Authentication Overview
Sections:
- Multi-factor Authentication Overview
- Web Authentication Overview
- Guest & Clientless Users
- Authentication Client Download Overview
Resources:
- Sophos Authentication Servers
- Sophos Authentication Services
- Sophos Authentication Groups
- Sophos Authentication Users
- Sophos MFA
- Sophos Web Authentication
- Sophos Authentication Guest Users
- Sophos Guest User Settings
- Sophos Authentication Clientless Users
- Sophos Authentication Client Download
Overview:
- With Sophos Firewall, you can set up authentication using an internal user database or implementing an external authentication server. To authenticate themselves, users must have access to an authentication client
- Sophos Firewall also supports clientless authentication, in which devices can bypass the authentication client
- In addition to internal and external authentication services, the Sophos Firewall also supports multi-factor authentication, transparent authentication, and guest user access through a captive portal
- In this section, I will go over the different types of authentication services more in depth before setting up a lab exercise in later sections
Authentication Server Overview
Overview
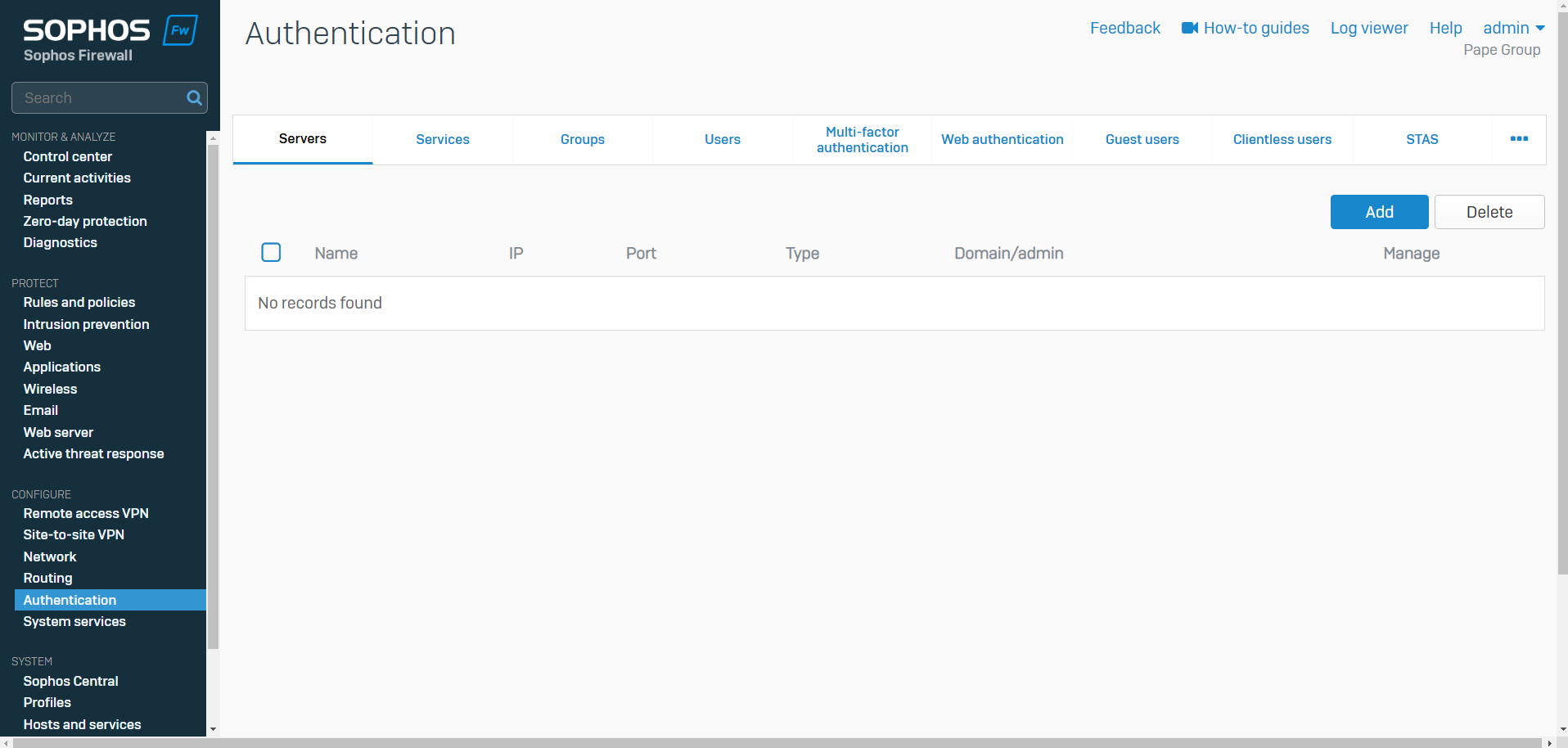
- Authentication servers are specialized servers that handle the process of verifying the identity of users, devices, or applications attempting to access a system, network, or service. They manage the authentication process, which typically involves verifying credentials (such as passwords, biometrics, or tokens) to ensure that users and devices are authorized to access specific resources
- The authentication 'Servers' tab in the Sophos Firewall web admin interface gives administrators the ability to define external servers used to authenticate users attempting to access the firewall and associated services
- When you add an authentication server, you define an external server and provide settings for managing access to it
Authentication Server Types
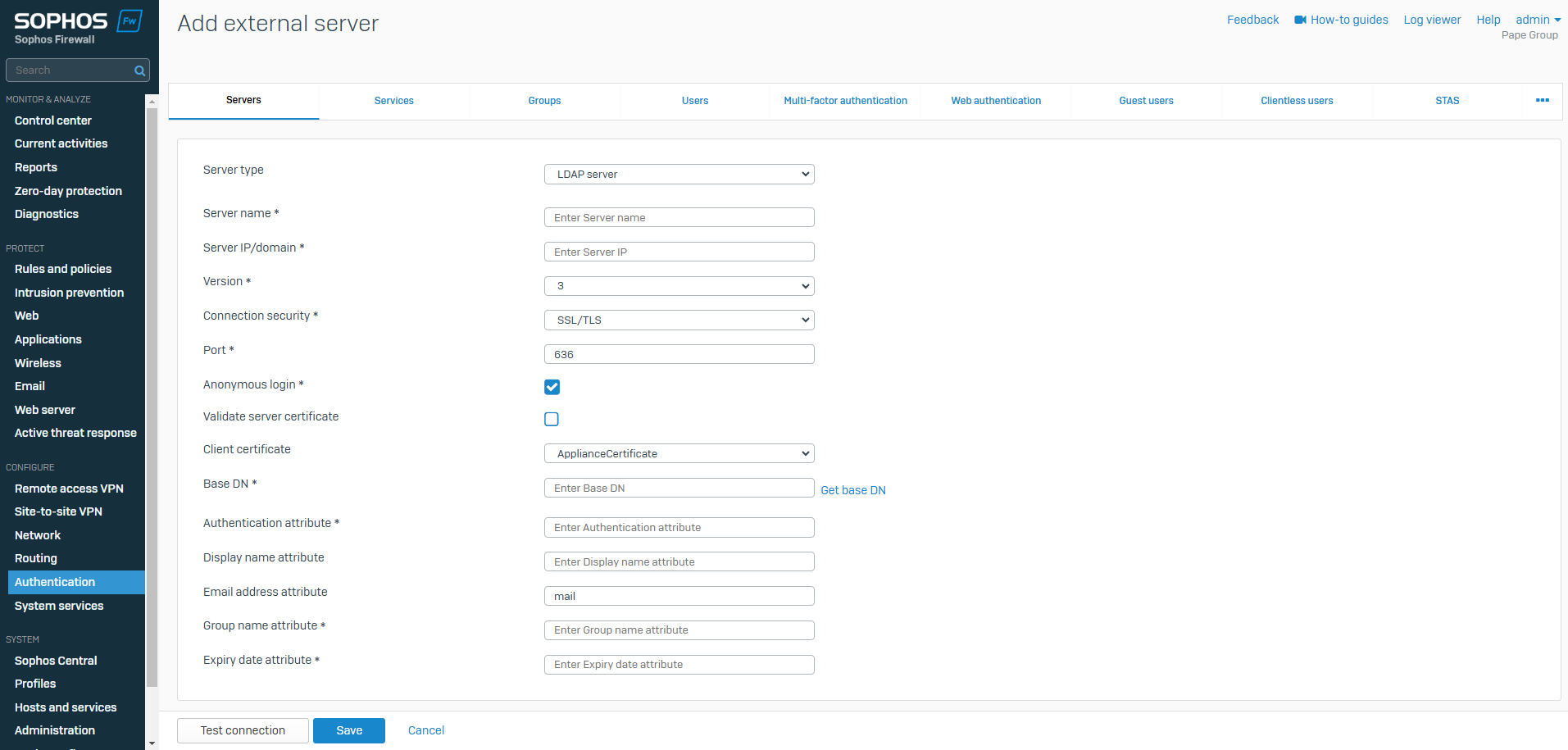
LDAP Server
- Resource: Add an LDAP Server
