RADIUS Lab
Sections:
- RADIUS Overview
- Deploying (NPS) Network Policy Server
- Cisco IOS AAA
- RADIUS Authentication for Sophos Firewall
- Defining Device Access Profiles
- Define Device Access Profiles for RADIUS Admins
- Add RADIUS Authentication Server
- Add Sophos RADIUS Client
- Set Sophos Primary Authentication Methods
- Import Active Directory Groups for RADIUS
- Captive Portal & Assigning Profiles for RADIUS
- (Privilege 1 - Read-only) RADIUS Verification
- (Privilege 15 - Full-control) RADIUS Verification
- Sophos Firewall Authentication Logs
- Defining Device Access Profiles
Resources:
- Sophos Firewall
- Windows Server NPS
- Cisco IOS
Overview:
- In this lab demonstration, I will be defining and configuring an external Windows server utilizing the NPS (Network Policy Server), a RADIUS solution, to be used for administrator authentication for the Sophos Firewall and Cisco Catalyst switches
- In the next few sections, I will demonstrate configuring the RADIUS NPS interface on the Windows server virtual machine providing other services such as Active Directory and Windows file services for network shares across the domain
- Aside from configuring the RADIUS NPS interface, I will also be demonstrating configuring AAA on Cisco Catalyst switches using RADIUS and Active Directory authentication for login credentials
RADIUS Overview
Overview
- The RADIUS protocol is a networking protocol that provides comprehensive and centralized Authentication, Authorization, and Accounting (AAA) management for users who connect and use a network service
- Key Functions
- Authentication
- RADIUS is used to authenticate users or devices attempting to connect to a network. It checks the credentials (username and password, or other authentication methods) provided by the user or device against a database or directory, such as Active Directory or an LDAP server
- Authorization
- Once a user is authenticated, RADIUS can determine what level of access the user or device should have. This could include what resources or network services the user can access, based on policies set by the network administrator
- Accounting
- RADIUS can log information about network access, including the duration of a session, data usage, and any events such as login attempts (both successful and failed). This information is typically used for billing, auditing, and troubleshooting purposes
