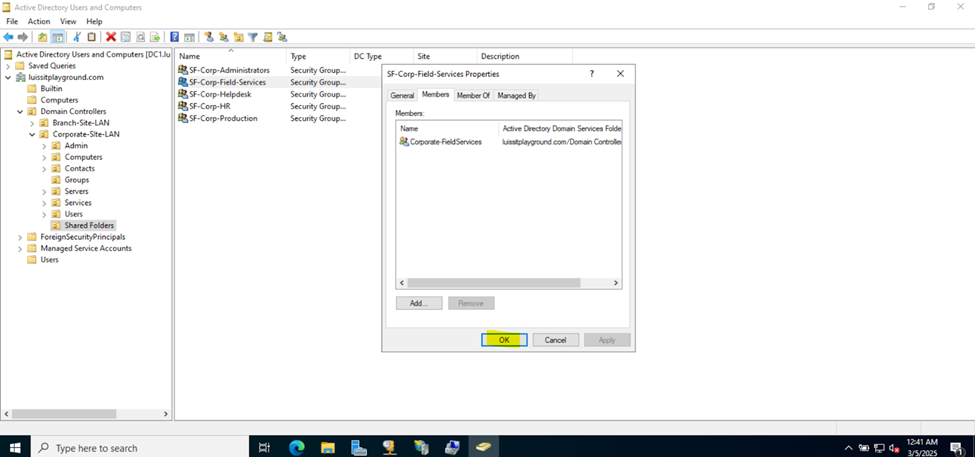
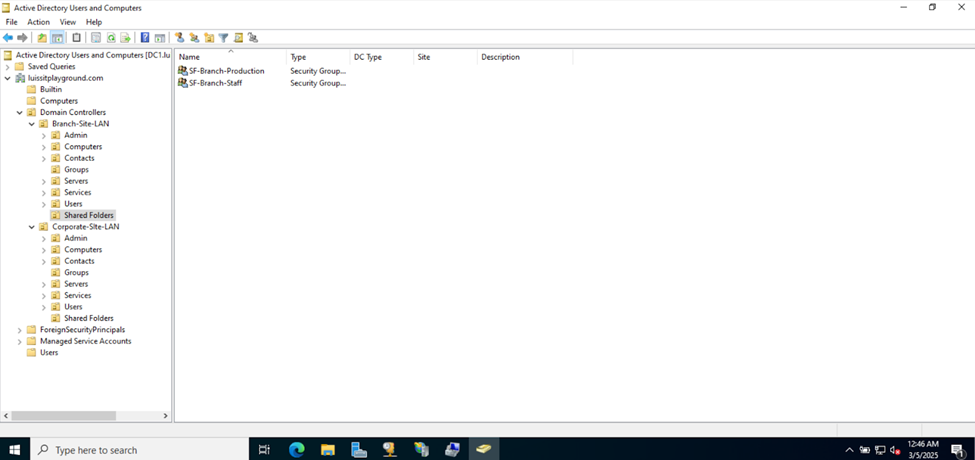
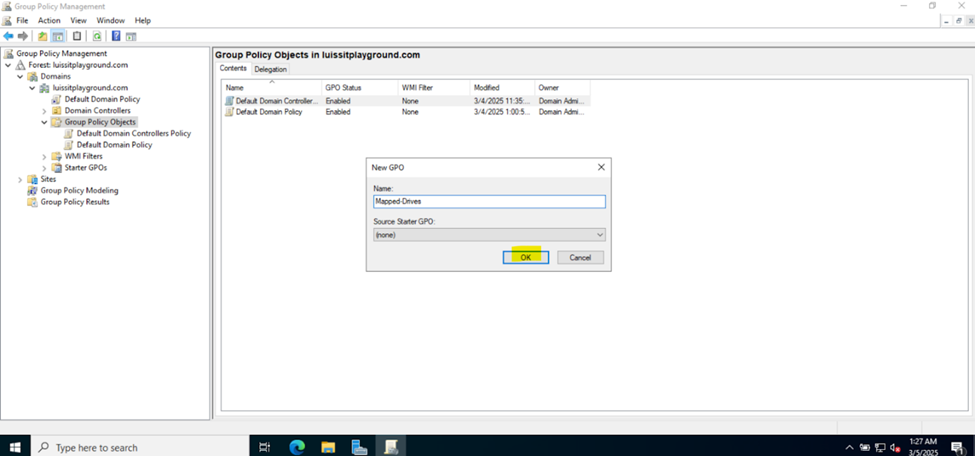
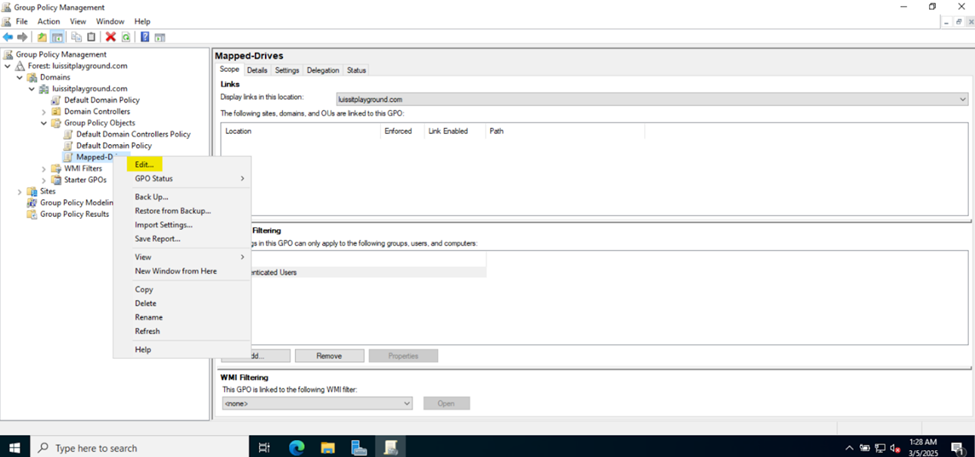
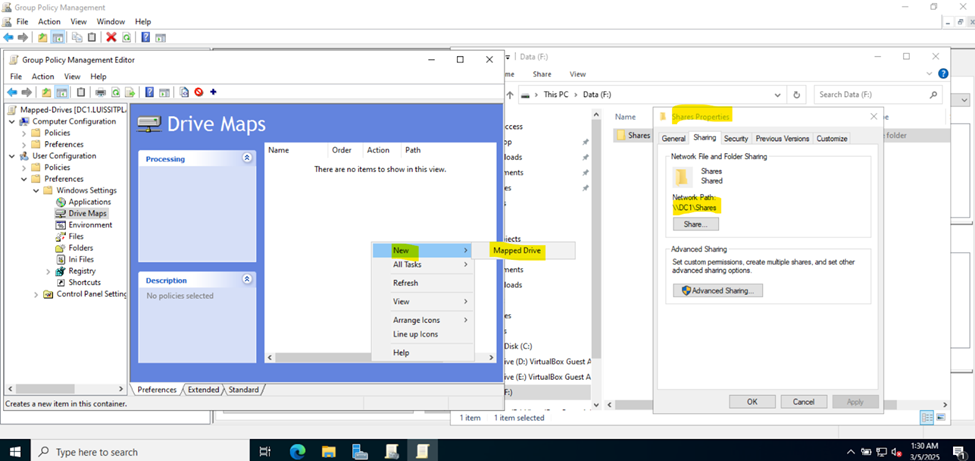
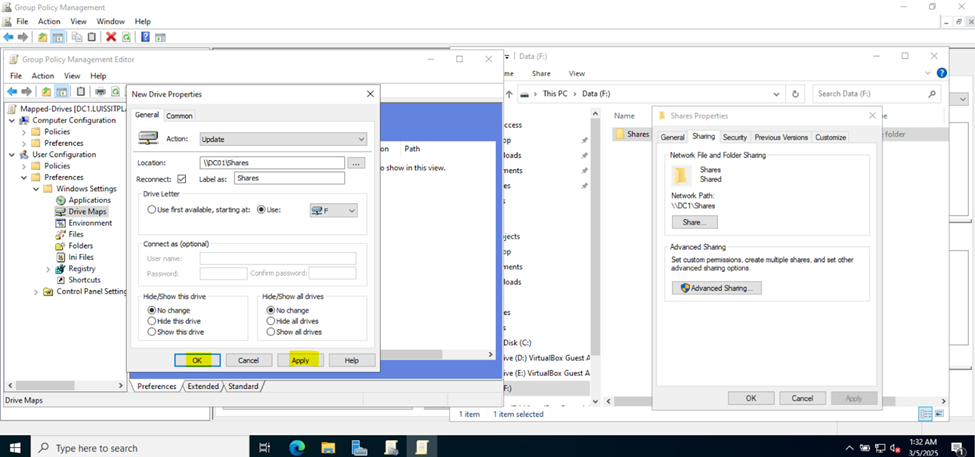
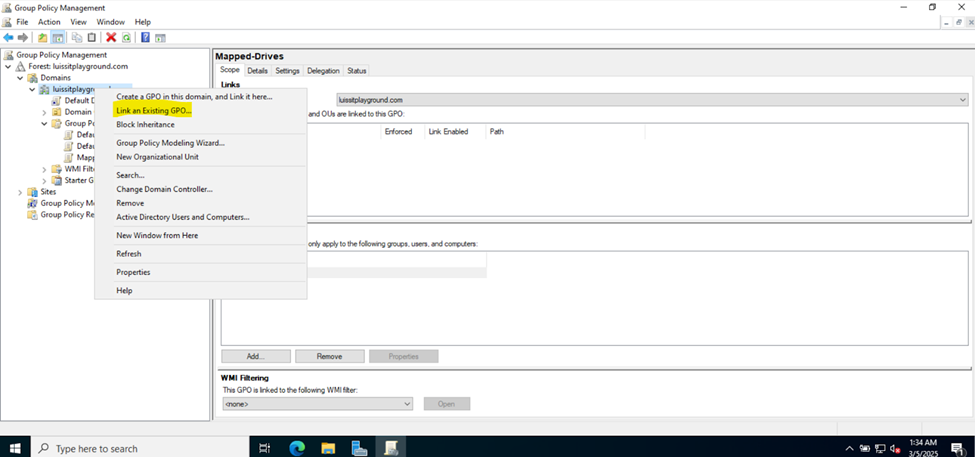
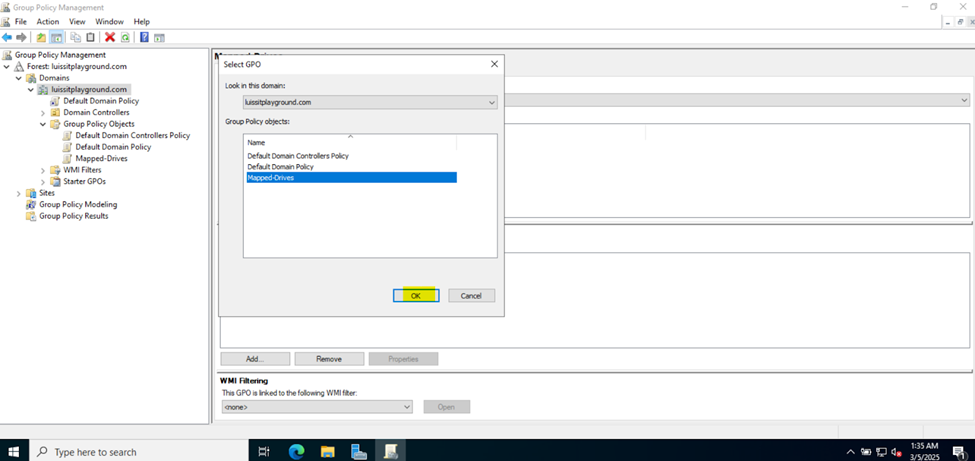
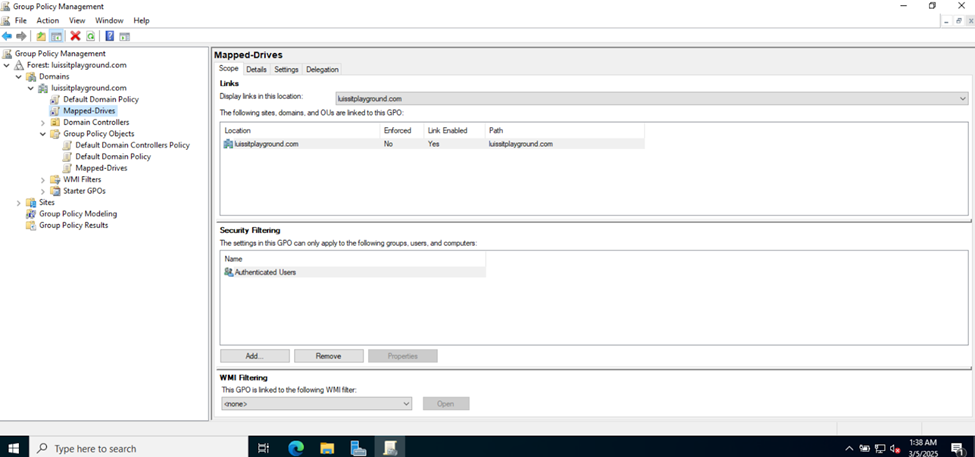
Joining a Windows Domain
- Resources
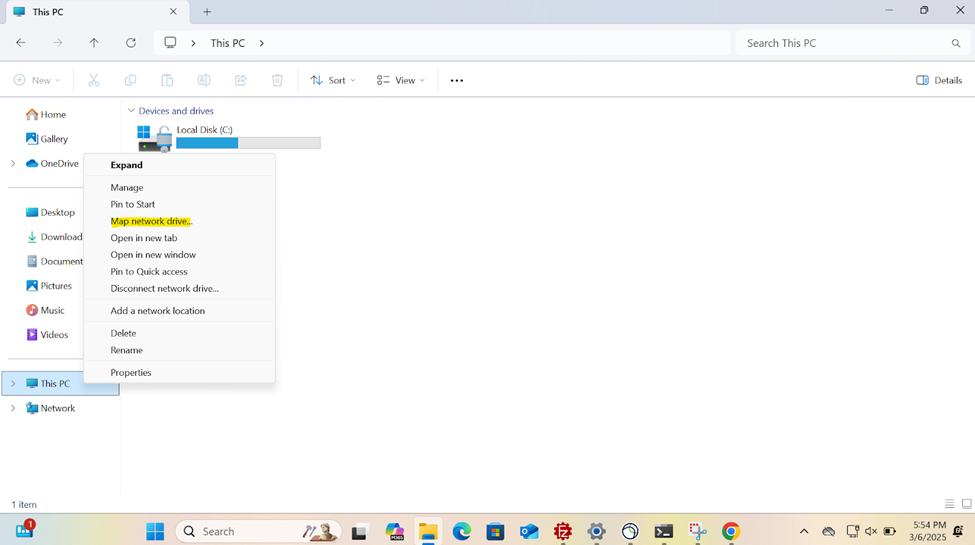
- In this demonstration, I will walk-through joining a Windows 11 client in the Helpdesk VLAN to the Windows domain server and map the network drive accessible by the Windows domain server defined in the 'Create a Windows File Server Share' section
- In this demonstration, I have the Sophos Firewall acting as the DNS server for resolving internal IP addresses to hostnames. Under the Sophos Firewall, I have a DNS host entry pointing to the Windows server 'DC1'
- Once a PC joins a domain, the domain controller can enforce policies, configurations, and updates ensuring that all domain-joined PCs are consistent in terms of security settings and software configurations
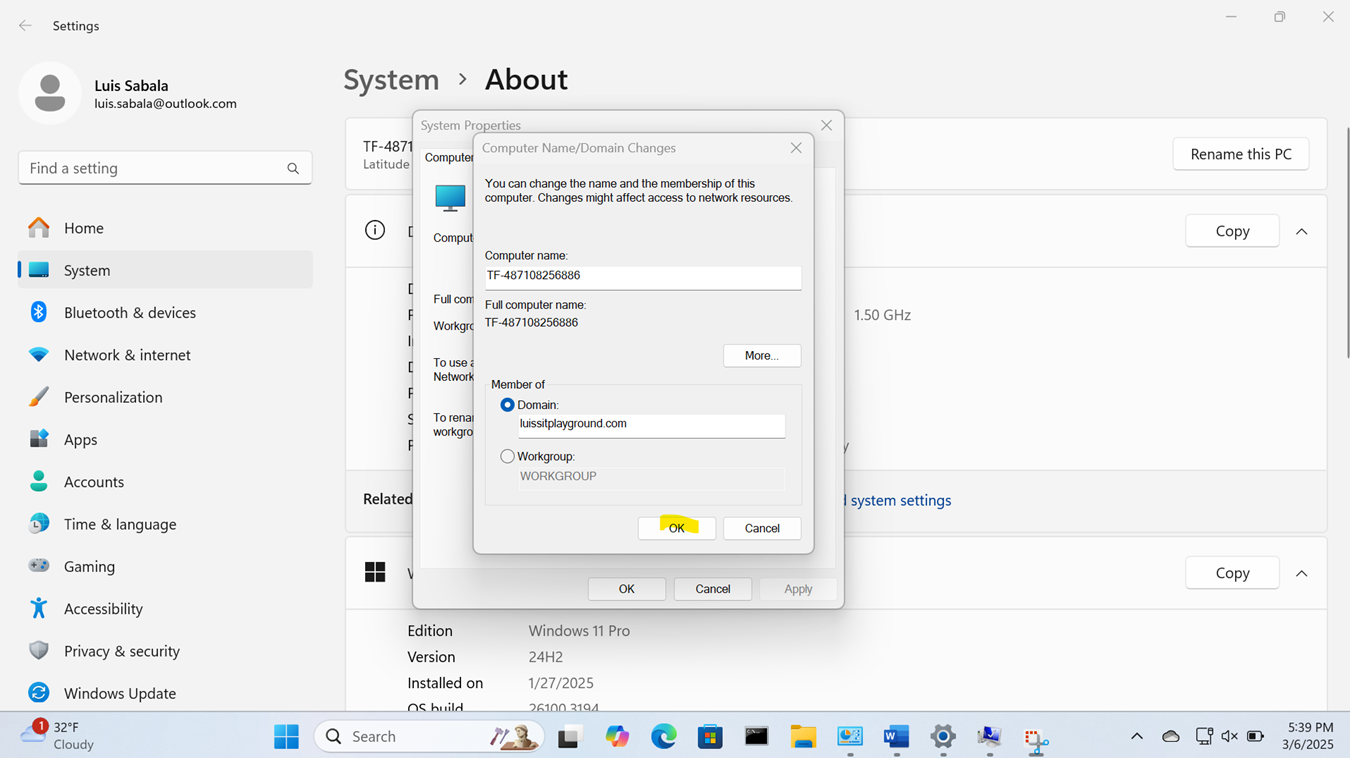
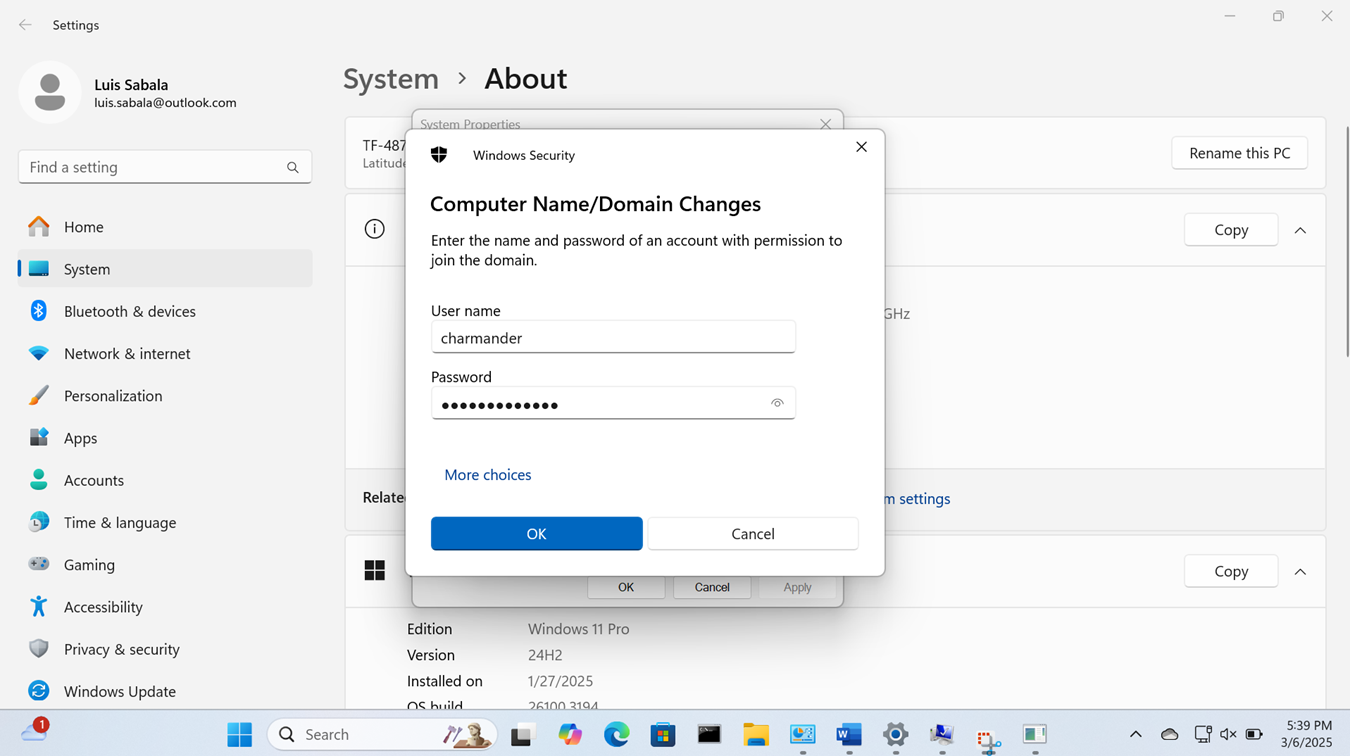
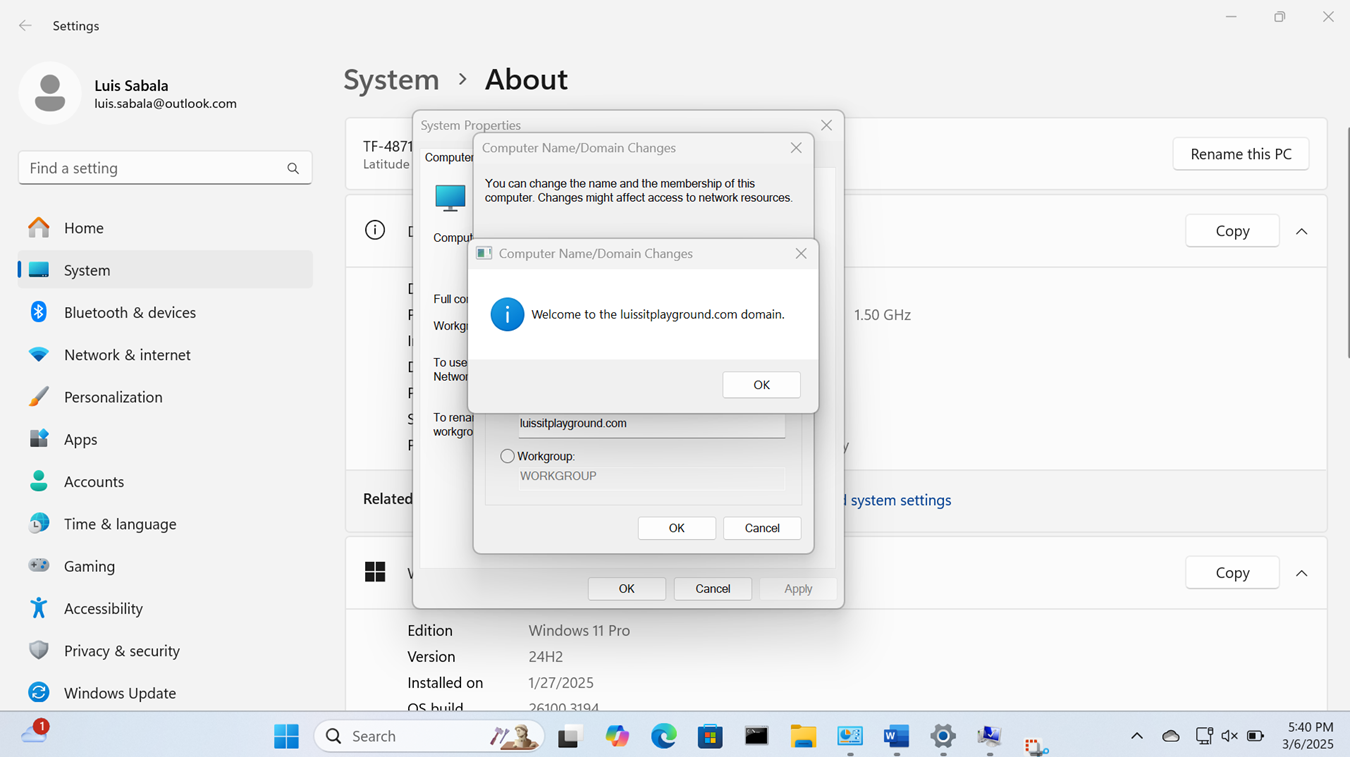
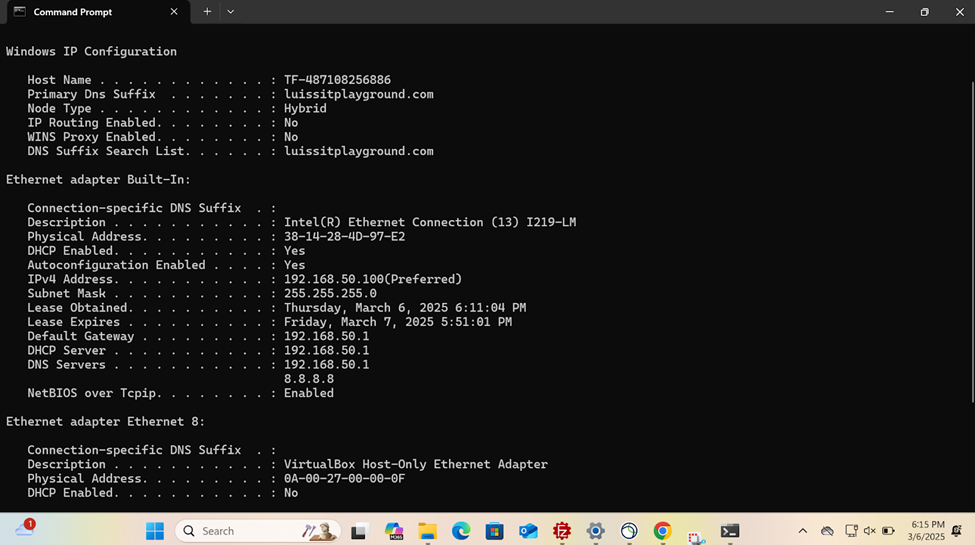
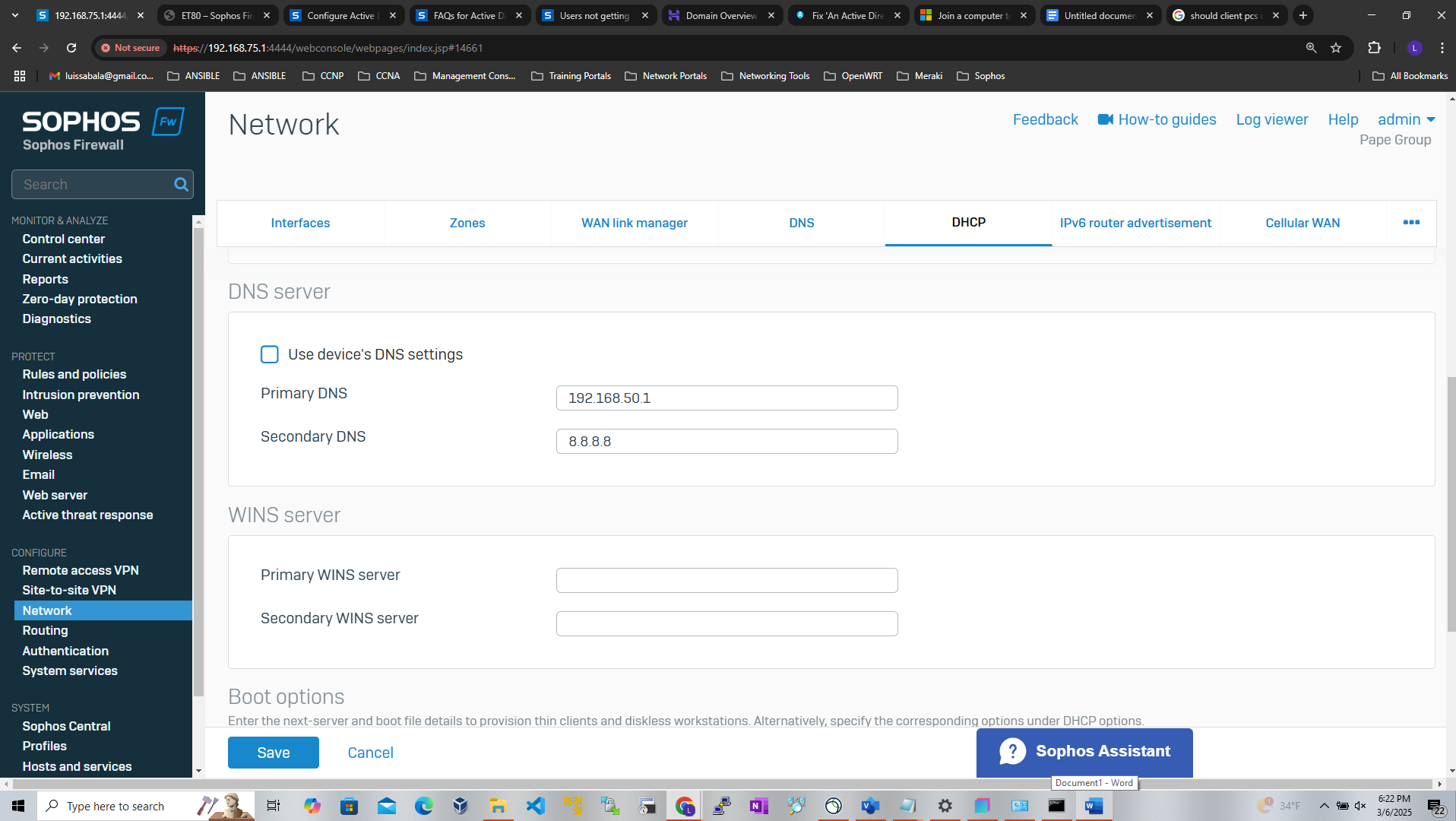
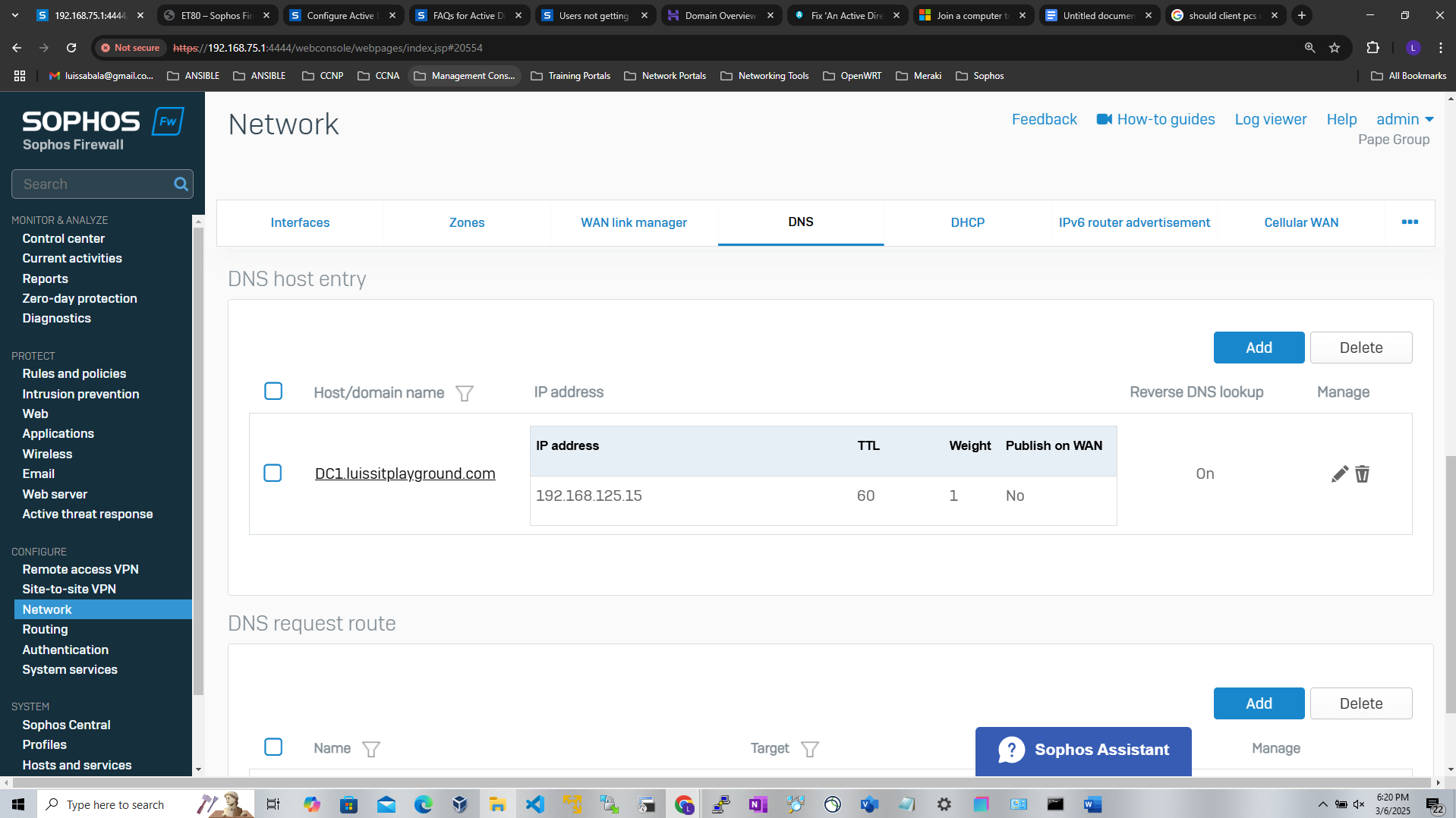
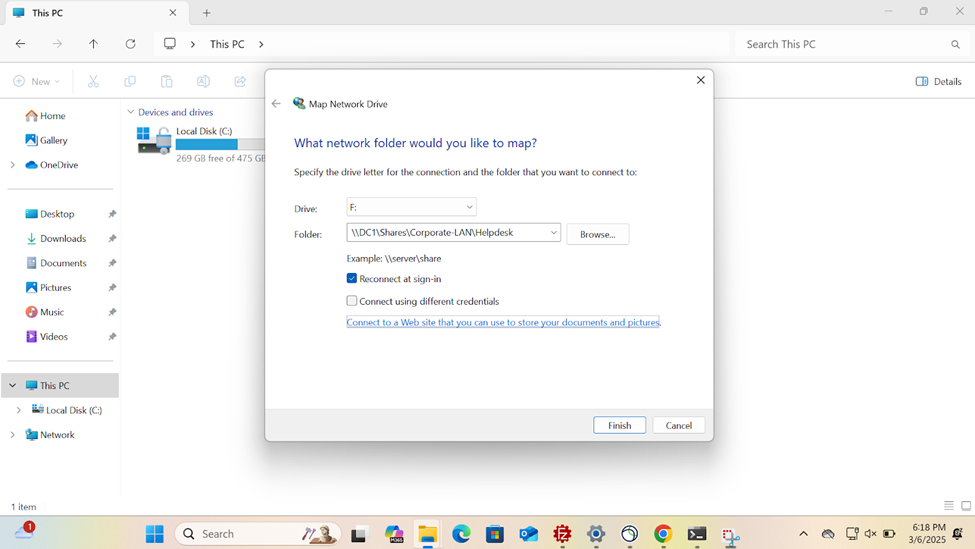
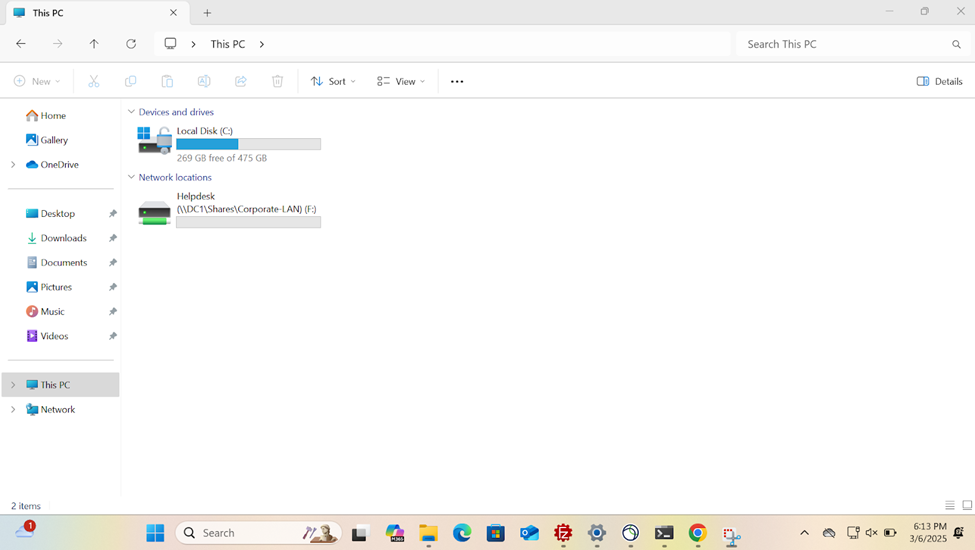
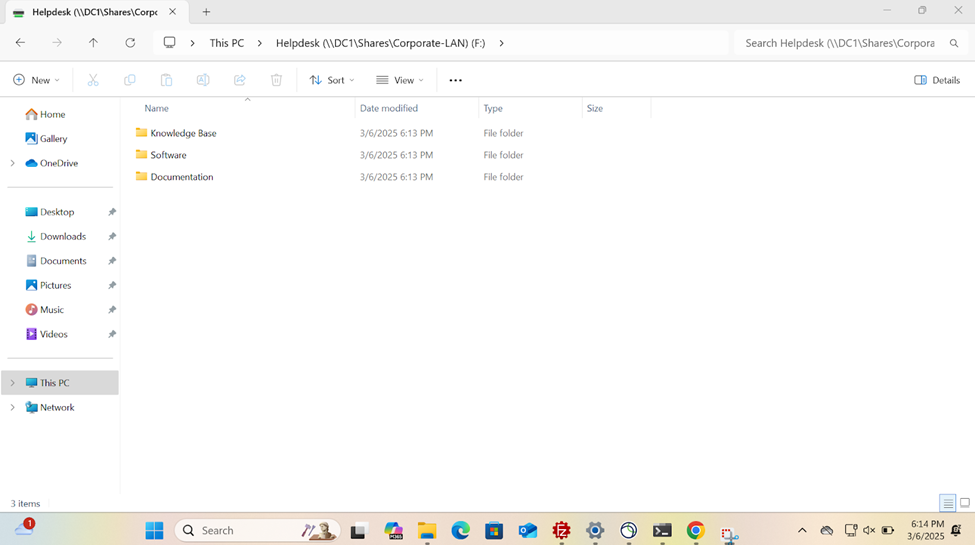
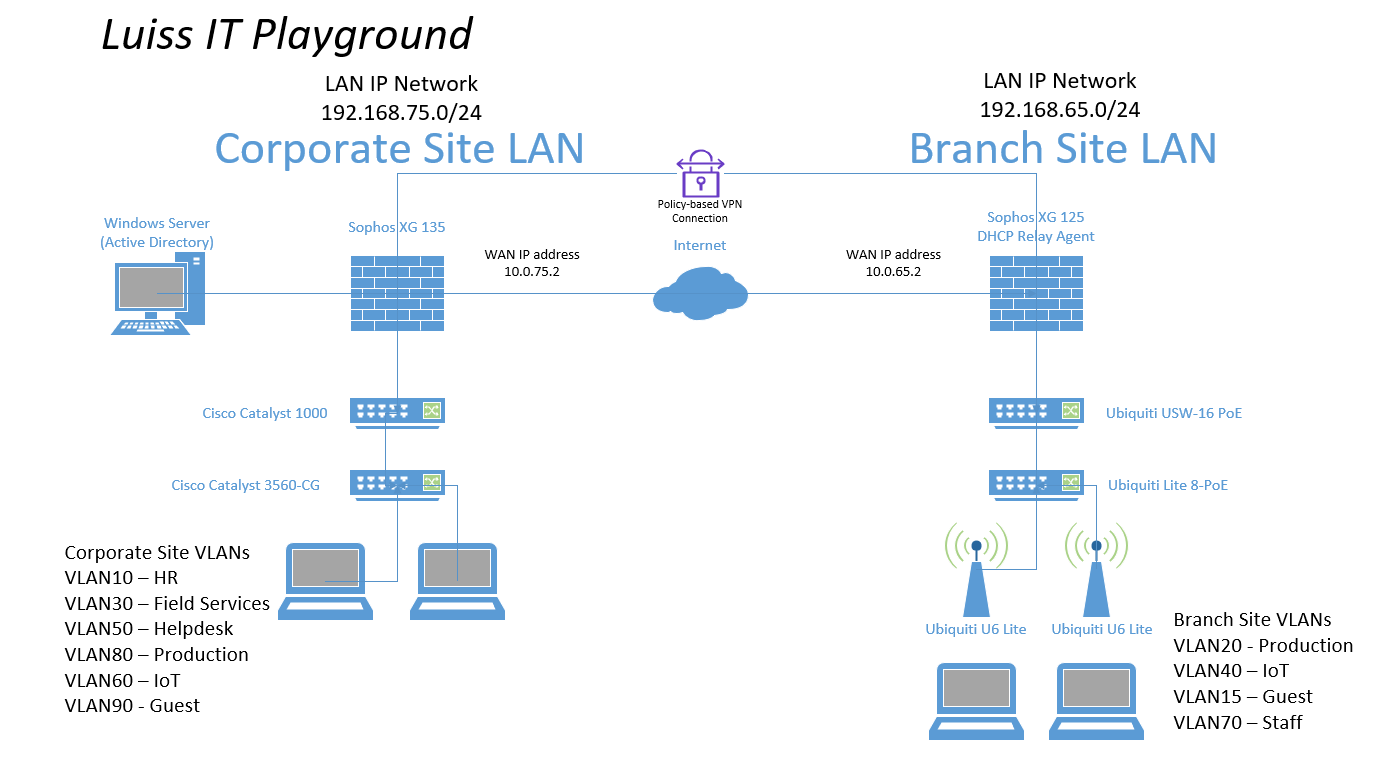
Active Directory Lab Topology
Active Directory for Sophos Authentication
Overview
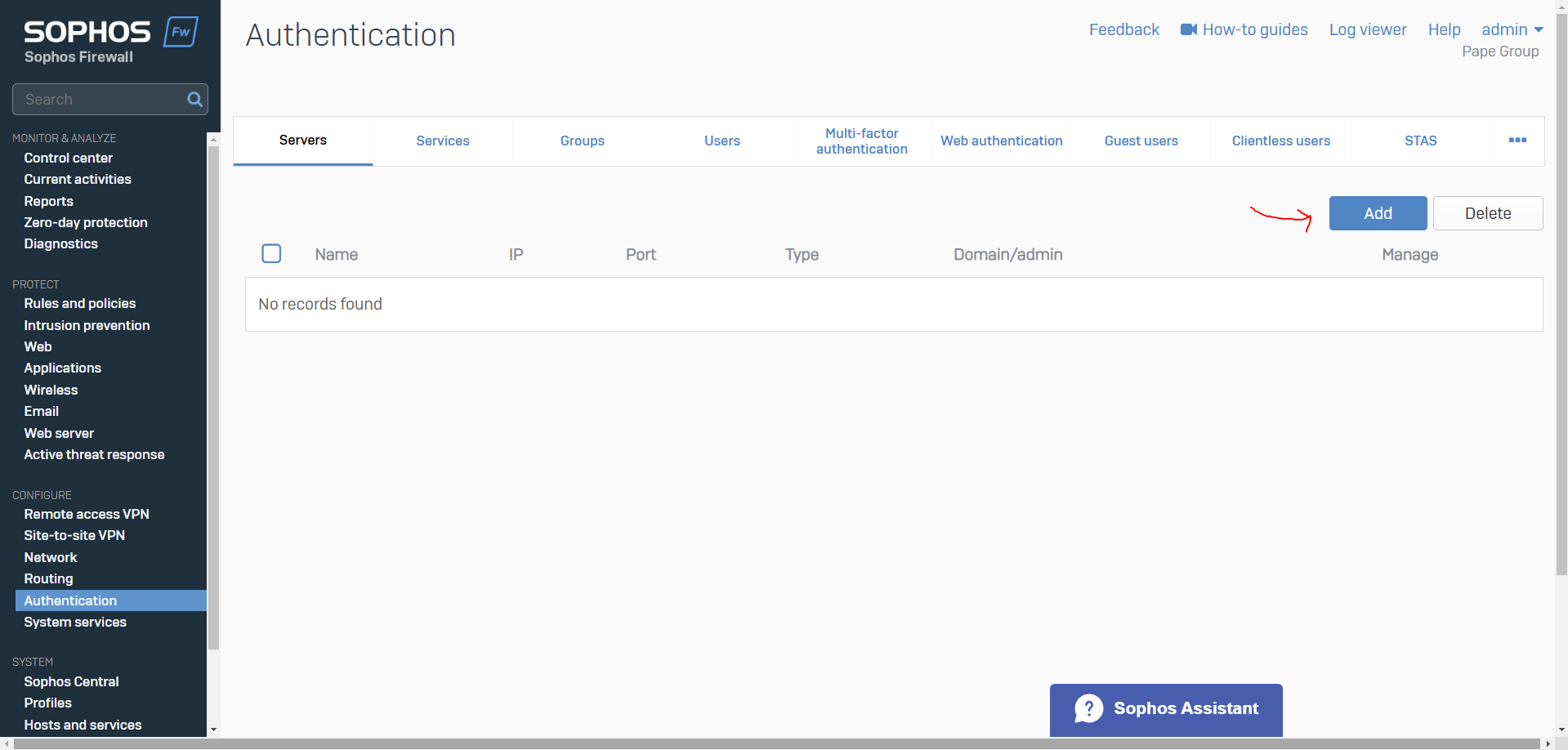
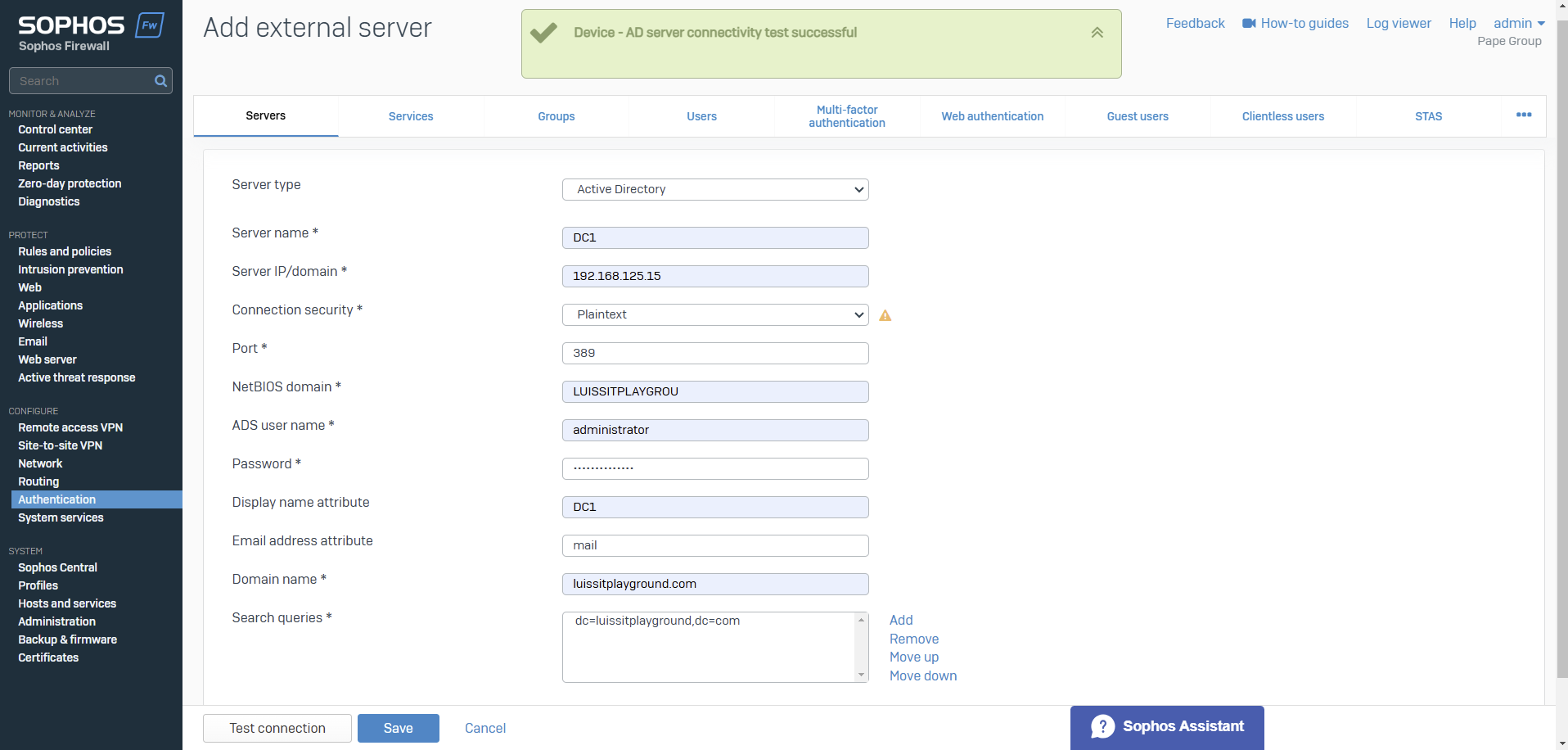
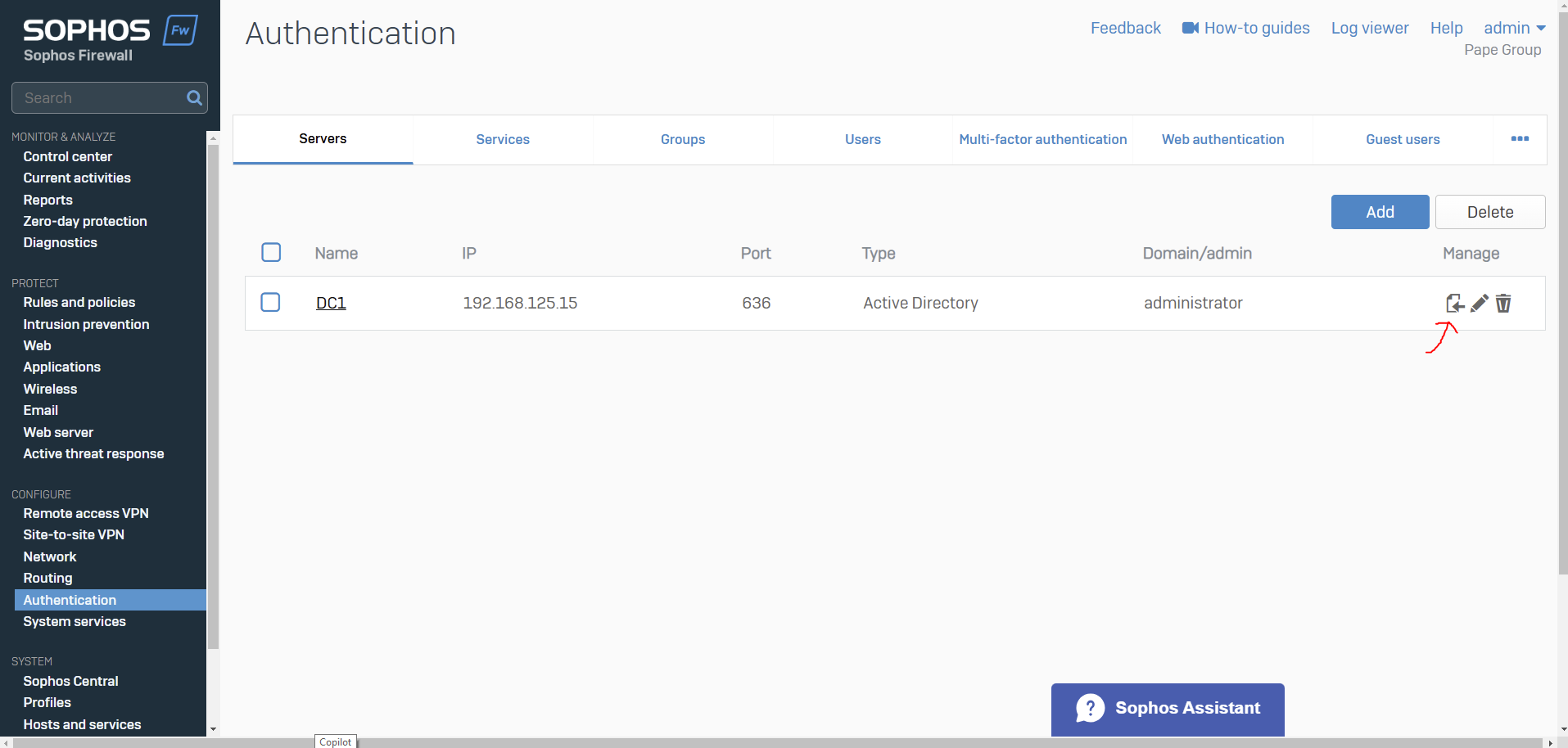
- Resource: Add an Active Directory Server
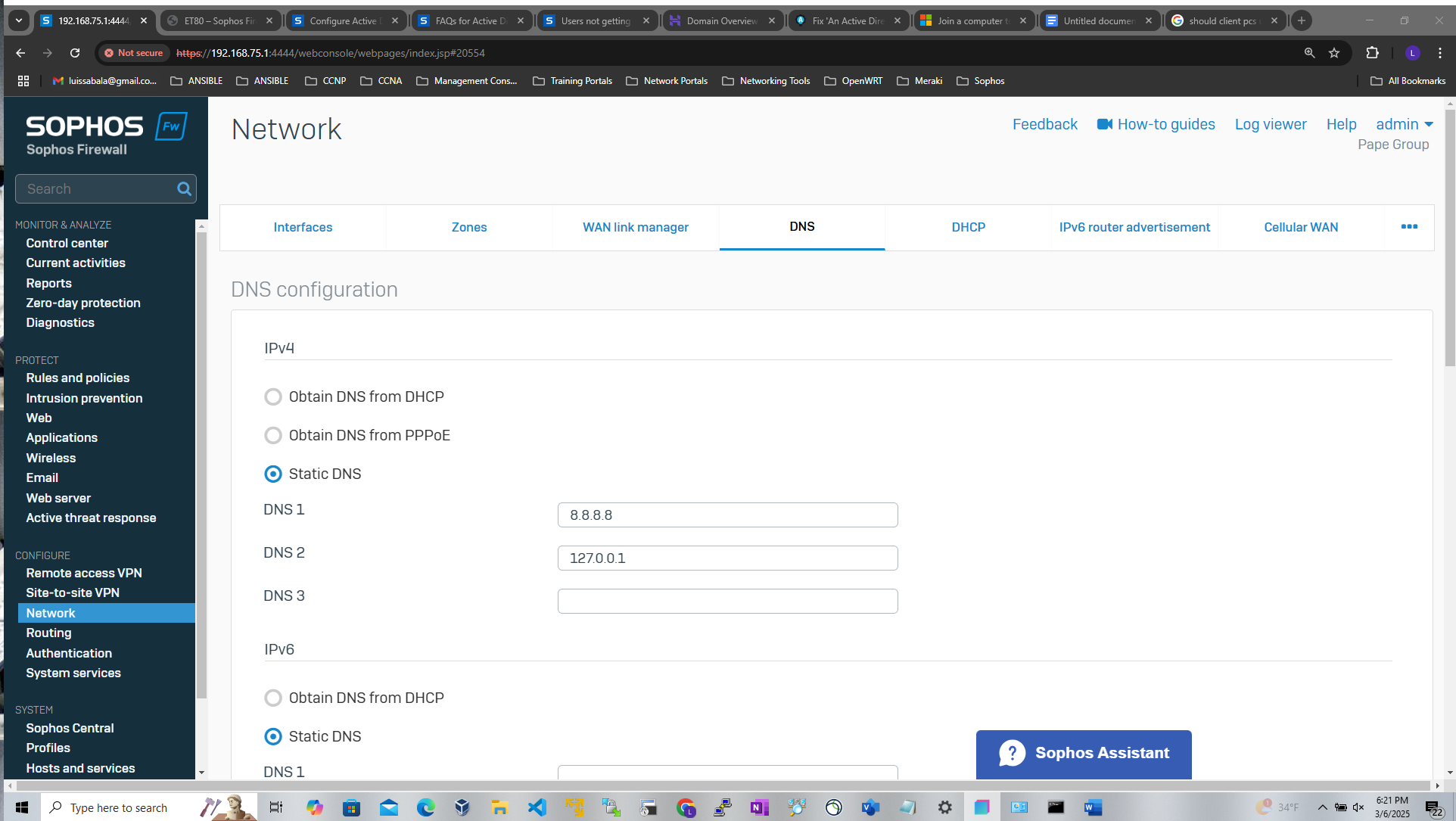
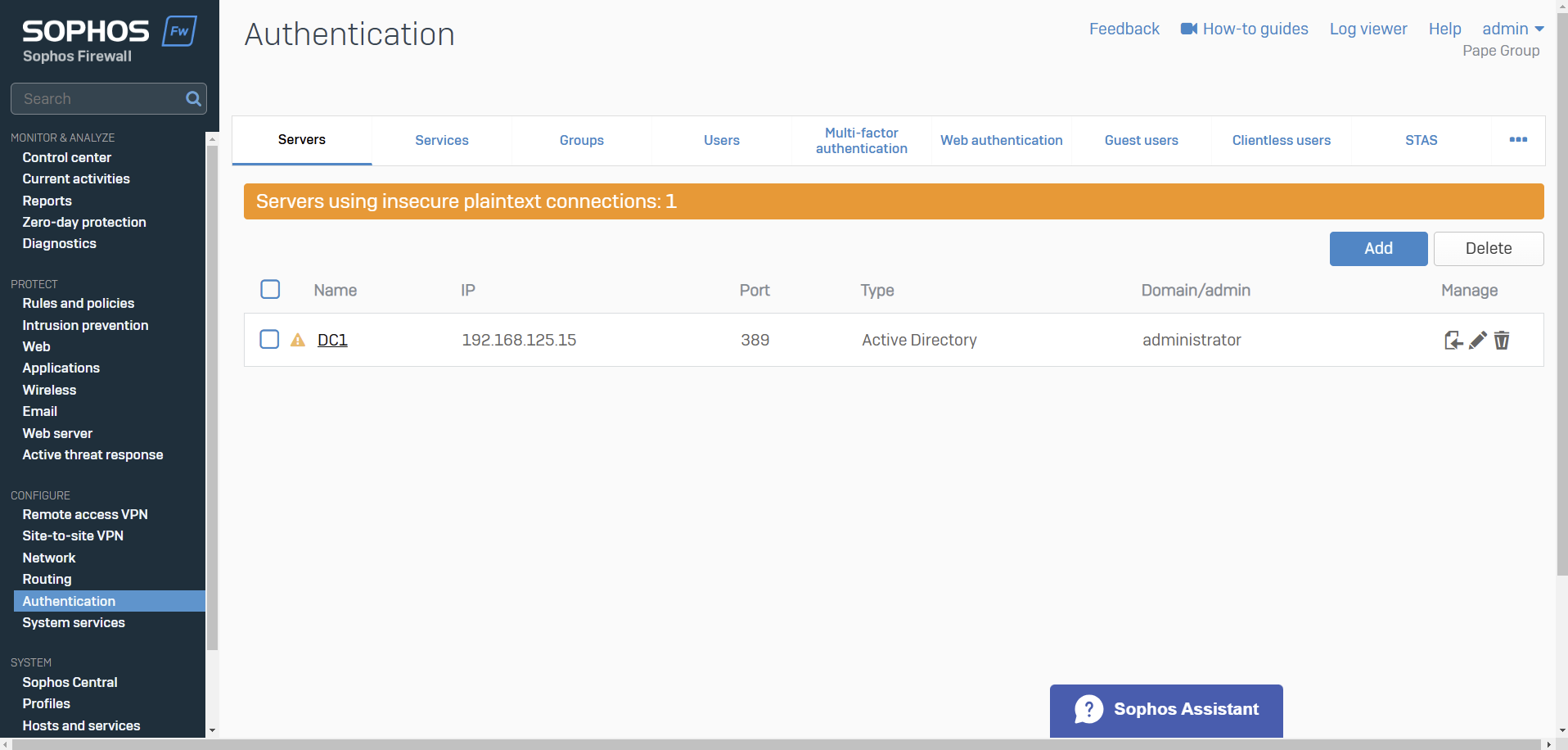
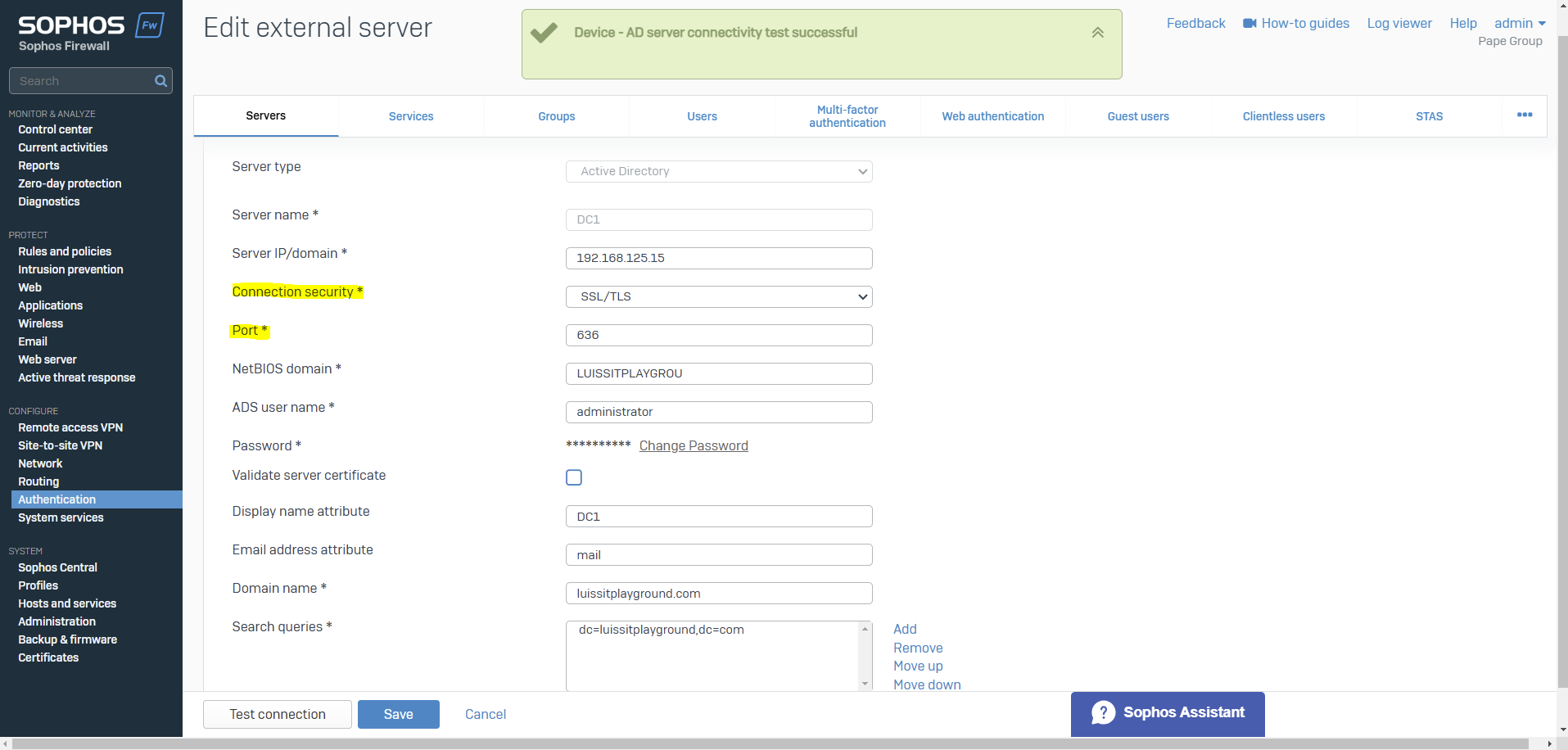
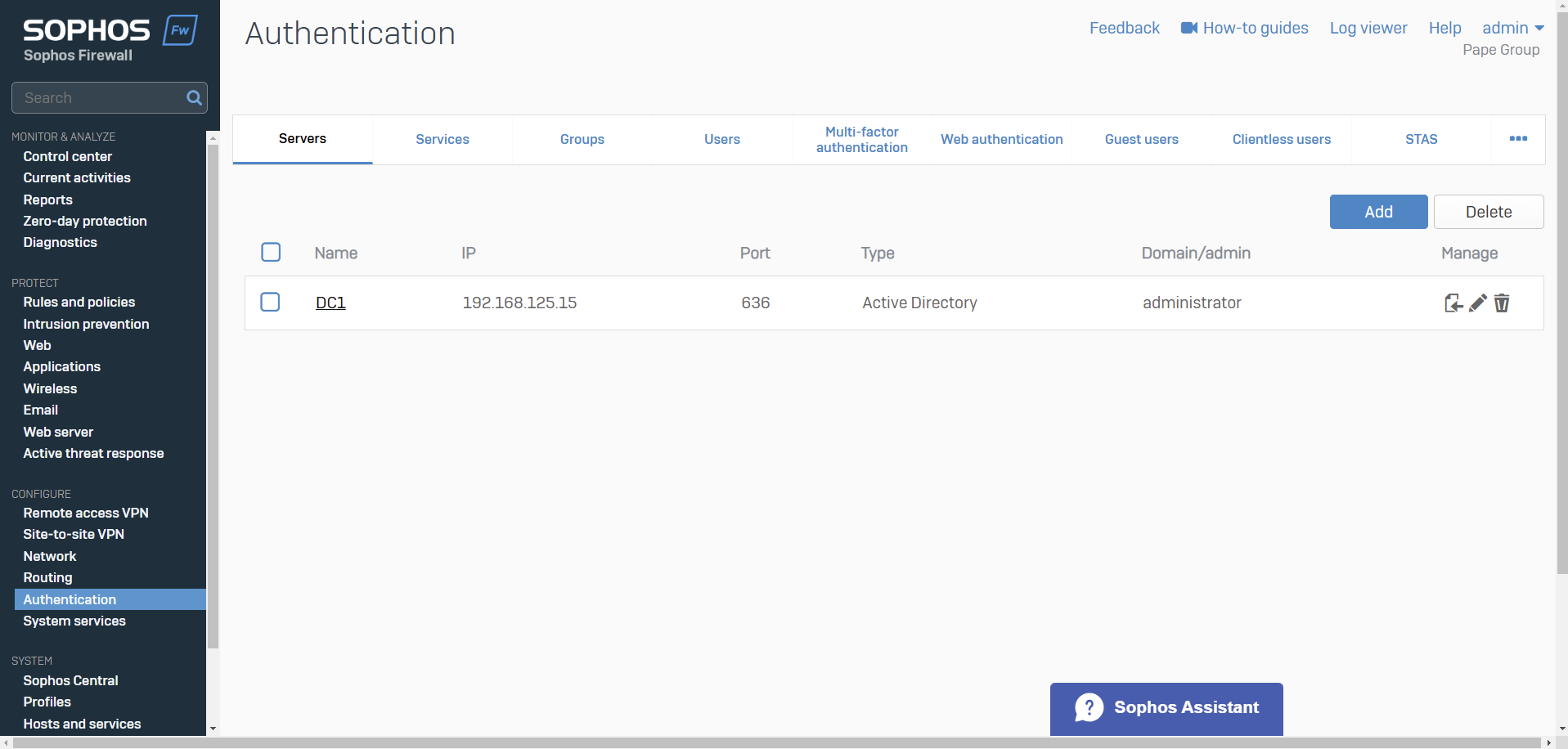
- When it comes to defining an external Active Directory server for Sophos authentication, administrators have the option to select between Plain-text or SSL/TLS connections between the firewall and the AD server
- With Plain-text authentication, the Sophos Firewall uses LDAP (Lightweight Directory Access Protocol, port 389) This means that user credentials (like usernames and passwords) are transmitted without encryption, which can pose a security risk if the network is not properly secured (via a VPN for example)