- Lightweight Directory Access Protocol is a networking protocol for querying and modifying directory services based on the x.500 standard
- The Sophos Firewall uses the LDAP protocol to authenticate users for several services, allowing or denying access based on attributes or group memberships
- The Sophos Firewall also supports LDAPS/SLDAP (LDAP Secure or Secure LDAP) over SSL or TLS
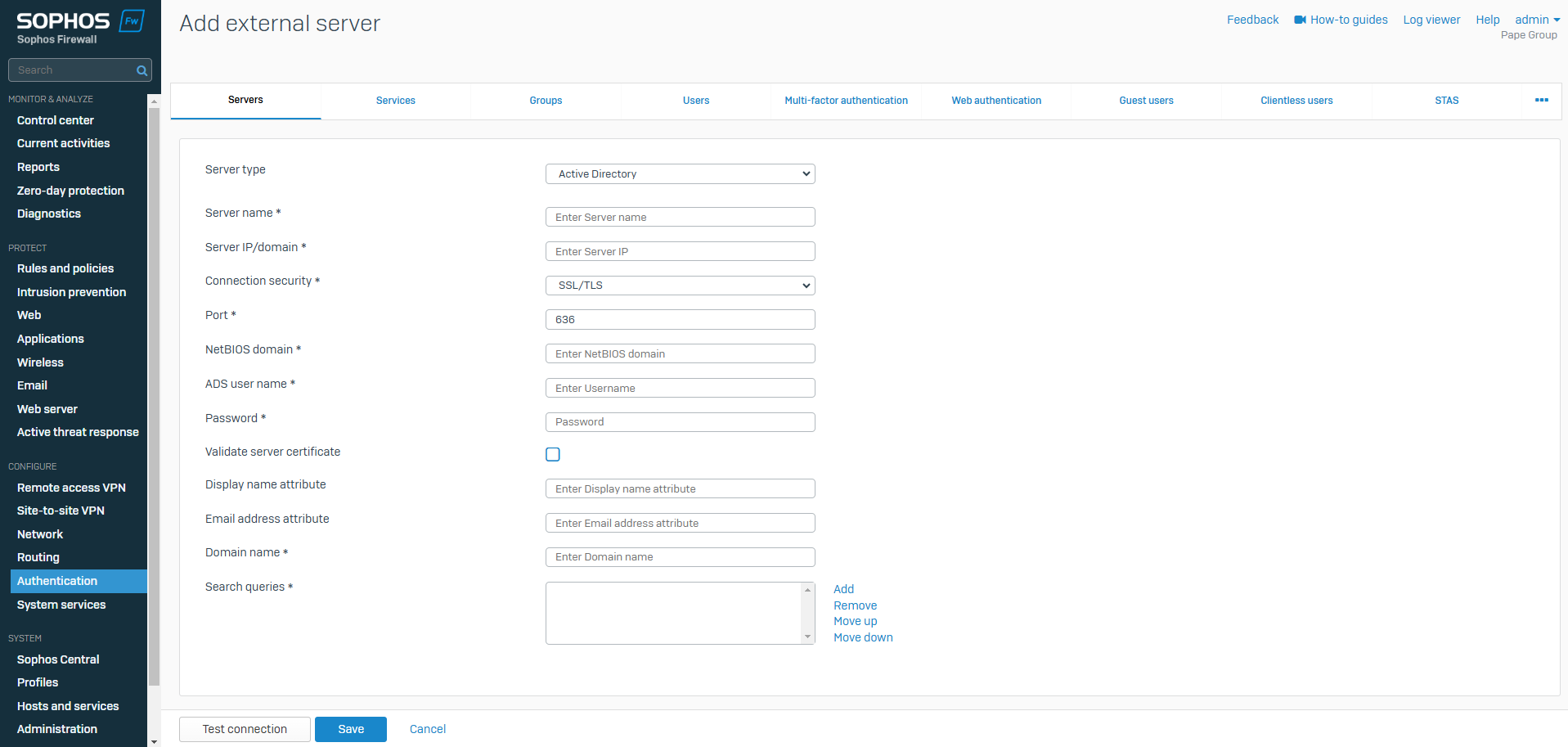
Active Directory Server
- Resource: Add an Active Directory Server
- Active Directory is a directory service developed by Microsoft to manage and organize networked resources in a centralized manner. It allows administrators to manage users, groups, devices, and other resources within an organization's network
- Using Microsoft Active Directory, you can register the firewall as a Windows domain and create an object for it on the primary domain controller
- The Sophos Firewall can then query user and resource information on the Windows domain network
- When users sign in for the first time through Active Directory credentials, they're added to authentication groups on the Sophos Firewall automatically
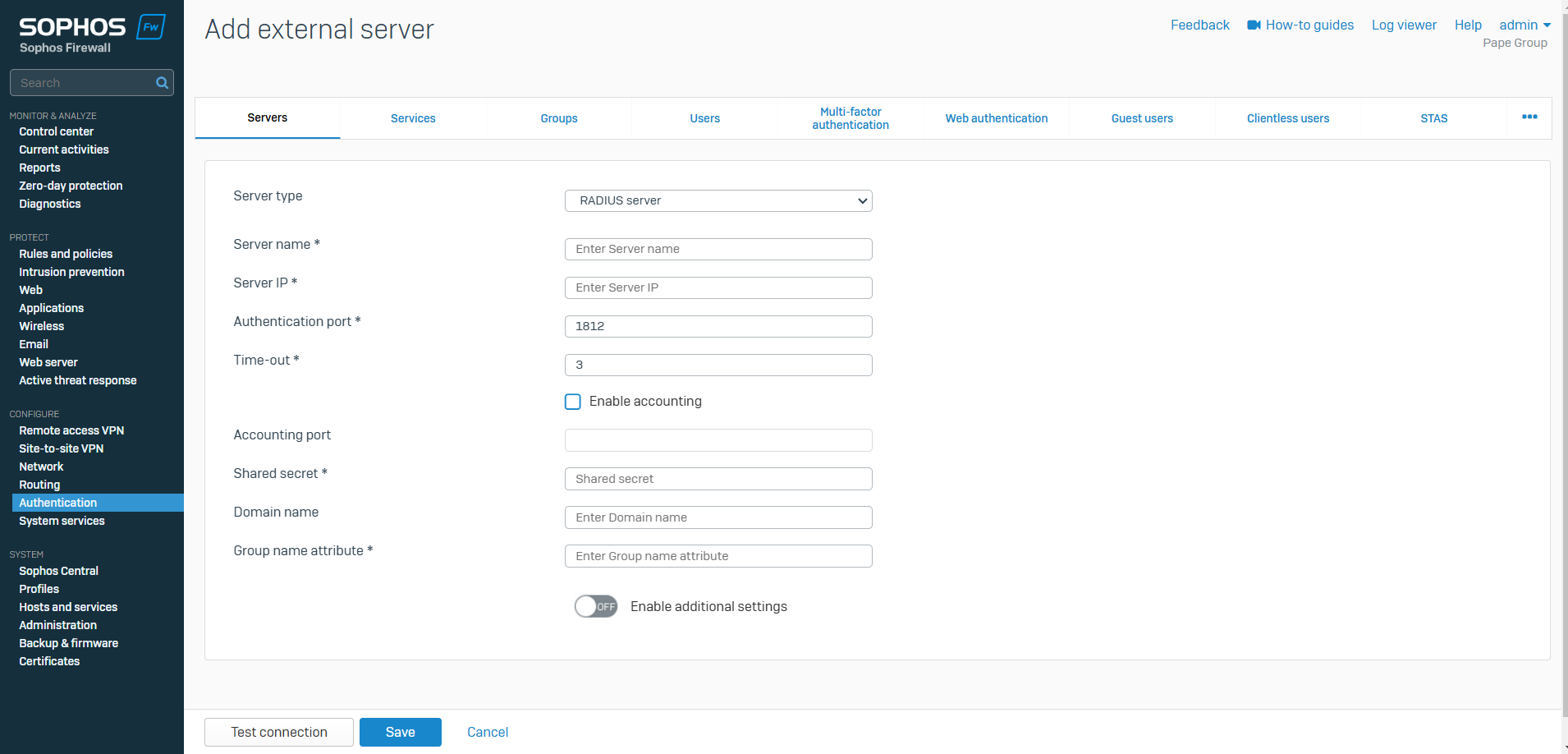
RADIUS Server
- Resource: Add a RADIUS Server
- RADIUS a networking protocol that provides centralized authentication, authorization, and accounting (AAA) services for users who connect to a network. It is commonly used to manage access to networks, including VPNs and wireless networks
- Passwords are encrypted using the RADIUS secret. Authorization to access a service is granted when a request matches a group of attributes, such as the IP address of the requesting client. Authentication and authorization data are stored in user profiles
- RADIUS Functions
- Authentication
- The RADIUS server verifies the identity of a user or device trying to connect to the network
- This is typically done by checking the provided credentials (username/password, digital certificates, etc.) against a central database
- Authorization
- Once the user is authenticated, the RADIUS server determines what level of access the user has
- It can assign policies that specify which resources the user is allowed to access (certain networks, applications, services, etc.)