- Authentication
- How RADIUS Works
- User Initiates a Conection
- A user or device attempts to connect to a network through a device like a VPN server, wireless access point, or firewall
- RADIUS Request
- The network access server (NAS) sends a request to the RADIUS server for authentication, including the user's credentials (like a username and password)
- RADIUS Response
- The RADIUS server checks the credentials against its database or an external authentication source (like Active Directory). If the credentials are valid, the RADIUS server sends an "Access-Accept" message, along with any additional information (such as specific access rights)
- If the credentials are invalid, the RADIUS server sends an "Access-Reject" message
- Authorization
- After successful authentication, the RADIUS server checks the user's permissions based on the network policies and sends the appropriate authorization response
- Accounting
- The NAS then logs the user's session information, such as start and end times, data usage, etc., and can send accounting records back to the RADIUS server for tracking and reporting
- User Initiates a Conection
NPS RADIUS Overview
Overview
- A Network Policy Server (NPS) allows network administrators to create and enforce policies for network access, ensuring that only authorized users and devices can access network resources
- NPS is Microsoft's implementation of a RADIUS server in the Windows Server operating systems, being a crucial component in network management and security
- Effective policy management sets a clear framework for how network security is handled within an organization. It defines the protocols for access control, user authentication, data handling, and response to security incidents. This structured approach ensures consistency, efficiency, and adaptability in responding to evolving security threats
Benefits of using NPS
Fine-grained Access Management
- NPS enabled administrators to define detailed access policies, granting appropriate access levels to different user groups
- This granularity ensures that users have access only to the resources necessary for their roles
Consistent Policy Enforcement