- With SSL/TLS authentication, the Sophos Firewall uses LDAPS (LDAP over SSL/TLS, port 636) This method encrypts the communication between the Sophos Firewall and the AD server using SSL/TLS, ensuring that user credentials and other sensitive data are protected from interception
- In the next section, I will demonstrate changing the connection method to SSL/TLS in which the 'Active Directory Certificate Services' role will need to be installed on the Windows server
Protocol Overview
- LDAP
- LDAP (Lightweight Directory Access Protocol) is a protocol used for accessing and managing directory services, like those provided by Active Directory (AD)
- LDAP uses port 389 by default for unencrypted traffic
- In short, LDAP enables systems (like a firewall, server, or application) to authenticate, search for, and manage directory information in a network
- LDAPS
- LDAPS (LDAP over SSL/TLS) is a secure version of LDAP. It uses SSL or TLS to encrypt the communication between the LDAP client (like a server, firewall, application, or service) and the LDAP server (such as Active Directory or OpenLDAP)
- LDAPS uses port 636 by default for encrypted traffic
- Many organizations are required to follow security standards and regulations (such as GDPR, HIPAA, or PCI-DSS) that mandate encrypting sensitive data in transit. LDAPS ensures compliance with these standards by securing the LDAP communication channel
Secure Active Directory for Sophos Authentication
Overview
- Resource: How to Integrate AD with SSL/TLS connection security
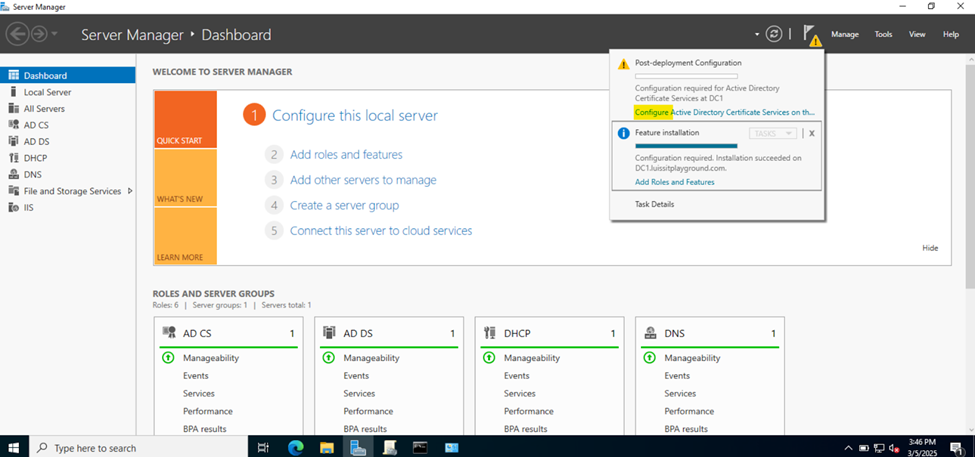
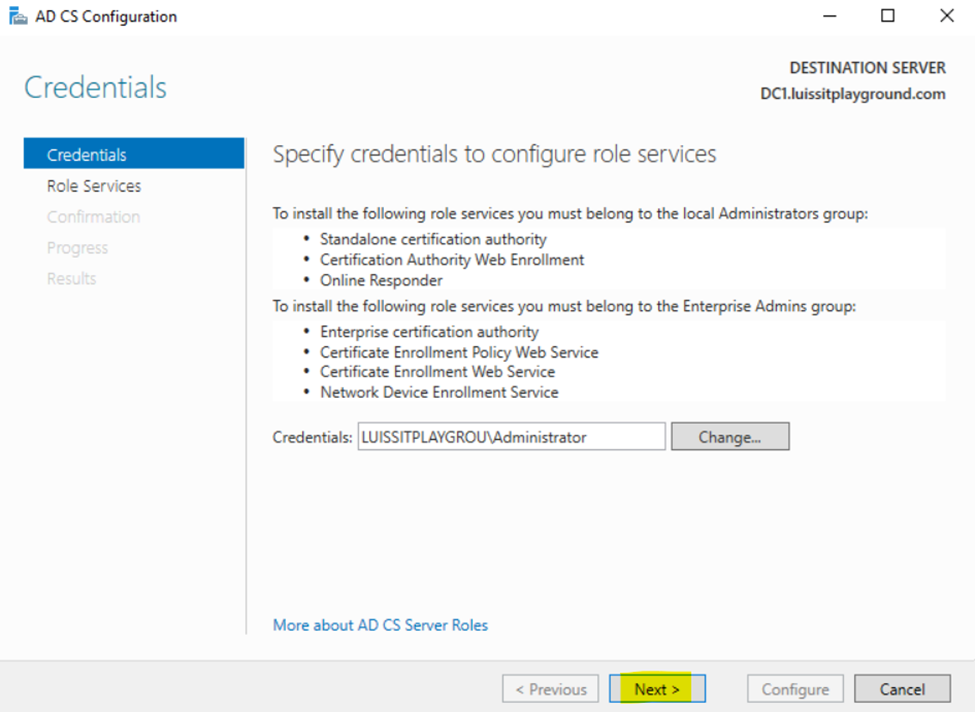
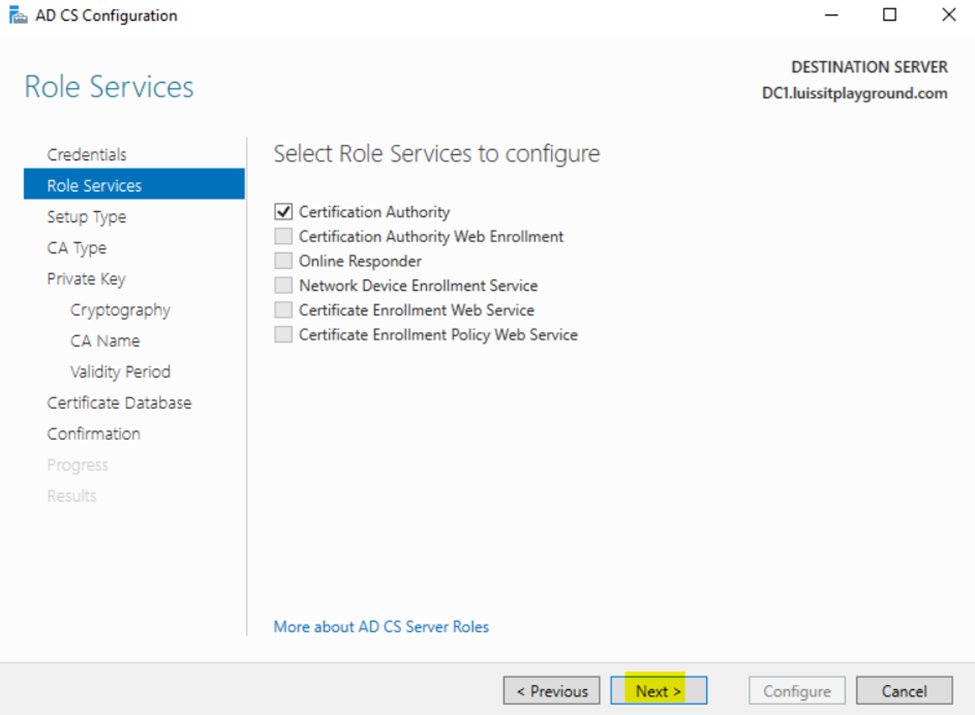
- In this demonstration, I will walk-through the process of installing the 'Active Directory Certificate Services' role on the Windows server and configure the role service
- Post configuring the Active Directory Certificate Services role, I will re-establish the Active Directory connection on the Sophos Firewall in the Corporate site LAN to use SSL/TLS for communications between the firewall and AD server
Installing Active Directory Certificate Services
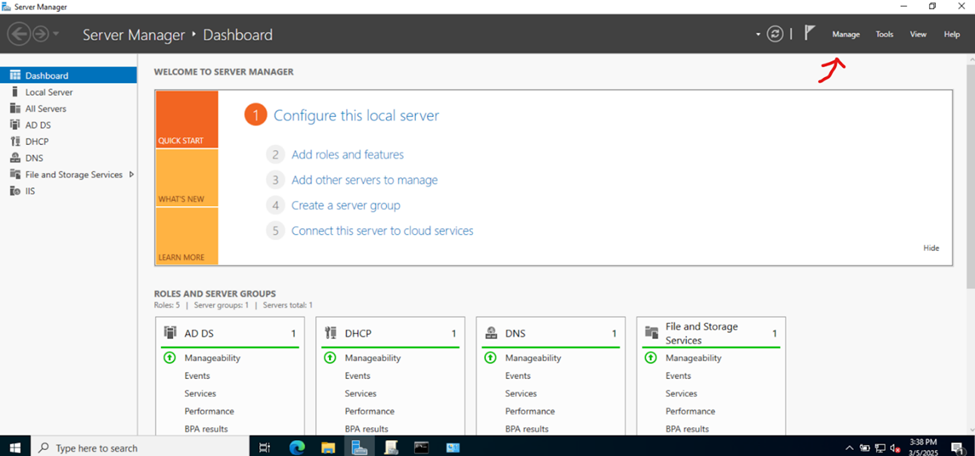
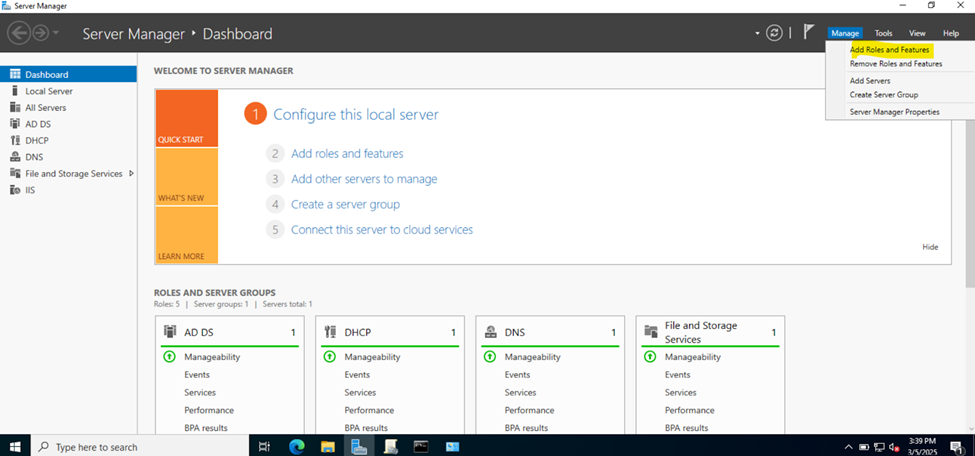
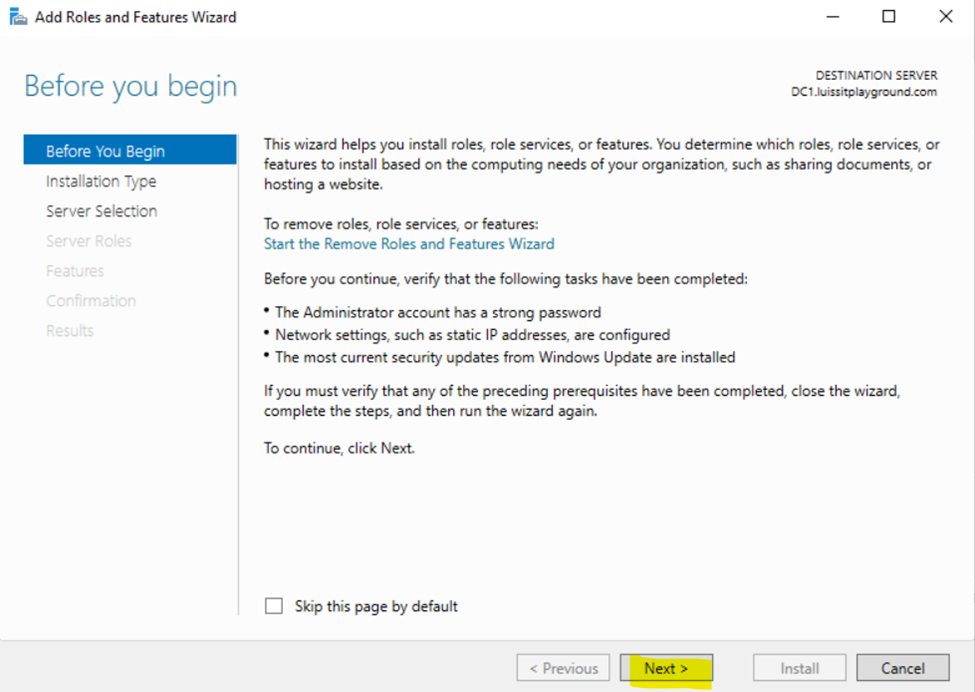
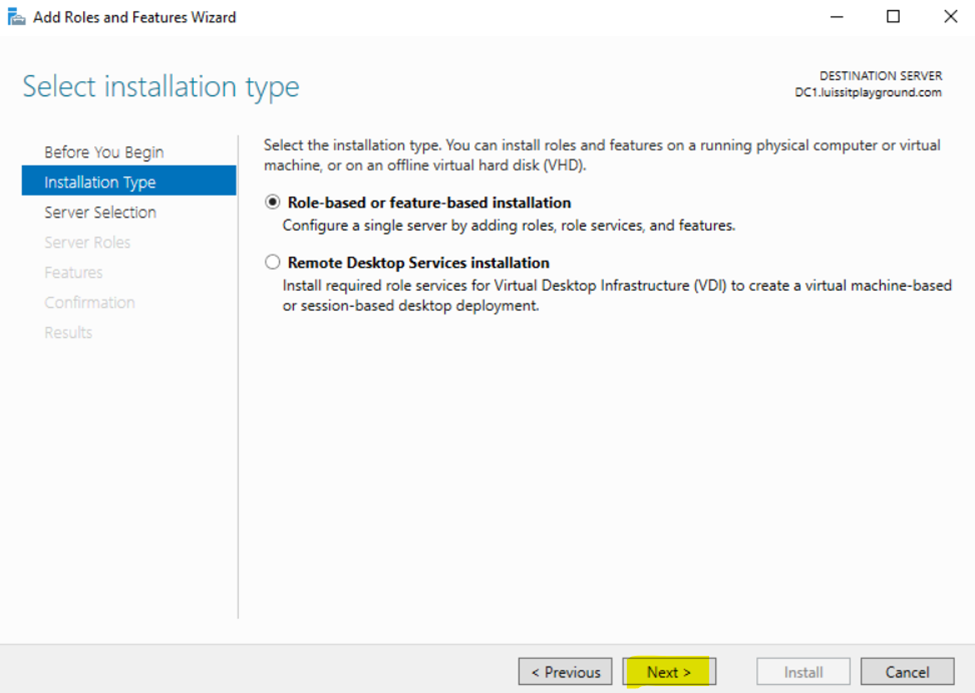
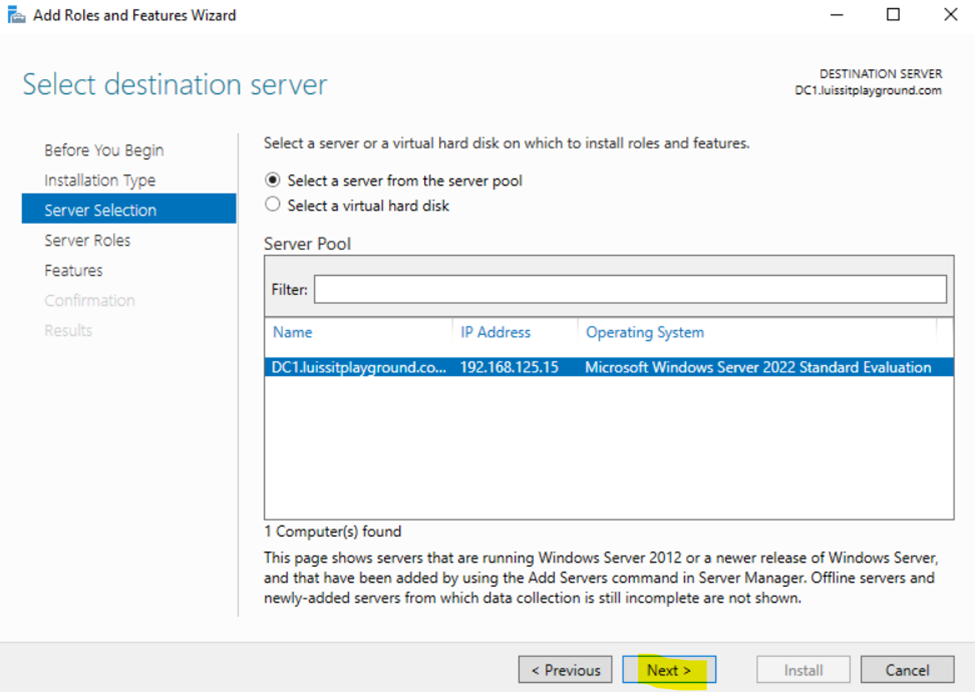
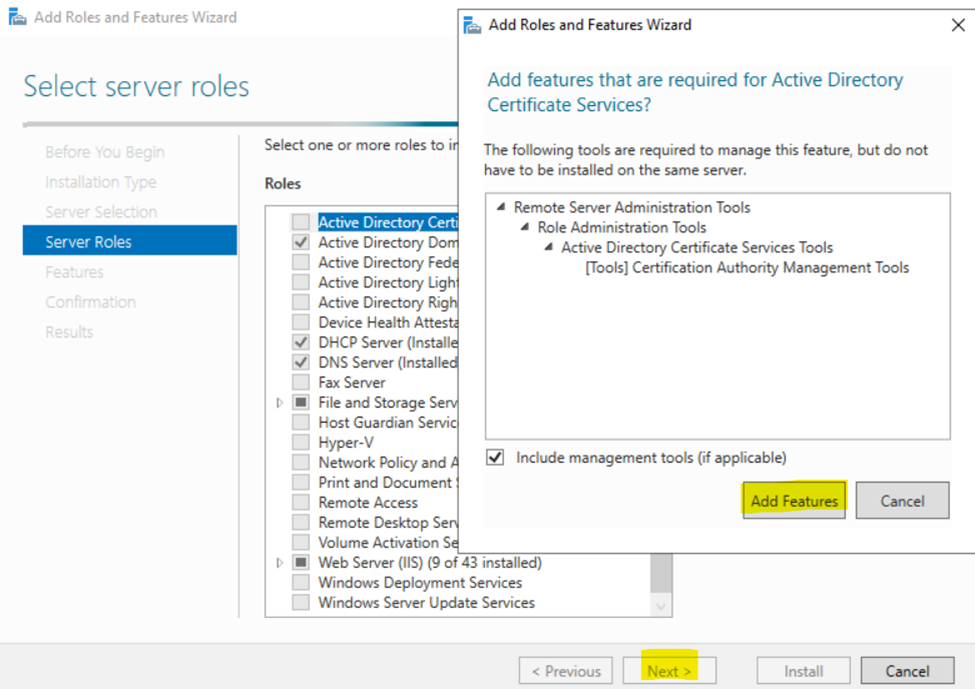
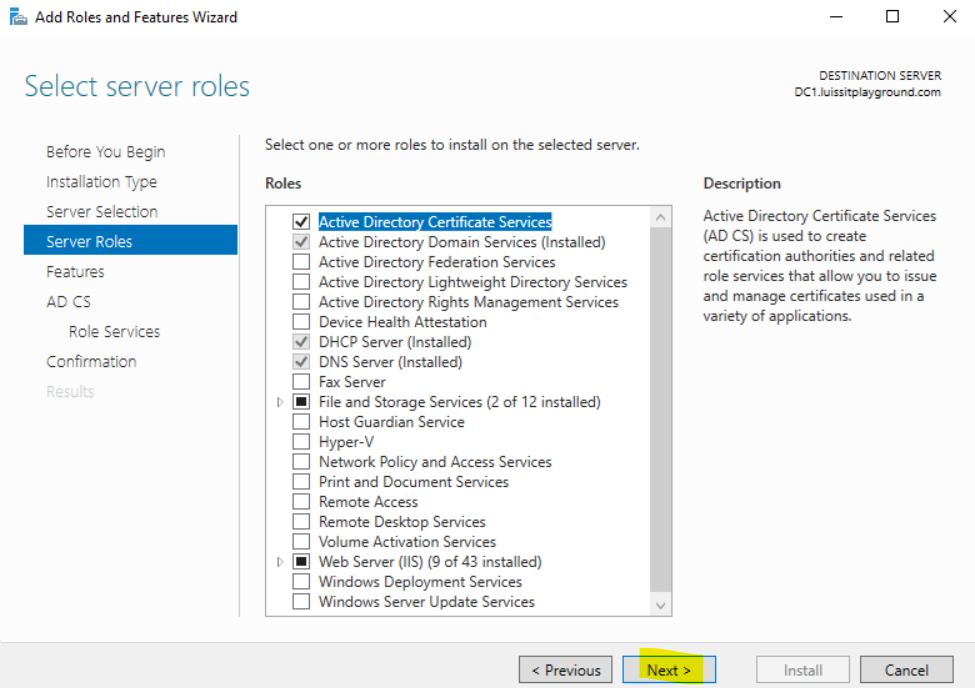
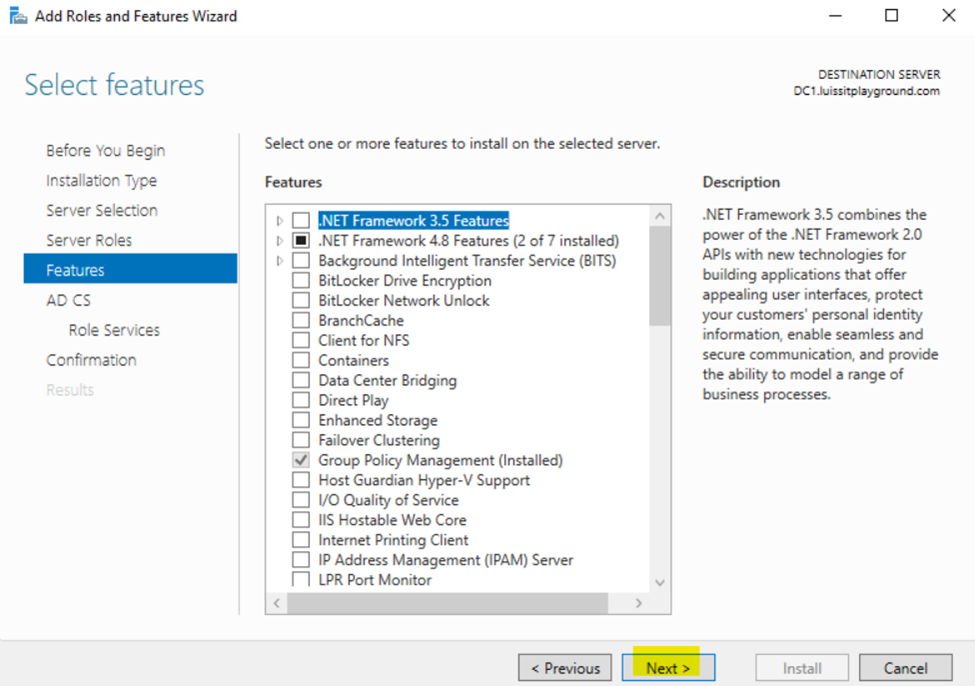
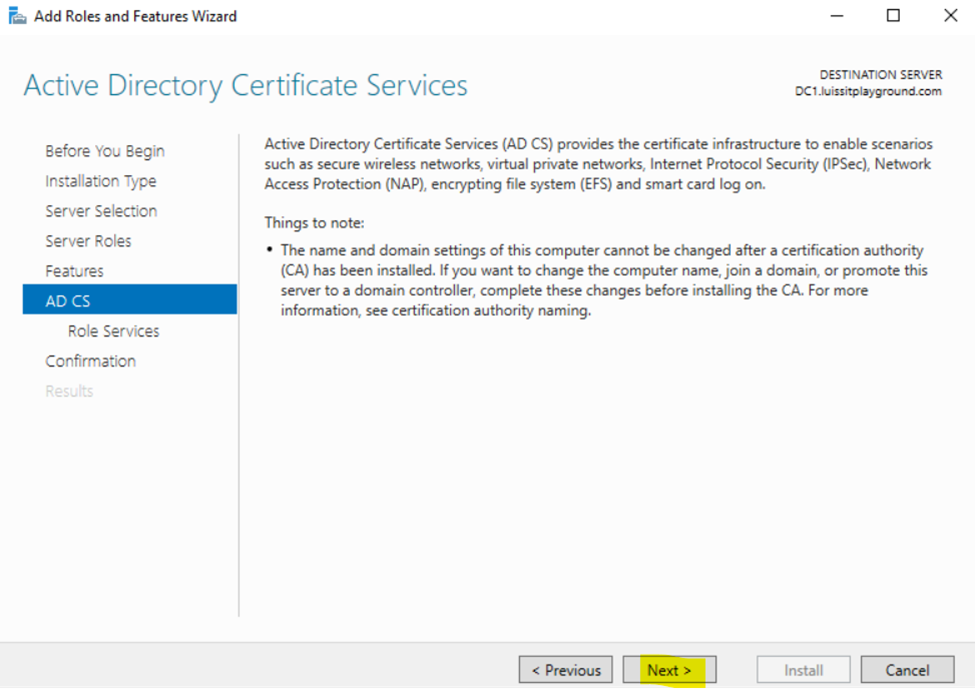
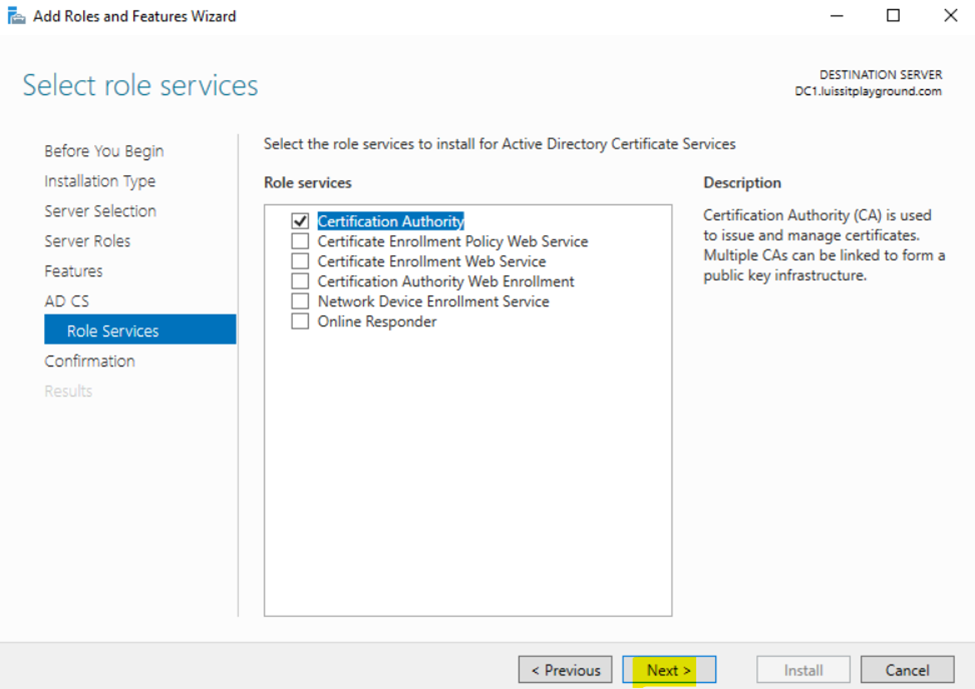
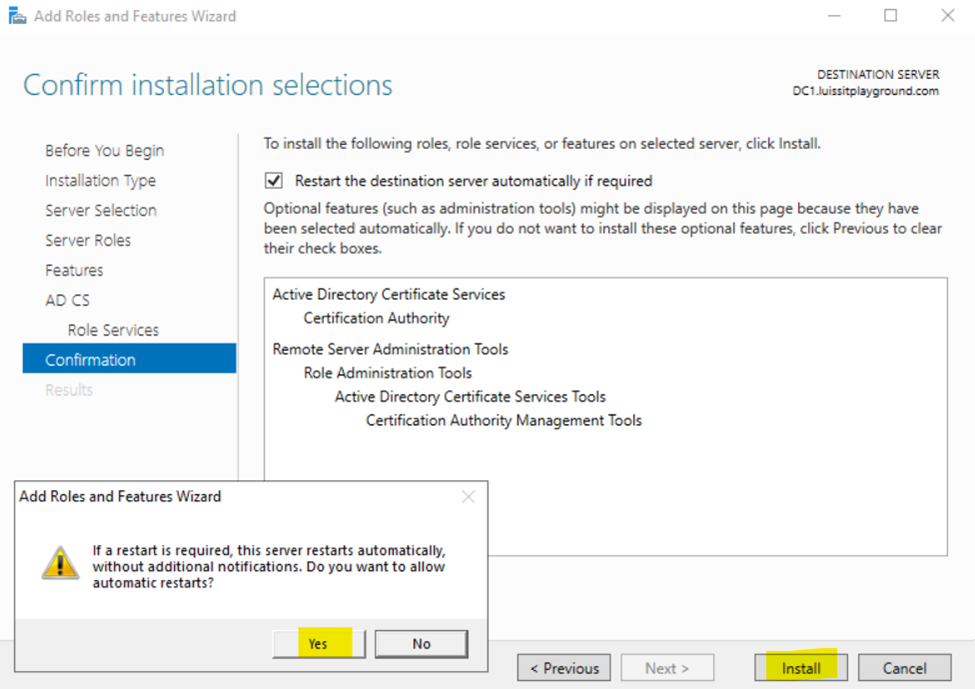
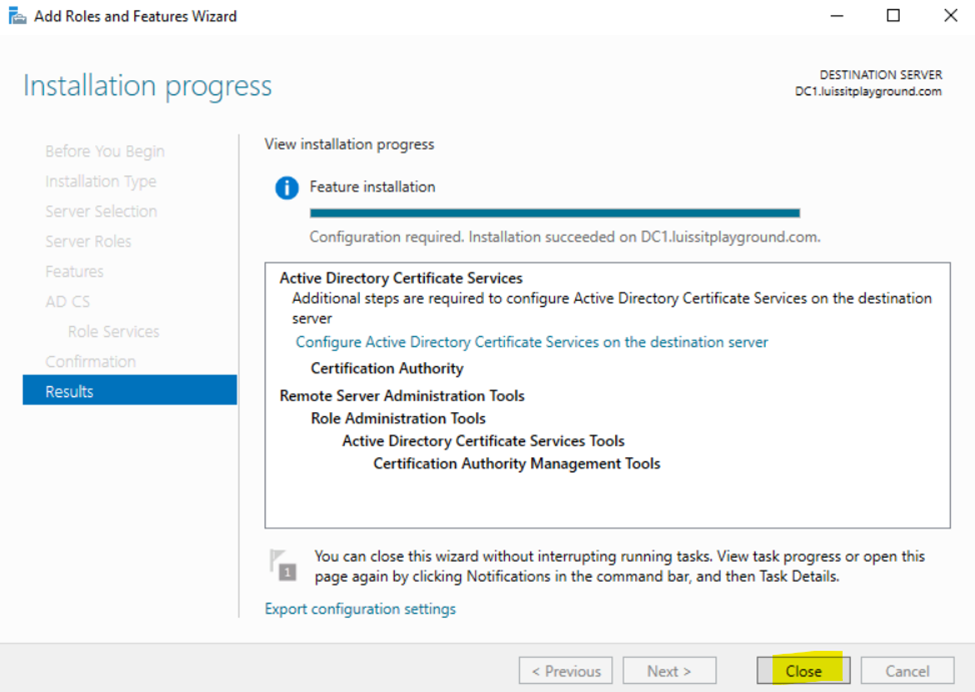
Configuring Active Directory Certificate Services