- Accounting
- RADIUS servers also track user activities, such as login time, duration of the session, and amount of data transferred
- This information can be used for auditing, billing, or monitoring purposes
- Authentication
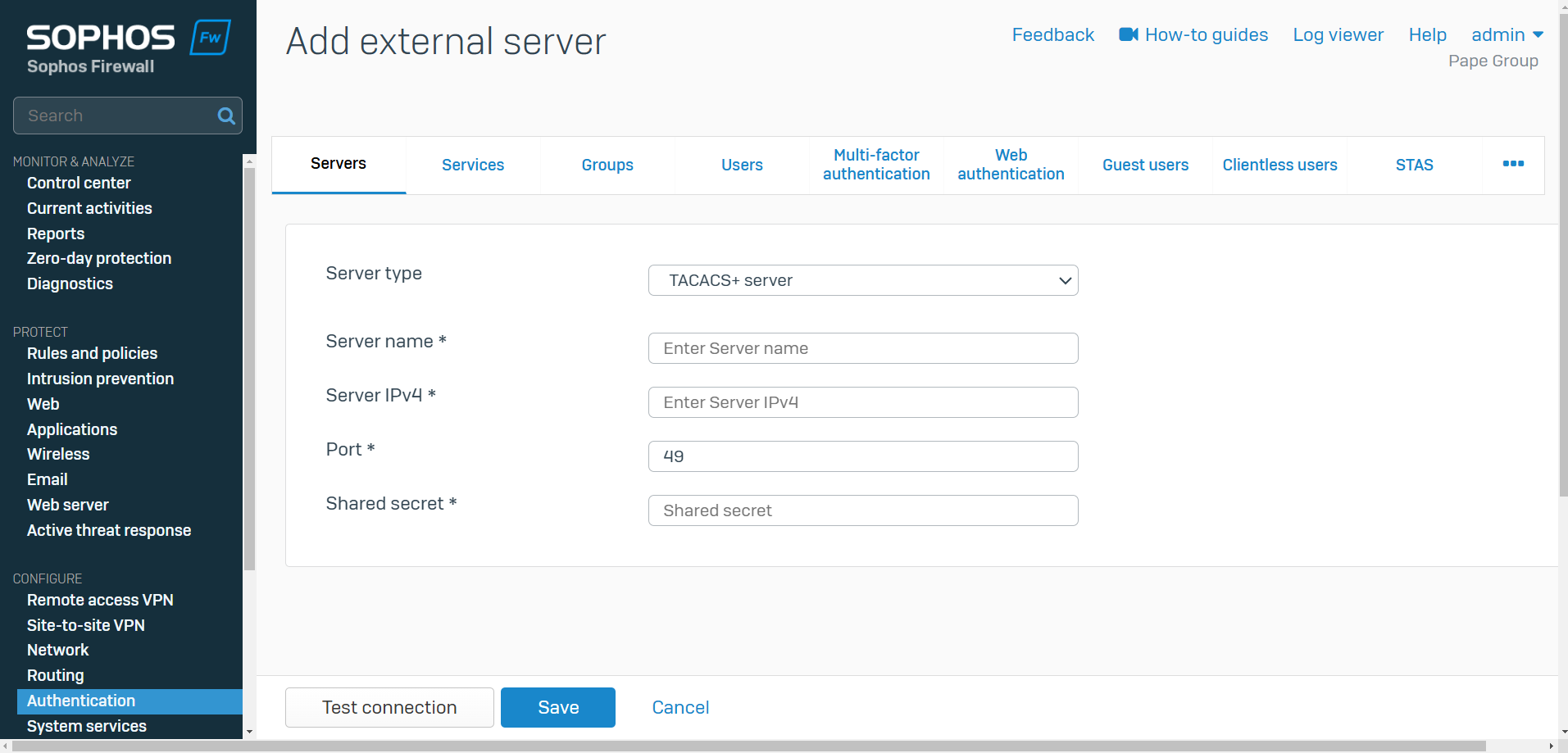
TACACS+ Server
- Resource: Add a TACACS+ Server
- TACACS+ is a proprietary protocol offered by Cisco and provides detailed accounting information and administrative control over authentication and authorization processes
- TACACS+ is commonly used for device management, especially in enterprise environments for controlling access to network devices such as routers, switches, firewalls, and other infrastructure devices
- TACACS+ Features
- Authentication
- User Verification
- TACACS+ helps verify the identity of users who are attempting to access network devices
- This is typically done by checking credentials (username/password, or other factors) against a central server
- Supports Multiple Authentication Methods
- TACACS+ can integrate with various authentication sources such as Active Directory, RADIUS, or a local database
- User Verification
- Authorization
- Access Control
- Once authenticated, TACACS+ determines what level of access a user has on the network device
- It controls whether a user can perform certain commands or access specific configurations
- Granular Control
- TACACS+ allows administrators to define specific privileges for different user roles, helping enforce the principle of least privilege
- Access Control
- Accounting
- Activity Logging
- TACACS+ tracks the actions performed by users on network devices, including commands issues, configuration changes made, and session duration
- Auditing
- This information is stored and can be used for auditing, monitoring, and troubleshooting purposes. It also helps in ensuring compliance with internal and external security policies