- With NPS, network policies are applied uniformly across all access points
- This consistent enforcement of security policies helps maintain a high-security standard throughout the network
Robust Authentication & Authorization
- NPS strengthens network security by ensuring robust authentication and authorization of users and devices
- This reduces the risk of unauthorized access and potential security breaches
Dynamic Response to Security Threats
- NPS can be configured to respond to security incidents dynamically, such as temporarily increasing security measures during a detected threat
Adapts to Organizational Growth
- NPS is scalable and can handle an increasing number of authentication requests as an organization grows
- This scalability ensures that the network can expand without compromising on security or performance
Support for a Variety of Network Types
- NPS is versatile and supports various network types and access methods, including VPNs, and wireless networks, making it a flexible solution for diverse network environments
Centralized Management
- By centralizing the management of network policies and access controls, NPS simplifies administrative tasks, saving time and reducing the likelihood of errors
Integration with Existing Systems
- NPS integrates well with other Microsoft products and services, such as Active Directory, providing a seamless management experience
Detailed Logging & Reporting
- NPS maintains comprehensive logs of network access and activities, which are invaluable for auditing purposes and to ensure regulatory compliance
Supports Compliance Requirements
- The detailed accounting and reporting capabilities of NPS assist organizations in meeting various data privacy and security standards such as GDPR, HIPAA, and PCI DSS
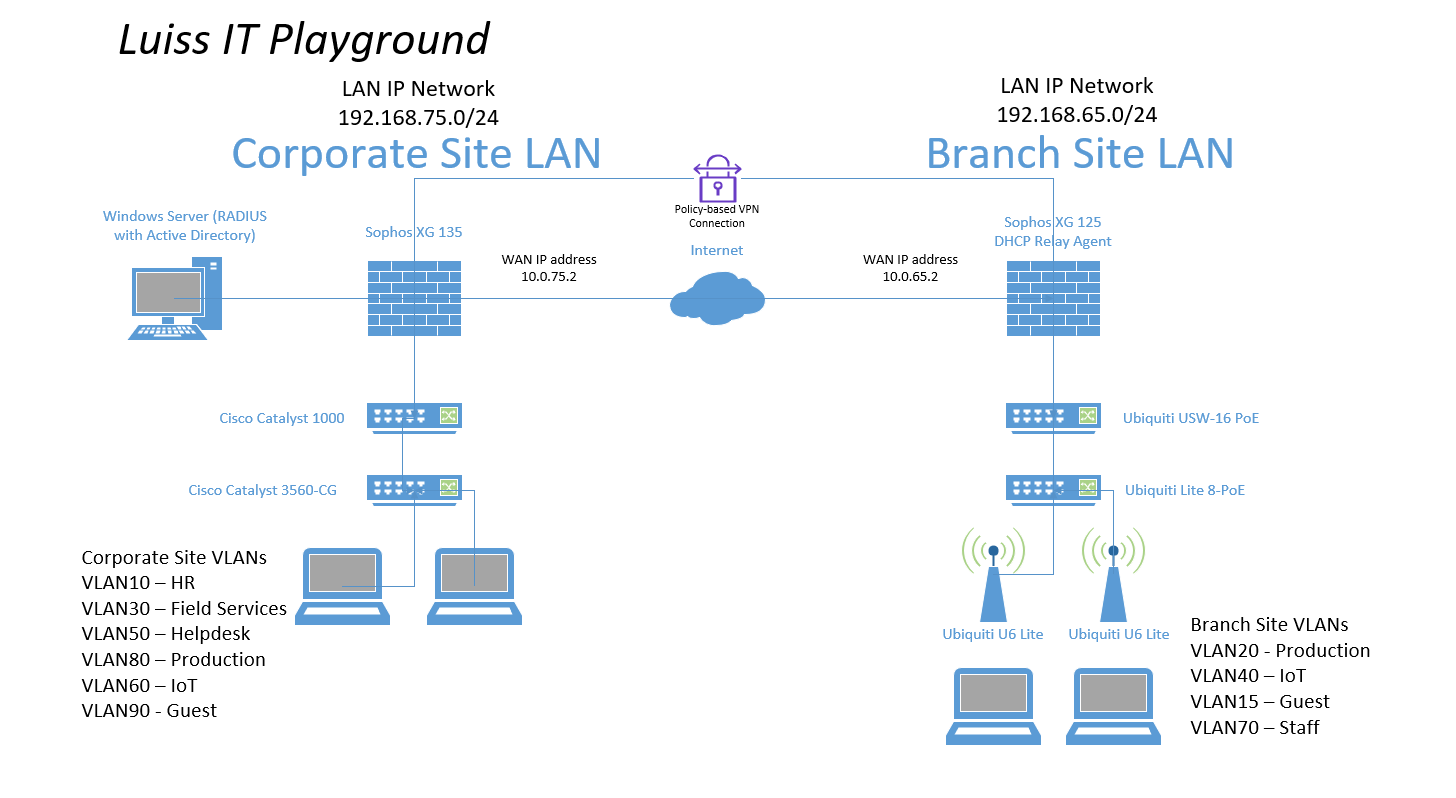
RADIUS Lab Topology
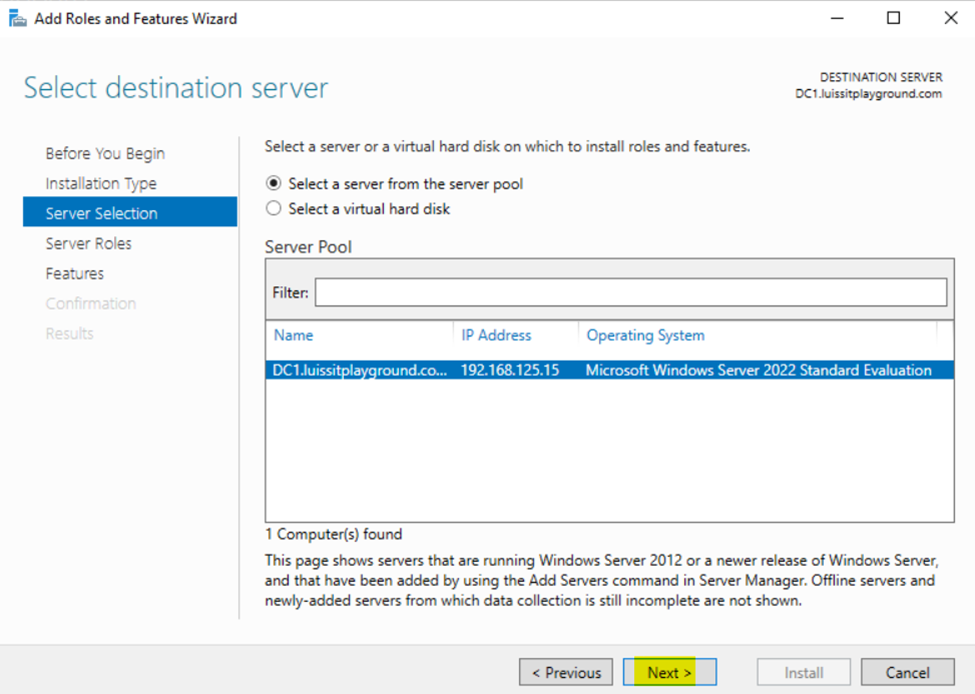
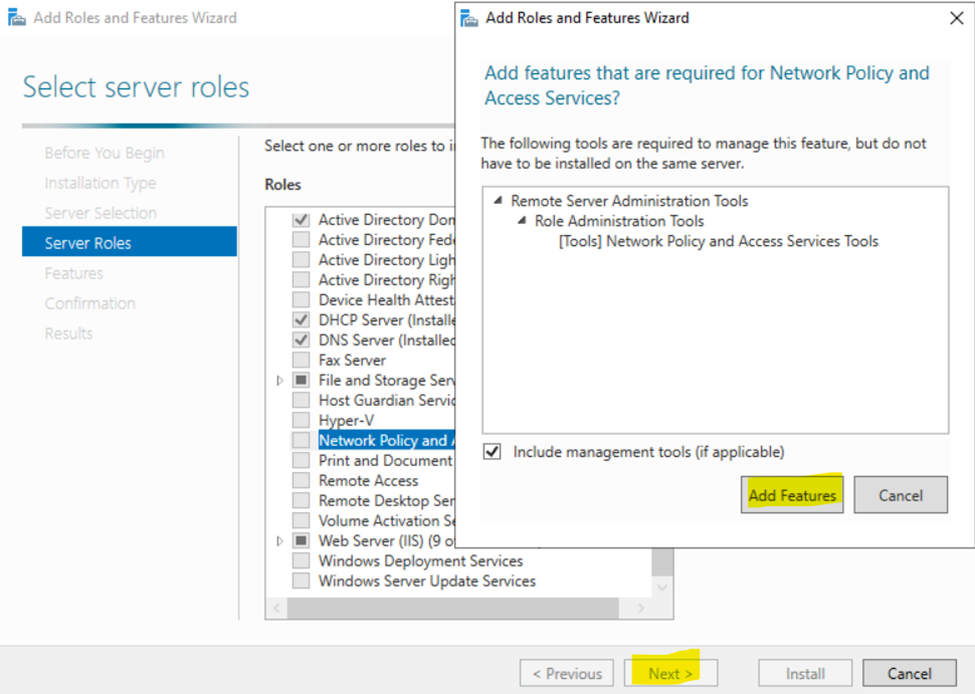
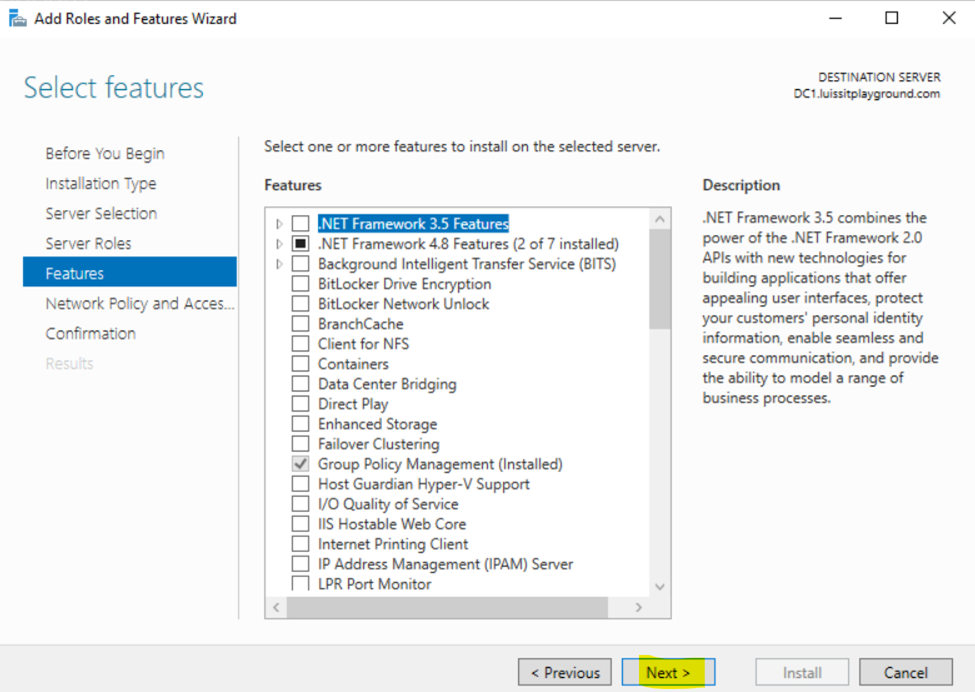
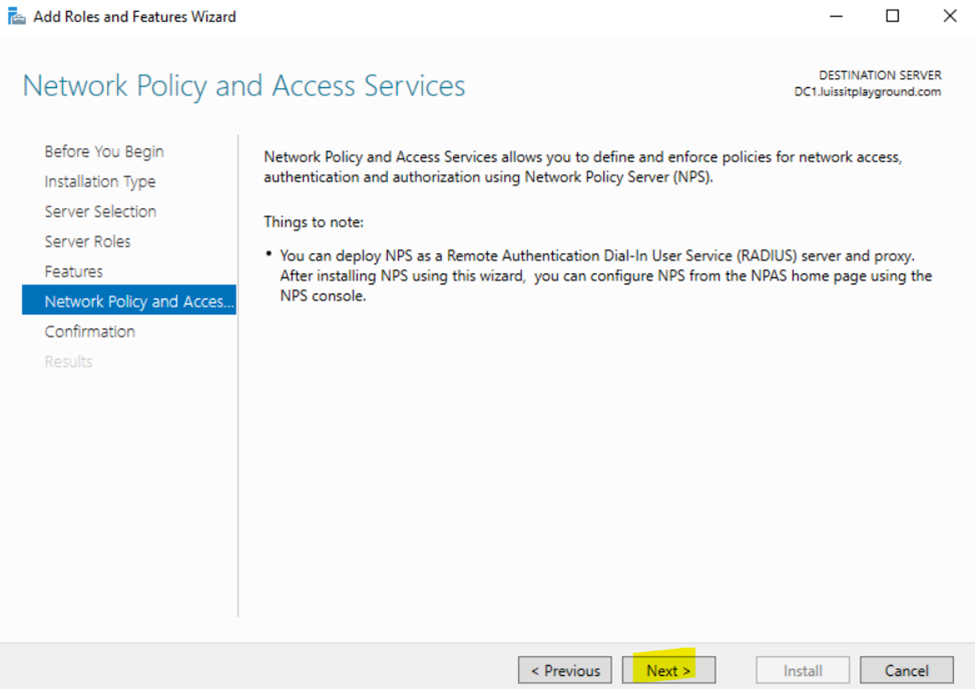
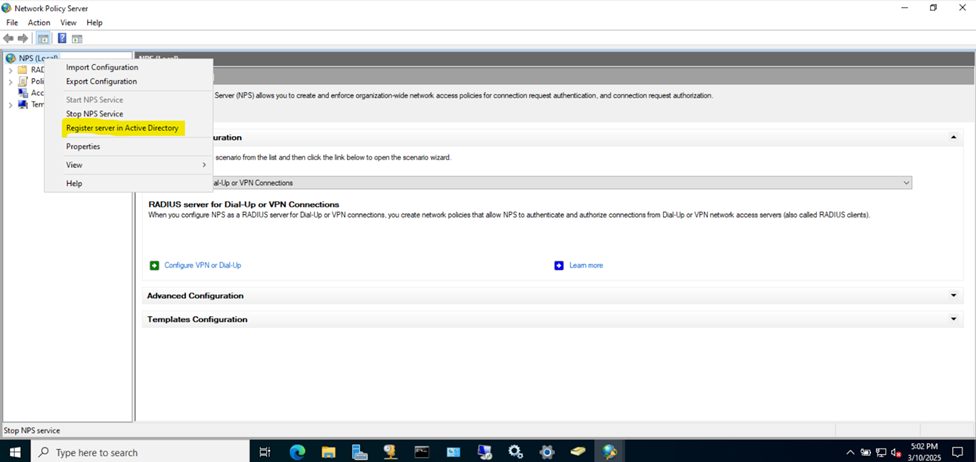
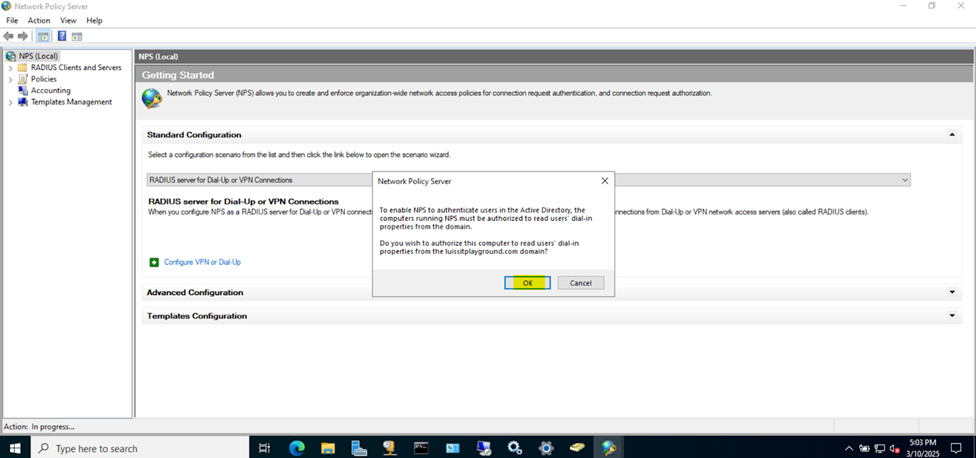
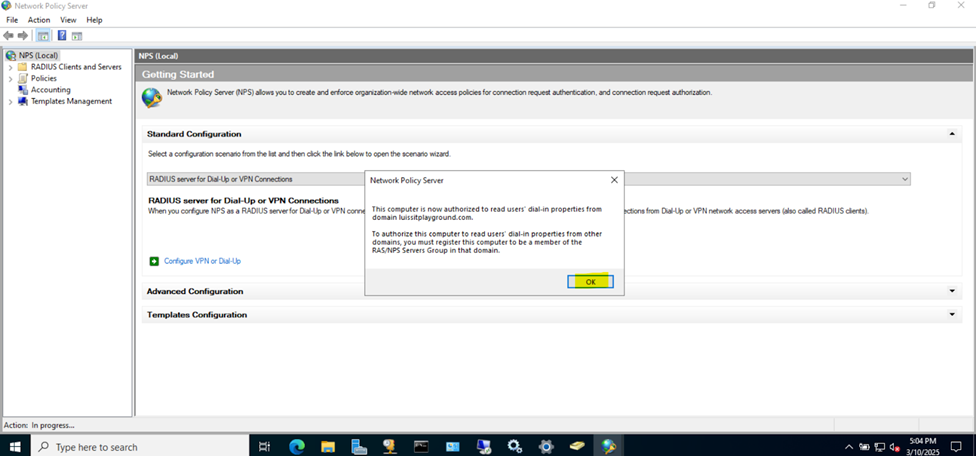
Installing the (Network Policy Server) Role on Windows Server
- Resource: Install Network Policy Server
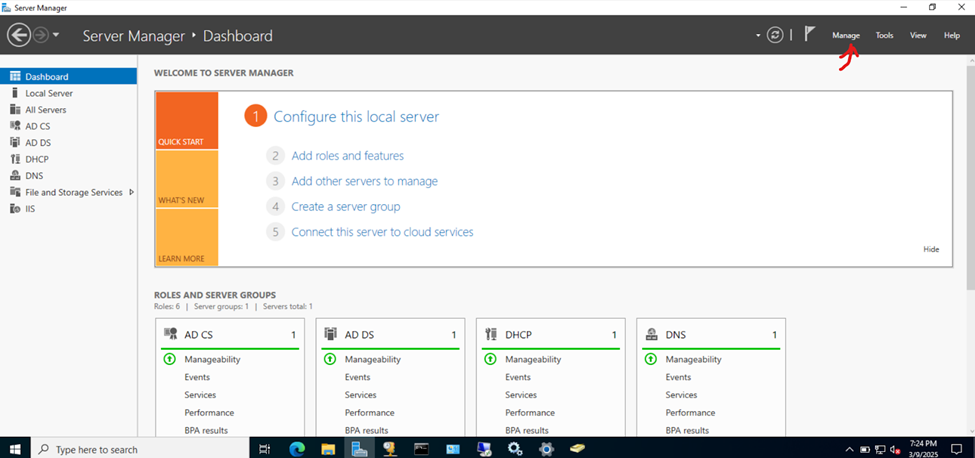