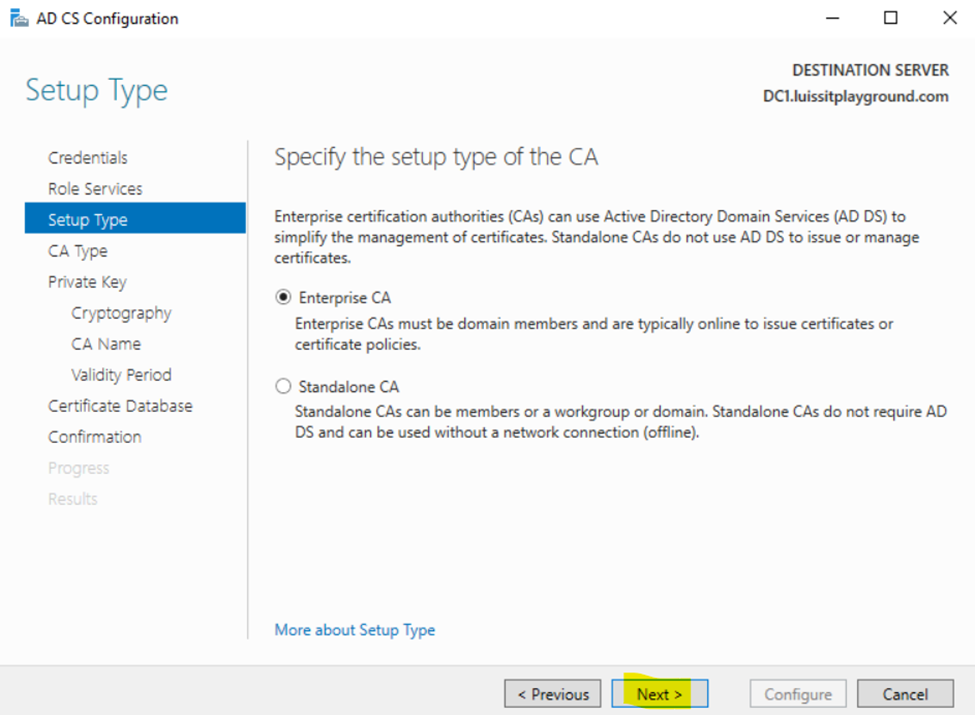
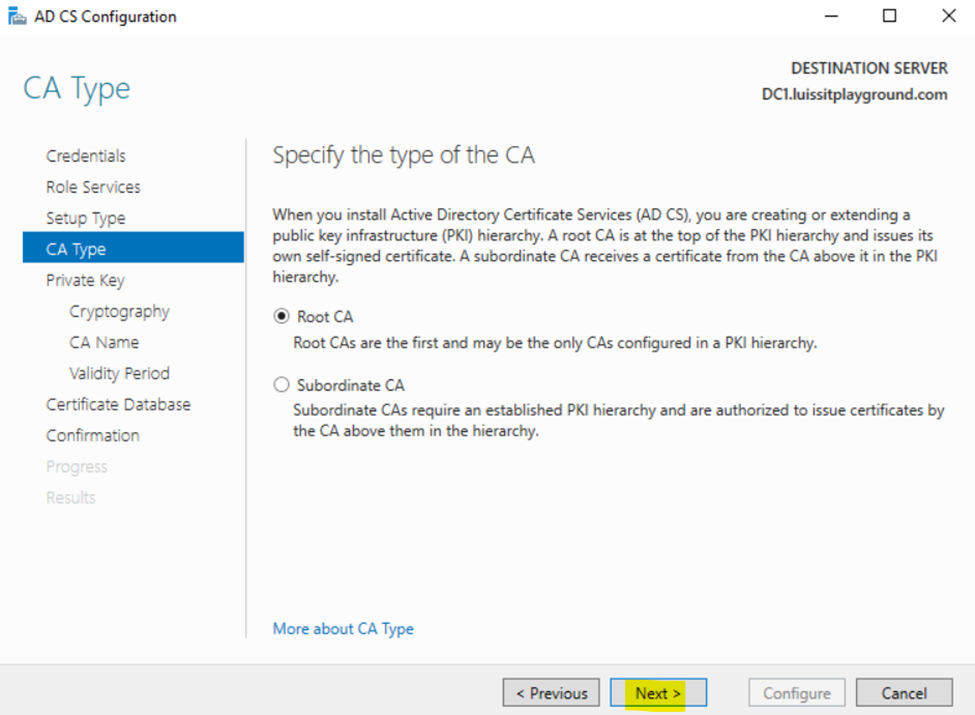
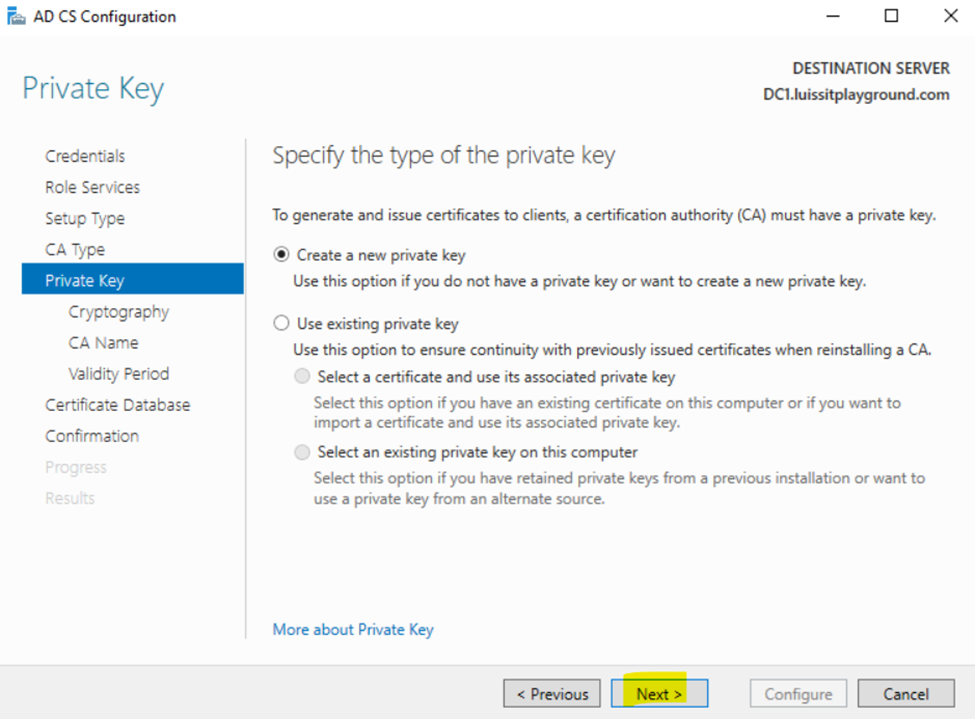
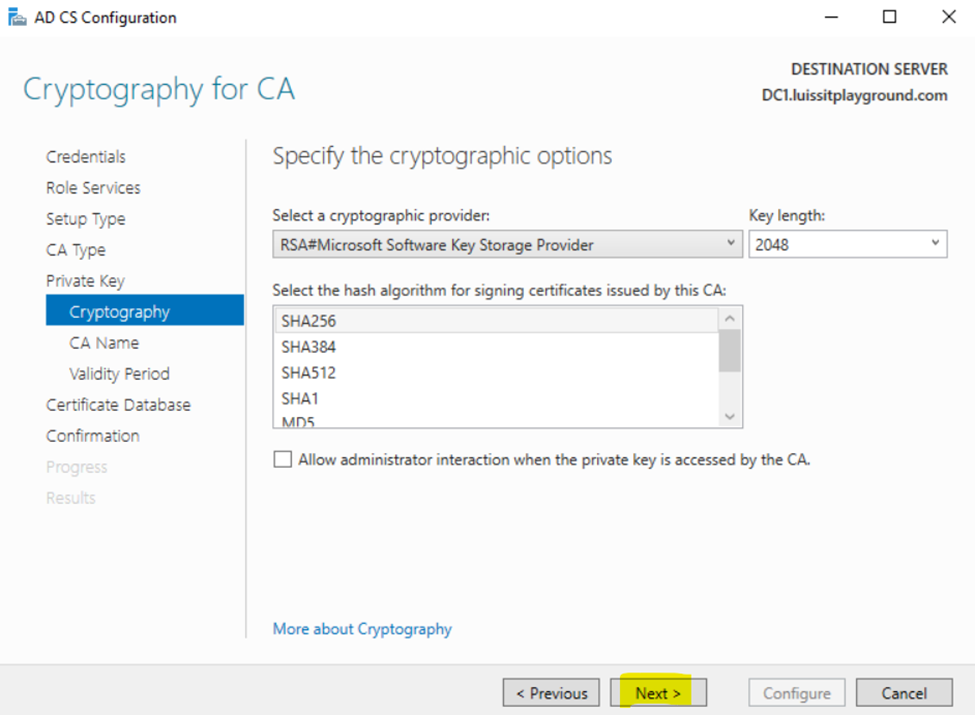
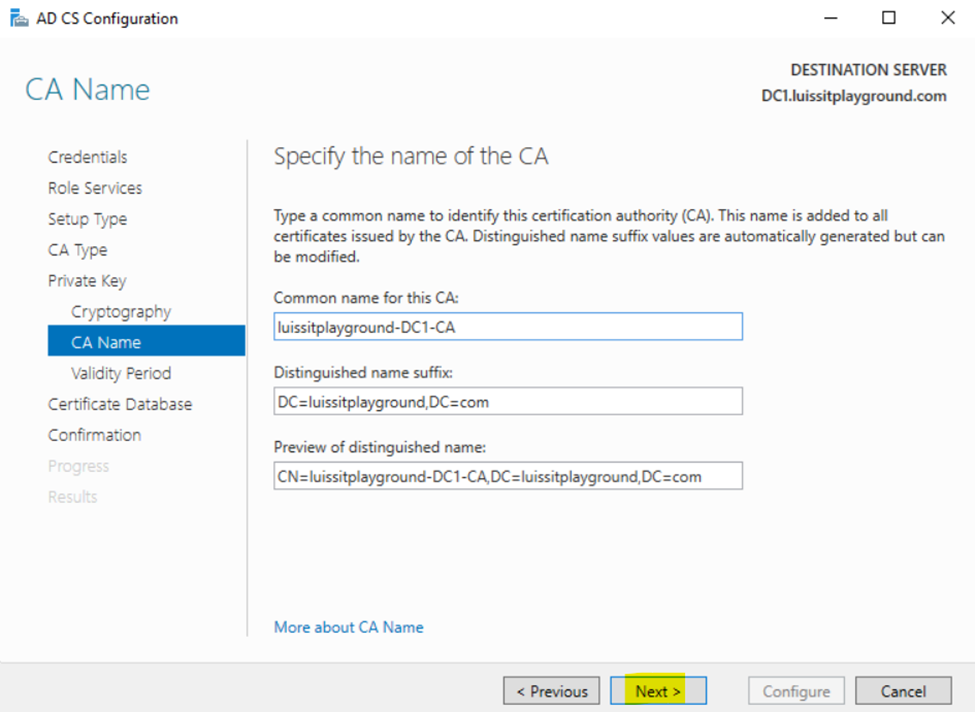
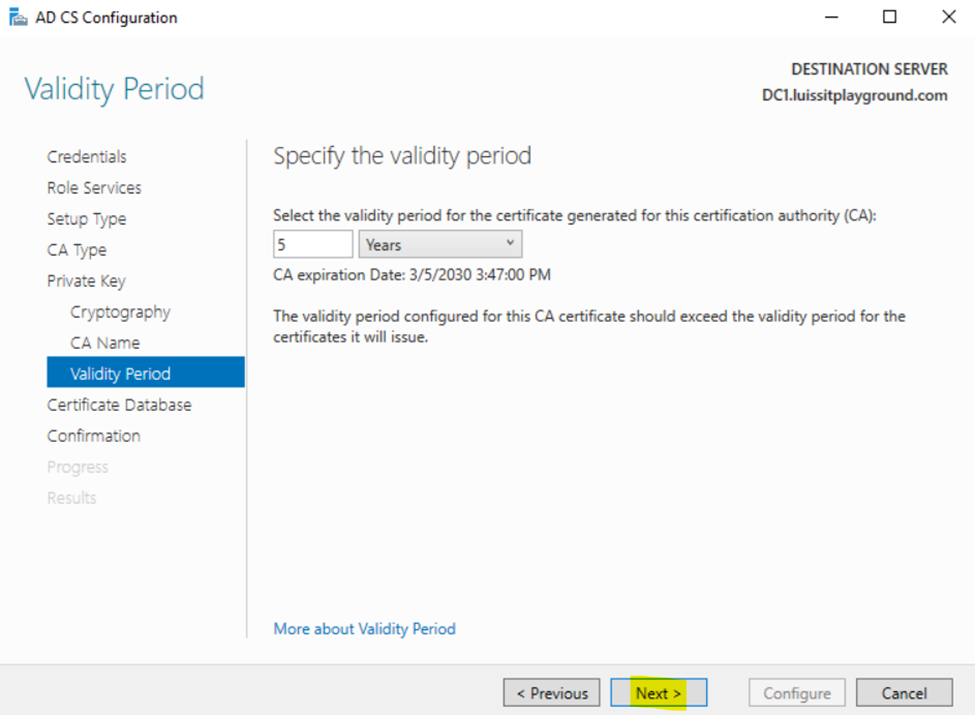
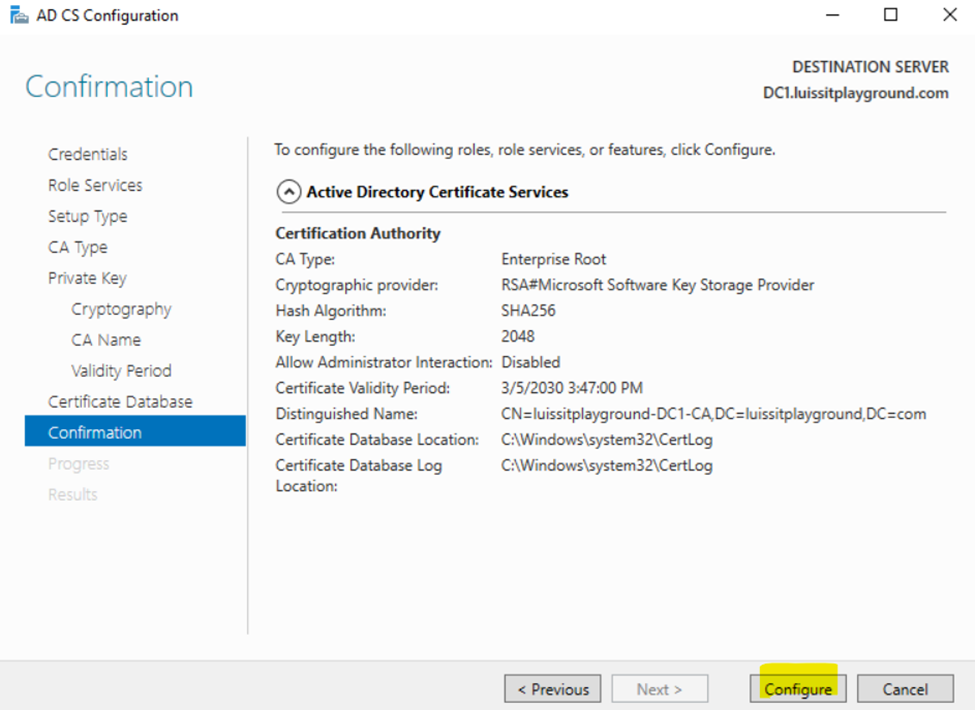
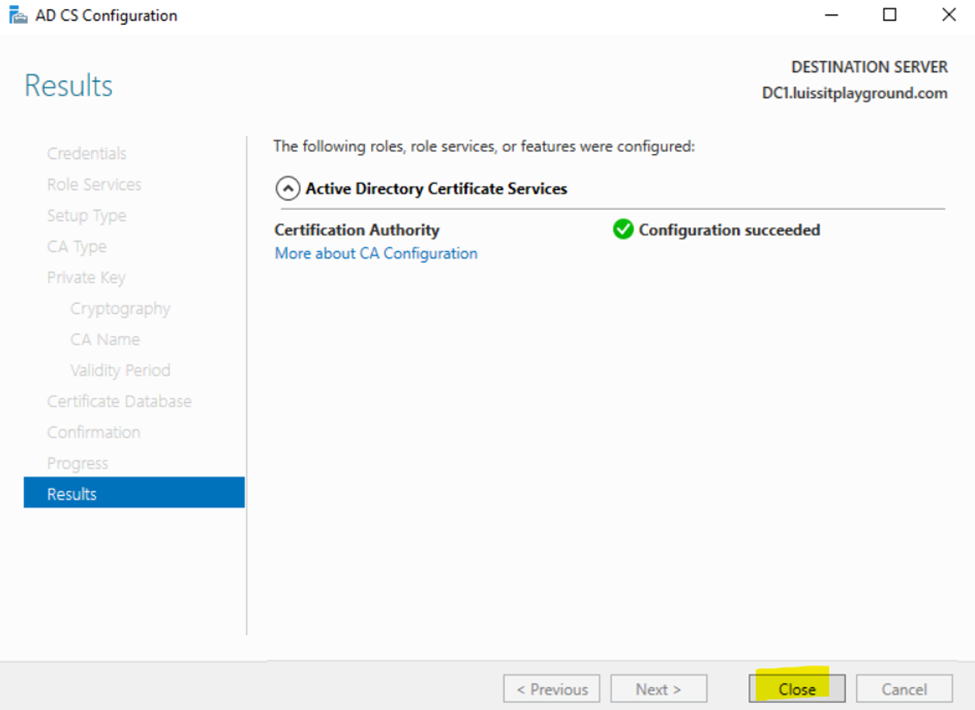
Active Directory SSL/TLS Connection
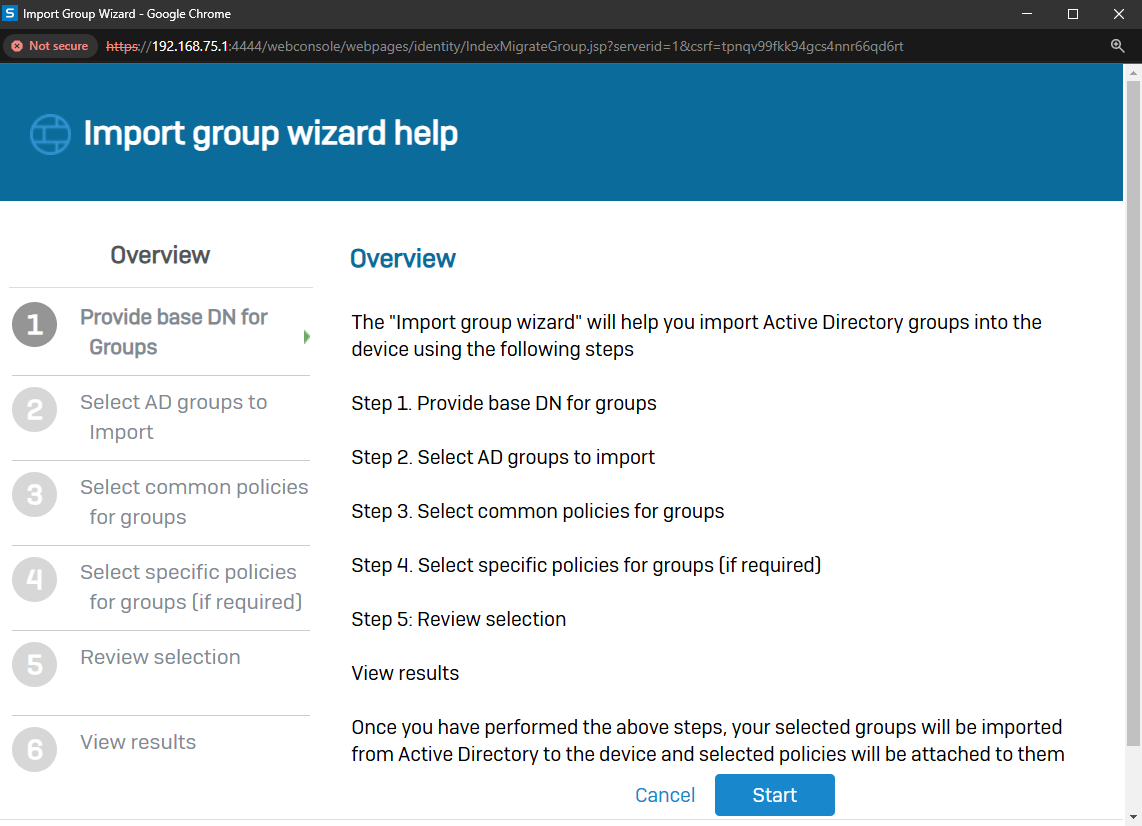
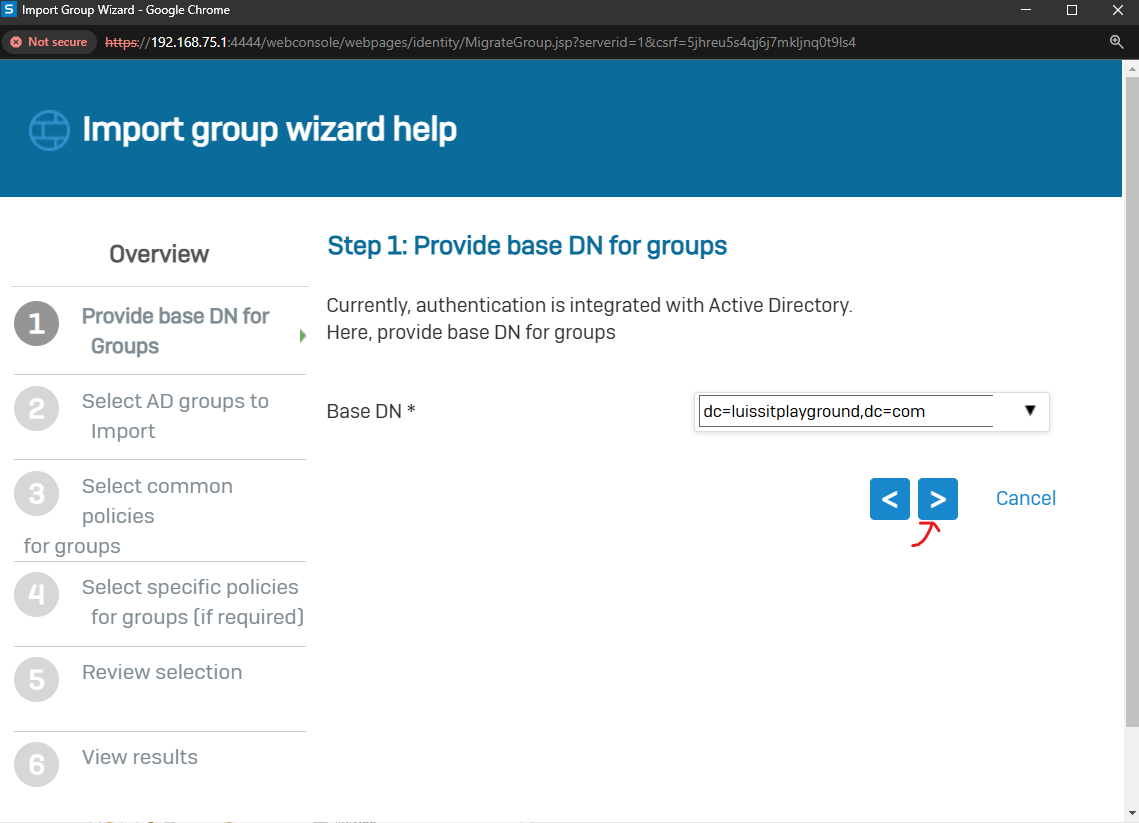
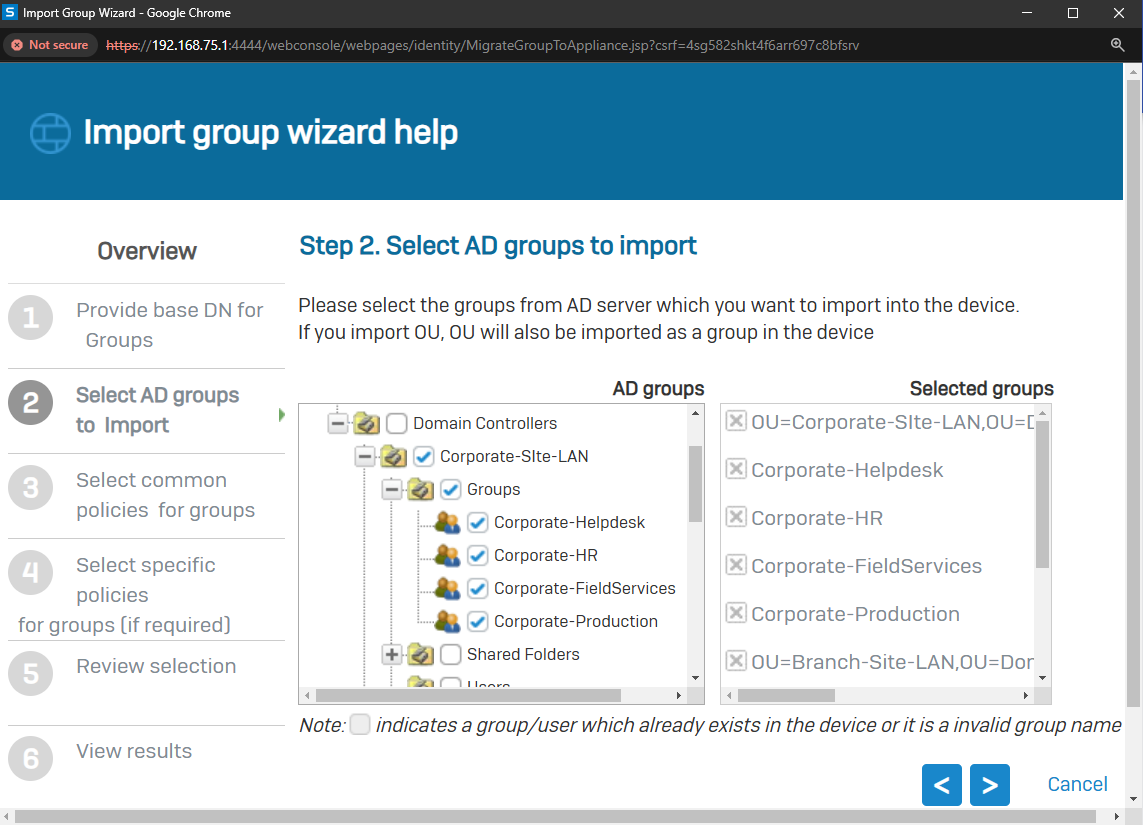
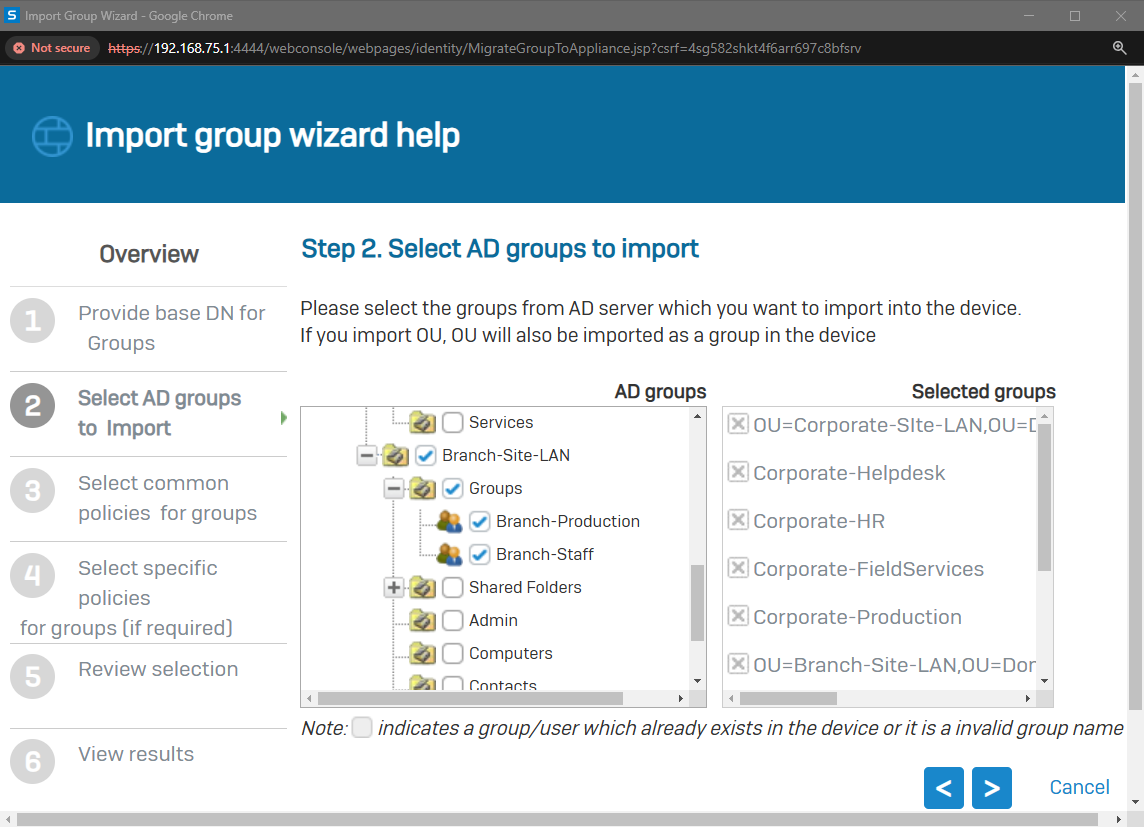
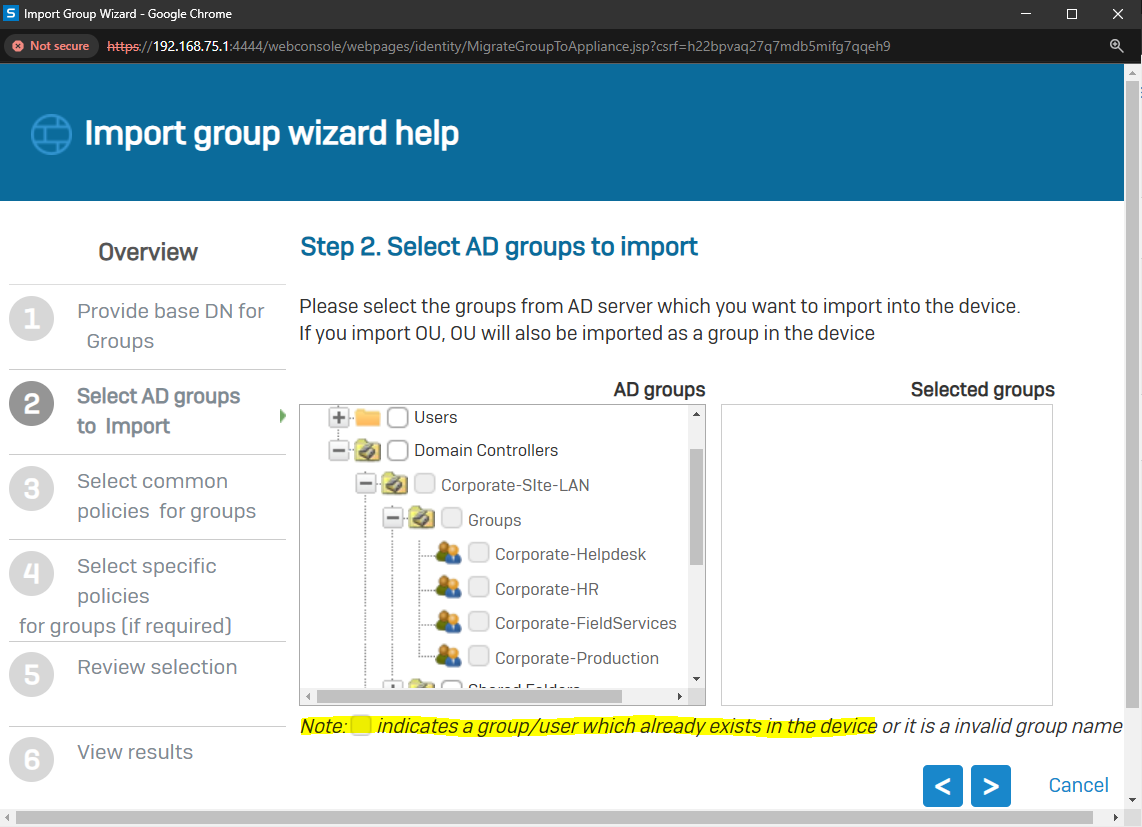
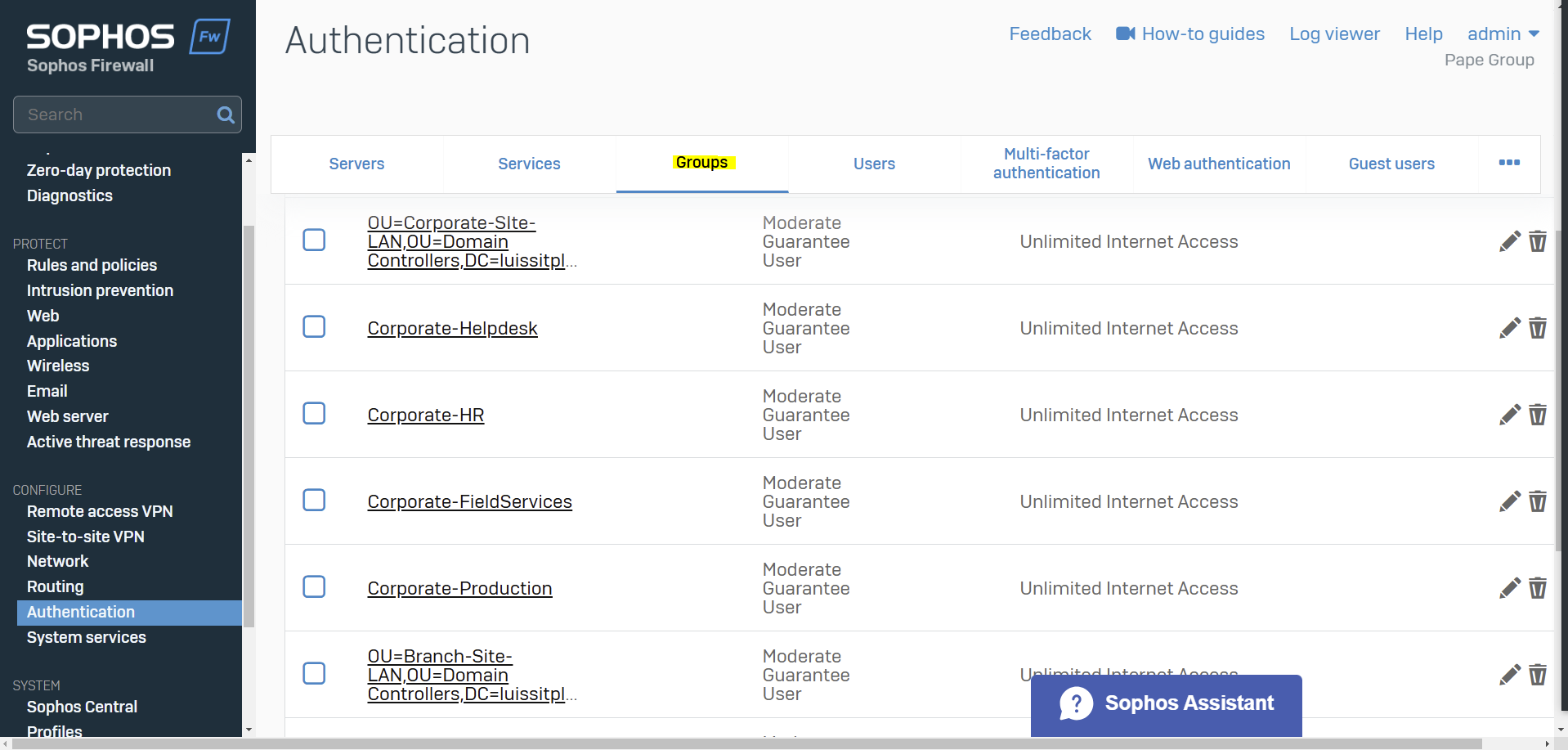
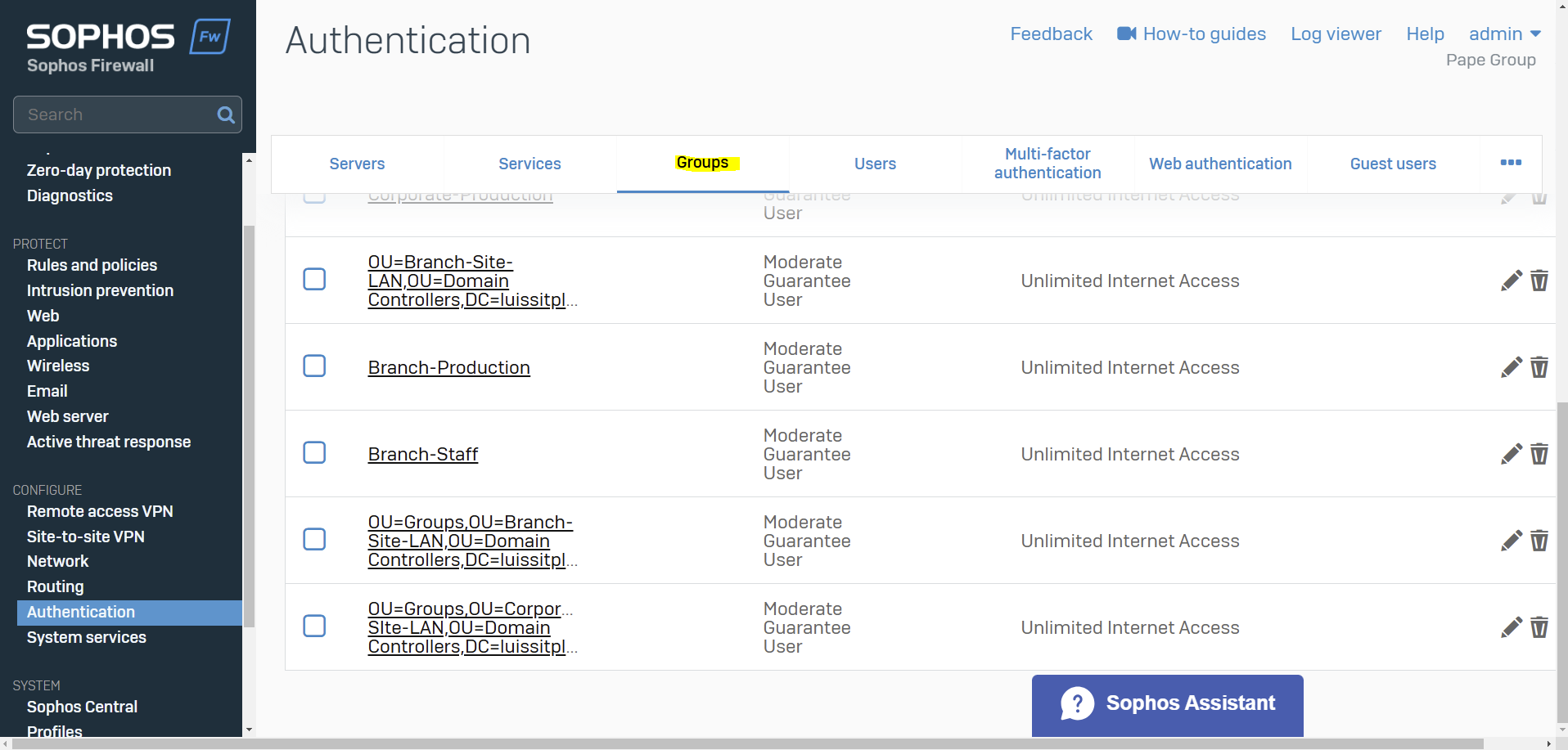
Importing Active Directory Groups
Overview
- Resource: Configure Active Directory Authentication
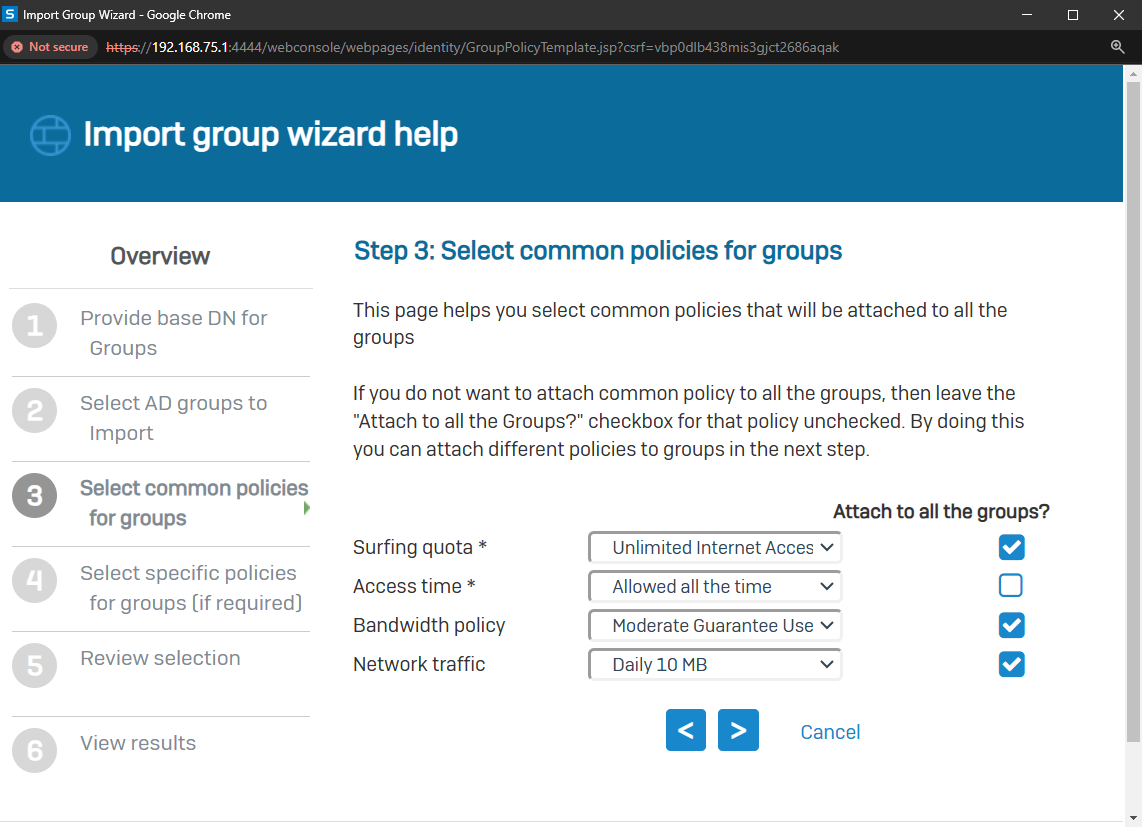
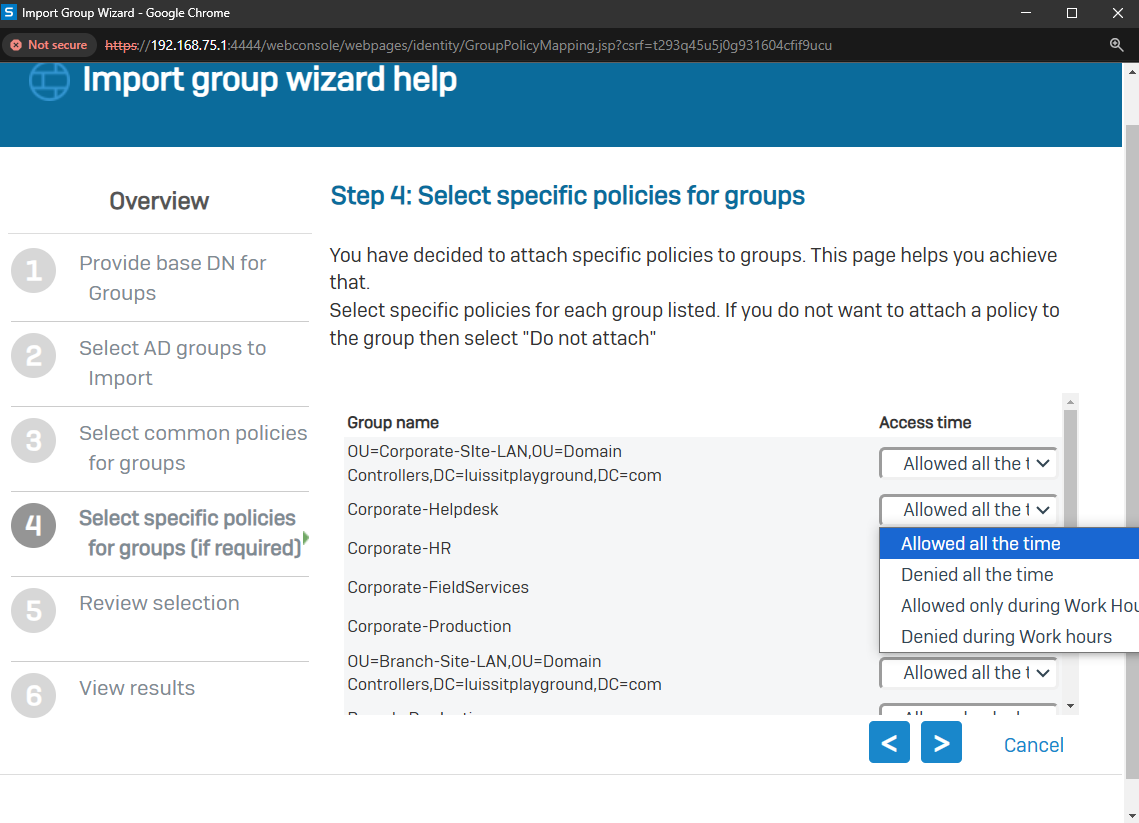
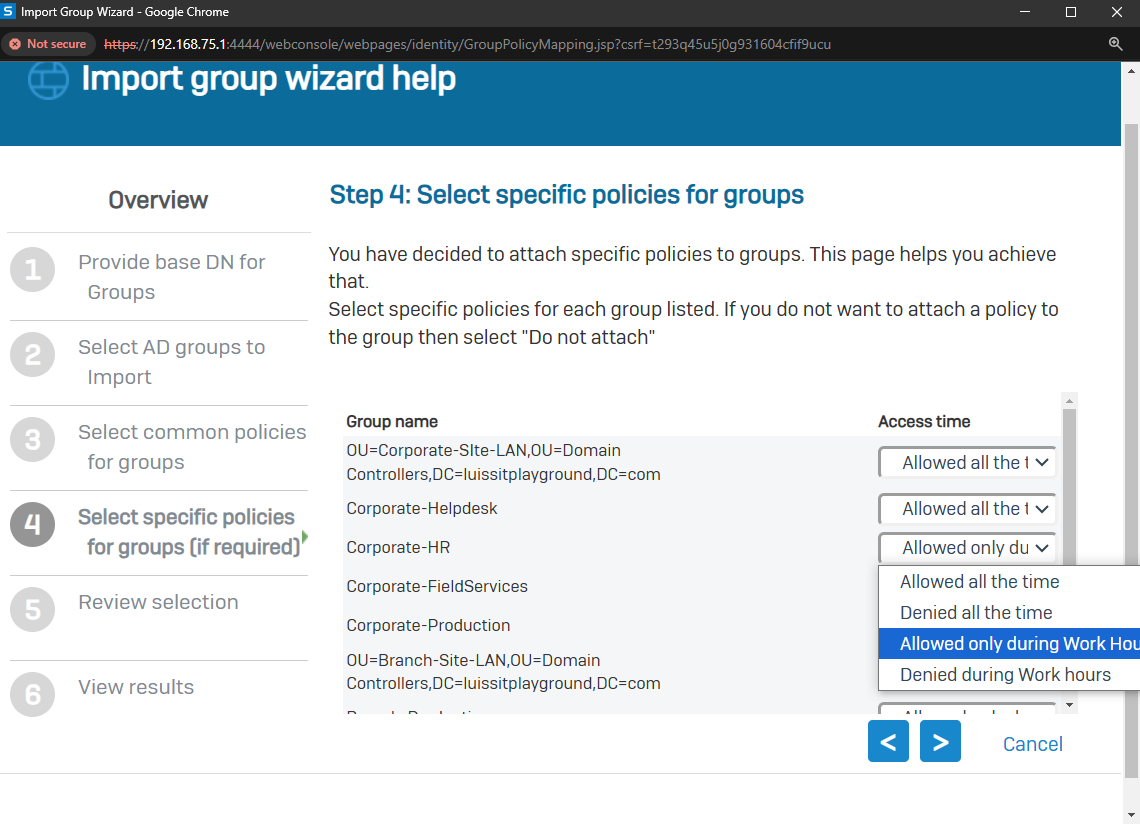
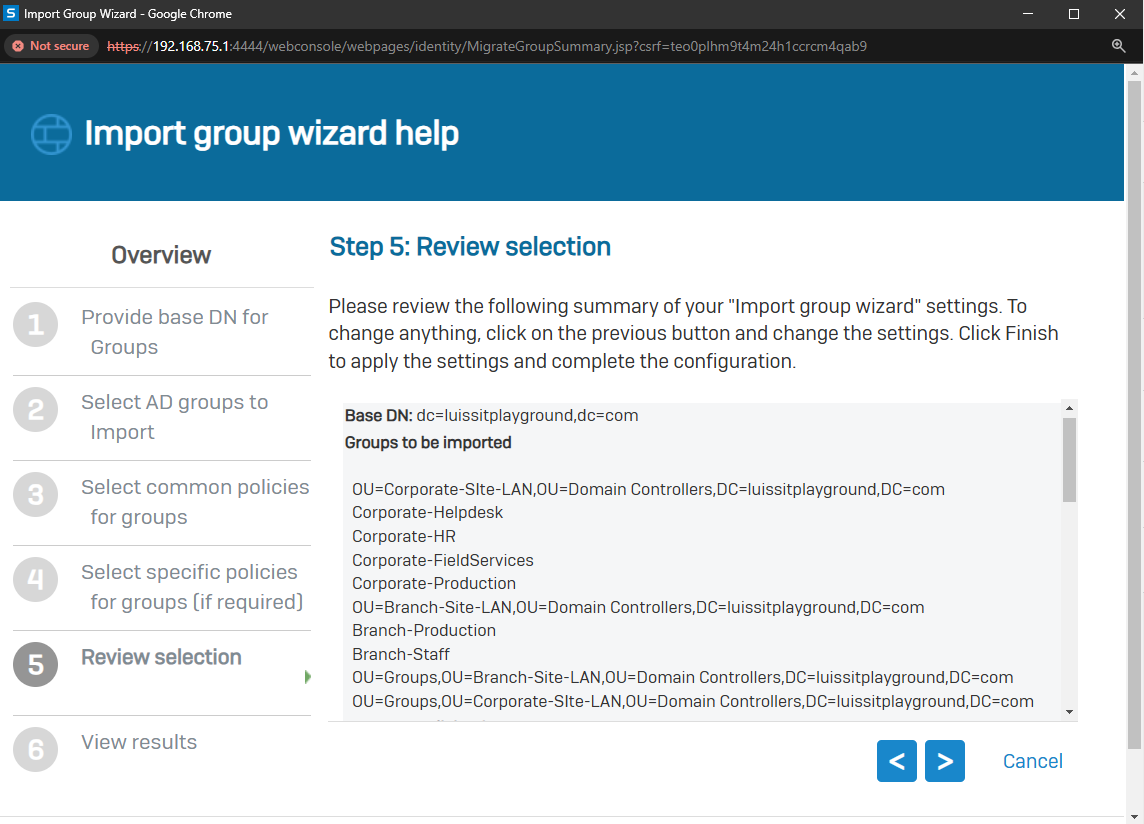
- In this demonstration, I will walk-through the process of importing Active Directory groups into the Sophos Firewall using the 'Import group wizard' interface and specify common policies
- All imported Active Directory groups can be assigned the same common policies or targeted different policies based on the AD group
- The following policies can be attached to imported Active Directory groups
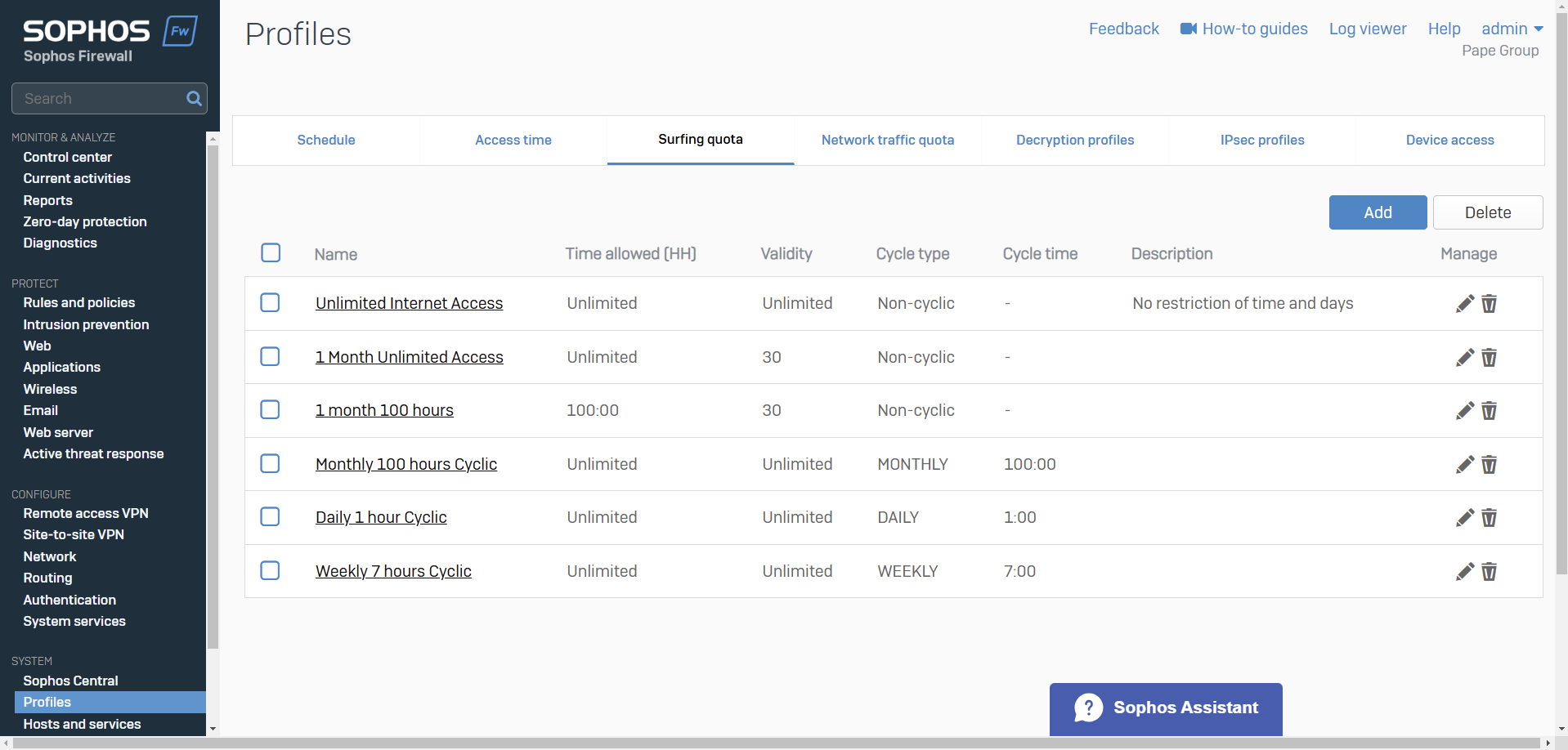
- Surfing Quota
- Access Time
- Bandwidth Policy
- Network Traffic
Common Policies for AD Groups
Surfing Quotas
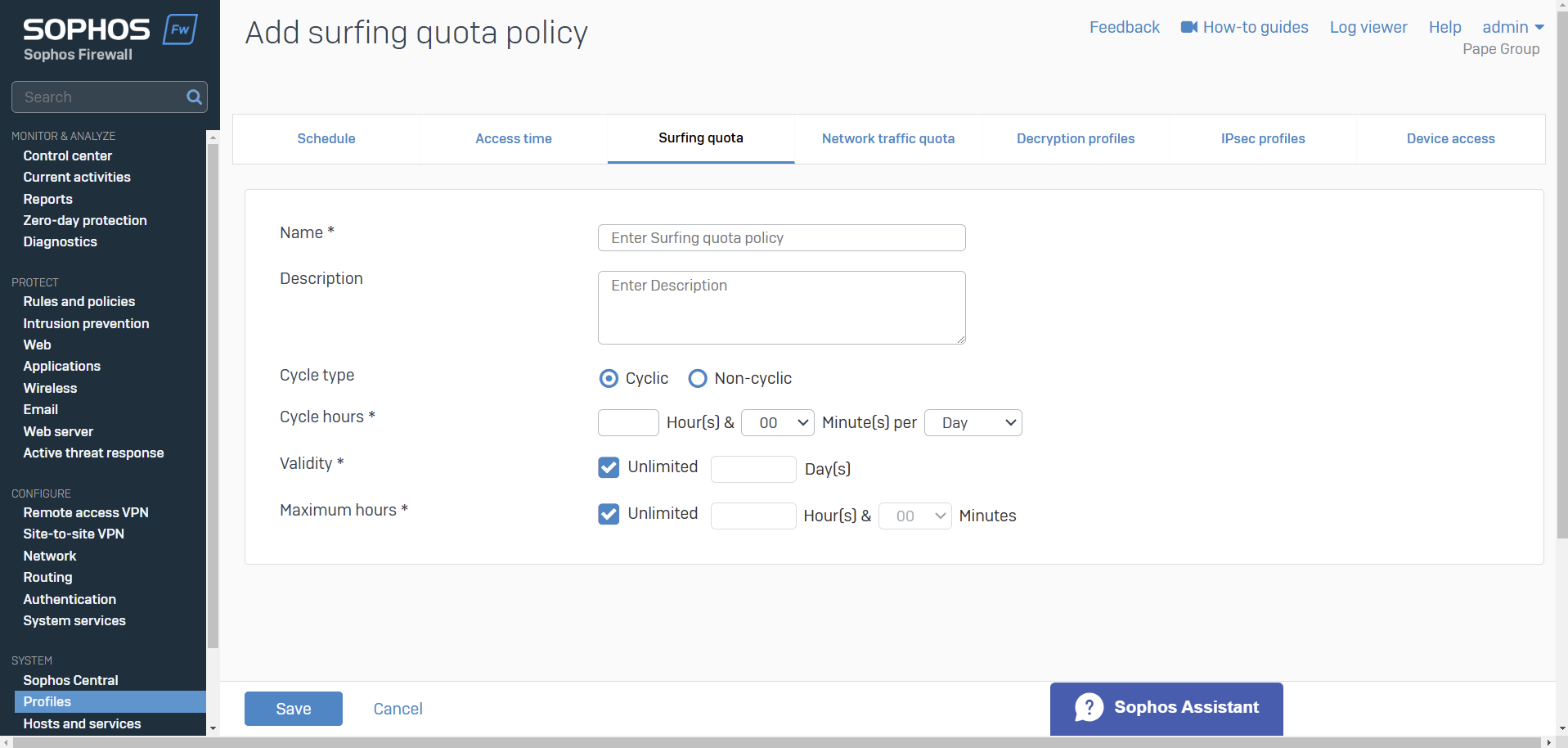
- Resource: Add a Surfing Quota
- Surfing quotas allow you to allocate Internet access time to your users
- Quotas allow access on a cyclical (repeat) or non-cyclical (one-time) basis
- You can add quotas and specify the access time allowed, or use the default quotas
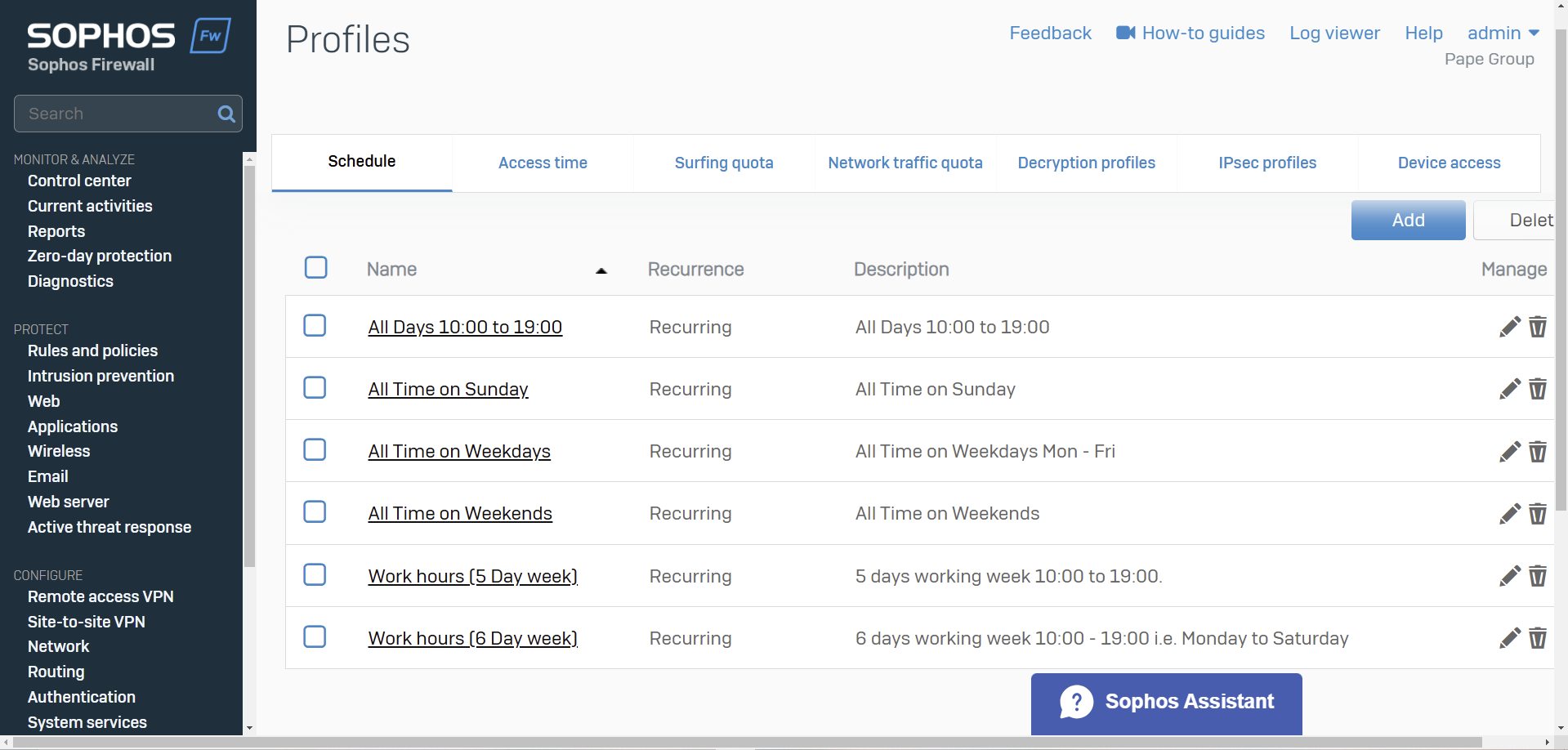
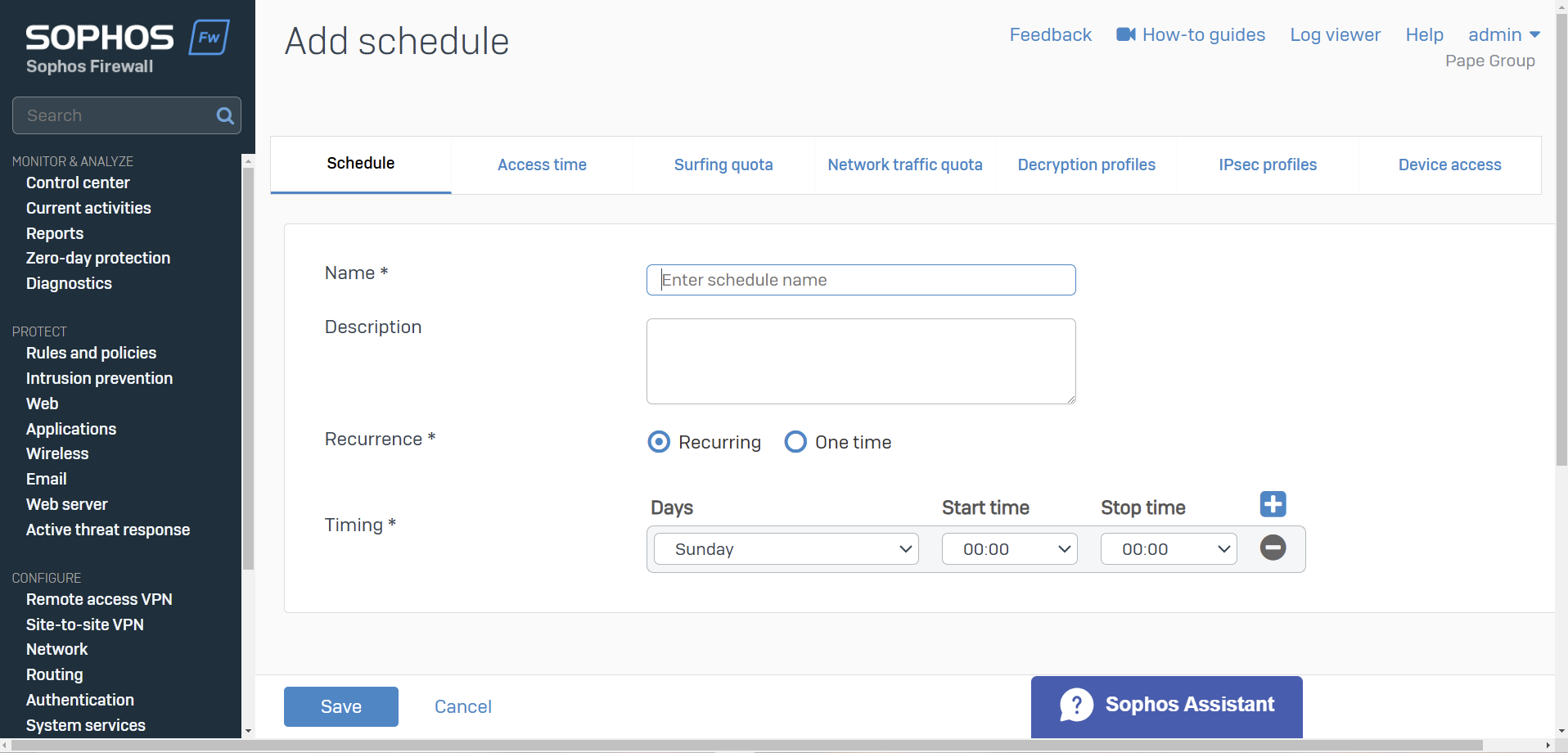
Access Time & Schedules
- Resources
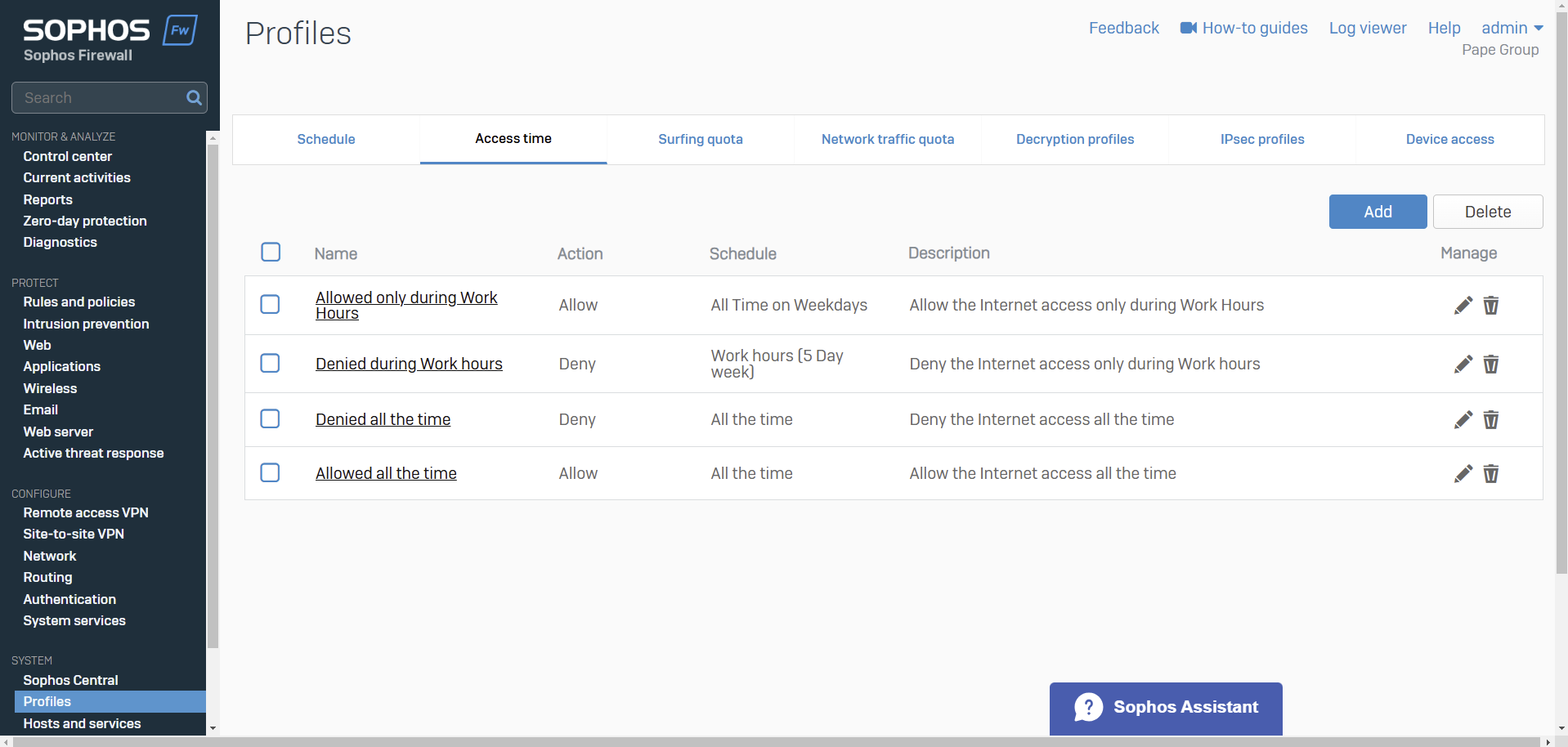
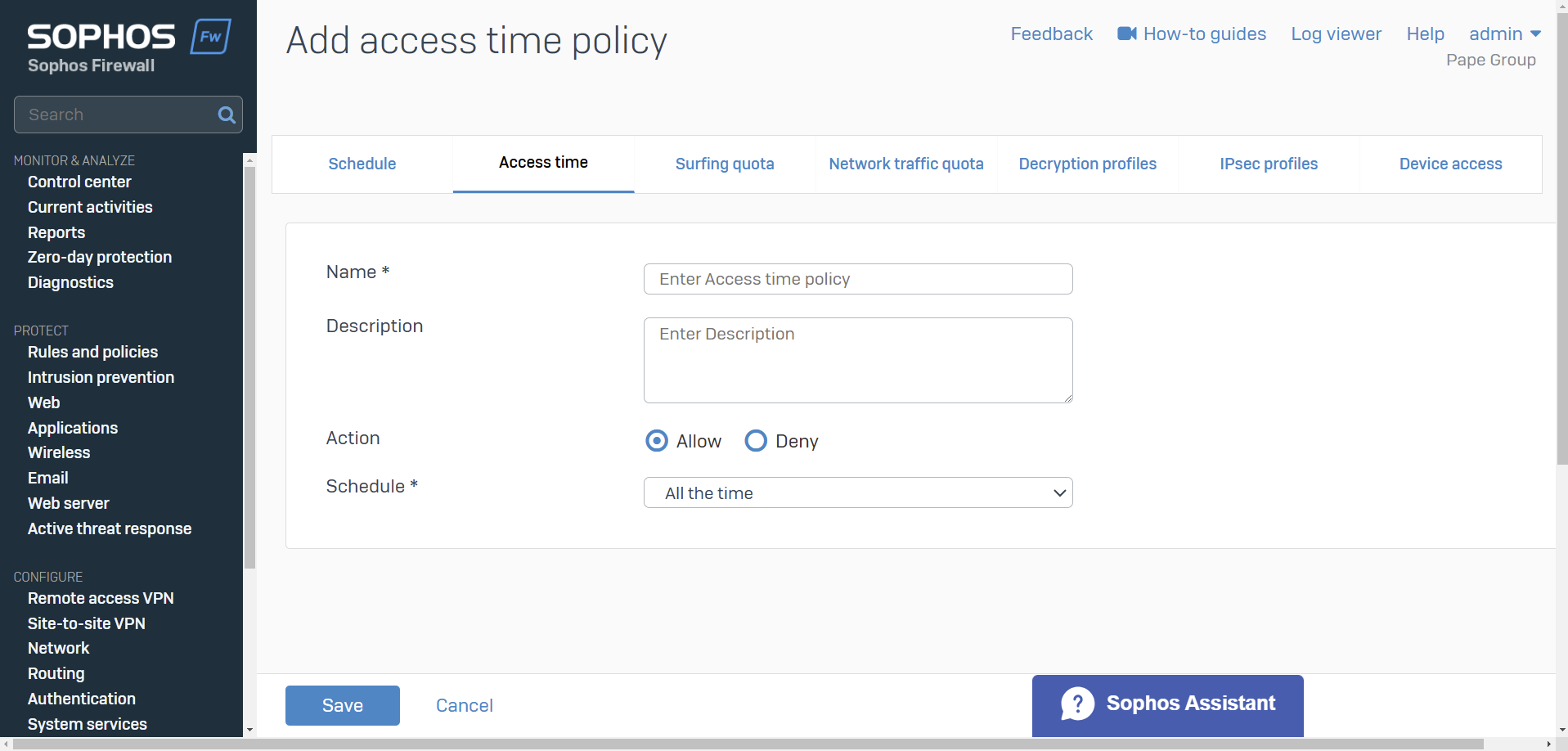
- You can control Internet access time for users, groups, and guest users
- You can allow or deny Internet access based on a scheduled time period
- You can create your own access time policies or use the default policies
- Schedules specify the duration for which rules and policies are in effect
- Schedules can be applied to the following
- Firewall rules
- Web policies
- Application policies
- Traffic shaping policies
- Access time policies
Bandwidth Policies
- Resource: Add a Traffic Shaping Policy
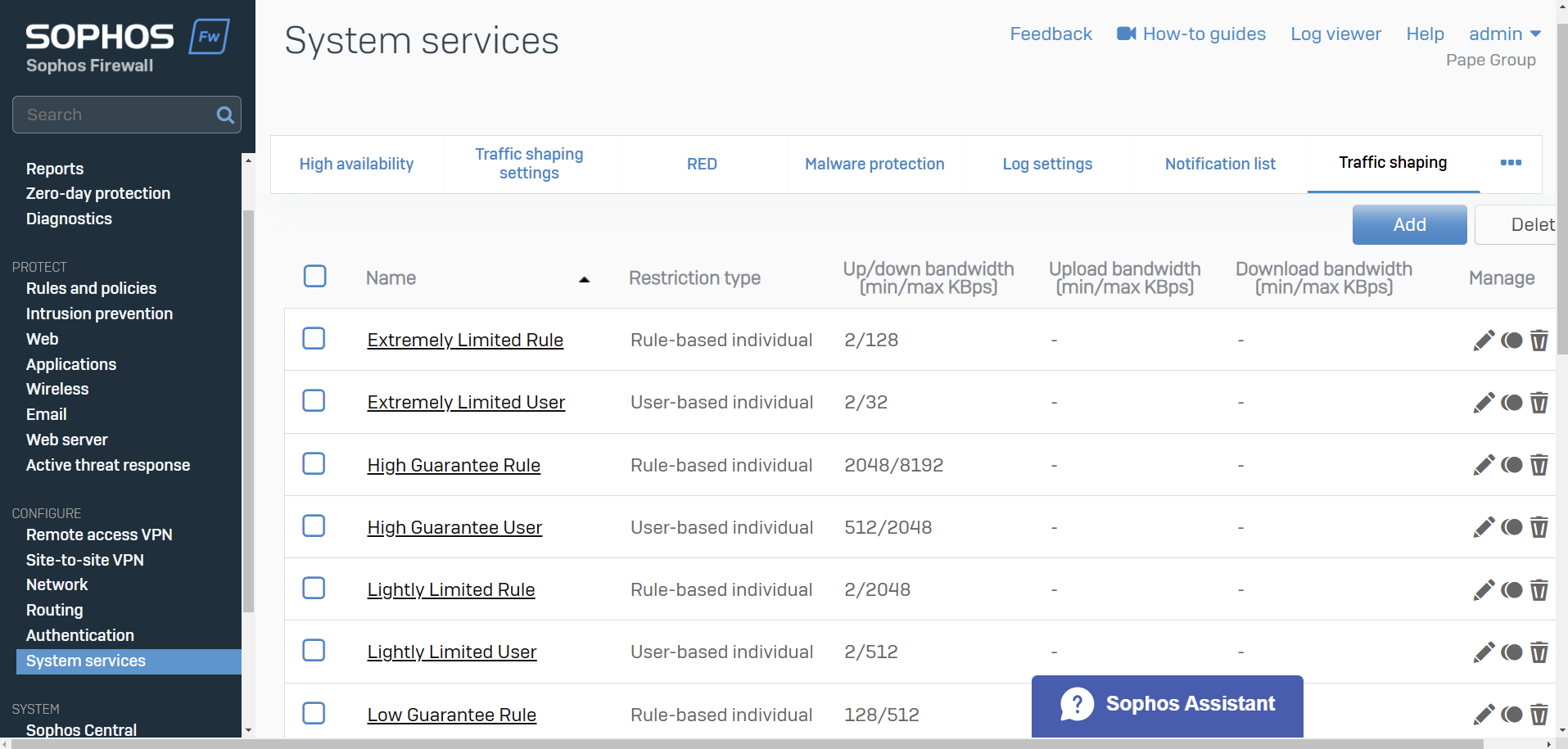