- Activity Logging
- Authentication
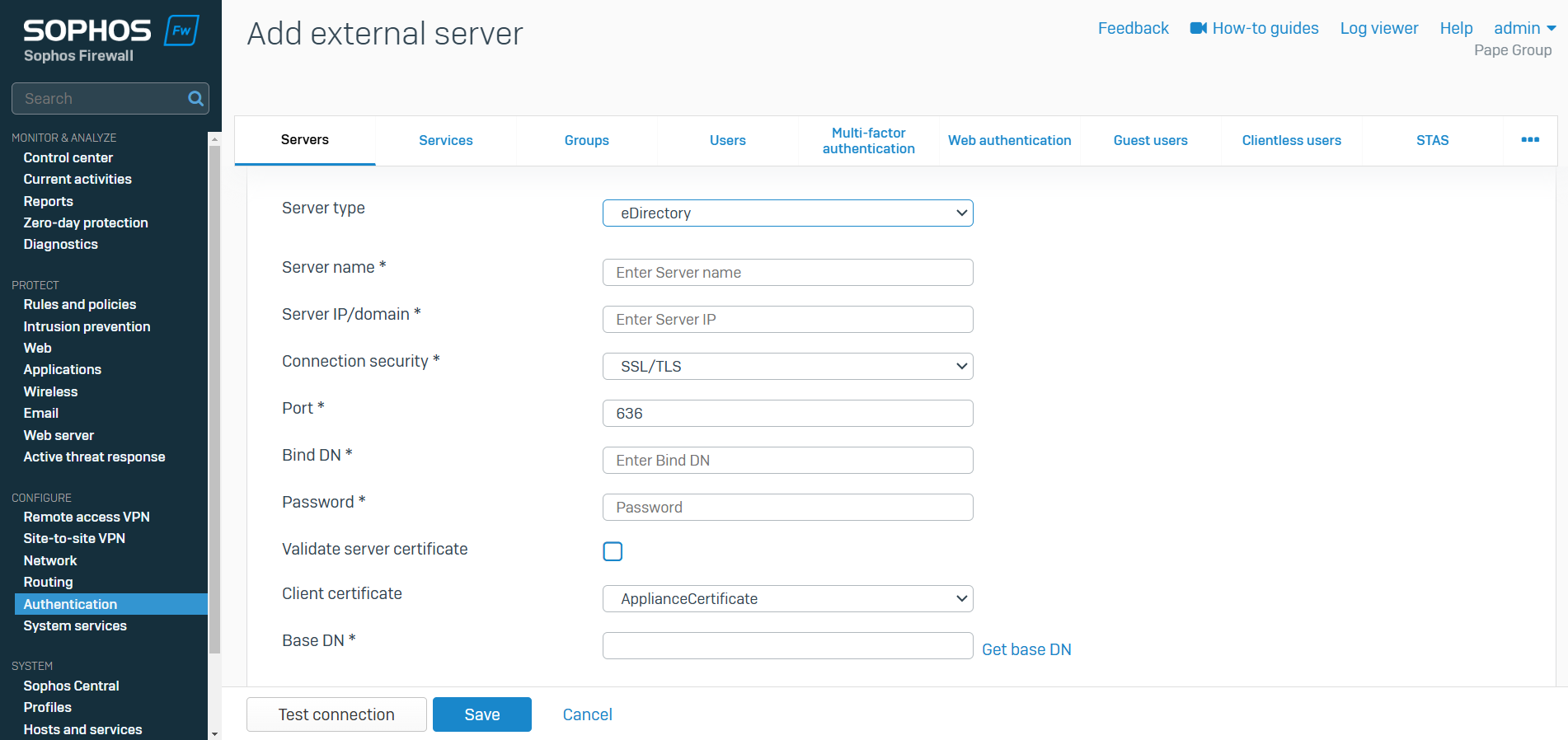
eDirectory Server
- Resource: Add an eDirectory Server
- eDirectory is an x.500-compatible directory service for managing access to resources on multiple servers and devices on a network
- eDirectory is commonly used for managing users, groups, devices, and other resources across a network, enabling centralized authentication, access control, and policy enforcement in enterprise environments
- eDirectory is designed to scale for large, complex networks, and it is known for its high performance, security features, and cross-platform support
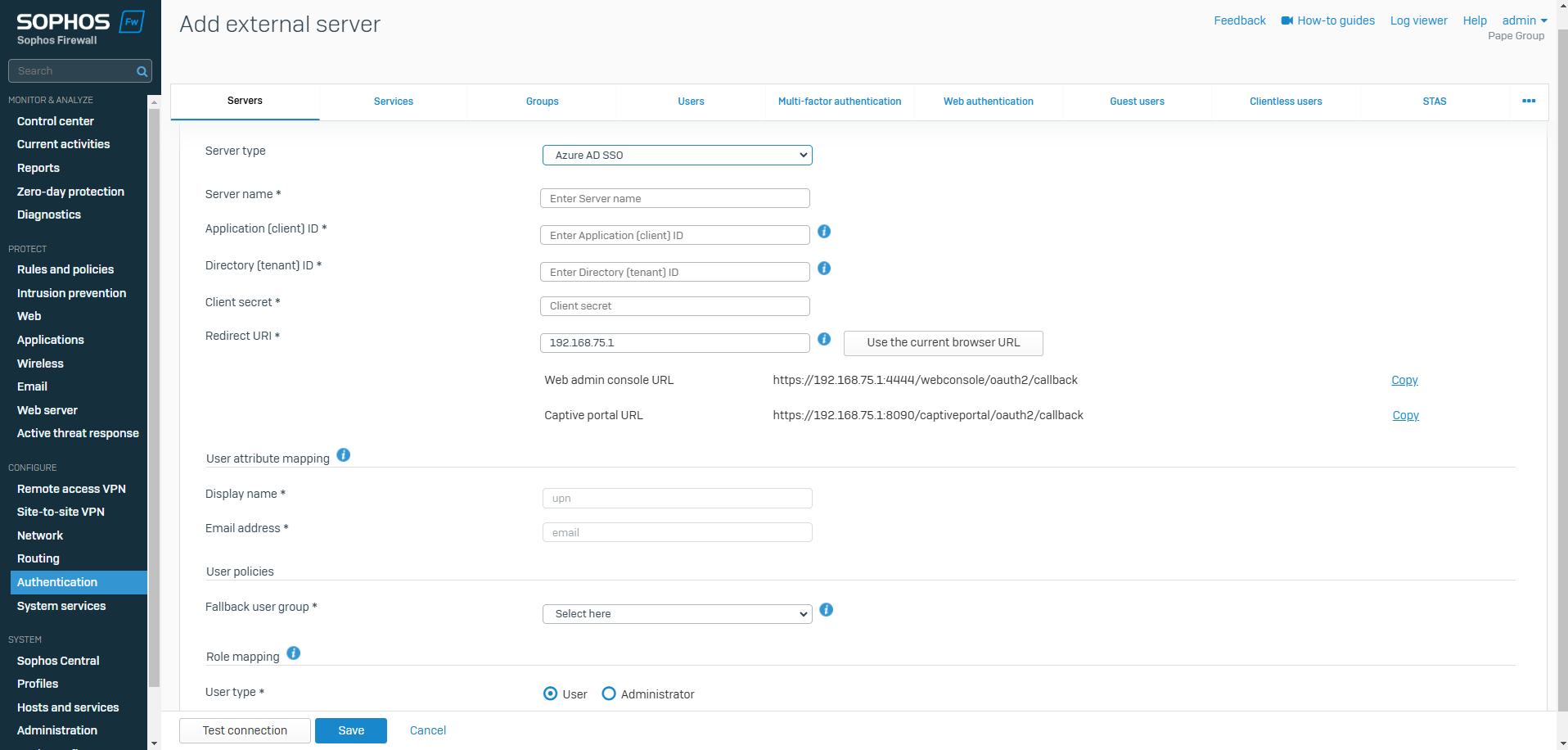
Azure AD SSO
- Resource: Add an Azure AD Server
- You can use Microsoft Entra ID to authenticate a user signing in to the web admin console of the firewall
- The Microsoft Entra ID integration with the Sophos Firewall enables you to dynamically manage administrators using role and group mapping
- It provides a centralized platform to securely control access to your applications, data, and resources through the Sophos Firewall
Authentication Services Overview
Overview
- Using different authentication servers for different services can provide several benefits that enhance the security, performance, and flexibility of an organization's authentication infrastructure. Different types of authentication servers are optimized for specific tasks, and by using them in a targeted way, organizations can achieve more granular control and better management of their resources
- The authentication 'Services' tab in the Sophos Firewall web admin interface gives administrators the ability select which authentication servers to use for particular services such as VPN portal, Firewall, User portal, VPN, SSL VPN, Administrator, and other global settings
- With Sophos Firewall, you can select a maximum of 20 authentication servers for each authentication method