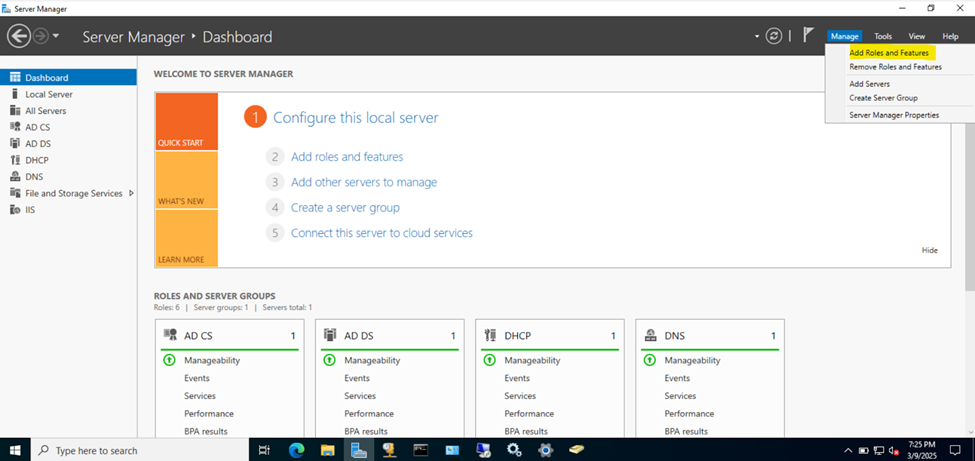
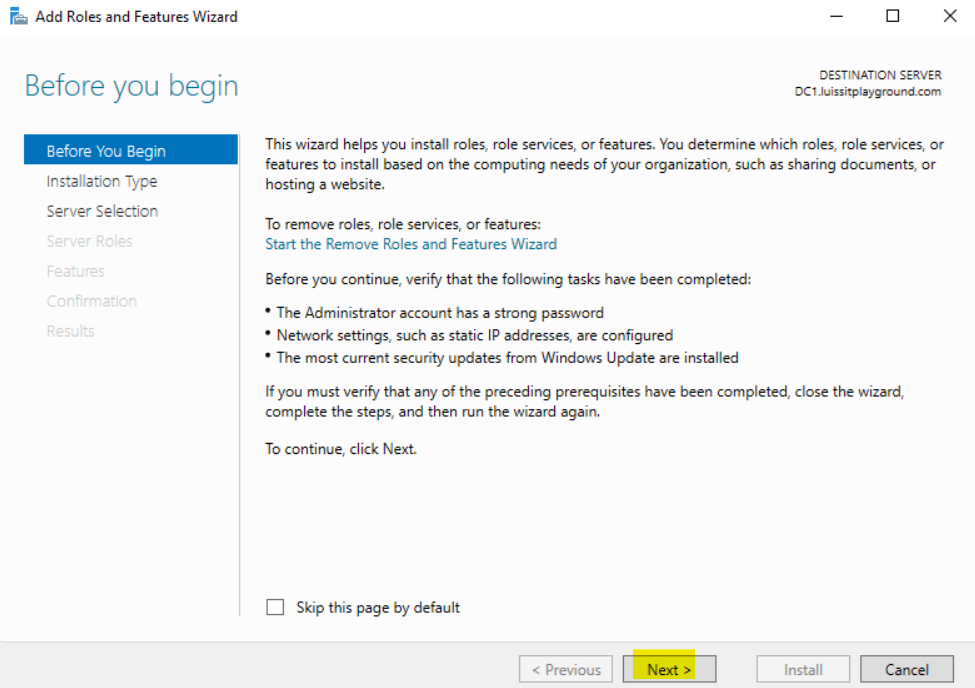
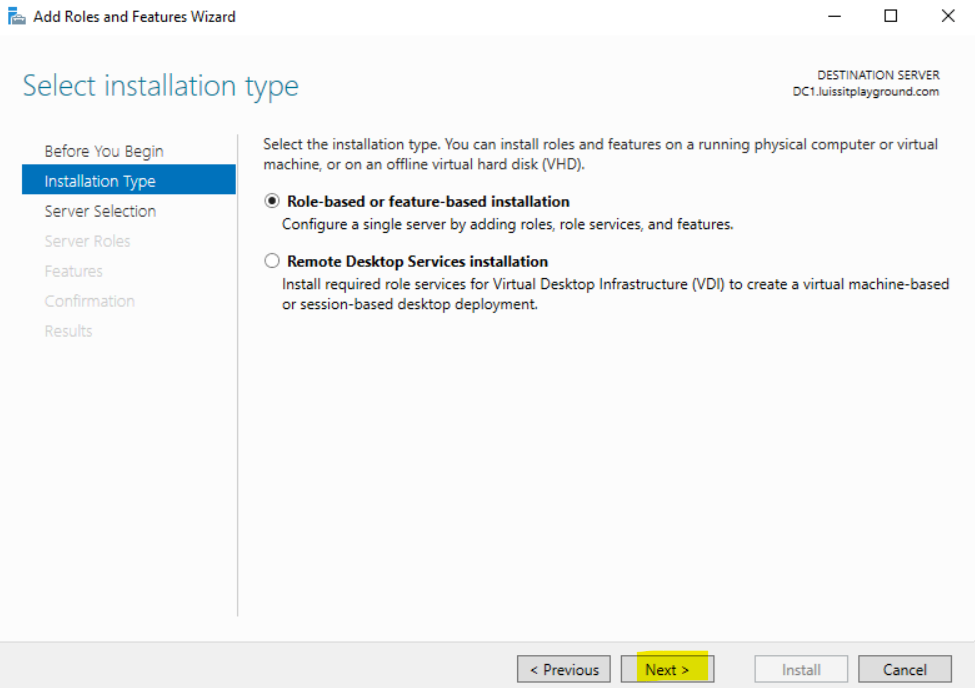
- In this demonstration, I will walk-through installing Microsoft's RADIUS solution, the NPS service role, on a Windows server
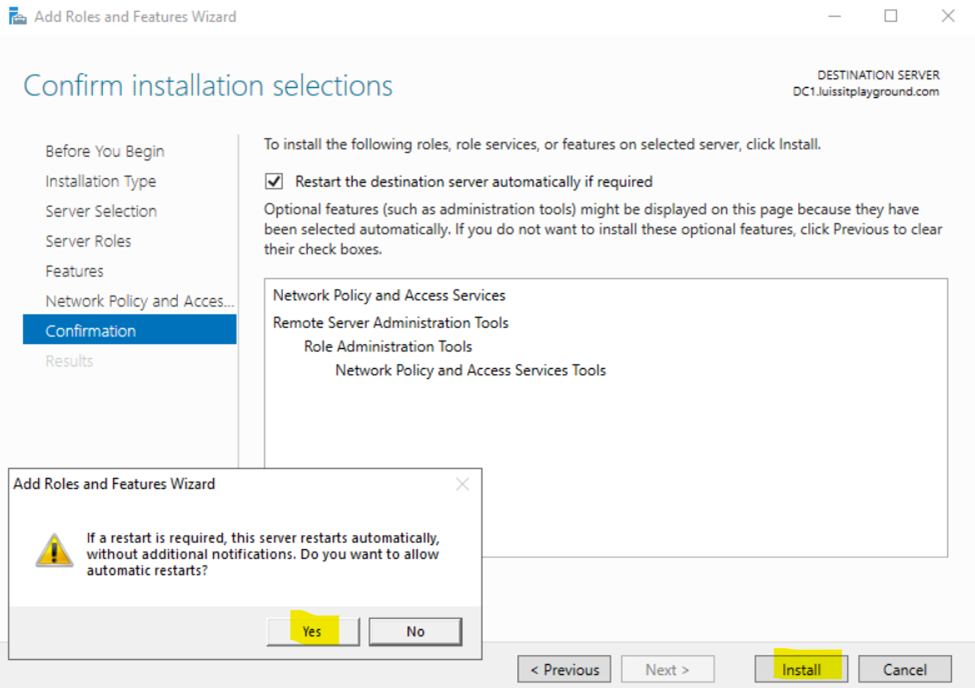
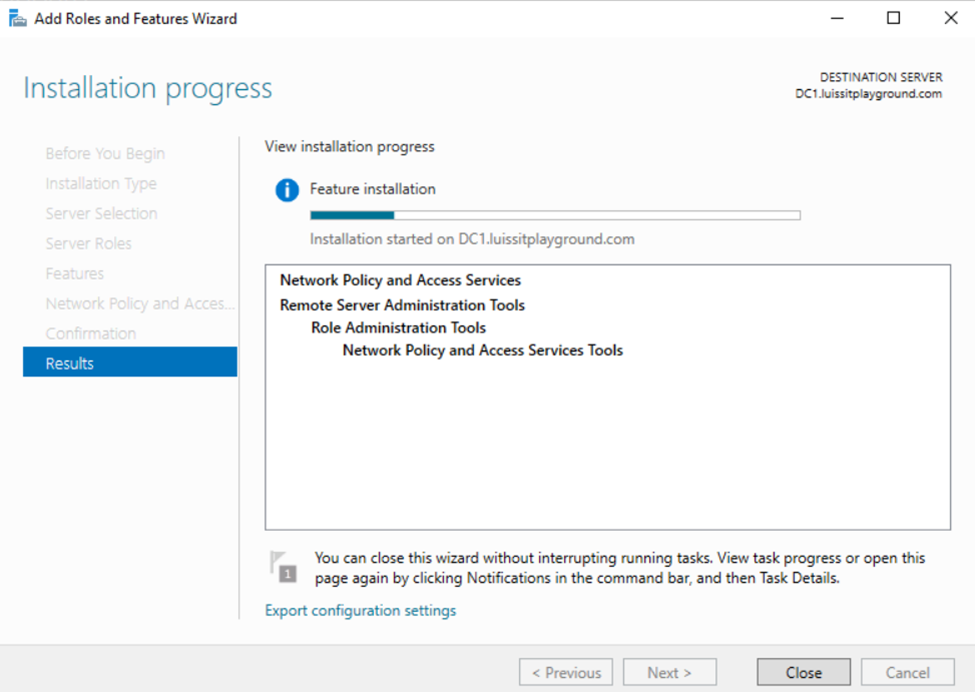
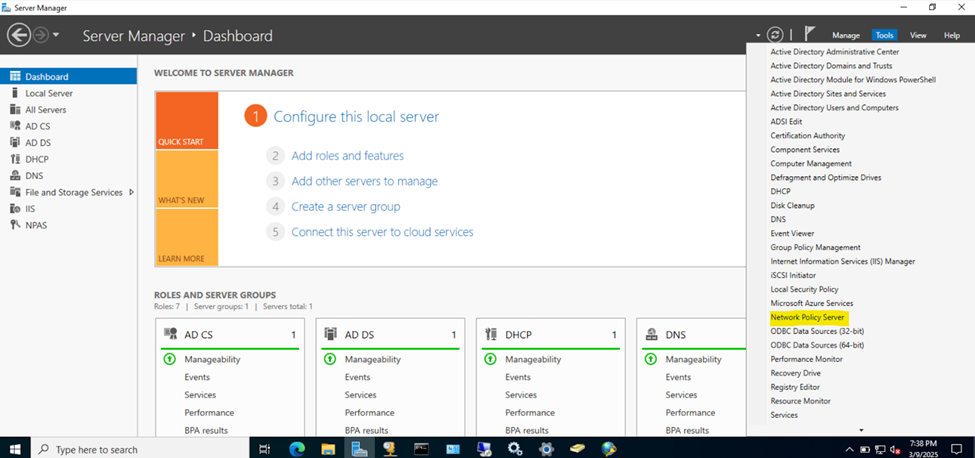
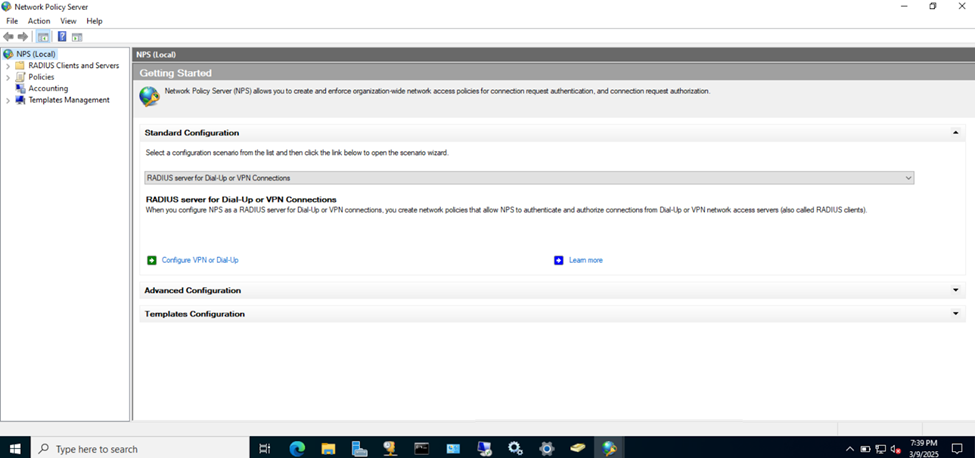
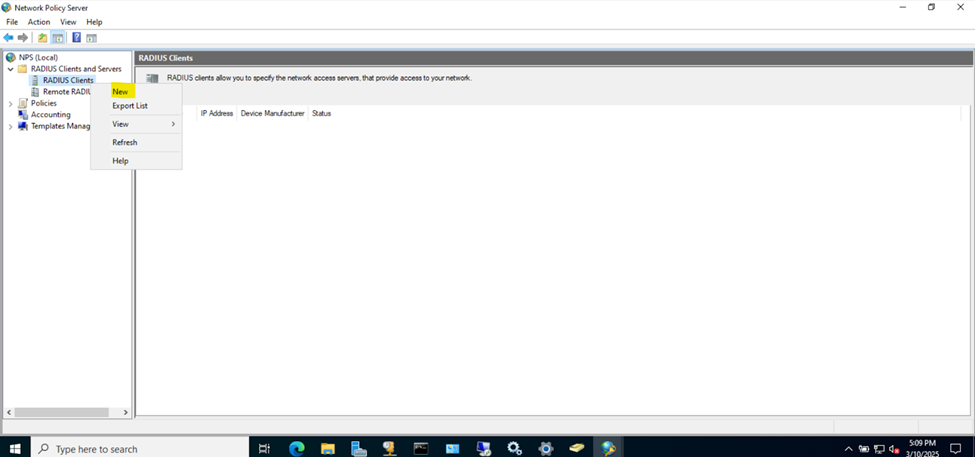
Adding RADIUS Clients
- Resources
- In this demonstration, I will walk-through setting RADIUS clients on the NPS server interface
- RADIUS clients
- In the context of NPS on Windows server, a RADIUS client refers to a device or system that sends authentication, authorization, and accounting (AAA) requests to the NPS server
- These clients are typically network access devices such as:
- VPN servers
- Wireless access points
- Switches
- Firewalls
- When a device (RADIUS client) receives a connection request from a user or device trying to access the network, it sends this request to the NPS server for validation. The NPS server processes the request based on its configured policies and returns an accept or reject response