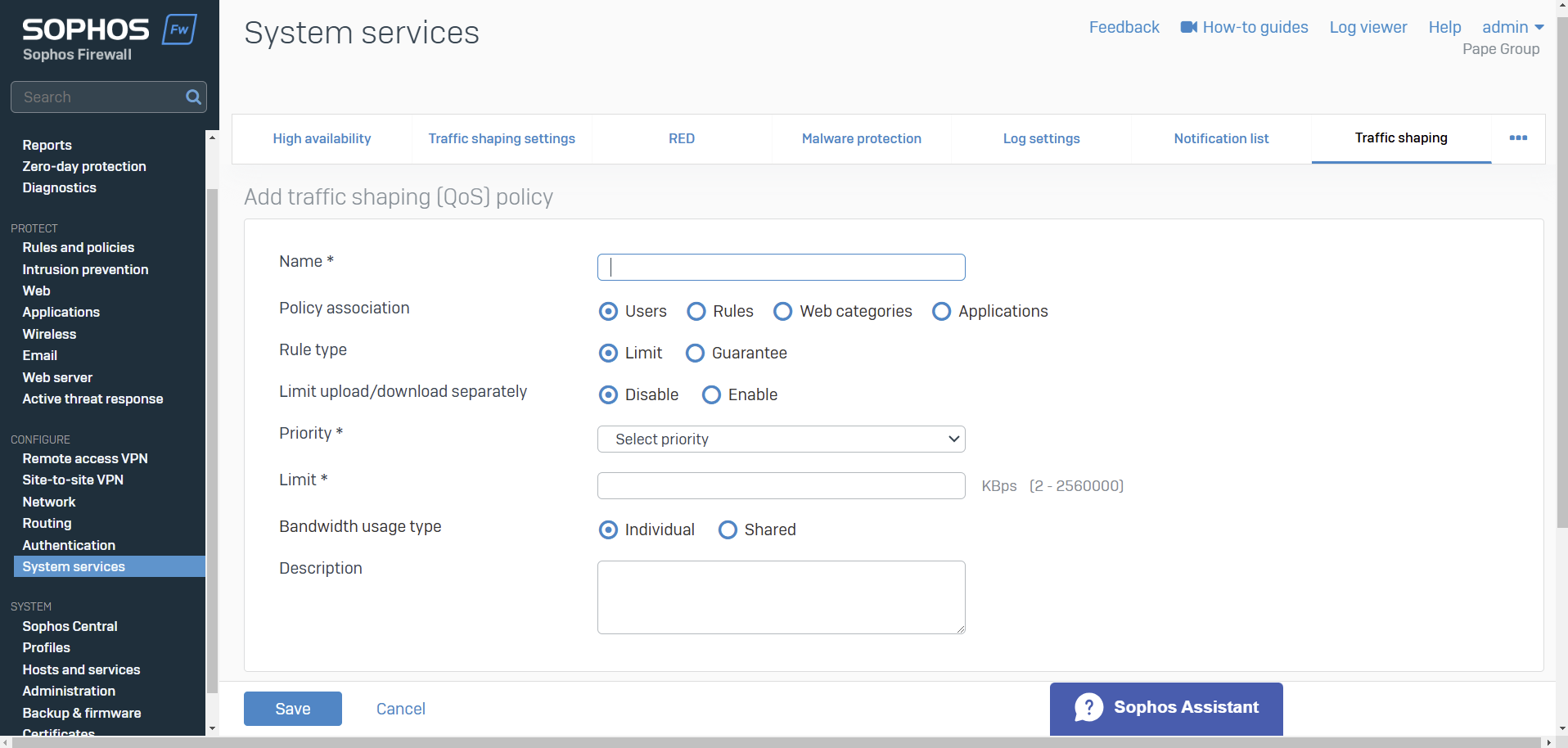
- Bandwidth policies or traffic shaping policies determine the Quality of Service (QoS) for traffic
- You can create policies to guarantee and limit bandwidth. Policies can assign bandwidth to individual objects or be shared among the objects to which you apply them. You can also specify a time for the policy
- You can apply traffic shaping policies to firewall rules, and WAF rules, users and groups, applications and application categories, and web categories
- QoS isn't applied to system-generated traffic
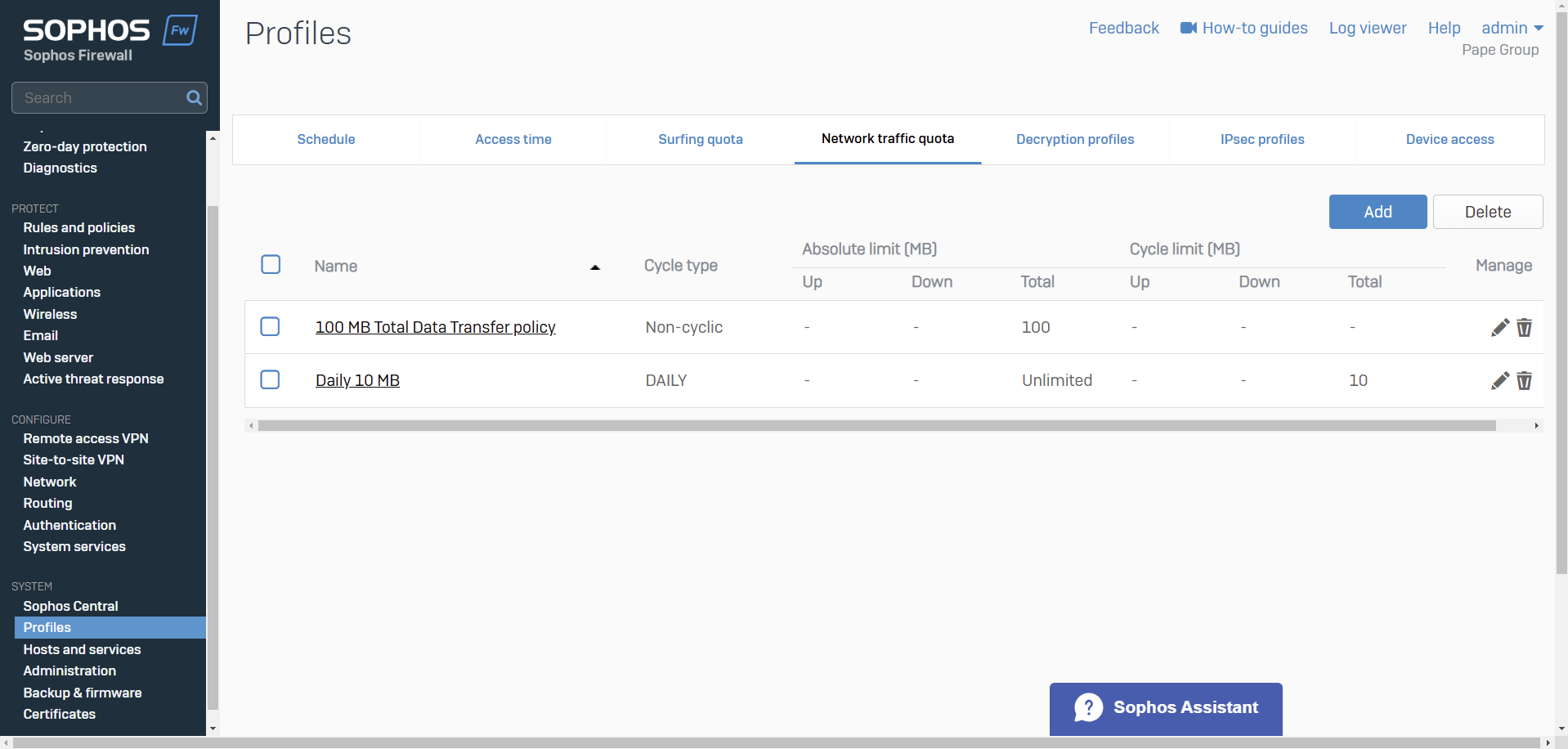
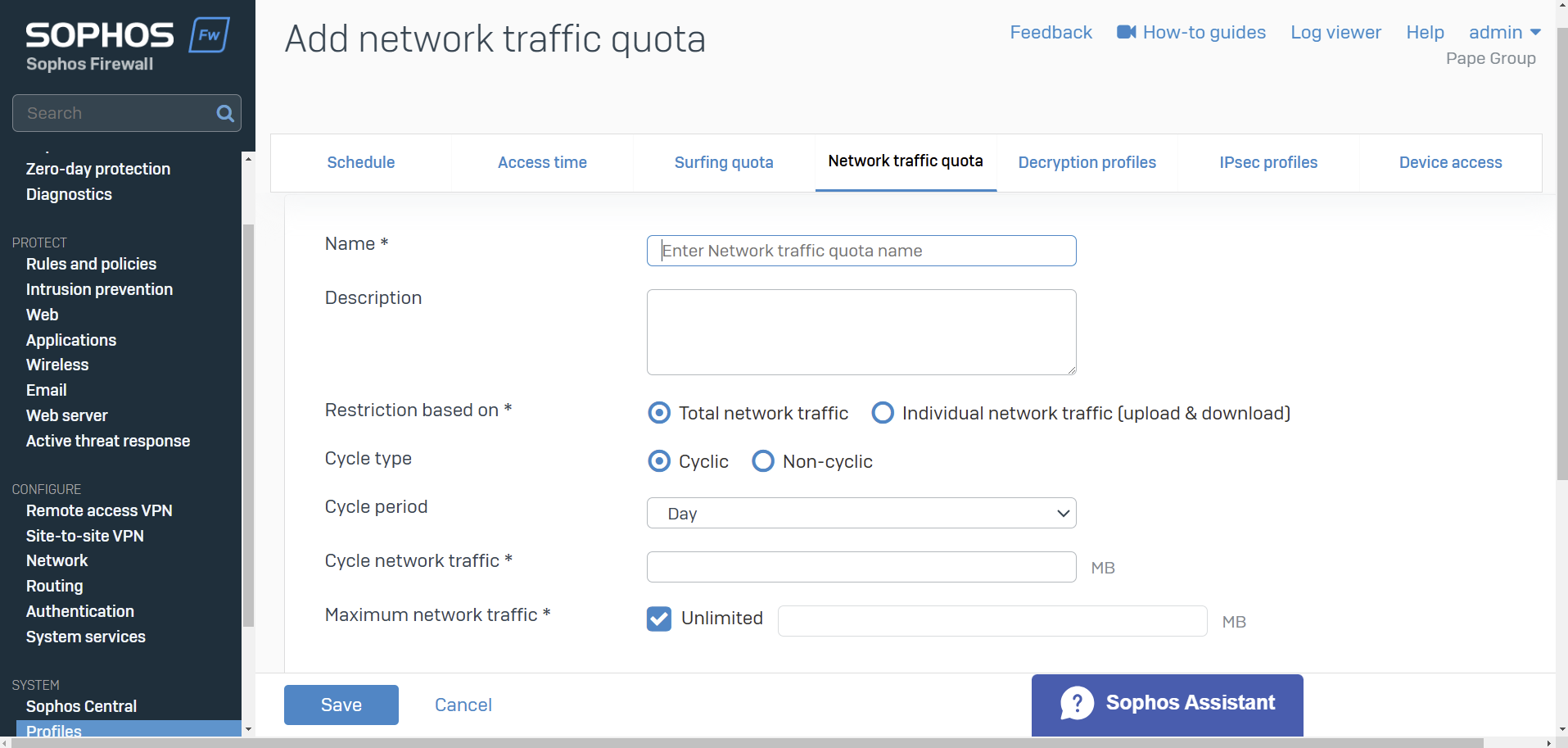
Network Traffic
- Resource: Add a Network Traffic Quota Policy
- Use network traffic quota policies to control data transfer by users and groups
- You can restrict data transfer based on total data transfer or individual network traffic (upload and download)
- Quotas can be cyclic (repeating) and non-cyclic (non-repeating). Specify the amount of network traffic allowed
- You can create your own network traffic quota policies or use the default policies
Importing Active Directory Groups
Client Authentication Agent
Overview
- Resources
VPN Portal Authentication
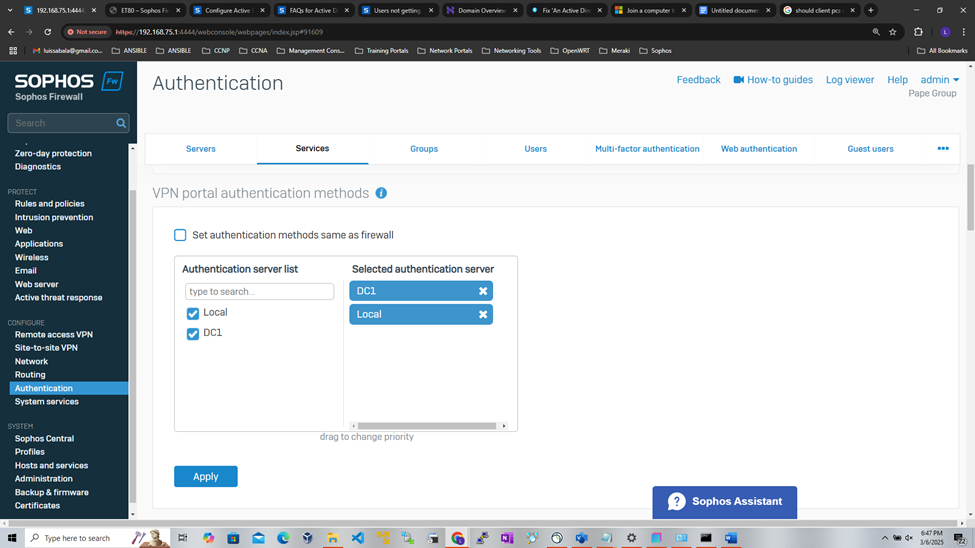
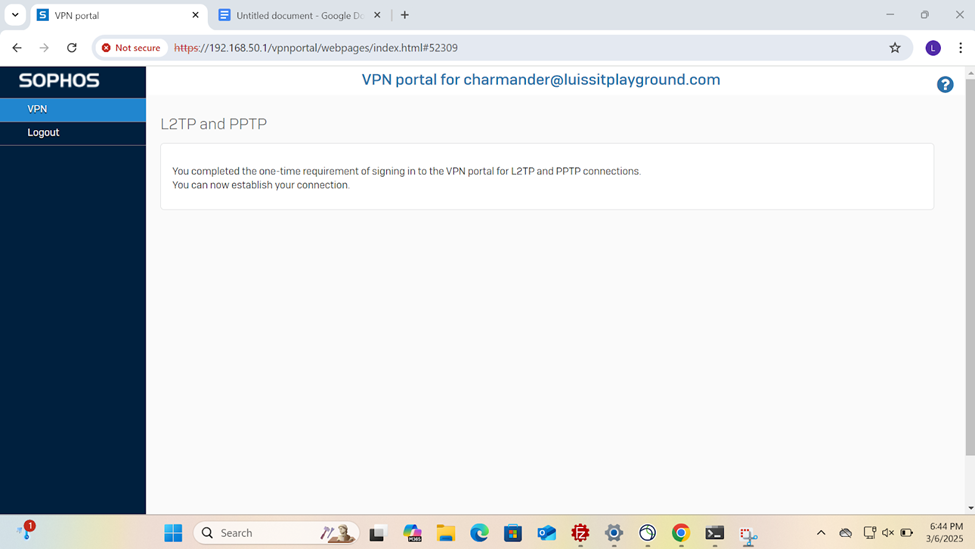
VPN Portal Authentication




Set Primary Authentication Method for Sophos Services
Overview
- Resource: Configure Active Directory Authentication
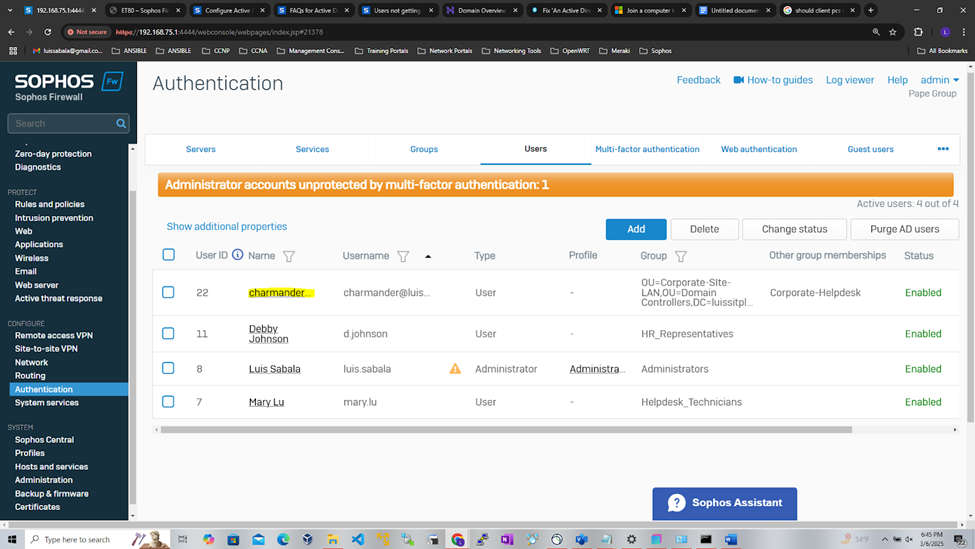
- Upon adding an external Active Directory server and importing groups, the Active Directory server will need to be set as the primary authentication method on the Sophos Firewall for the services required
- When users sign in to the firewall for the first time, they're automatically added as a member of AD groups imported
- In this demonstration, I will be setting my Active Directory server as the primary authentication method for the following Sophos Firewall services
- VPN Portal
- User Portal
- VPN (IPsec/dial-in/L2TP/PPTP)
- SSL VPN
VPN Portal Authentication




User Portal Authentication
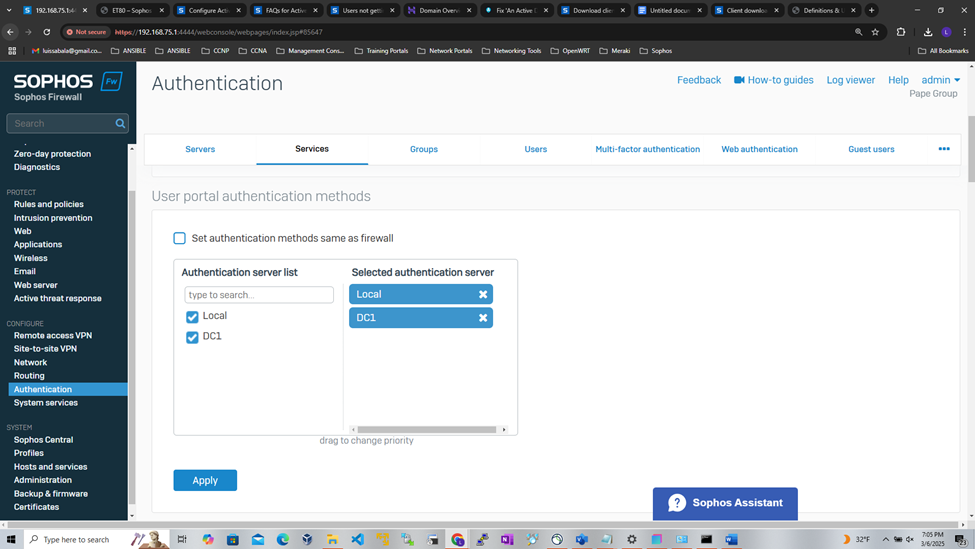
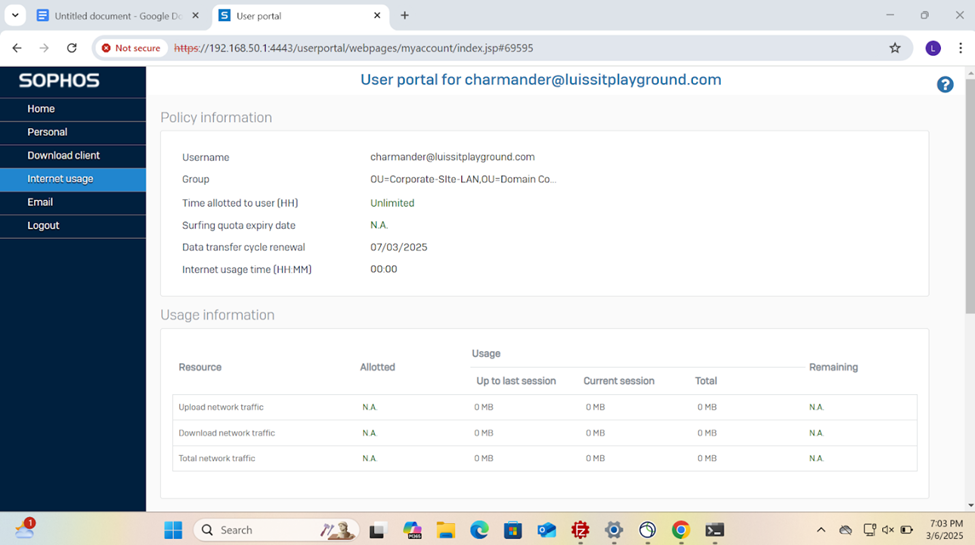
VPN (IPsec/dial-in/L2TP/PPTP) with Firewall Authentication
- Resources
- In this lab demonstration, I have a domain user located on each LAN (Corporate & Branch site) to test and verify IPsec S2S VPN & Firewall authentication via the Active Directory domain controller