Authentication Method Types
Firewall Authentication Methods
- Authentication server to use for firewall connections
User Portal Authentication Methods
- Authentication server to use for the user portal
VPN Portal Authentication Methods
- Authentication server to use for the VPN portal
VPN (IPsec/dial-in/L2TP/PPTP) Authentication Methods
- Authentication server to use for VPN connections
SSL VPN Authentication Methods
- Authentication server to use for SSL VPN connections
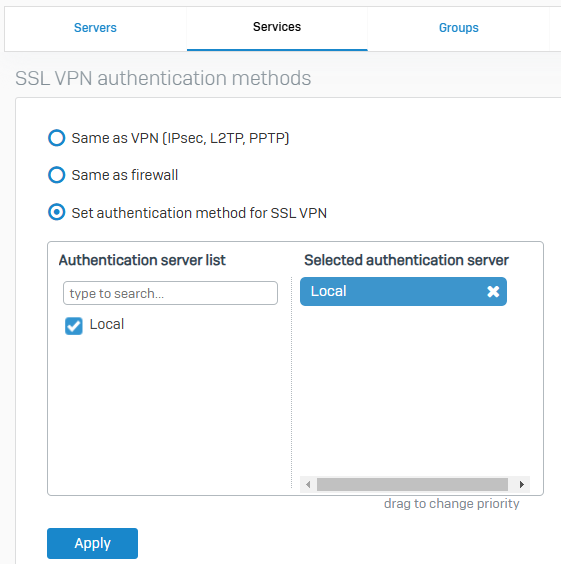
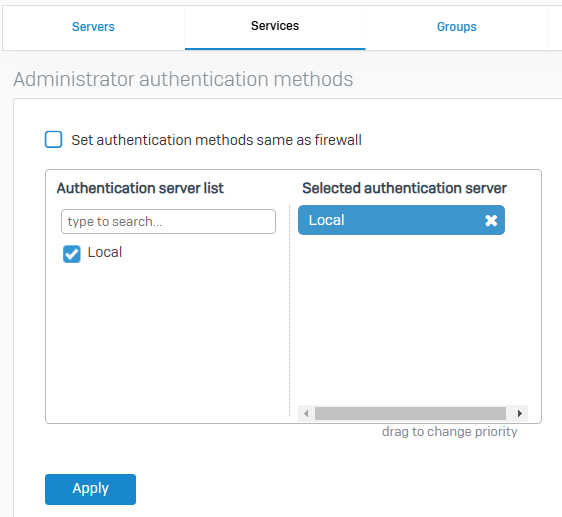
Administrator Authentication Methods
- Server to use for authenticating administrator users
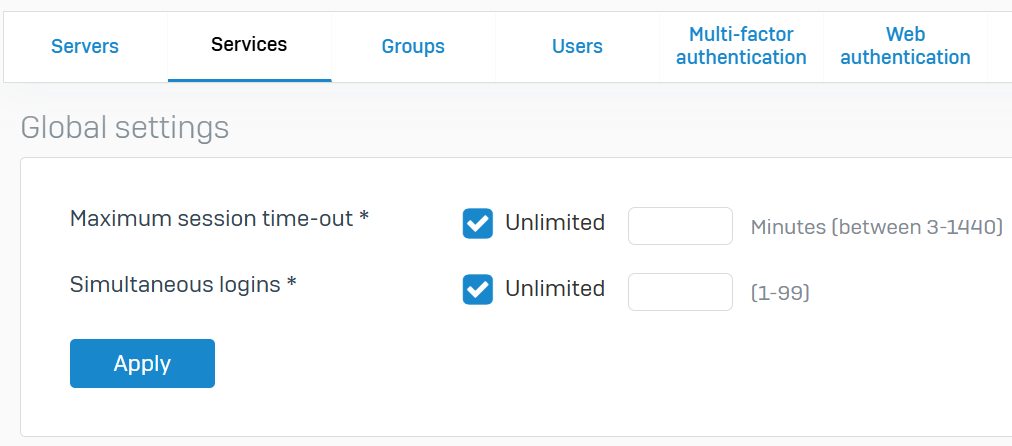
Global Settings
- With global settings, administrators have the ability to set global session timeouts and specify the maximum number of concurrent sessions allowed to users
- This restriction applies only to users who are added after you set this value
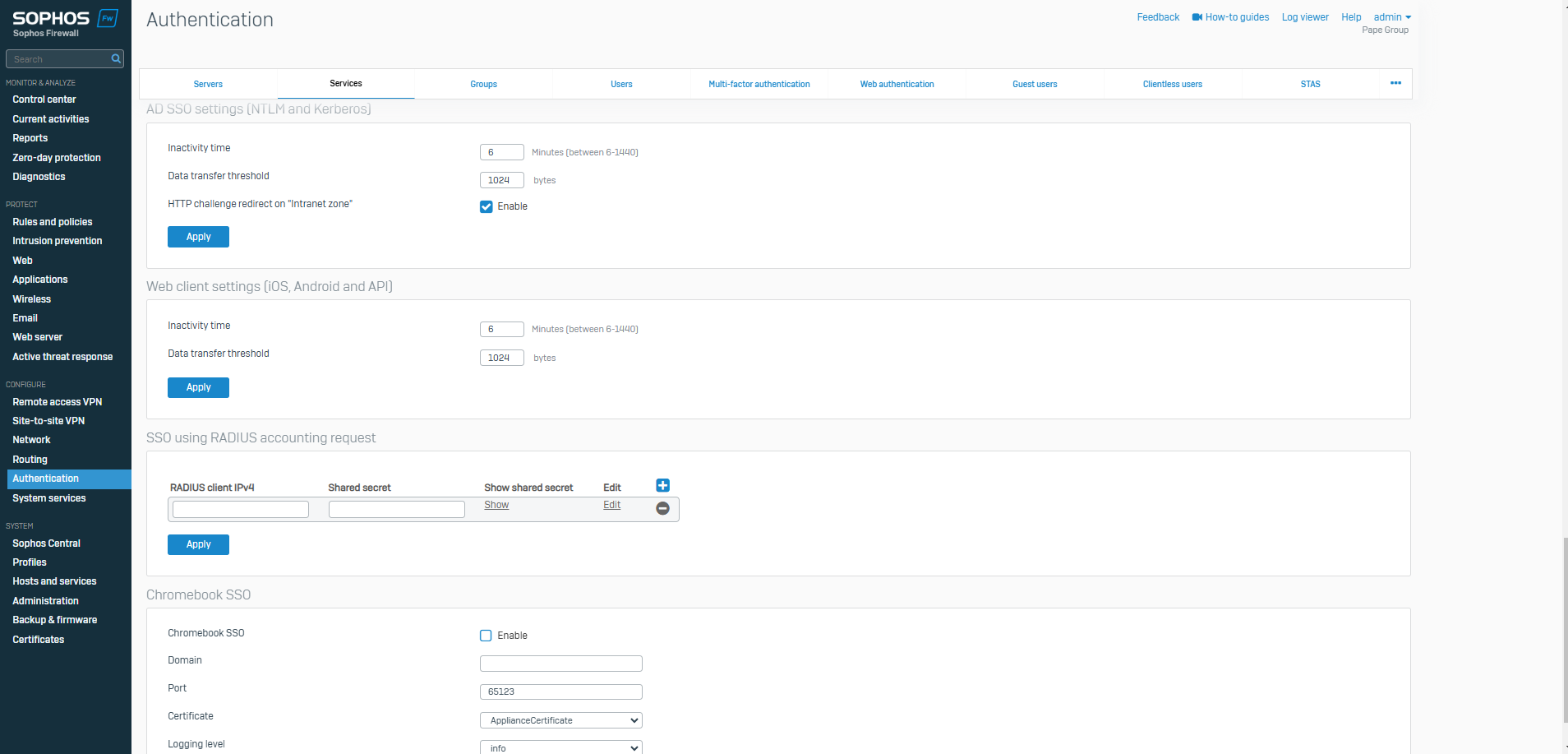
SSO Settings
- Sophos Firewall allows administrators to set single sign on settings for RADIUS, Chromebook SSO, AD SSO, and Web client settings
Authentication Groups & Users Overview
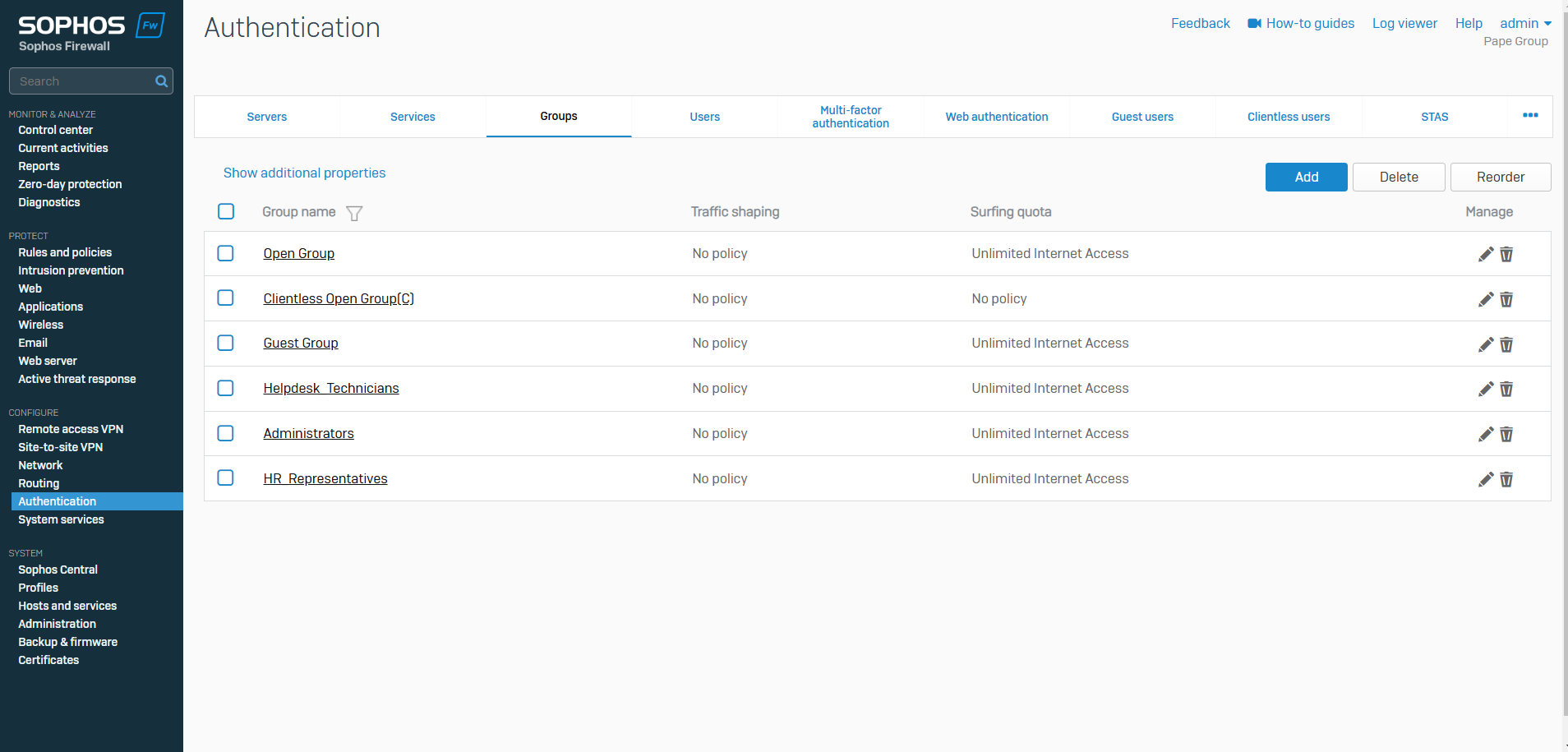
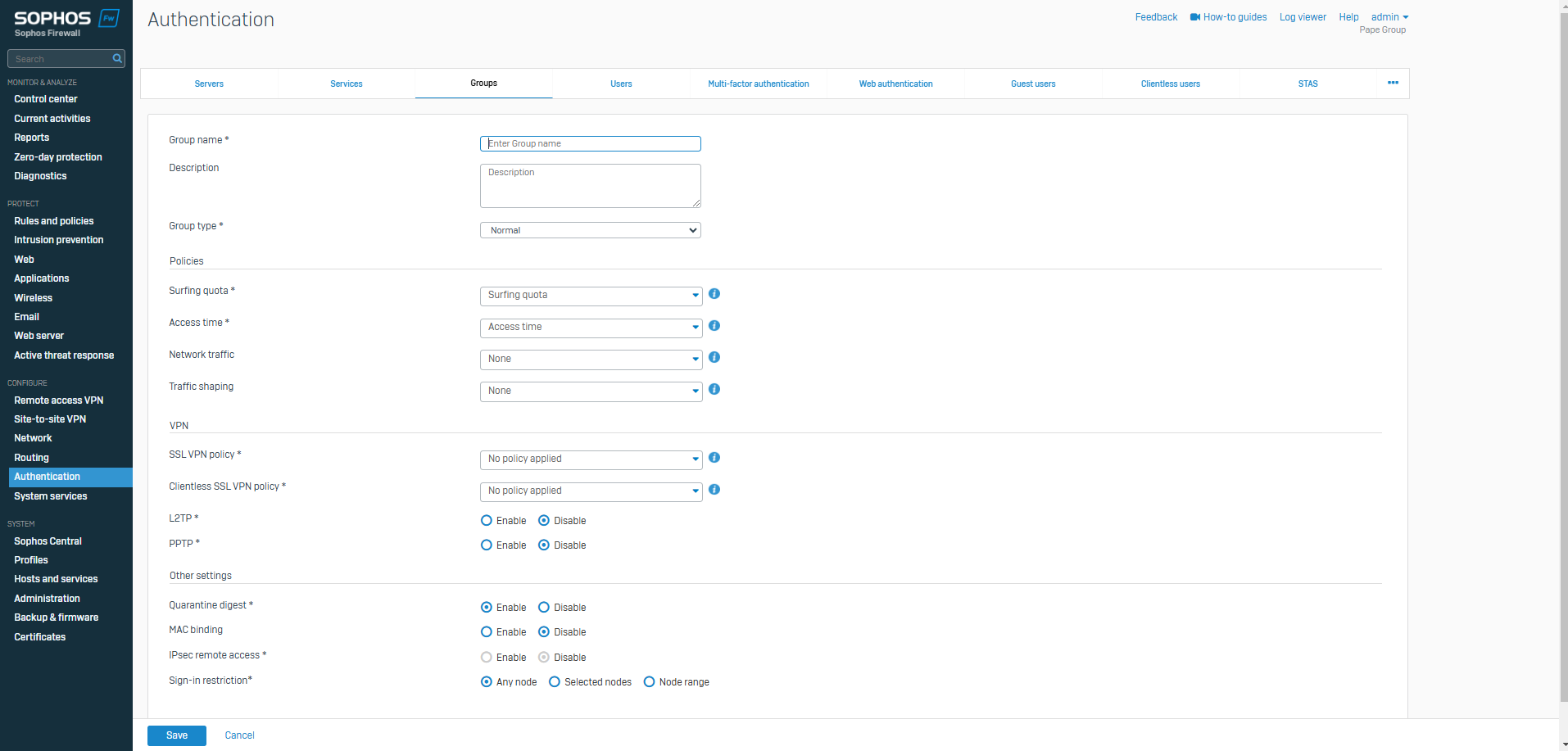
Groups Overview
- Resource: Add a Group
- Organizing groups and users on a firewall is an important strategy for maintaining a secure, efficient, and manageable network environment as it allows you to tailor access control policies to specific user roles, network segments, or devices, helping to prevent unauthorized access, simplify management, and ensure compliance with security policies
- Groups contain policies and settings you can manage as a single unit for users
- With groups, you can simplify policy management for users