- For the entirety of this lab demonstration of the section, I will be taking a closer look into configuring the Branch site domain user, 'Mudkip' for VPN authentication but the same configurations would apply to the Corporate domain user 'Charmander' accessing the Branch site LAN via the VPN
- Domain Users
- Corporate Site - 'Charmander' on the Helpdesk VLAN50 internal network
- Branch Site - 'Mudkip' on the Staff VLAN70 internal network
Sophos Client Authentication Agent
- The Sophos Client Authentication agent is a software application that allows users to authenticate directly with a Sophos Firewall by installing a client on their computer
- This enables the firewall to identify and manage user access based on their identity rather than just their IP address; providing a more granular level of network access control
- Users have the ability to install the client software via the User portal and shared amongst users. When users sign in to the client, they're signed directly into the network through the firewall
- The client authentication agent is supported on the following
- Windows 10 & later
- Linux: Ubuntu 16.4 & later
- macOS: Catalina (10.15) & later
Installing Sophos Client Authentication Agent
- In this demonstration, I will be installing the authentication agent on the Branch site PC for domain user 'Mudkip', a staff employee to authenticate to the Branch Sophos firewall to eventually access internal resources located at the Corporate site location via the IPsec S2S VPN
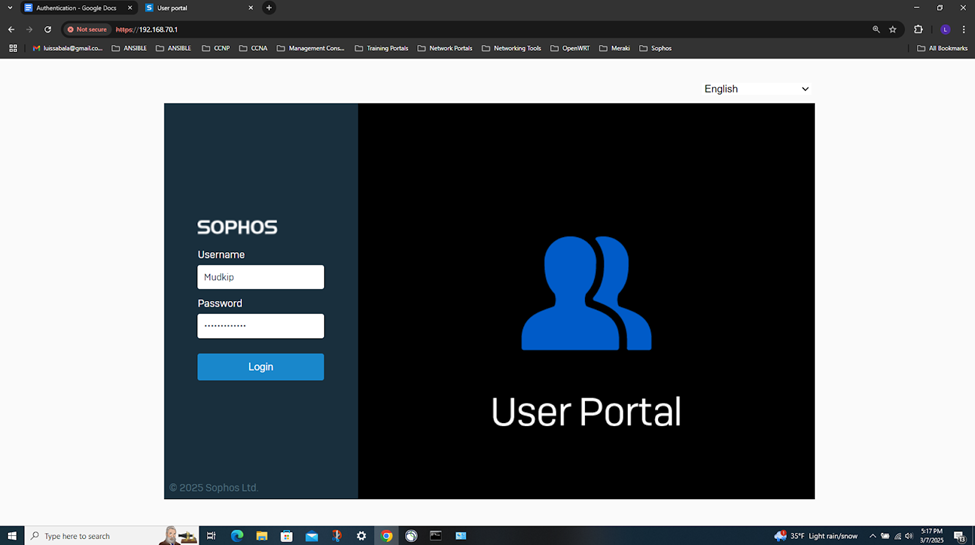
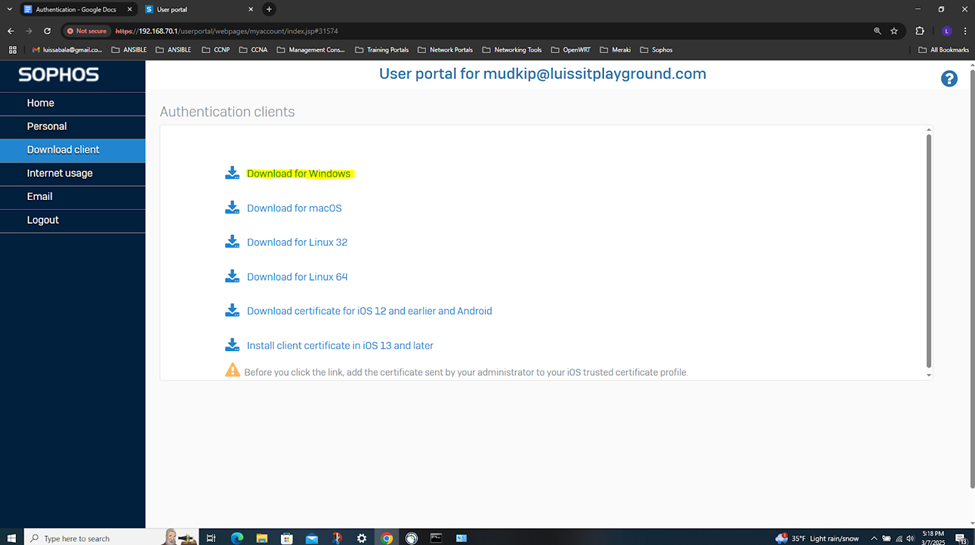
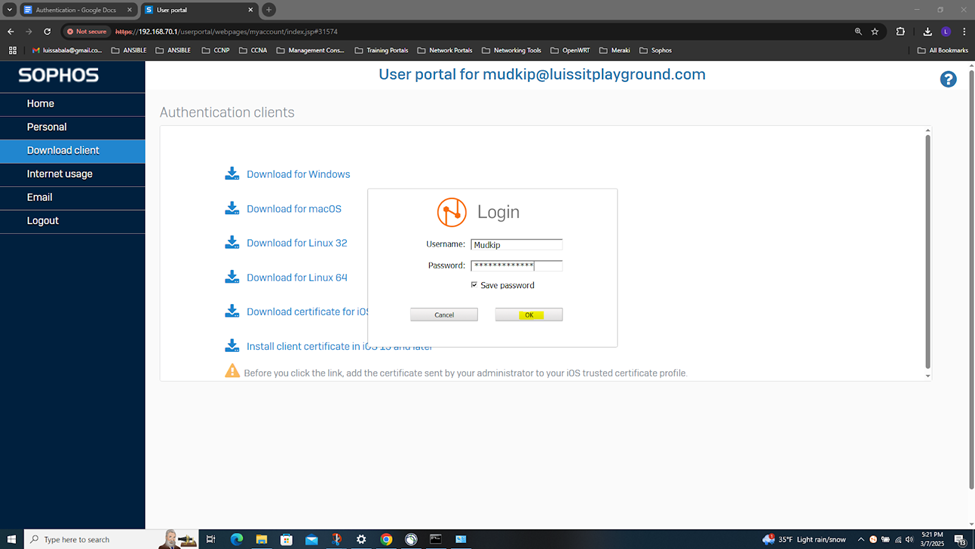
IPsec Firewall Rule & Authentication Configuration Overview
- In this demonstration, I will be demonstrating the inbound and outbound IPsec Firewall rules that will dictate what internal access to the Corporate LAN the authenticated Branch site domain users have via the IPsec S2S VPN
- In this demonstration, I will also be documenting the Sophos Firewall Authentication configurations including the active S2S VPN, the defined Active Directory server using LDAPS for communication between itself and the Sophos Firewall, the imported AD groups and a list of domain users that have authenticated to the Firewall, and lastly the primary Sophos authentication method for the 'Firewall' & 'VPN (IPsec)' services
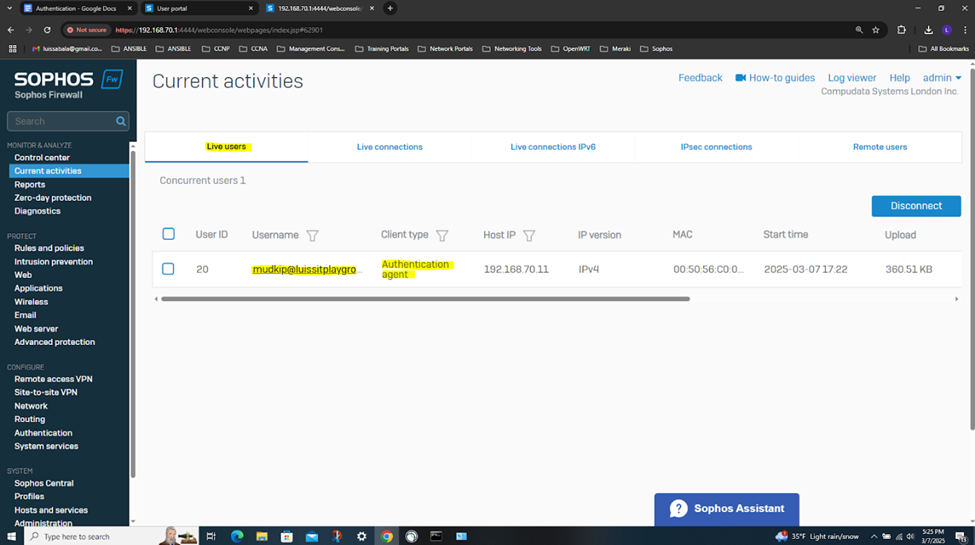
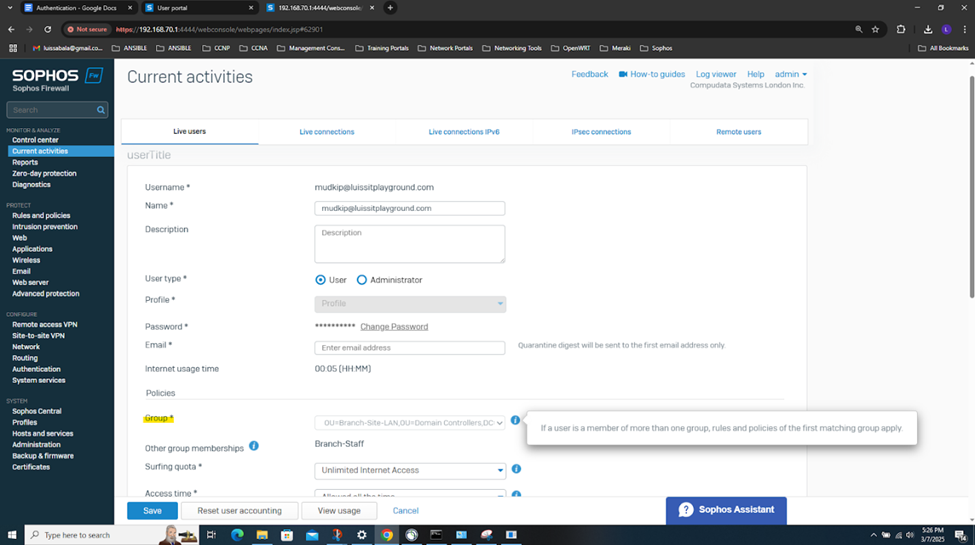
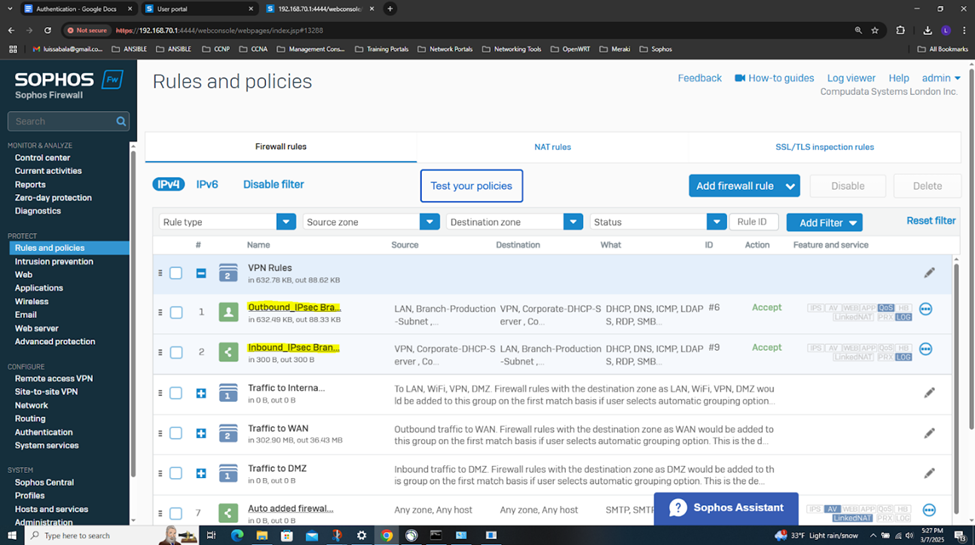
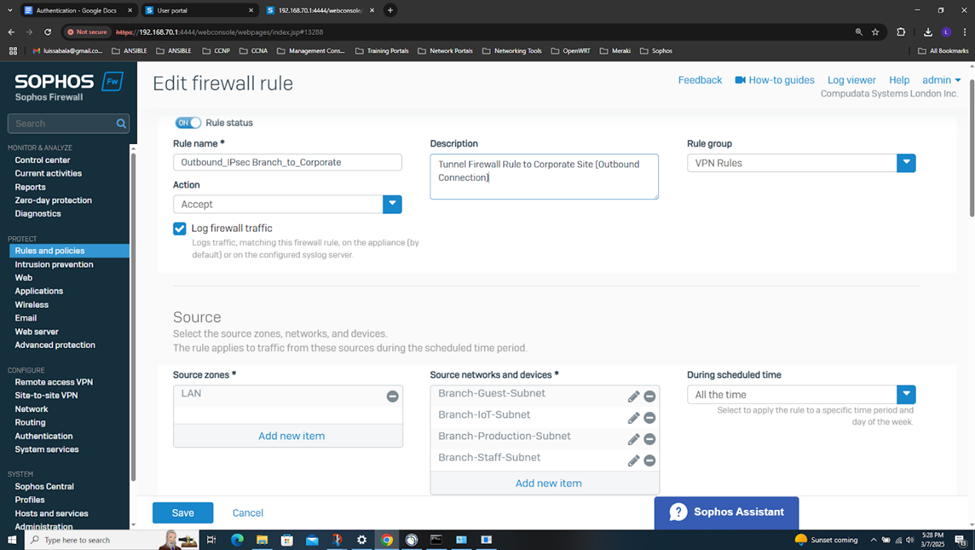
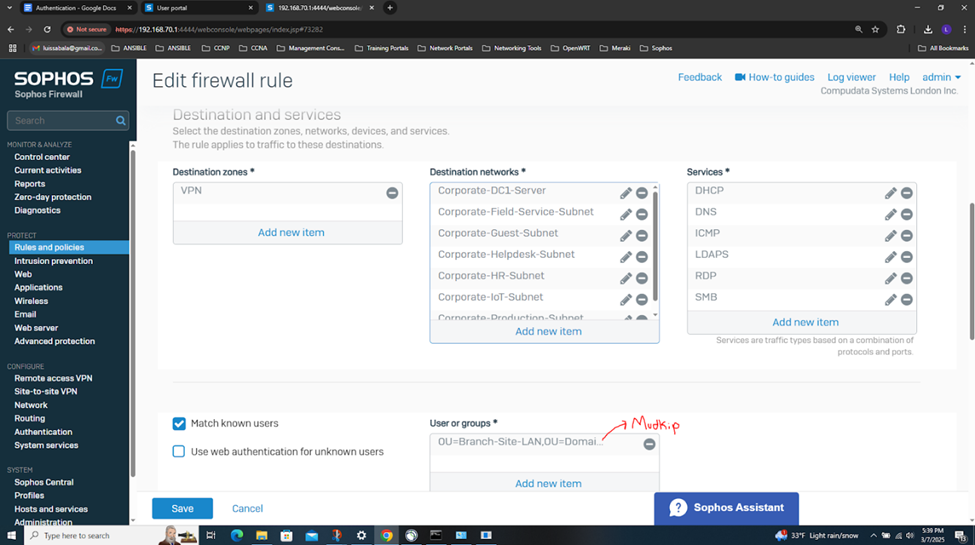
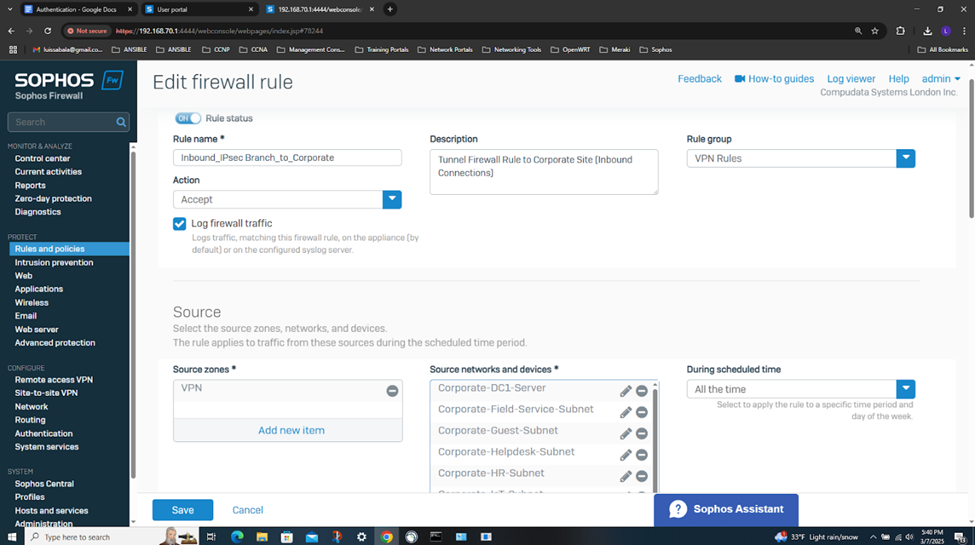
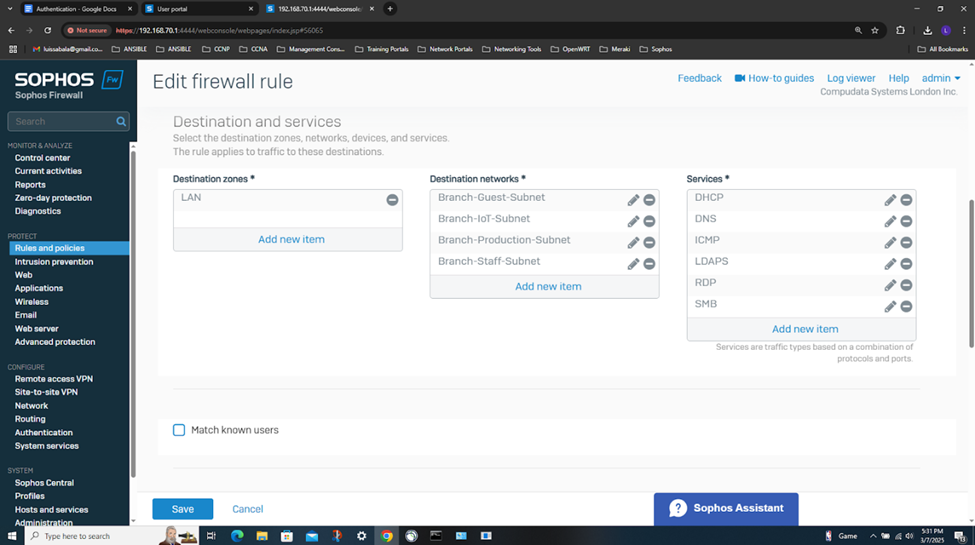
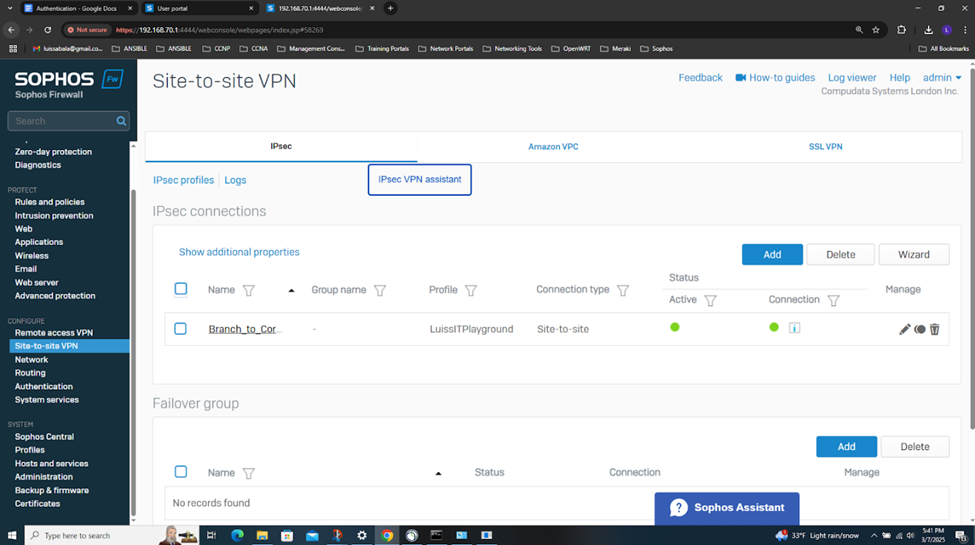
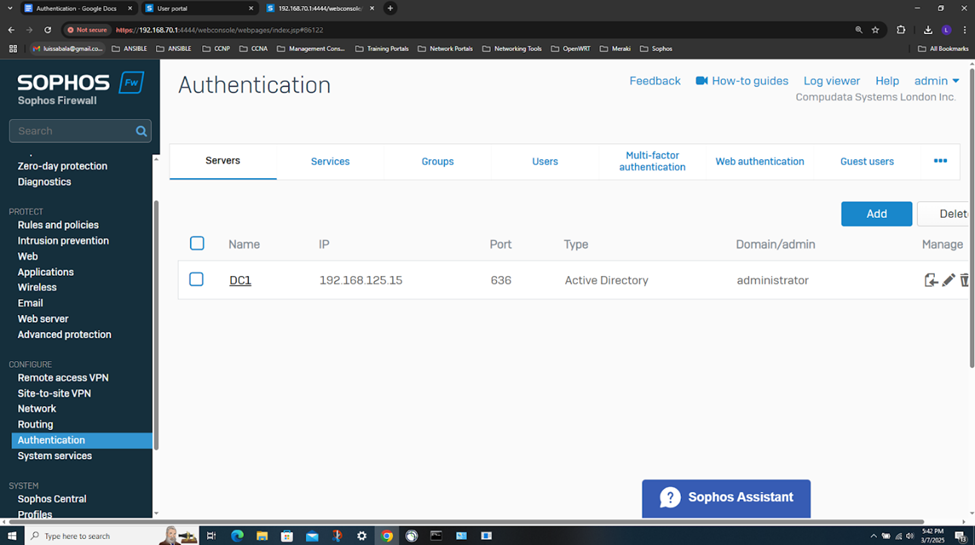
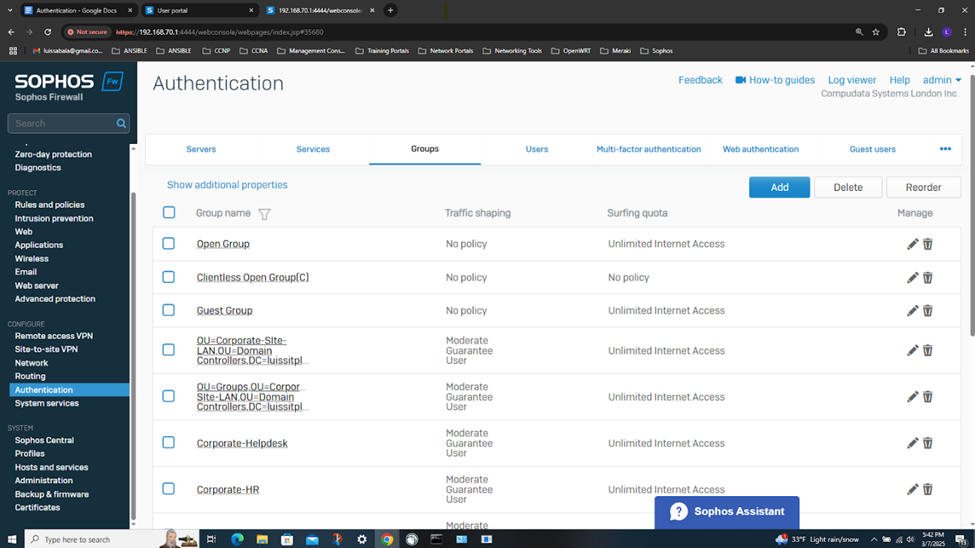
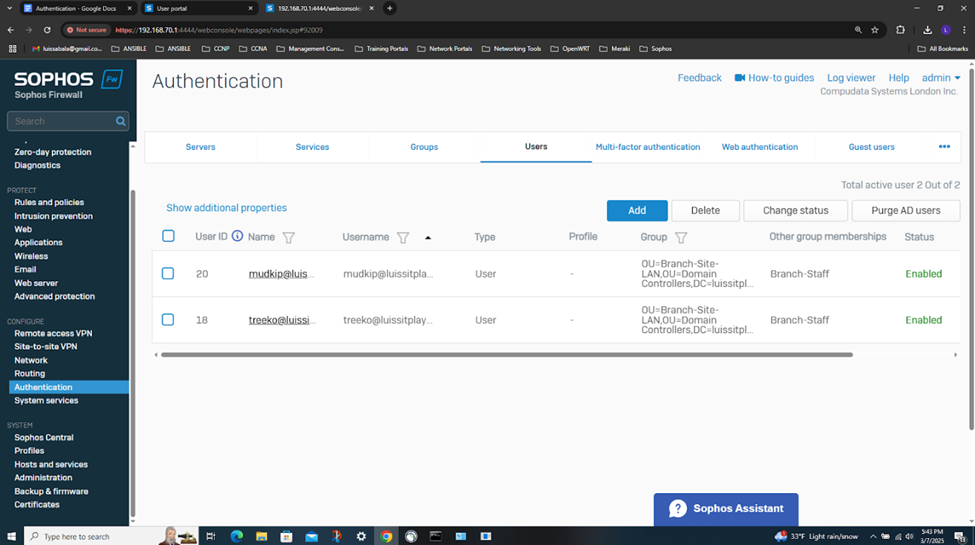
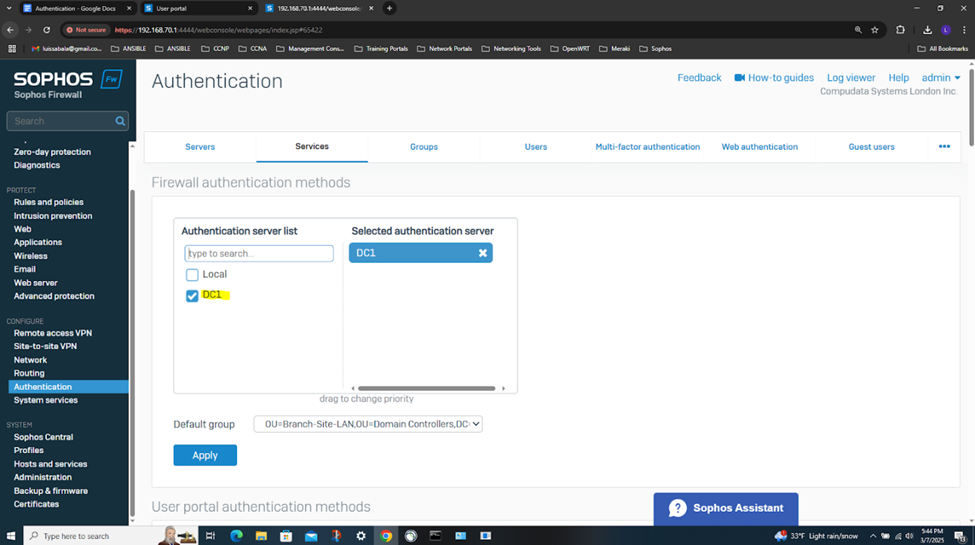
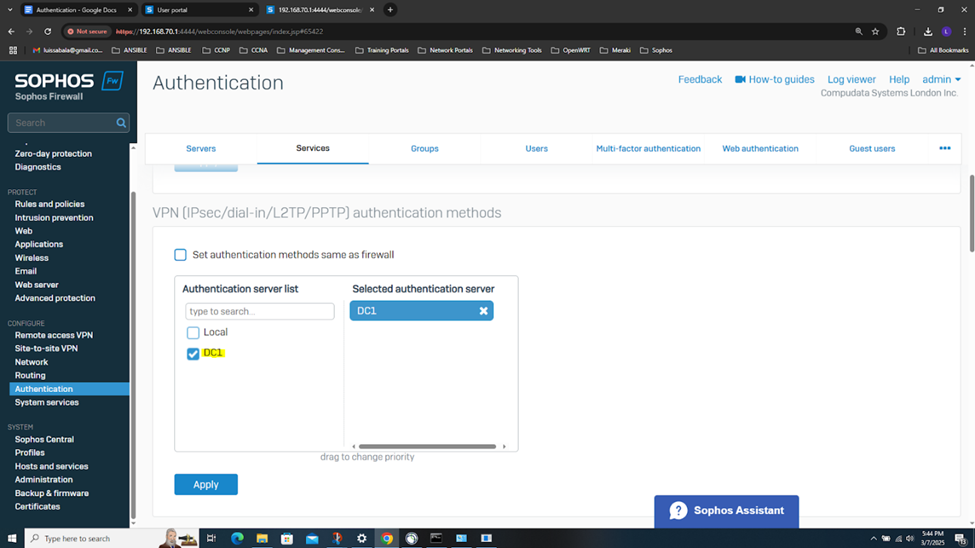
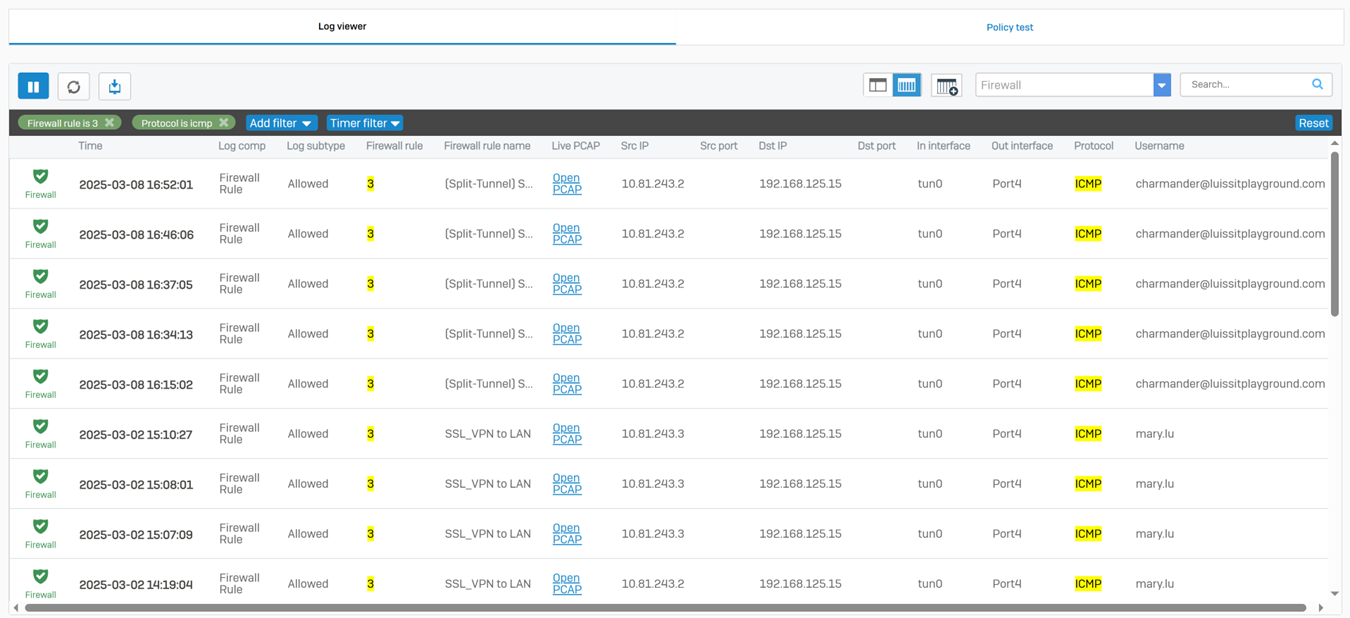
Testing IPsec Firewall Rules via Active Directory Authentication
- In this demonstration, I will be testing the IPsec inbound and outbound Firewall rules by accessing the services defined in the rules
- In this demonstration, I will perform various tests from the Branch site authenticated AD user 'Mudkip'
- Pinging the Corporate site domain user 'Charmander' on the Helpdesk VLAN50 network over the S2S VPN
- Connecting to an accessible network share from the Windows DC1 server over the S2S VPN
- Establish an RDP connection to the Windows DC1 server located at the Corporate site LAN over the S2S VPN
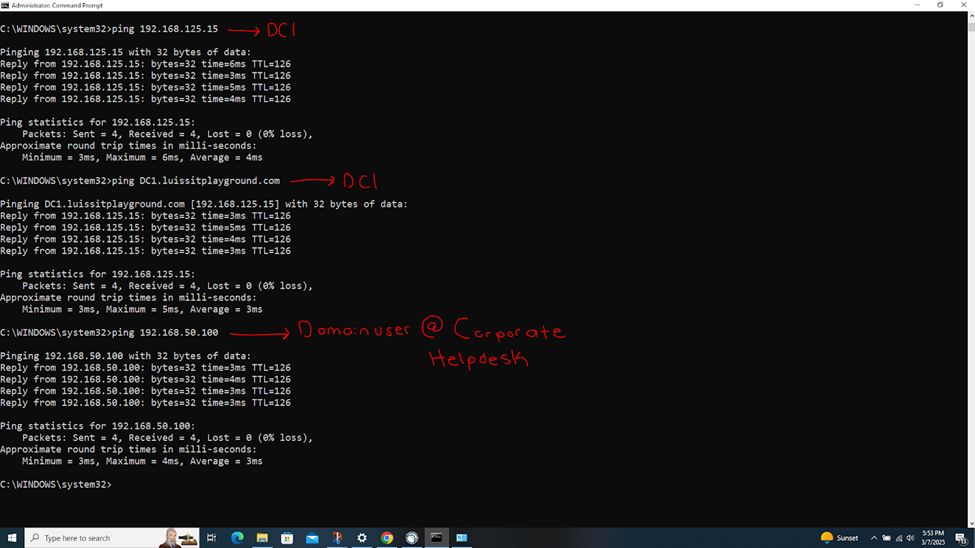
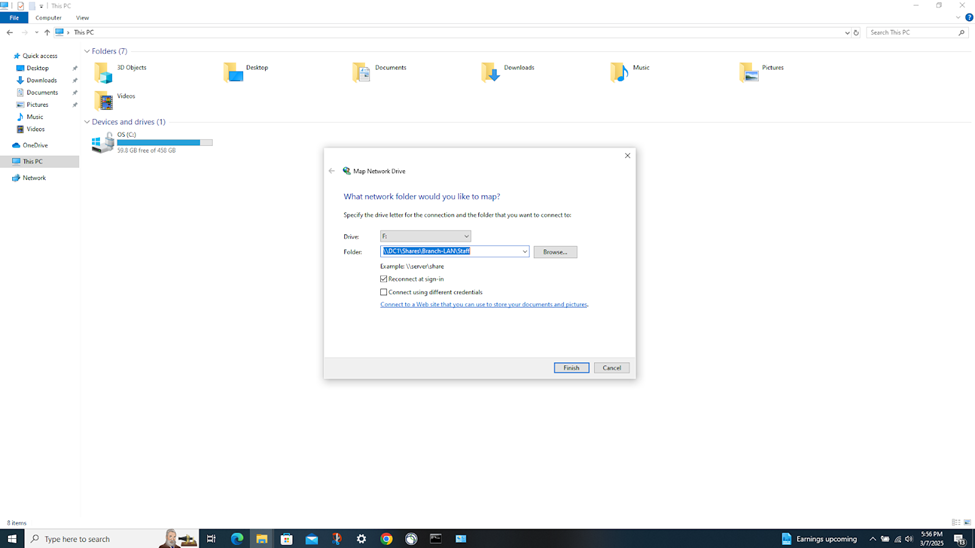
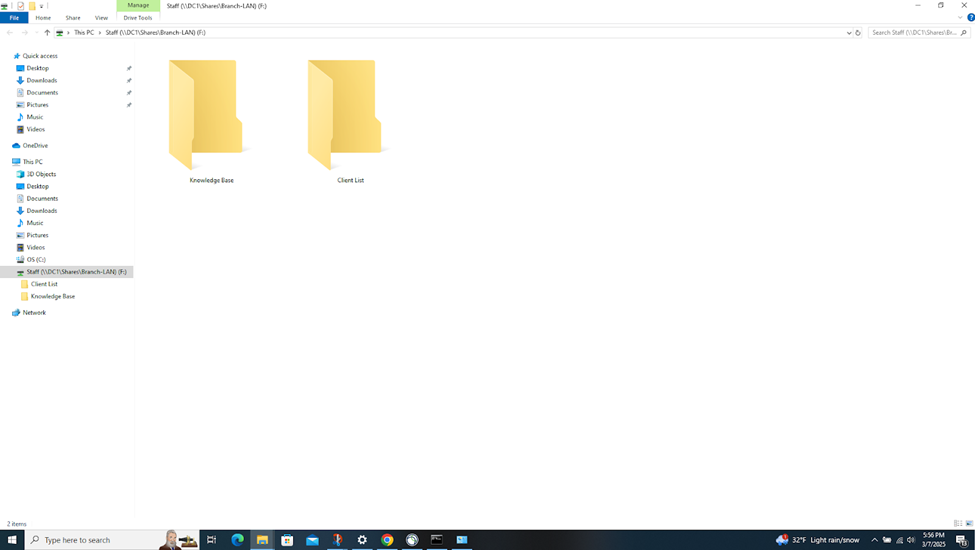
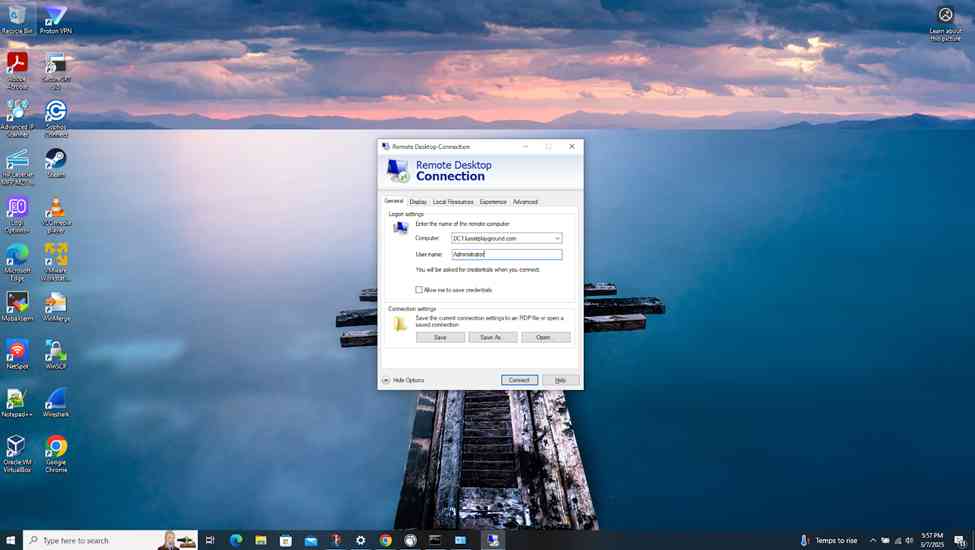
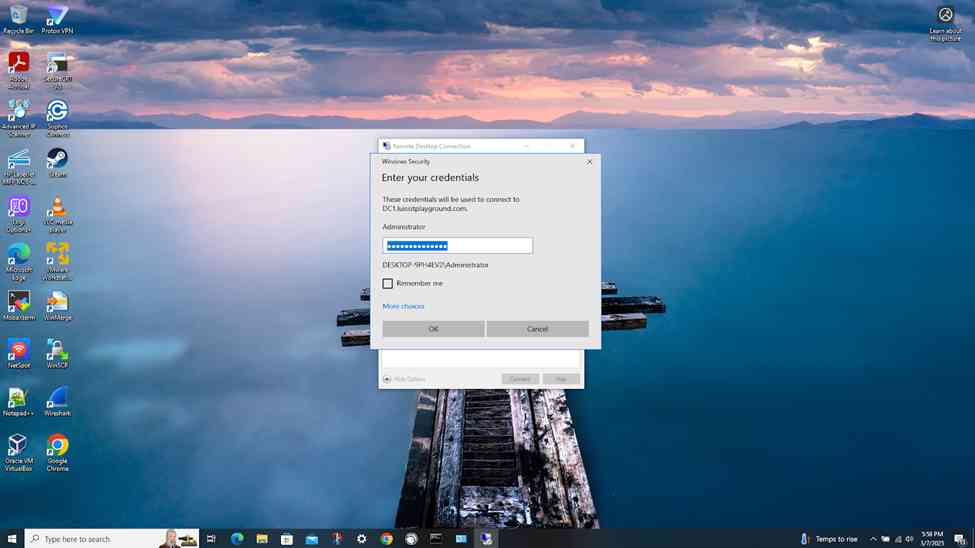
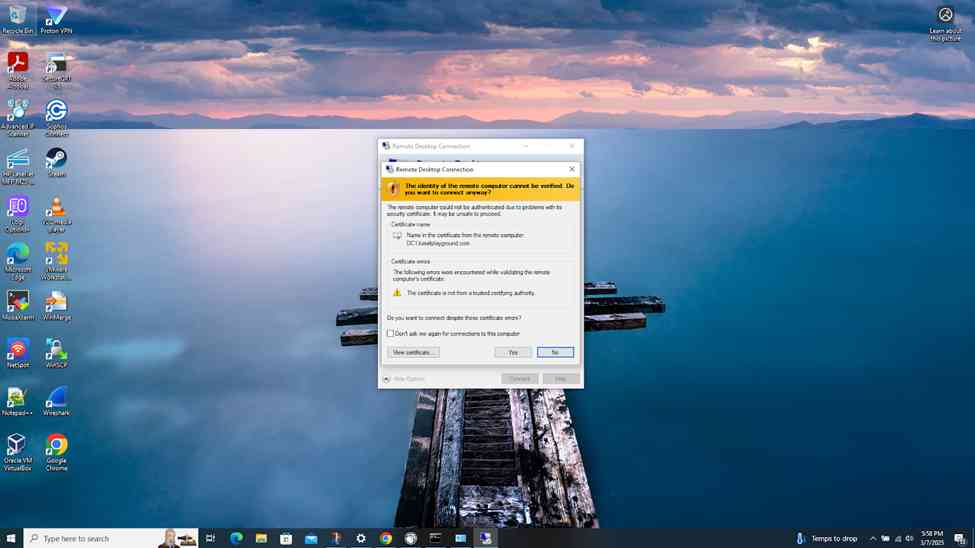
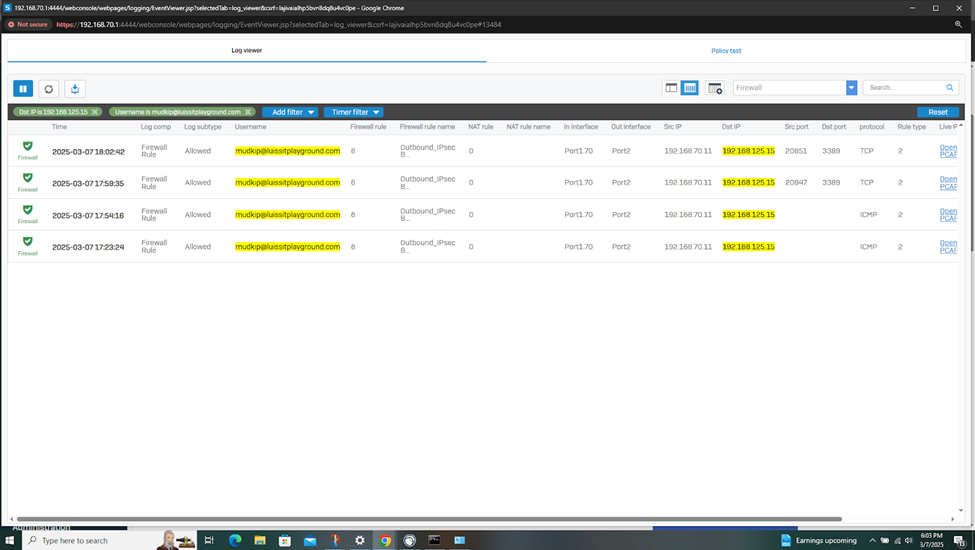
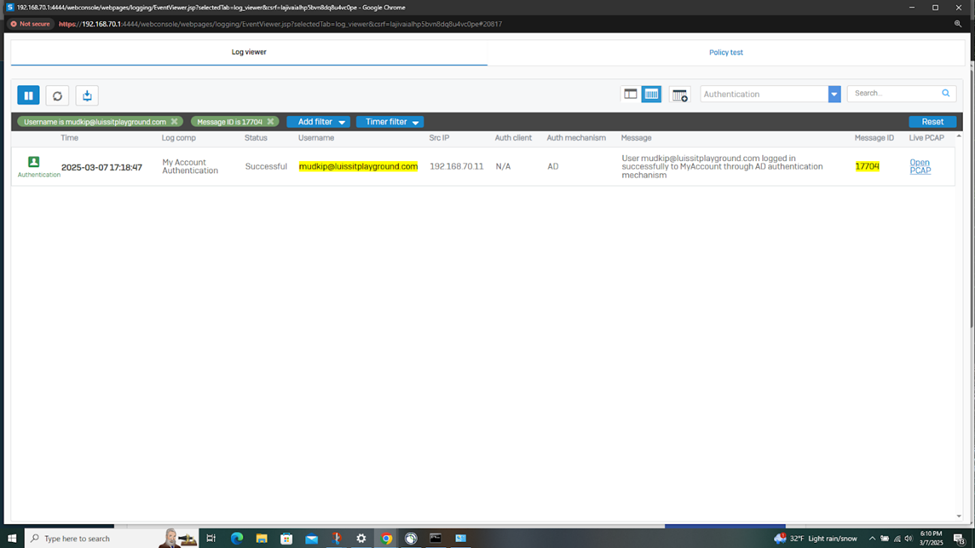
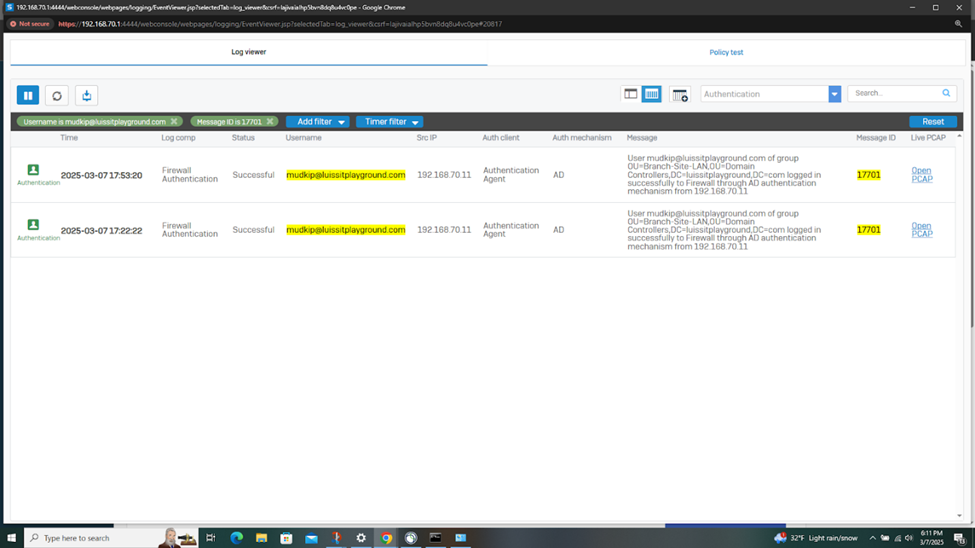
Verifying Sophos Firewall Logs for Active Directory Authentication
- At this point, the Active Directory authentication for Sophos firewall and VPN services has been complete and works as intended by installing and using the Sophos client authentication agent on domain users' computers
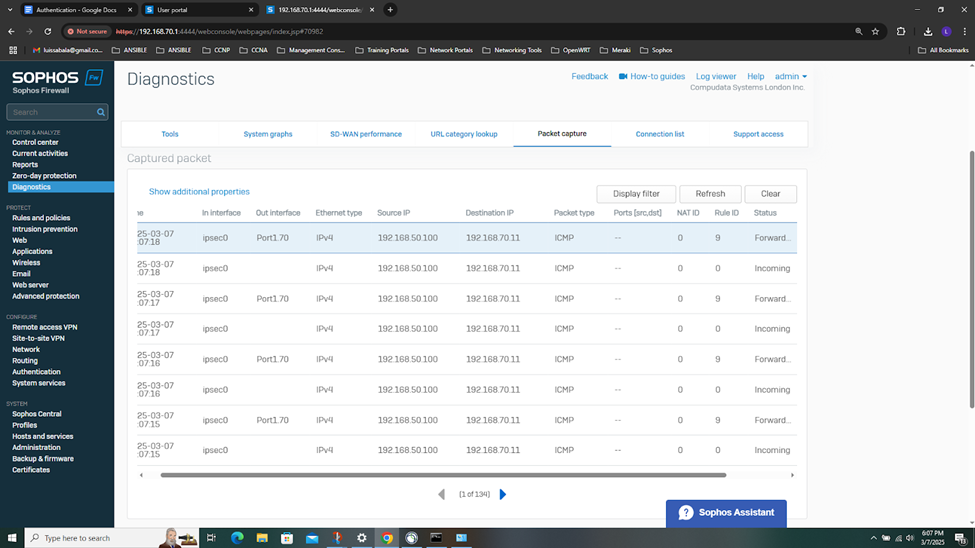
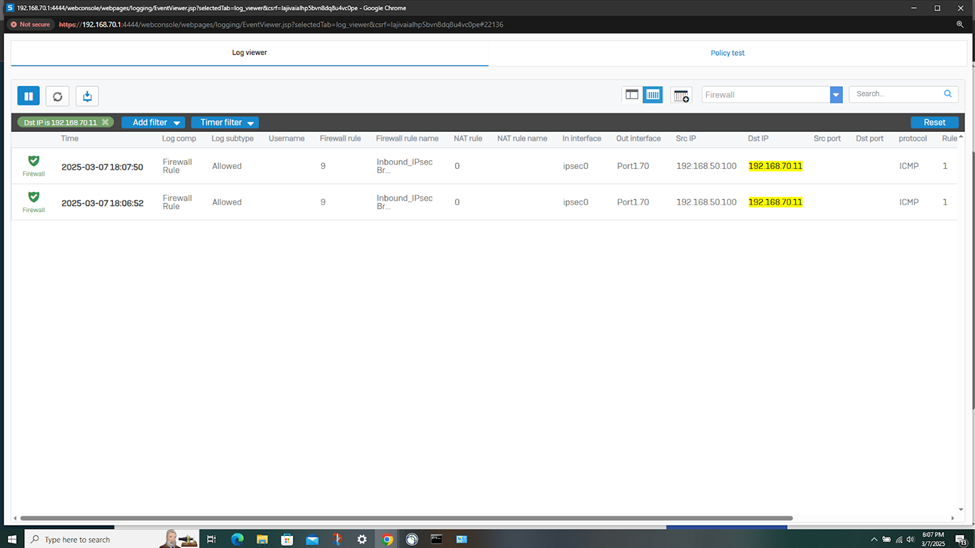
- In this demonstration, I will be taking a look into the Sophos Firewall logs for these successful attempts at accessing the services defined in the IPsec outbound and inbound firewall rules
- The Sophos Firewall logs record detailed data about network traffic, including source and destination IP addresses, ports, protocols, and the status of the traffic (allowed, blocked, or dropped). This helps administrators understand which traffic is being allowed or denied, and why
- Sometimes misconfigurations in firewall rules or network setup can cause problems. Firewall logs and packet captures provide insight into whether traffic is being blocked or not traversing through a particular device because of incorrect rules or polices, helping to pinpoint configuration issues
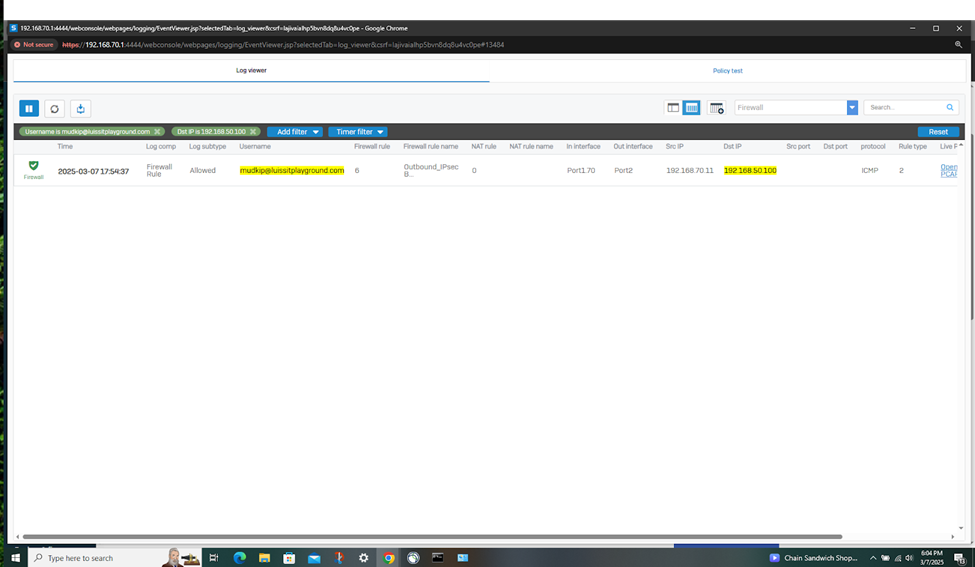
SSL VPN Authentication
- Resources
- In this lab demonstration, I have a Corporate domain user outside of the lab network using a cellular hotspot that will be utilizing the Sophos Connect client to access internal resources over the SSL VPN using Active Directory authentication