- Note: If you use external authentication servers such as Active Directory, users are automatically created and added to their directory group when they sign in. Directory users who belong to an OU (organizational unit) but not to a directory group are added to the default group when they sign in
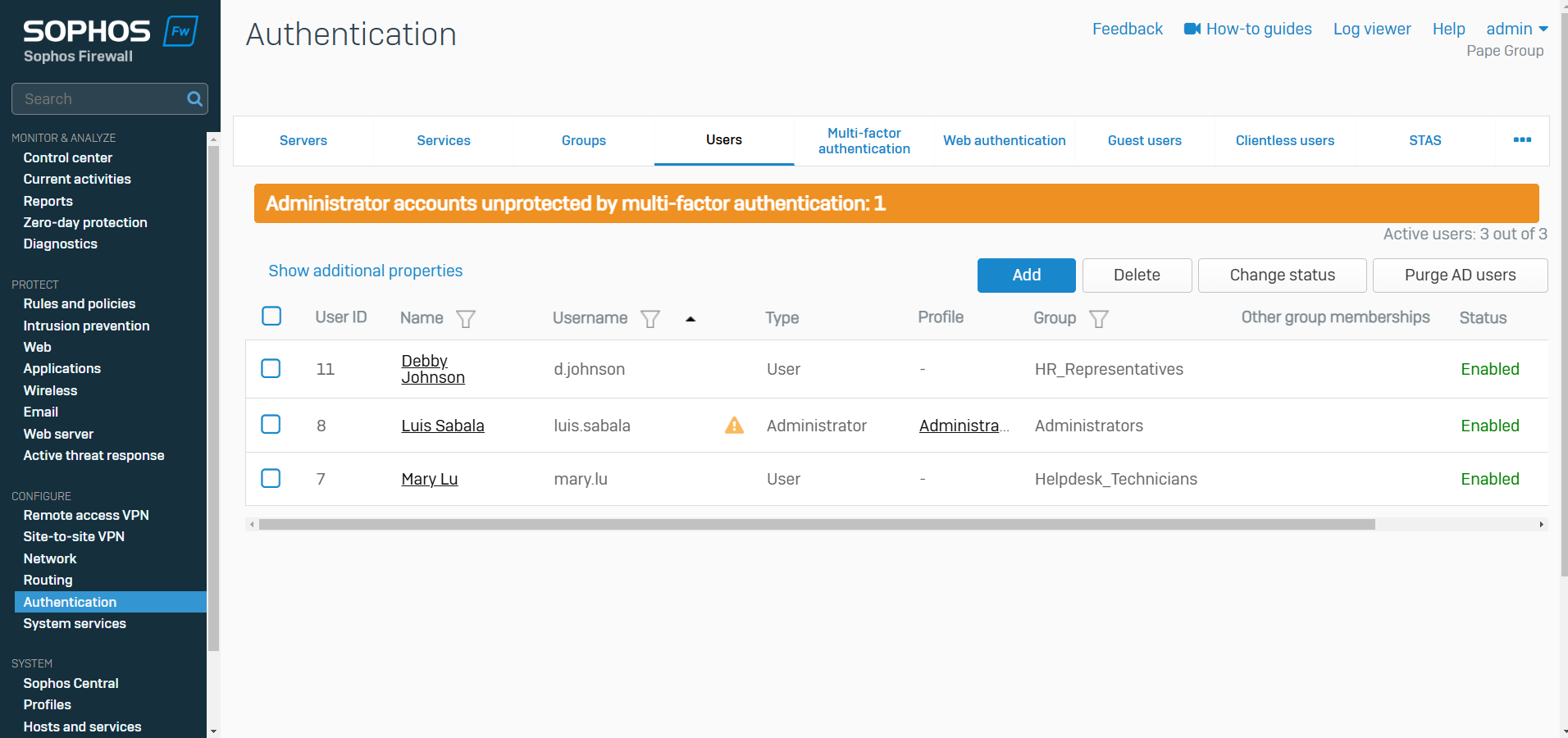
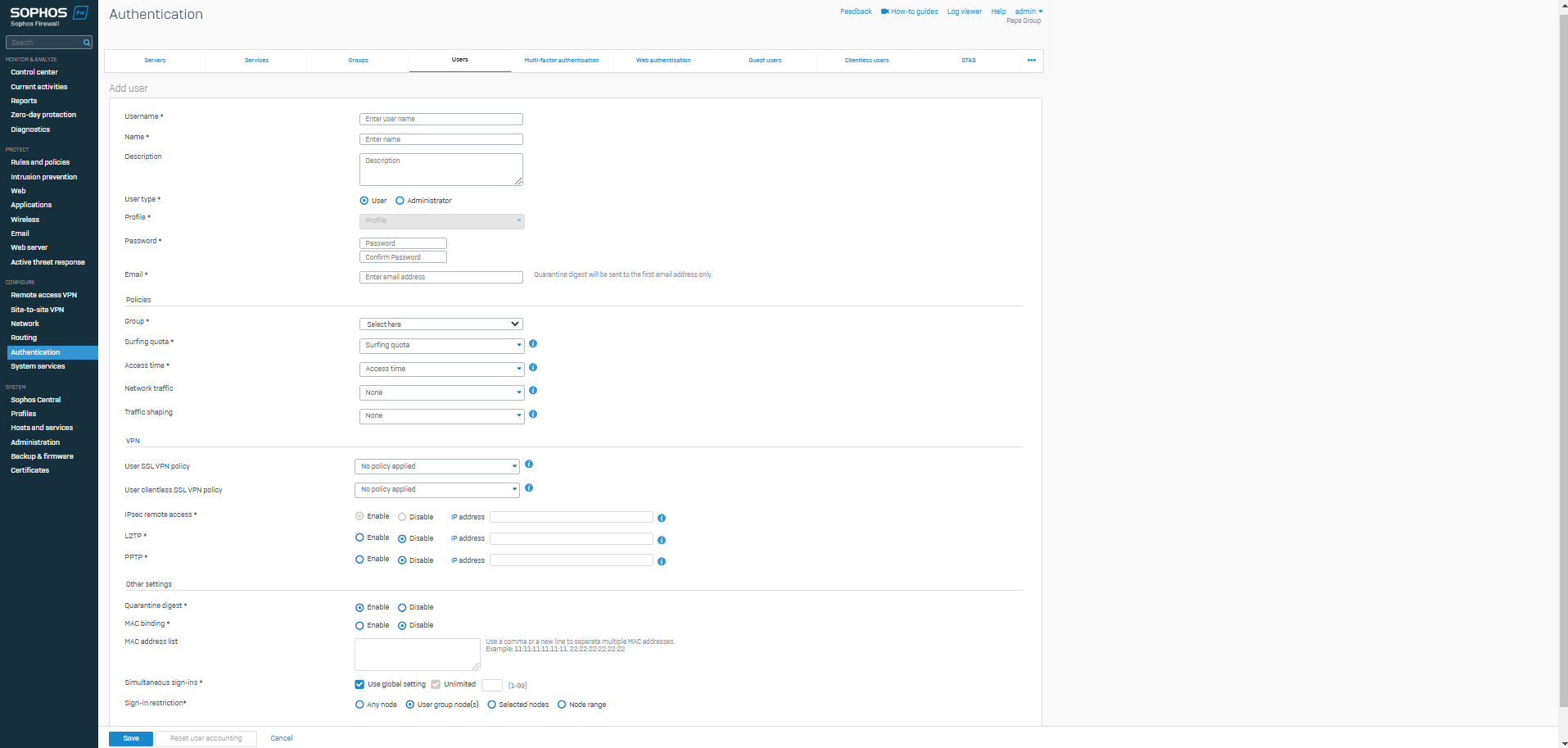
Users Overview
- Resource: Add a User Locally
- With Sophos Firewall, you can create user records locally on the firewall for users and administrators
- The users list also shows the users on your external authentication servers. These records are added when users are authenticated for the first time
Users & Groups
- A user can belong to more than one group
- The Sophos Firewall applies the group's settings if you select only the group in rules and policies. It applies the user's settings if you select both the user and their group
Groups
Users
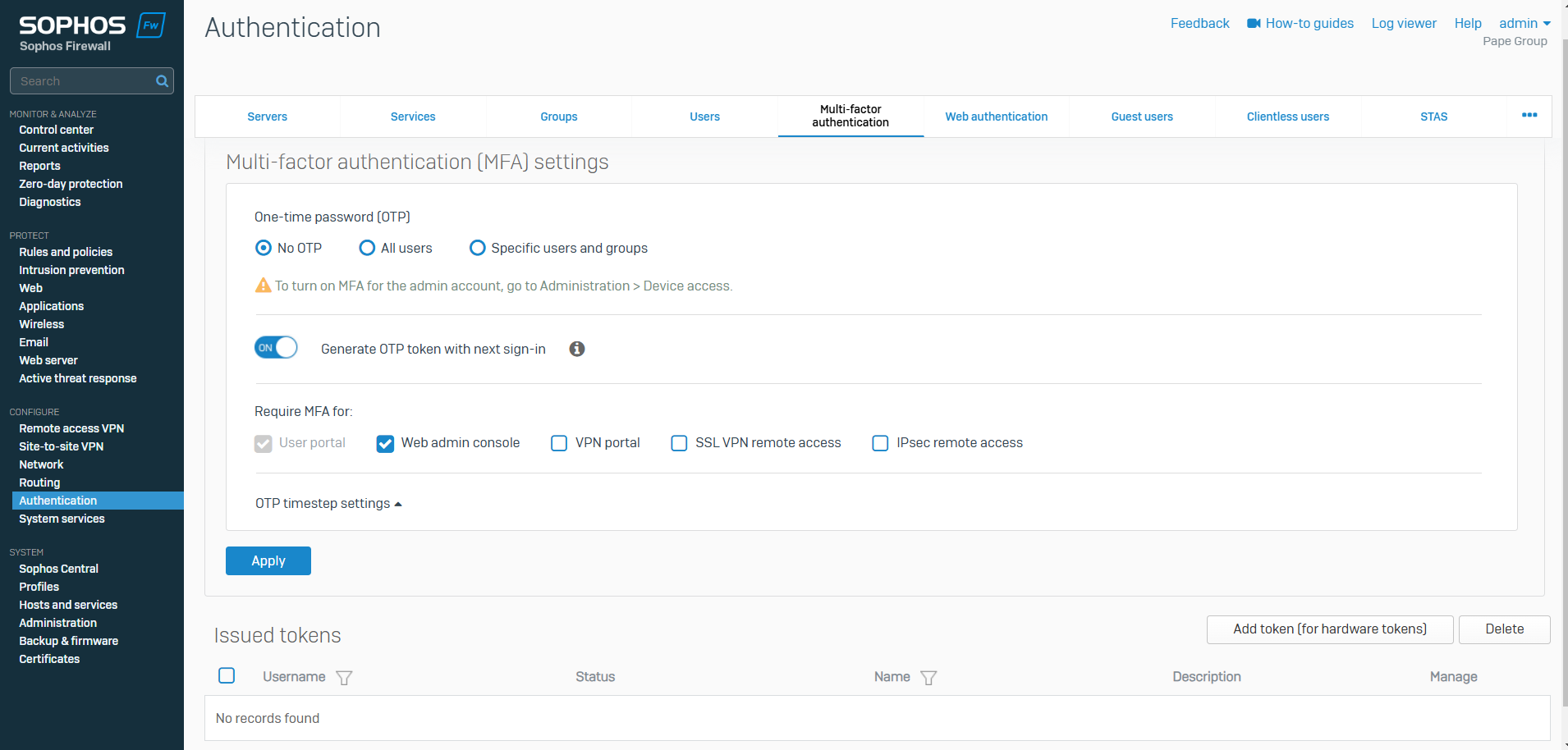
Multi-factor Authentication Overview
Overview
- Resource: Add a MFA Token
- MFA is a security method that requires users to provide two or more verification factors to gain access to a system, application, service, or network, adding an additional layer of protection beyond just a username and password. MFA helps protect against unauthorized access by ensuring that even if one factor (like a password) is compromised, the attacker still needs to provide additional factors to access the system
- Sophos Firewall supports multi-factor authentication using hardware or software tokens
- For software tokens, users must scan the QR code on the User portal using an authenticator application on their mobile devices
- With the MFA settings, you can configure MFA and apply it to users signing in to certain firewall services, such as the user portal and remote access VPN
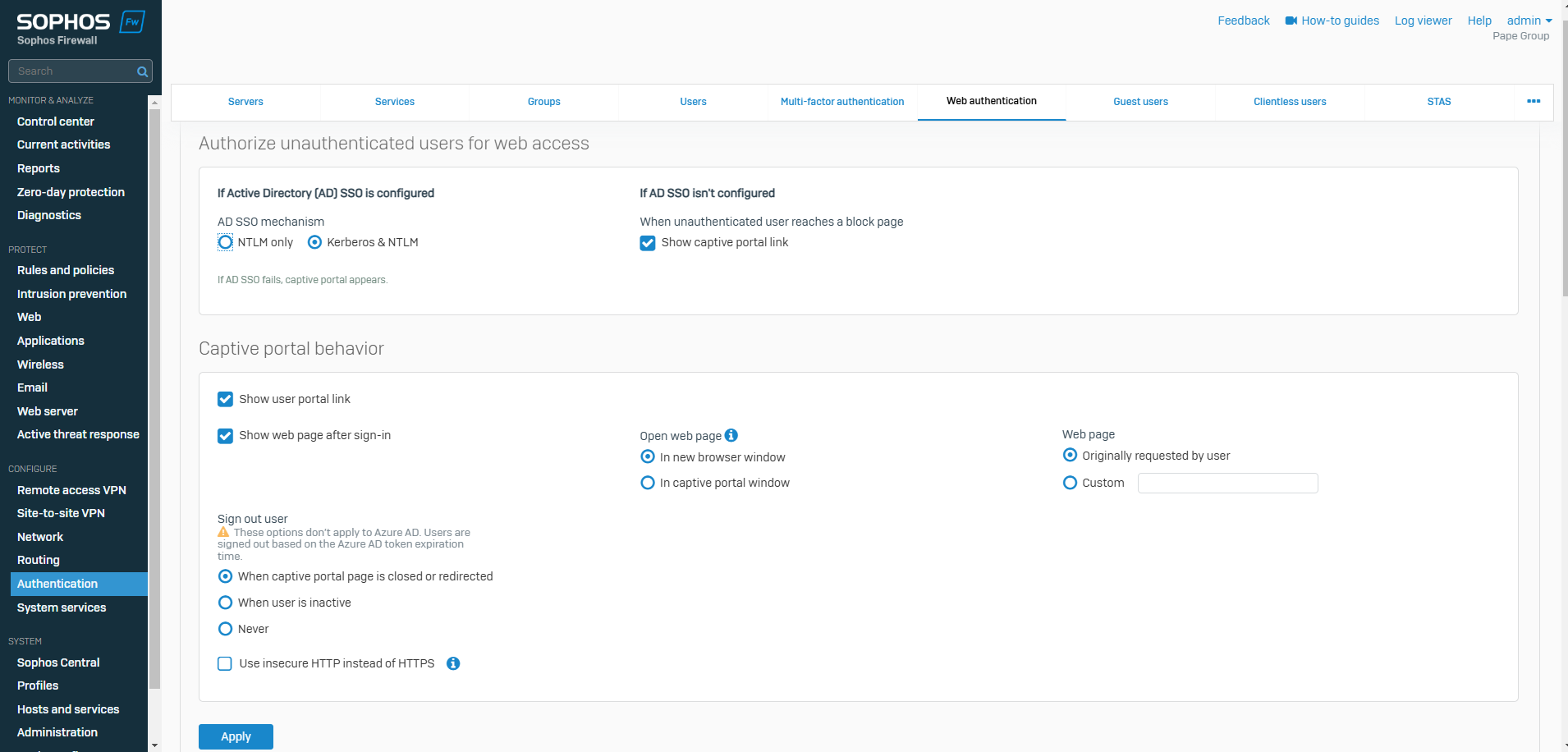
Web Authentication Overview
Overview