- For the entirety of this lab demonstration of the section, I will be taking a closer look into configuring the Corporate site domain user, 'Charmander' and the Sophos Firewall for SSL VPN authentication using Active Directory
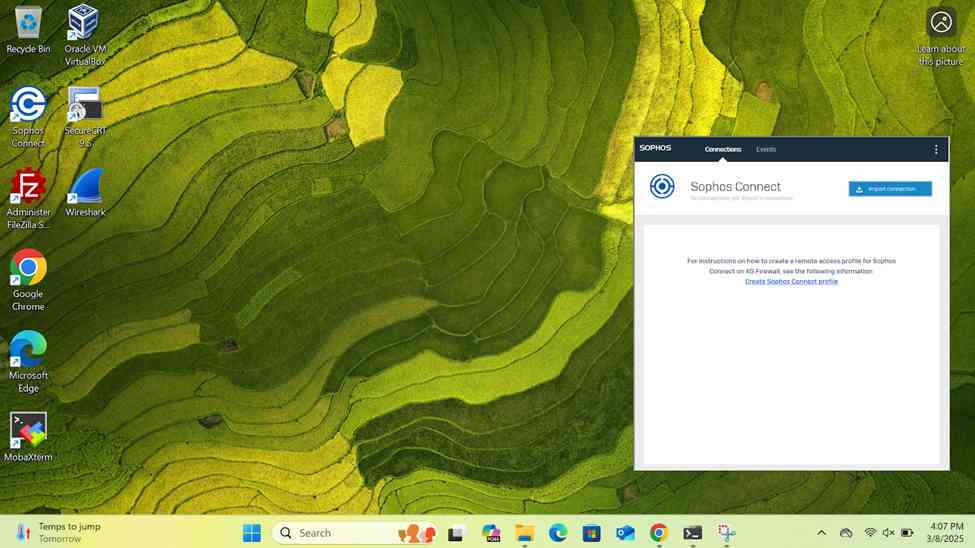
Sophos Connect Client
- The Sophos Connect client is a software application provided by Sophos to allow users to securely connect to a Sophos Firewall via SSL or IPsec VPN
- When implementing an external authentication server like Active Directory, it is often required for clients/users to download the client authentication agent, separate from the Sophos Connect client, to authenticate to the firewall for these types of services
- However, if Active Directory users are utilizing the Sophos Connect client for SSL VPN, users do not need the client authentication agent as the Sophos Connect client handles authentication directly, meaning users can connect to the VPN using their standard username and password without installing additional authentication software on their devices
SSL VPN Topology
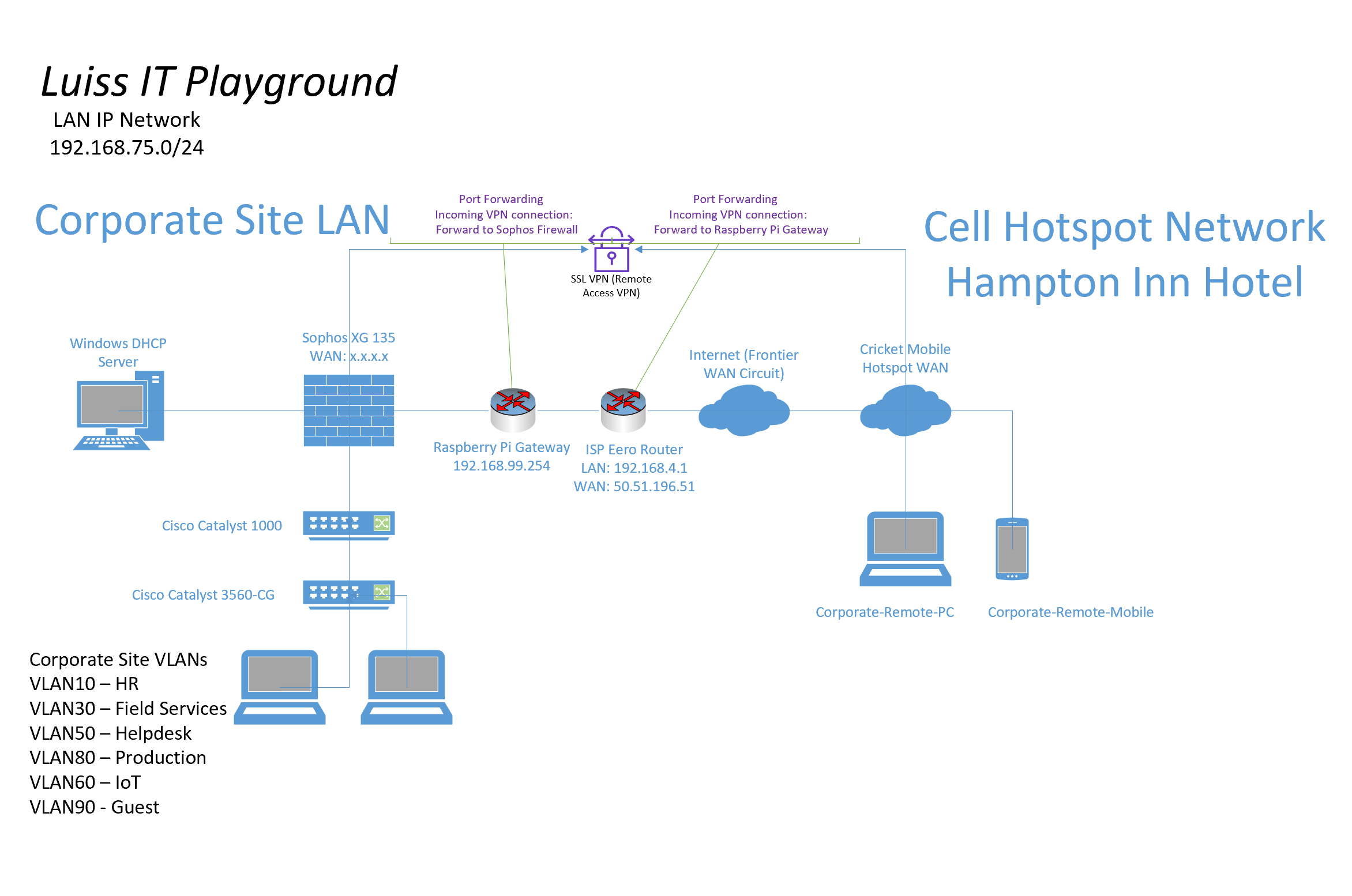
SSL VPN Authentication Configuration Overview
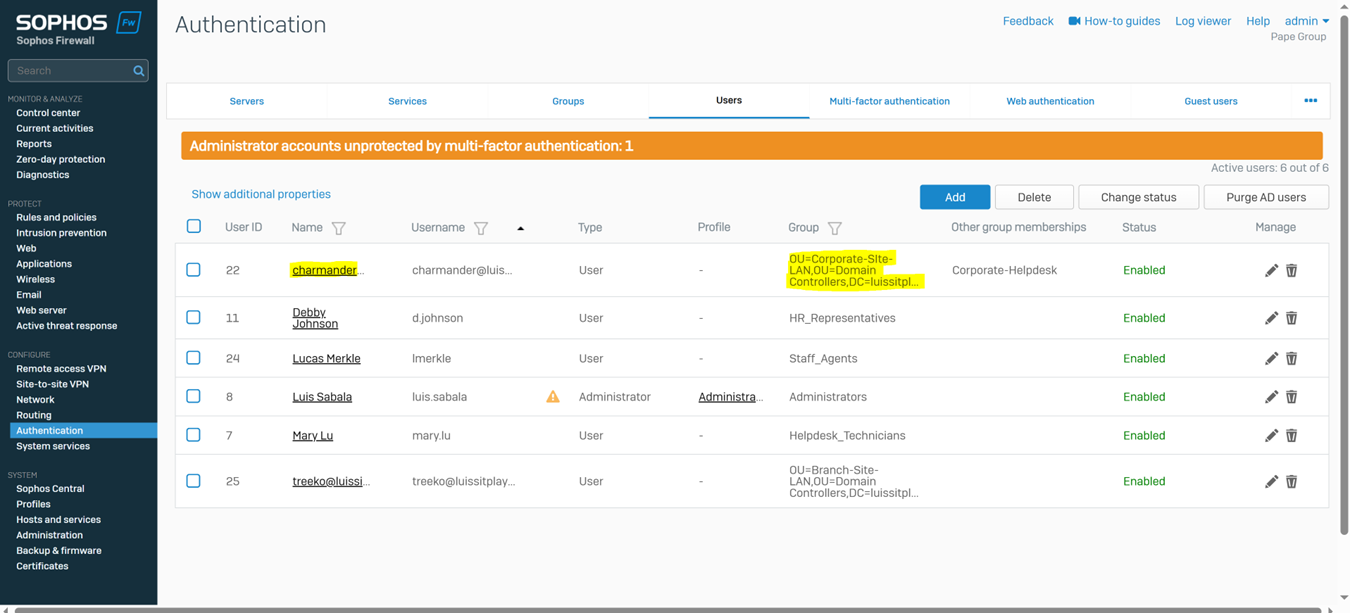
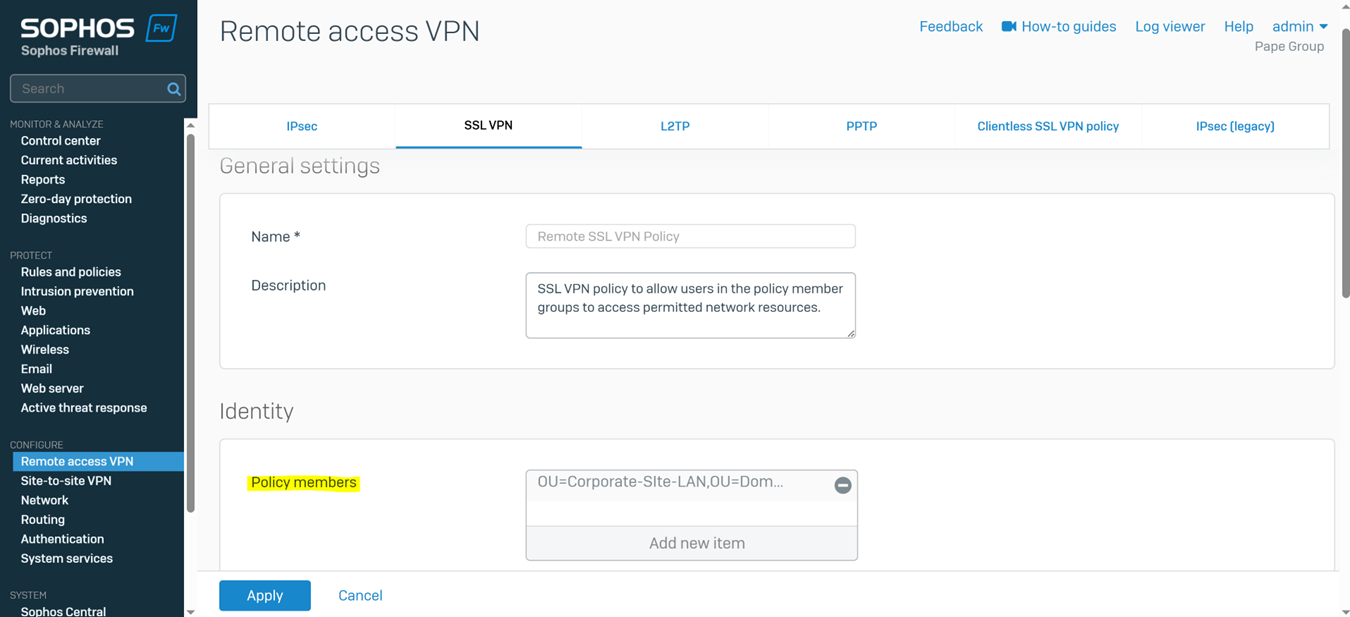
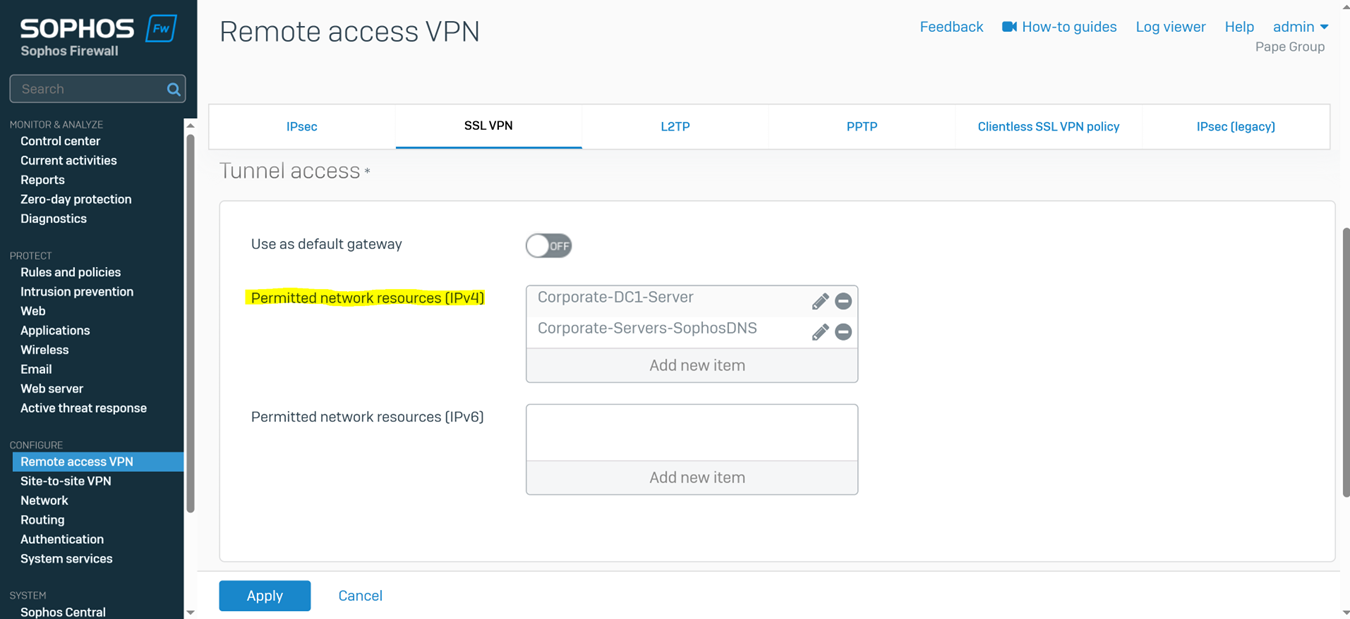
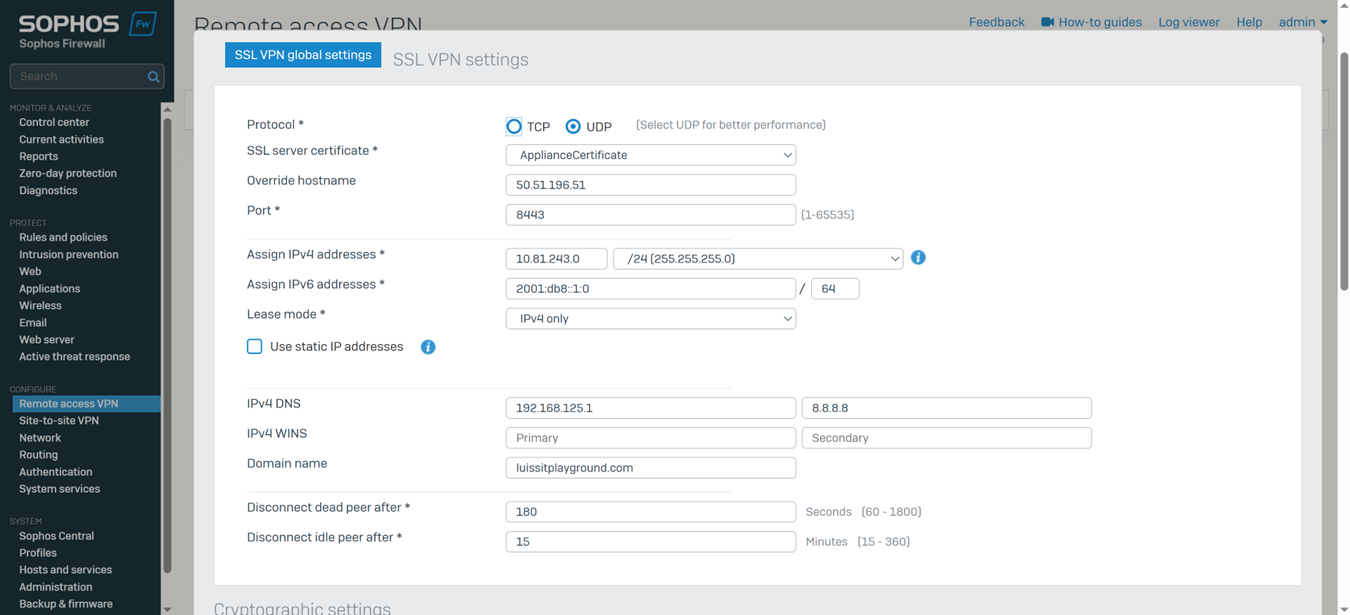
- In this demonstration, I will also be documenting the Sophos Firewall Authentication configurations including the following:
- Defined Active Directory server using LDAPs for communication
- Primary Sophos authentication methods for the 'Firewall' & 'SSL VPN' services
- Imported AD groups and users
- SSL VPN policy
- SSL VPN global settings
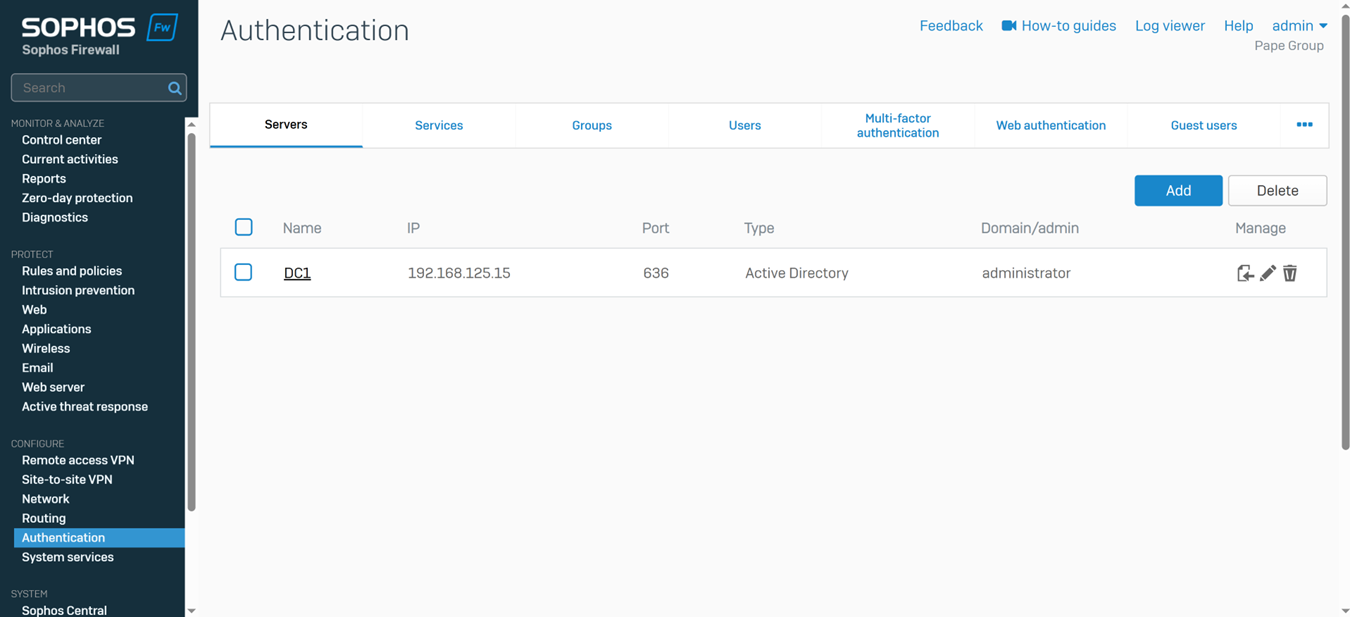
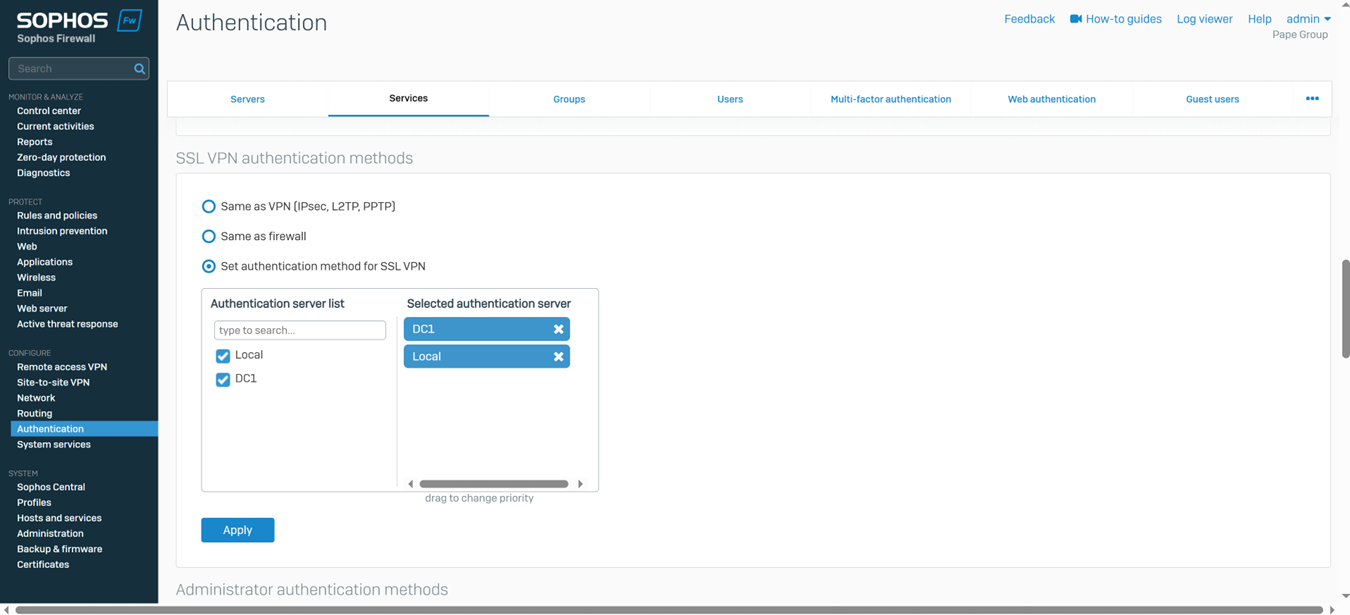
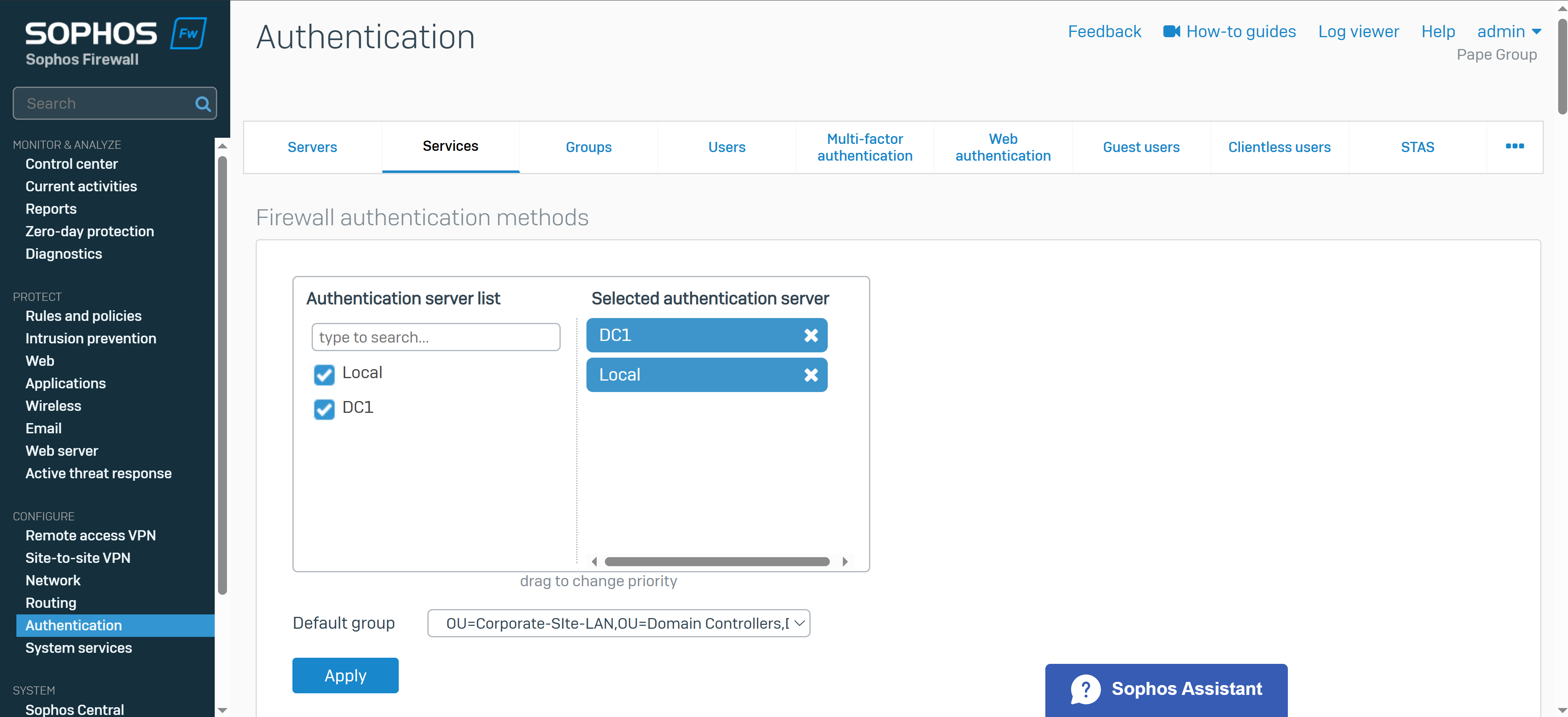
Installing Sophos Connect Client
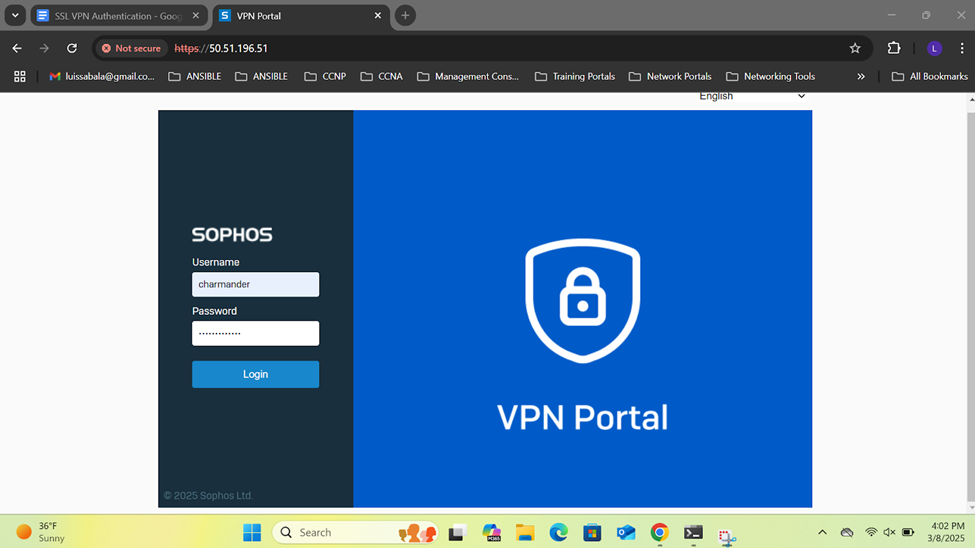
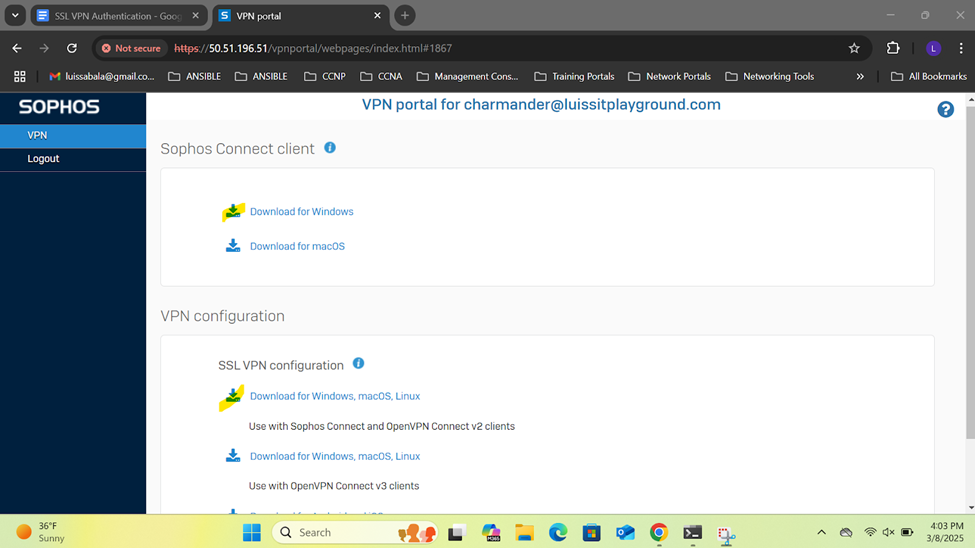
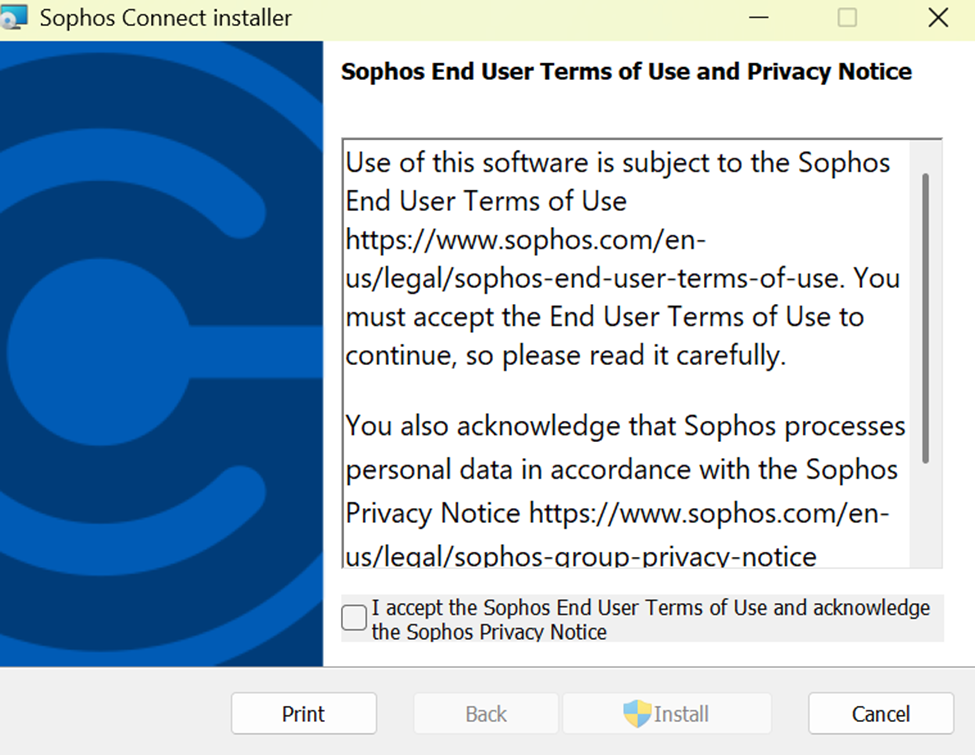
- In this demonstration, I will be installing the Sophos Connect client on the Corporate site PC for domain user 'Charmander', a helpdesk employee, to authenticate to the Corporate Sophos firewall to eventually access internal resources located at the Corporate site location via the SSL remote access VPN
- The Sophos Connect client and '.ovpn' configuration file can be installed by having the user access the Sophos VPN portal via either the 'LAN or WAN' zones or distributed by an administrator directly