- Resource: Configure AD SSO Web Authentication
- You can use Active Directory SSO or the captive portal to authenticate users. Users will then appear in logging and reporting and will be used as matching criteria in firewall rules and web policies
- Active Directory single sign on (SSO) attempts to silently authenticate users signed in to endpoint devices with Sophos Firewall without user interaction
- The captive portal is a web page that requires users behind the firewall to authenticate when attempting to access a website. You can also define the behavior and layout of the captive portal
- After authenticating with the captive portal, Sophos Firewall allows users to proceed to their requested destination or redirects them to a URL that you specify
Guest & Clientless Users Overview
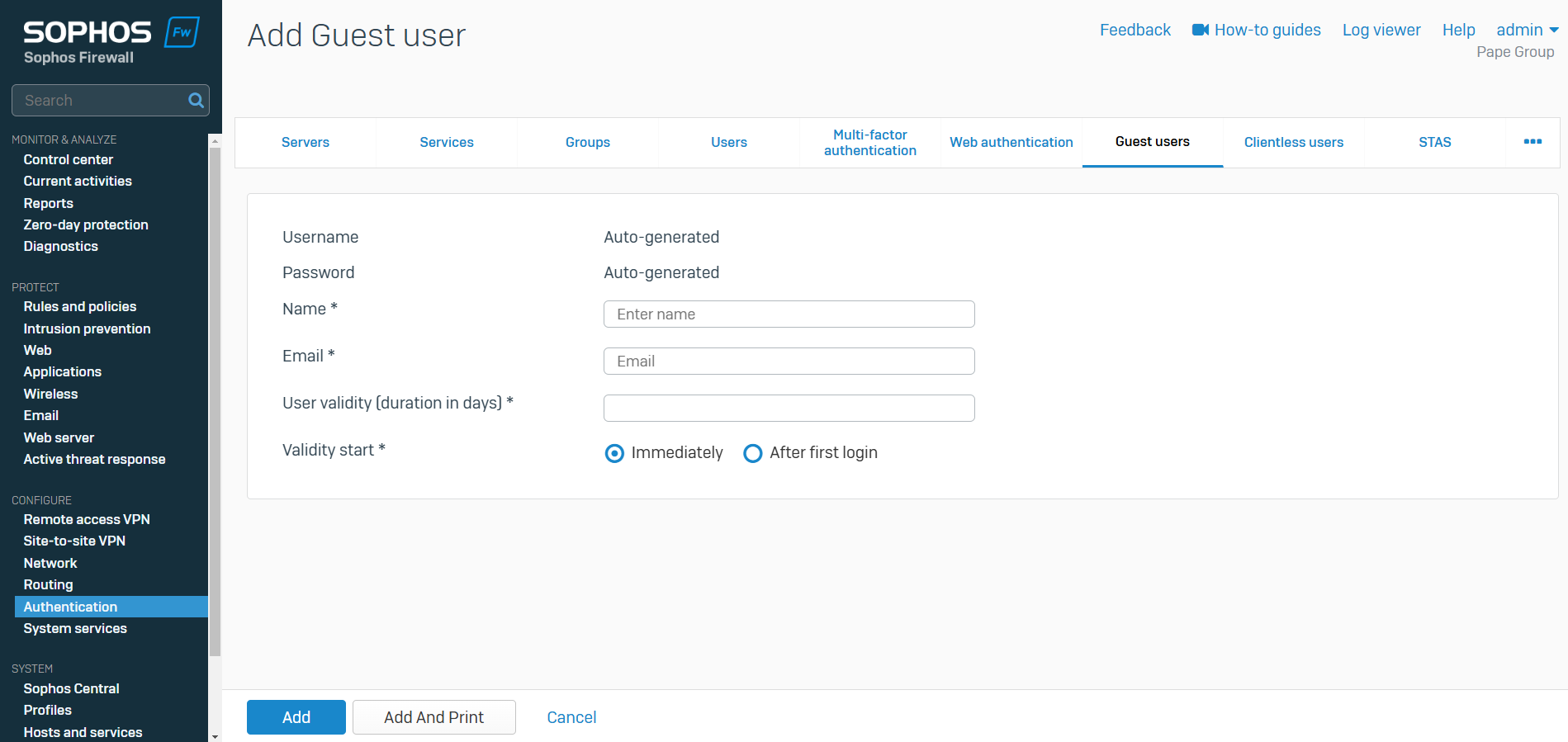
Guest User Overview
- Resource: Add a Guest User
- In environments where external users (such as customers, partners, or visitors) need temporary or limited access to network resources, properly defining and managing guest users provides clear boundaries, control, and monitoring of their activities
- Guest users are users who don't have an account and want to connect to your network to access the Internet
- You can register guest users or allow them to register through the guest user portal
- You can print credentials or send them through SMS
- After authentication, the guest user is granted access according to the selected policies or is redirected to the captive portal
- Before you add guest users, administrators must specify Guest user settings from the Sophos Firewall web admin interface
Clientless User Overview
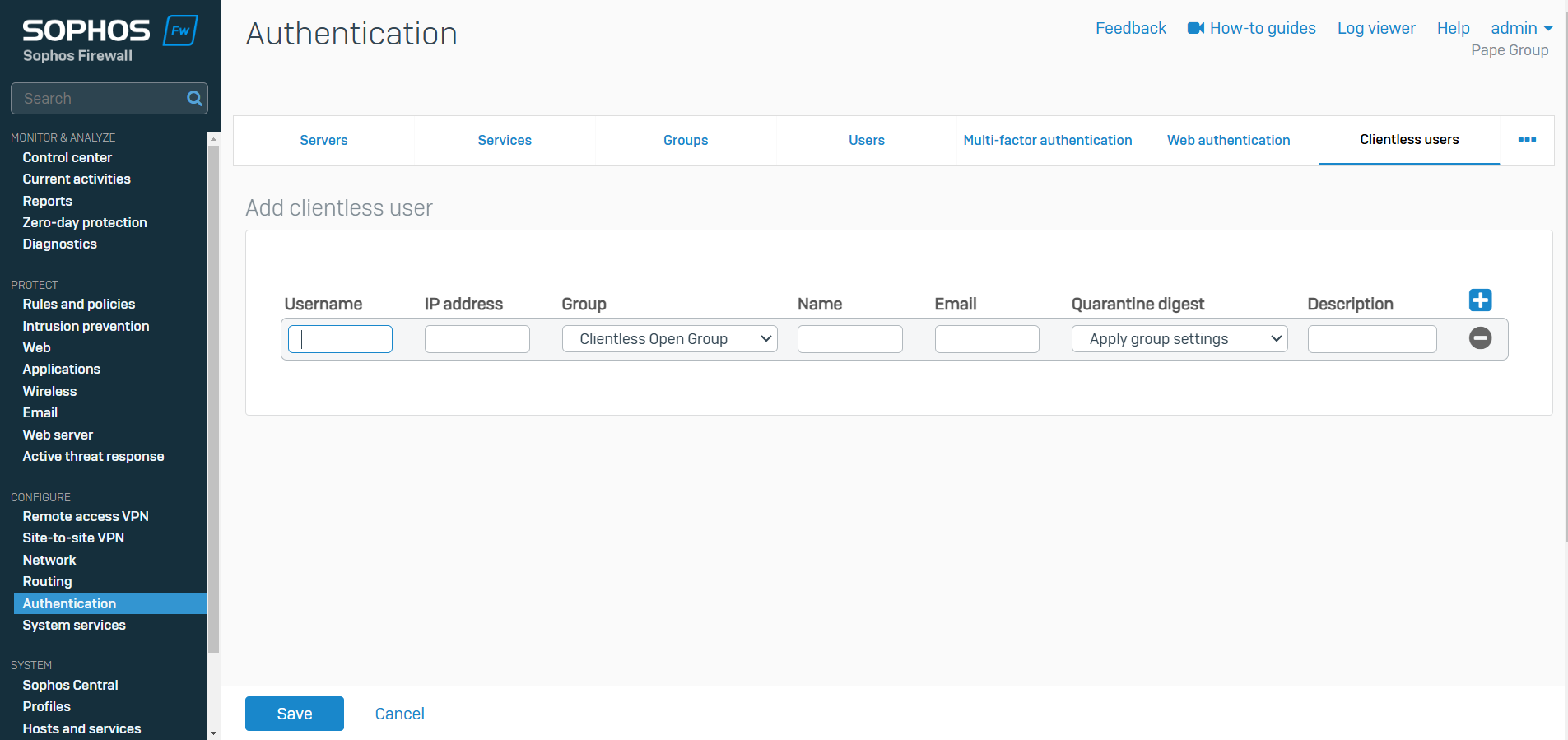
- Resource: Add a Clientless User
- Defining clientless users on a network can be highly beneficial for both security and efficiency, especially in scenarios where users or devices need to access network resources without installing or configuring specific client software on the device
- You can configure users and network devices, such as servers and printers, as clientless users
- Clientless users don't require authentication and don't use a client to access the network. Sophos Firewall allows these users to access the network by matching the username to the IP address you specify in the clientless user policy
- Sophos Firewall also allows administrators to configure people as clientless users, such as senior executives, for whom you don't want to require a sign-in when they're within the network. If you configure users rather than network devices, Sophos recommends that you map the users with static IP addresses on the DHCP server
- You can create clientless users individually or as a group. You can then edit each user's configuration and specify the policies and bandwidth usage
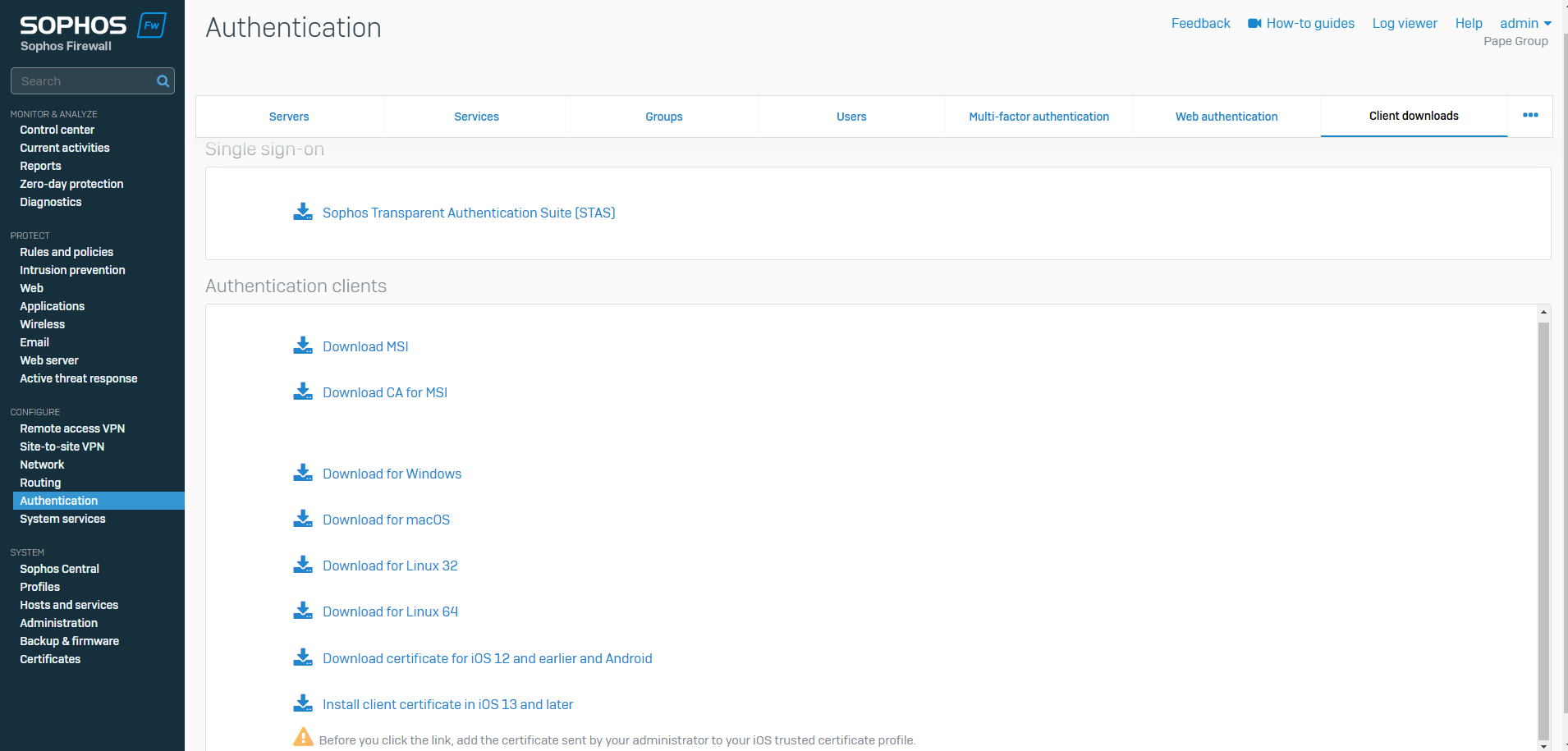
Authentication Client Download Overview
Guest User Overview
- Resource: Client Downloads
- This page offers the settings to download the authentication client and components that support single sign-on, transparent authentication, and email encryption
- You must install the authentication client agent and server CA on all your endpoint computers. You can download these files and share them with users. Alternatively, users can download these from the user portal and install them on their endpoint devices
- The client authentication agent communicates through IP address '1.2.3.4' and port '9922'
- When users sign in to the client, they're signed directly into the network through the Sophos Firewall
- The authentication client agent is supported on the following
- MSI (Windows 10 and later)
- Windows (Windows 10 and later)
- macOS (Catalina 10.15 and later)
- Linux 32 (Ubuntu 16.4 and later)
- Linux 64 (Ubuntu 16.4 and later)