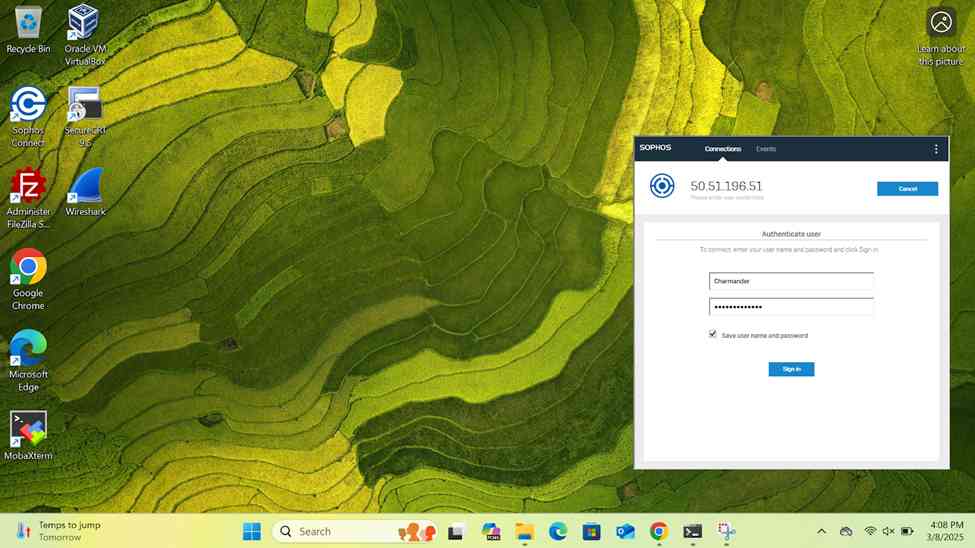
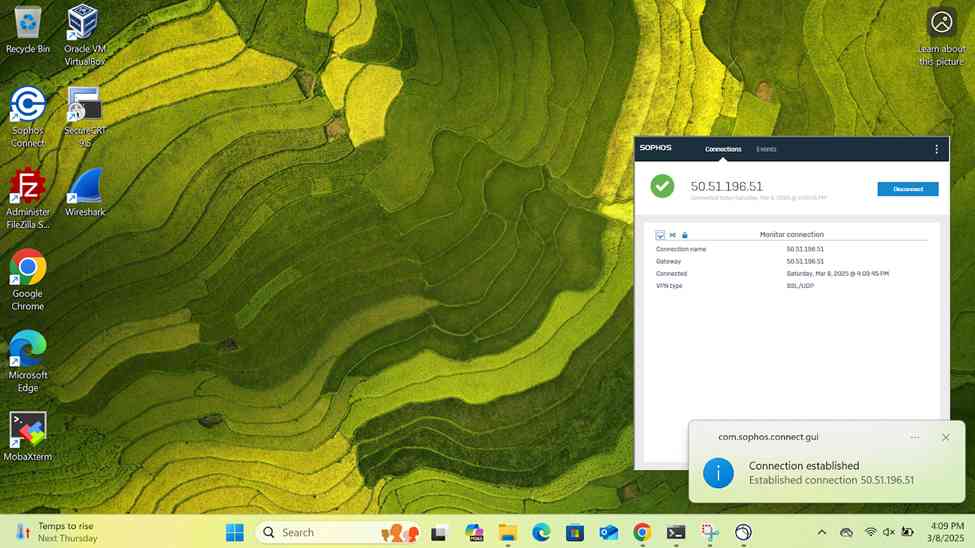
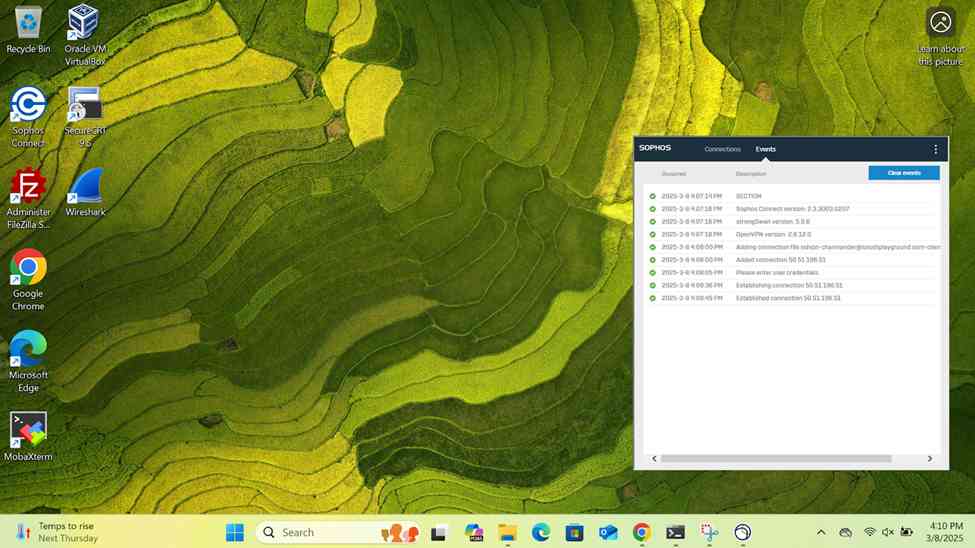
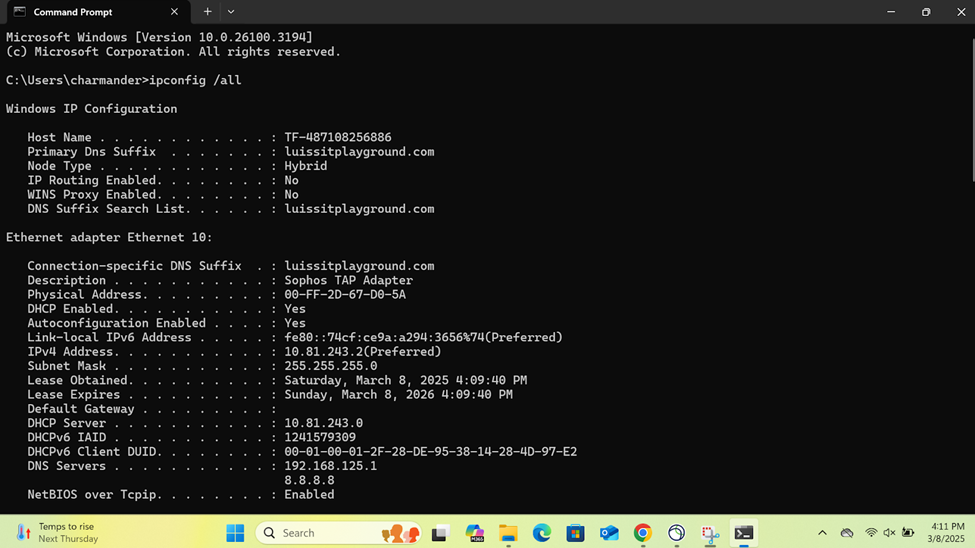
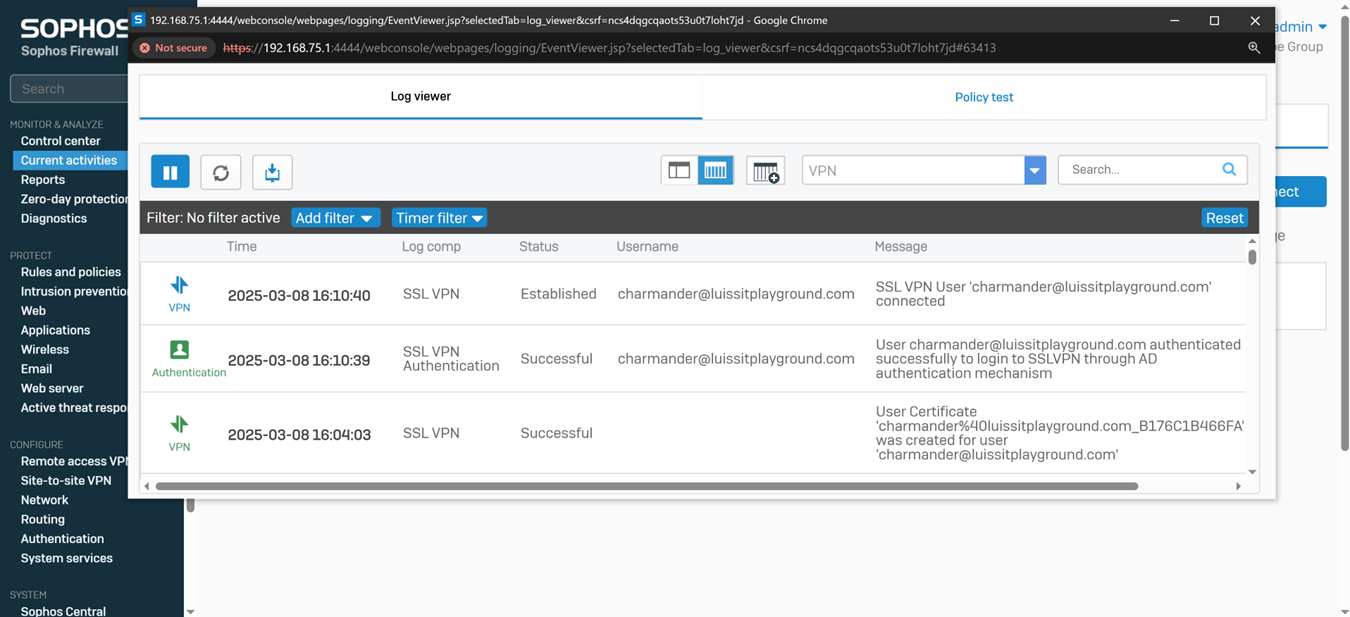
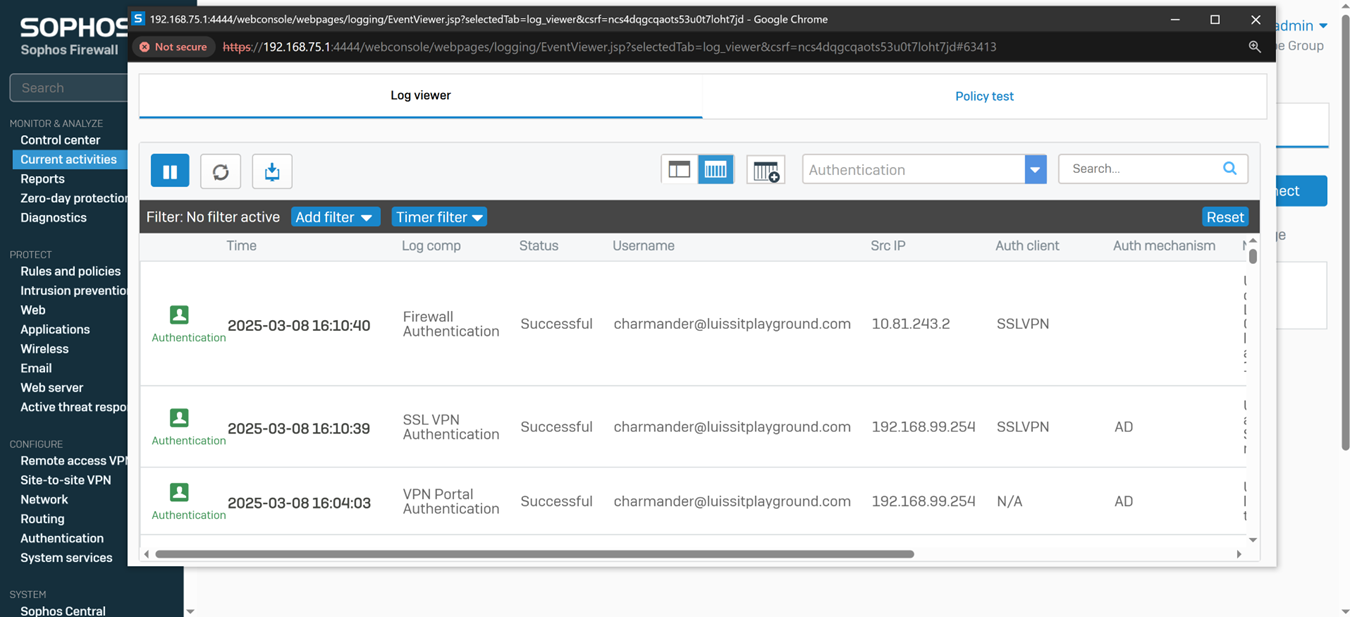
Verifying Sophos SSL VPN Authentication Logs & Firewall Rules
- In this demonstration, I will be verifying the Sophos SSL VPN authentication logs to confirm the successful SSL VPN authentication using a domain user's Active Directory login credentials (Charmander) via the Sophos Connect client
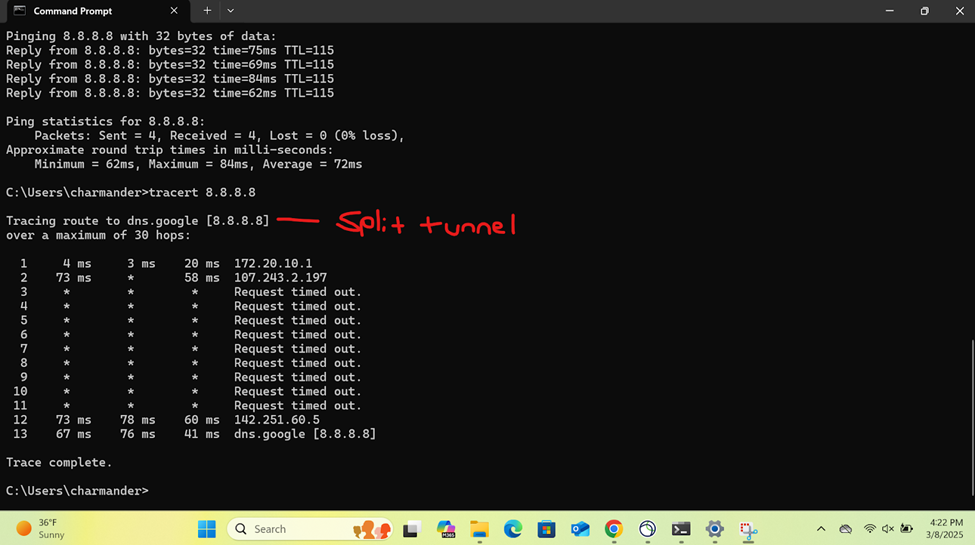
- In this demonstration, I will be demonstrating the split-tunnel SSL VPN Firewall rule that will dictate what internal access to the Corporate LAN the authenticated Corporate site domain users have via the SSL remote access VPN
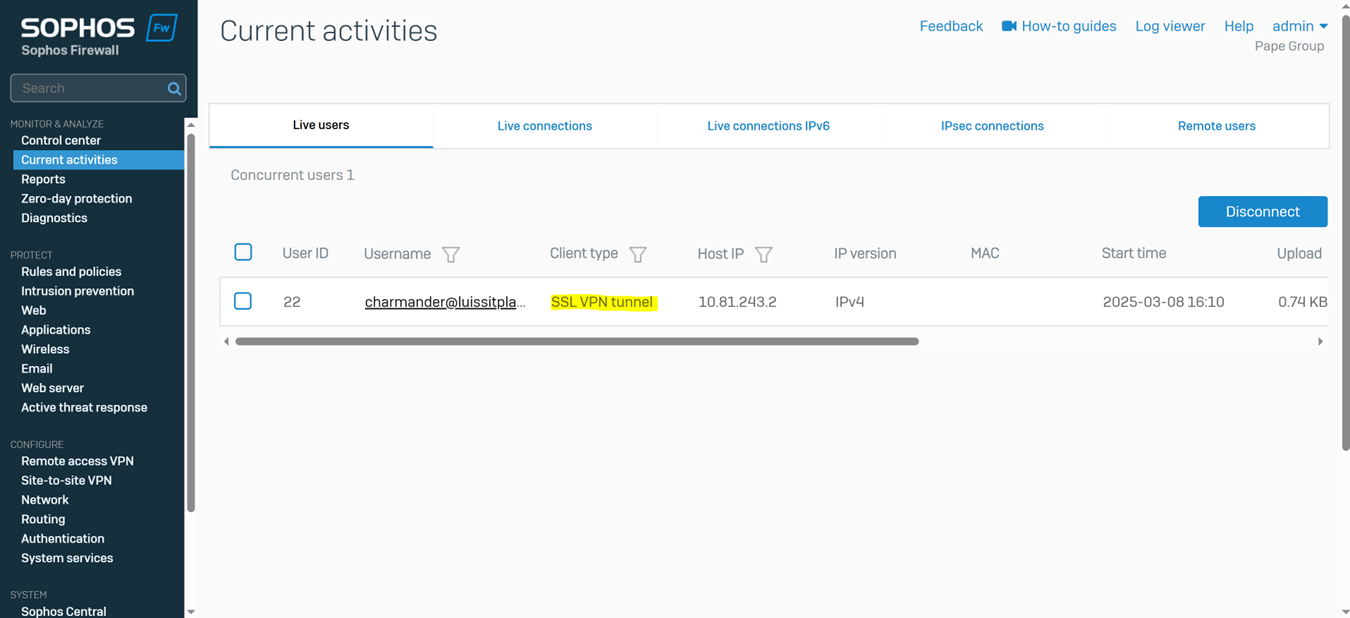
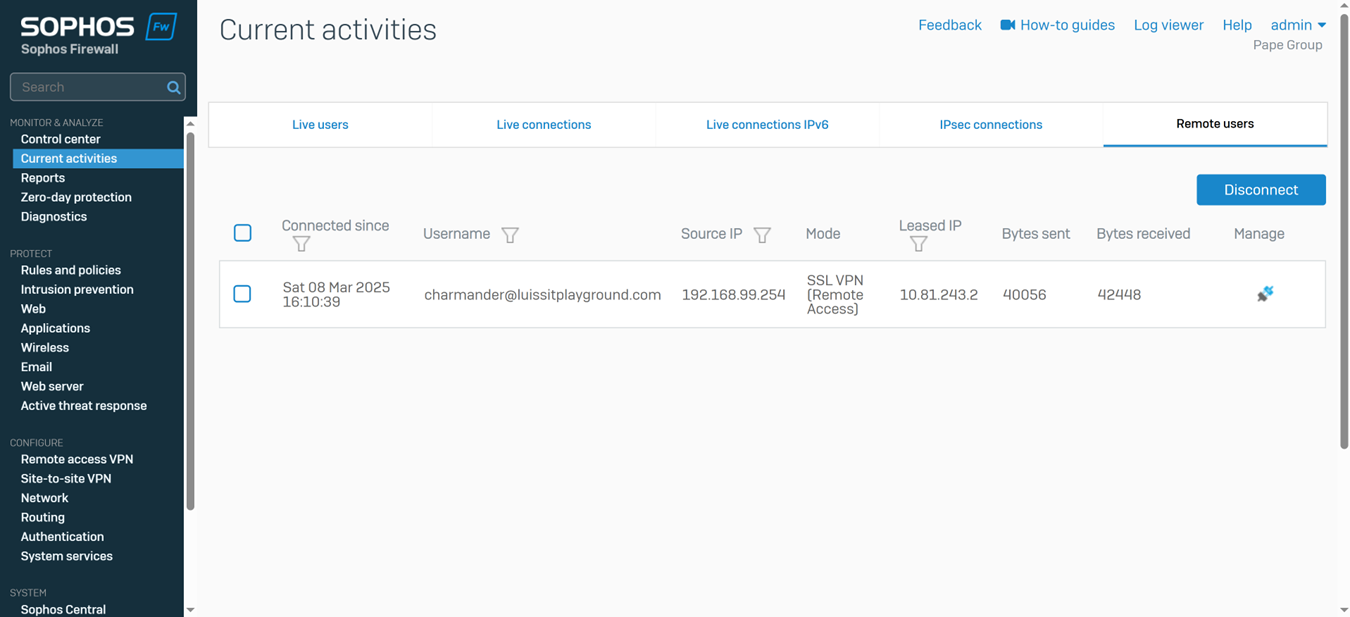
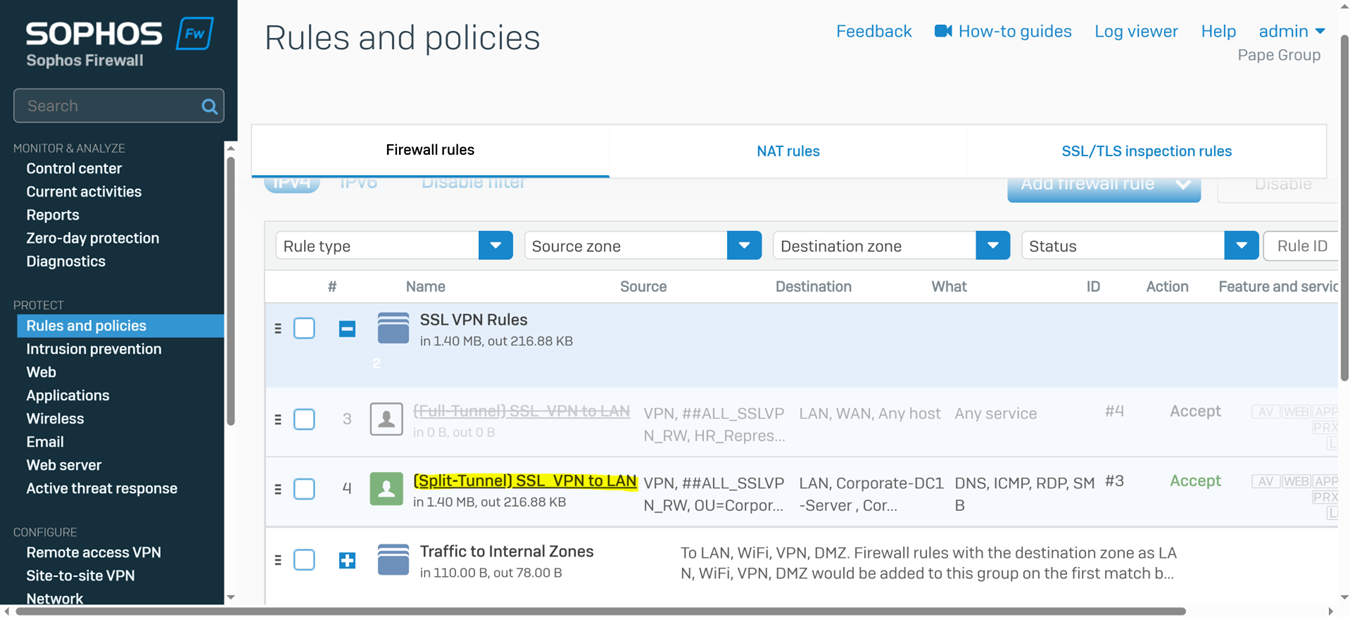
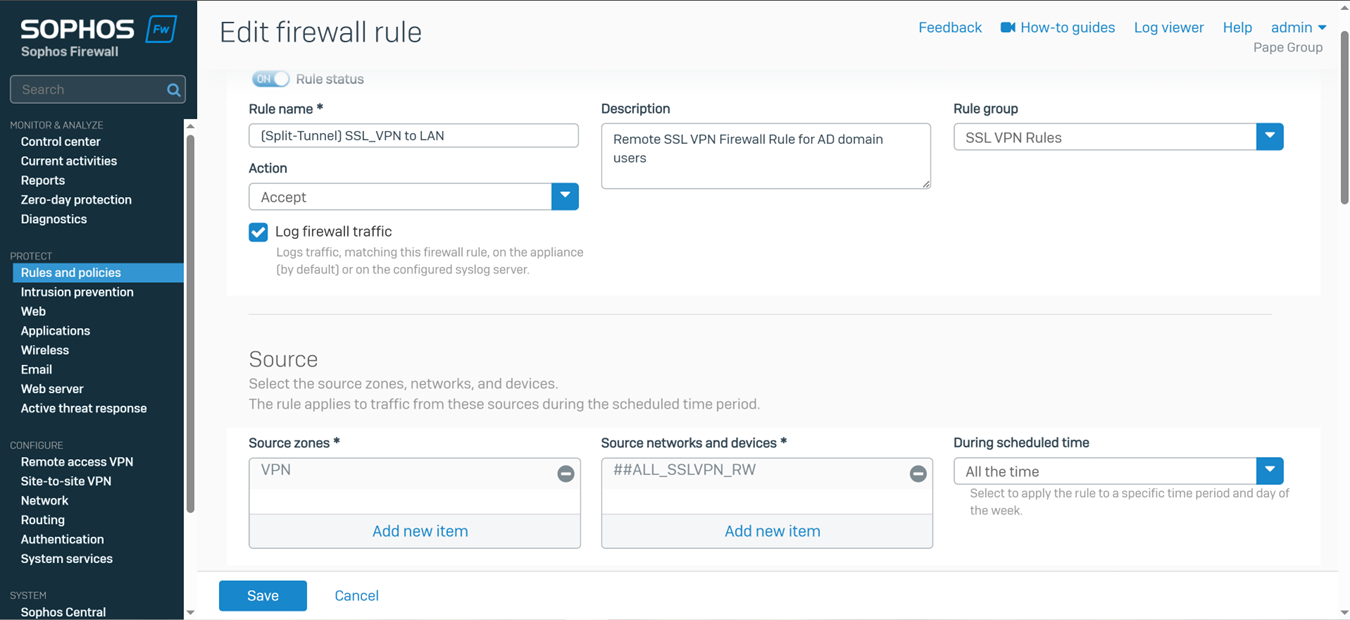
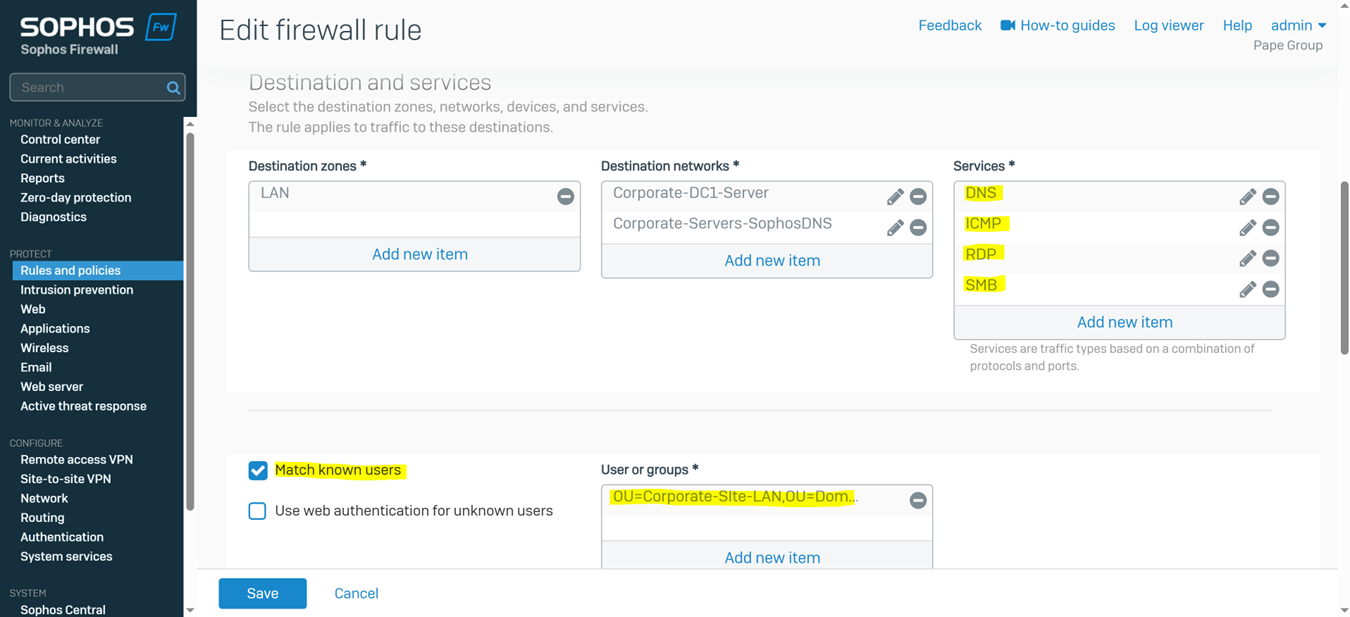
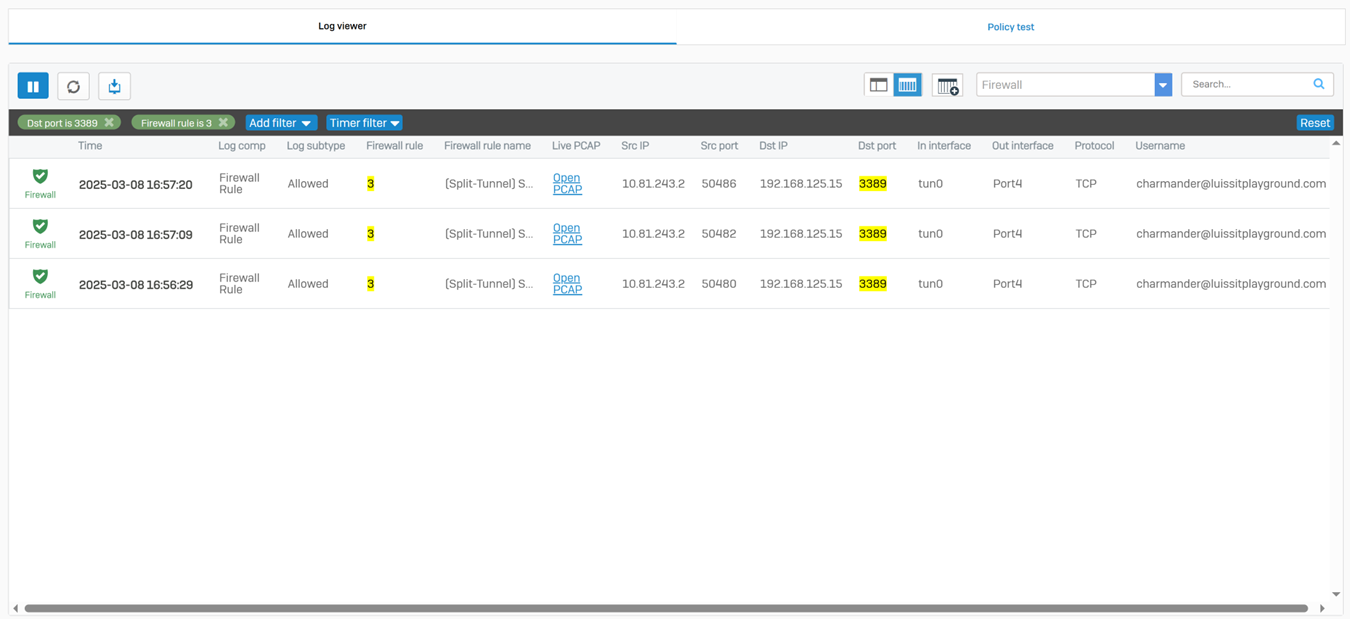
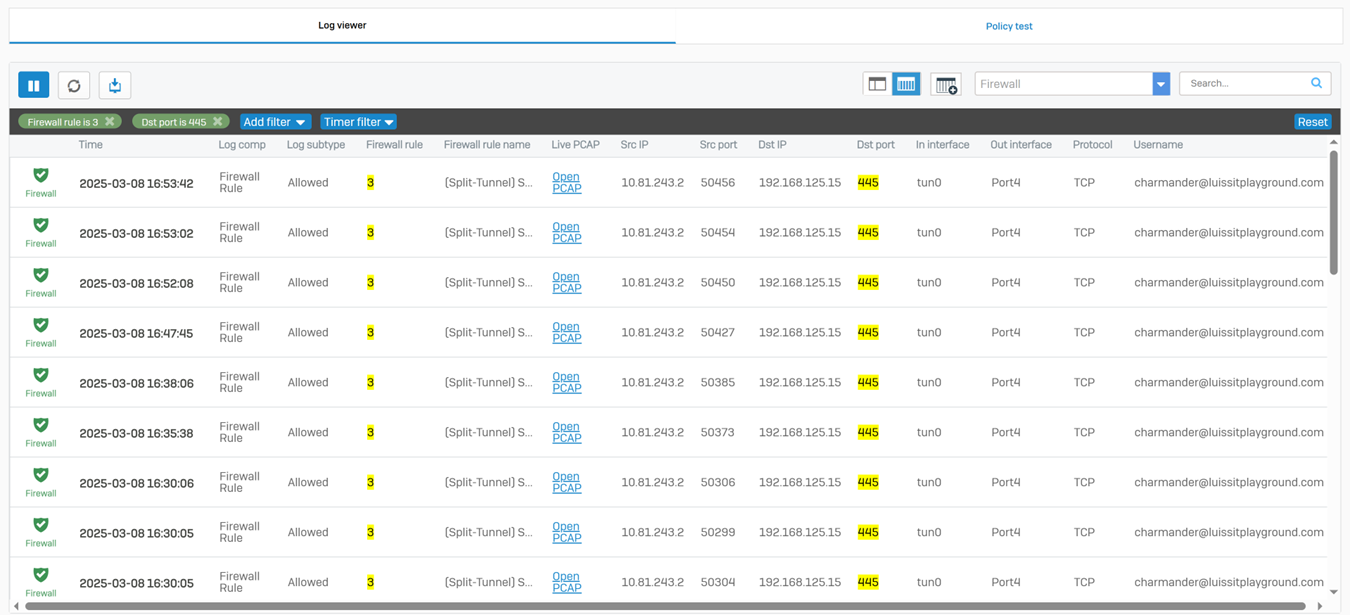
Testing SSL VPN Firewall Rule via Active Directory Authentication
- In this demonstration, I will be testing the SSL VPN firewall rule by accessing the services defined in the rule
- In this demonstration, I perform various tests from the Corporate site authenticated AD user 'Charmander'
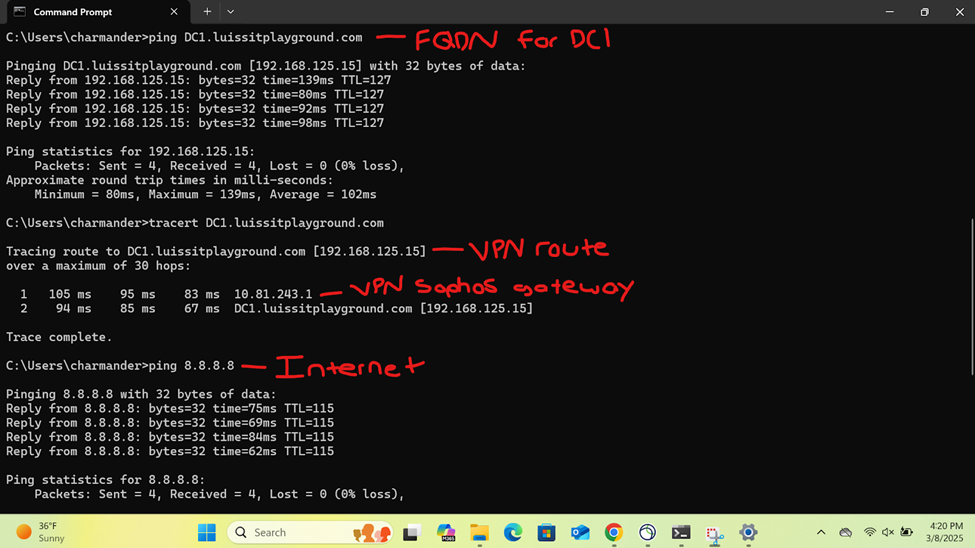
- Pinging the internal Sophos firewall interface in the Corporate site including the DC1 Windows server providing Active Directory & RDP services
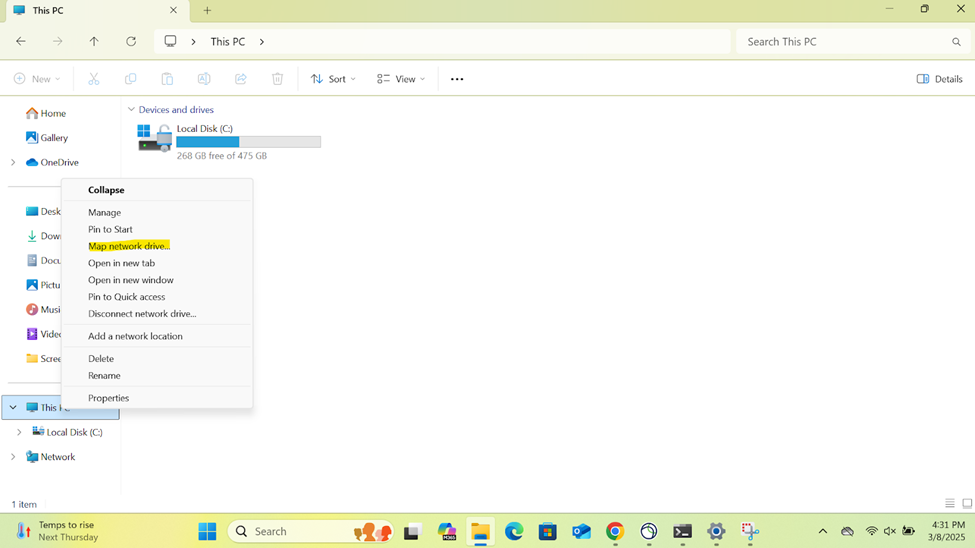
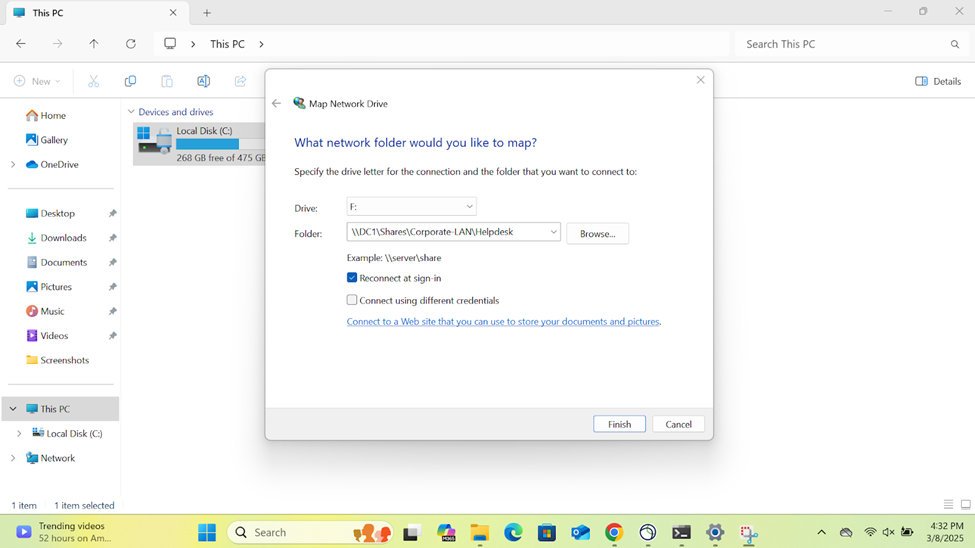
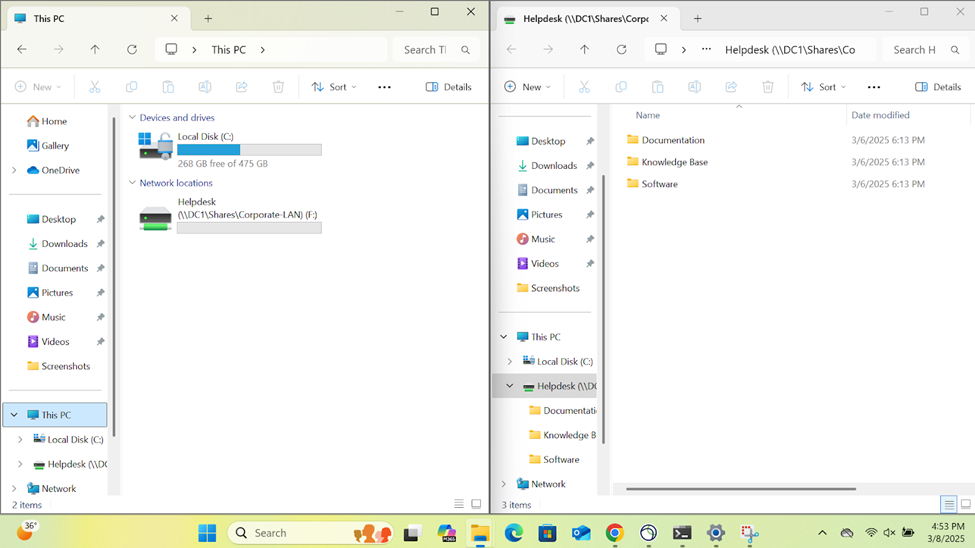
- Connecting to an accessible network share from the Windows DC1 server over the SSL VPN
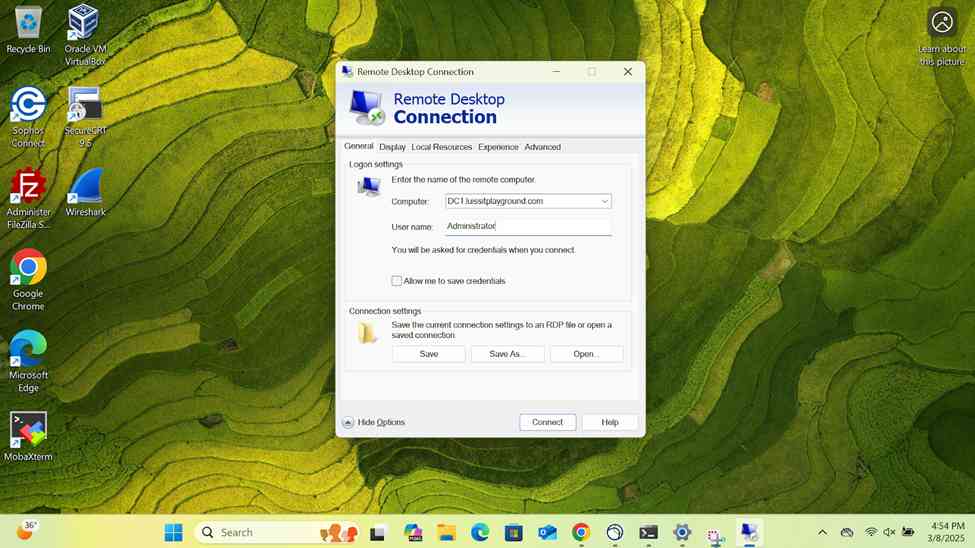
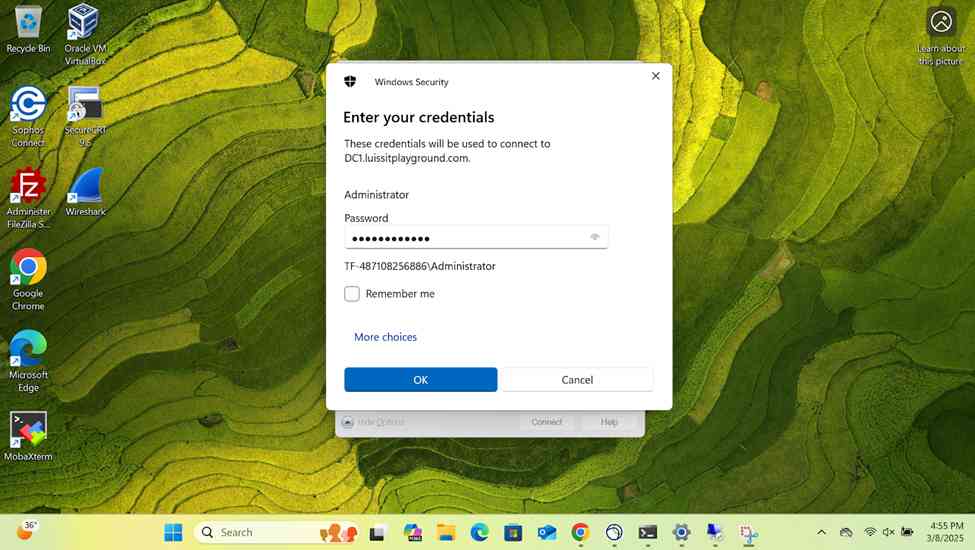
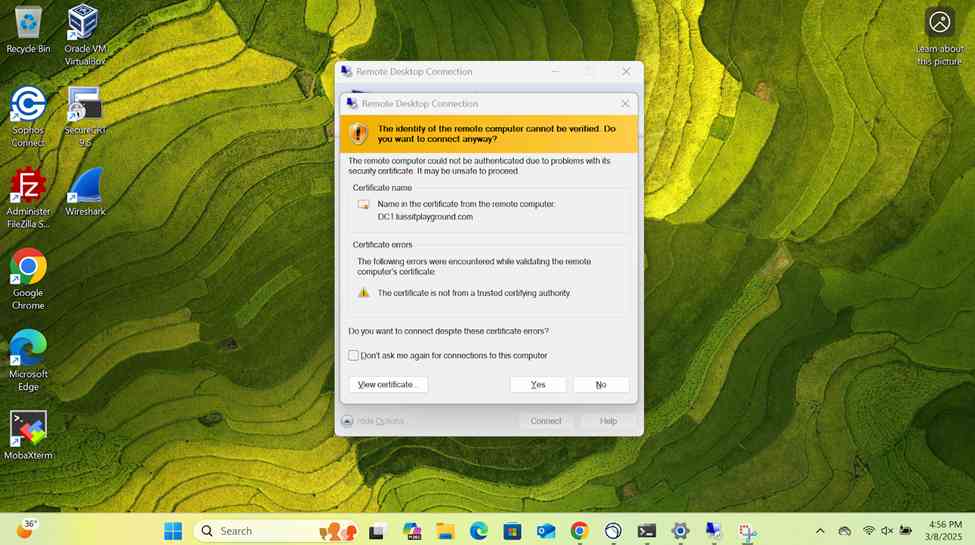
- Establish an RDP connection to the Windows DC1 server located at the Corporate site LAN over the SSL VPN
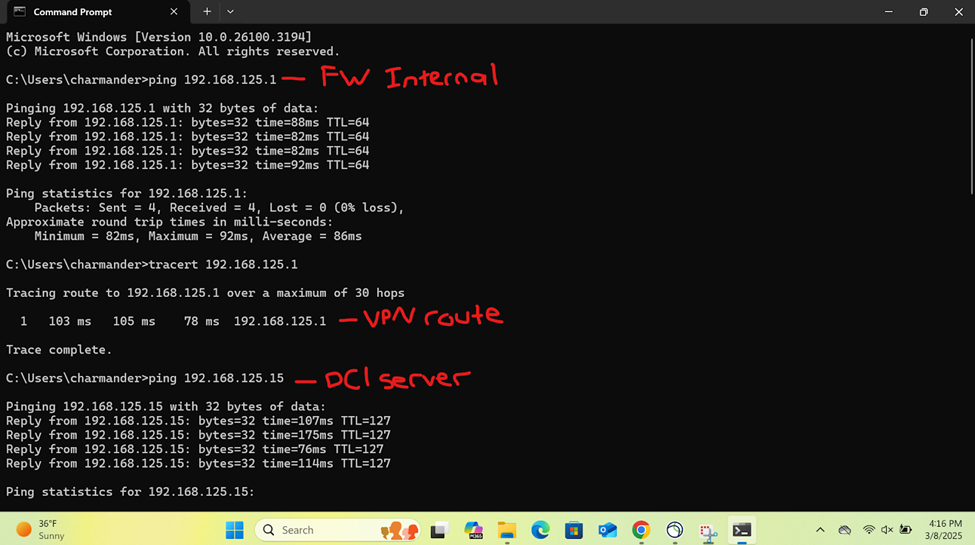
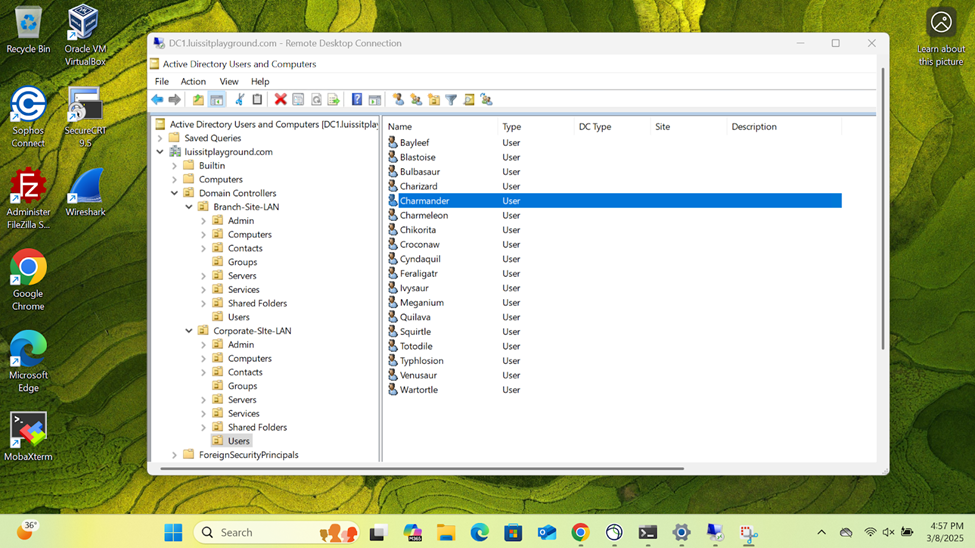
Verifying Sophos Firewall Logs for Allowed Traffic via AD Authentication
- At this point, the Active Directory authentication for Sophos firewall and SSL VPN services has been complete and works as intended by installing and using the Sophos Connect client on domain users' computers
- In this demonstration, I will be taking a look into the Sophos Firewall logs for these successful attempts at accessing the services defined in the SSL VPN firewall rule