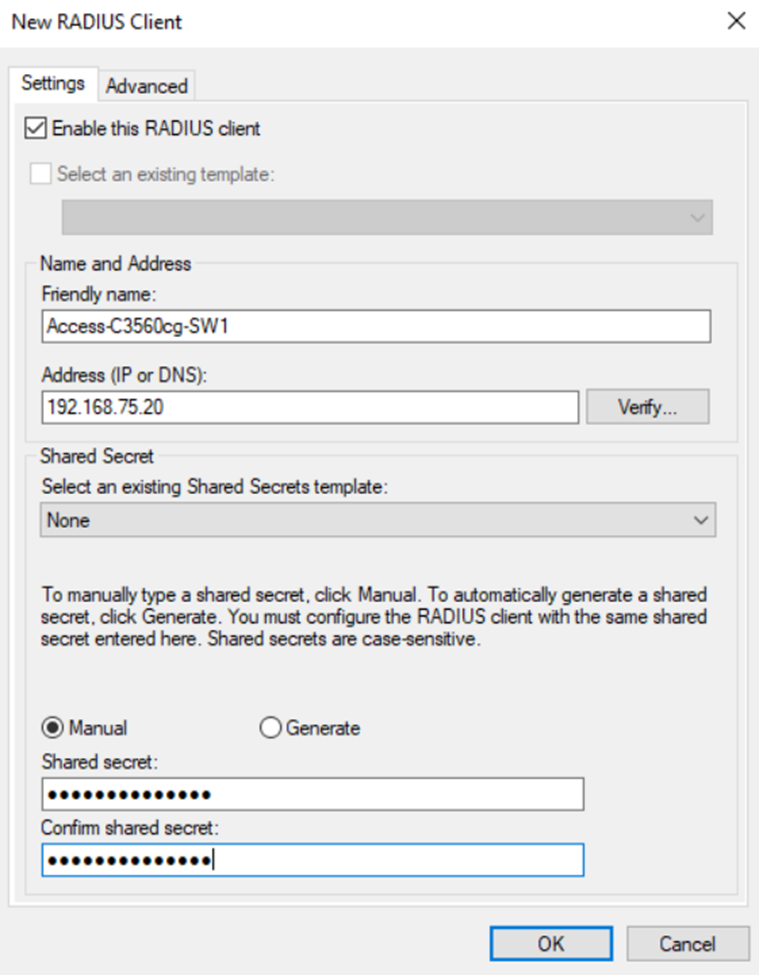
- It is important to set a static IP address for RADIUS clients (Catalyst switches) before adding them as RADIUS clients on the RADIUS server. When you configure a RADIUS server, you need to specify the IP address or hostname of each client
Gameplan
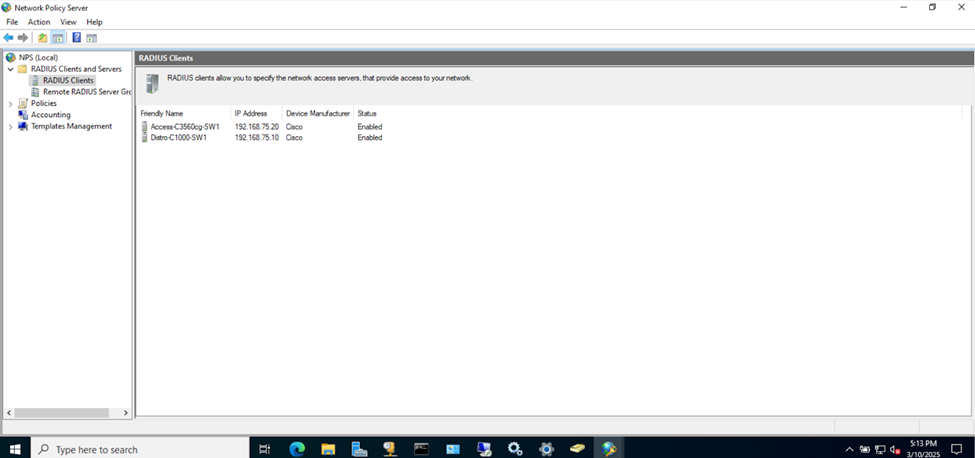
- In this lab exercise, I will be adding the access and distribution Catalyst switches as RADIUS clients from the Corporate LAN
- The end goal is for the NPS server to manage network (AAA) services for administrator users in the Active Directory domain attempting to connect to the switch infrastructure for management
- In a later section, I will demonstrate configuring the Cisco Catalyst switches to communicate with a RADIUS server (NPS) to perform these functions
RADIUS Clients
Defining Active Directory Groups & Users
- Resources
- In this demonstration, I will walk-through adding Active Directory groups and administrator users that can manage the Cisco Catalyst switches using their AD credentials upon post RADIUS configuration
- Network Policy Conditions
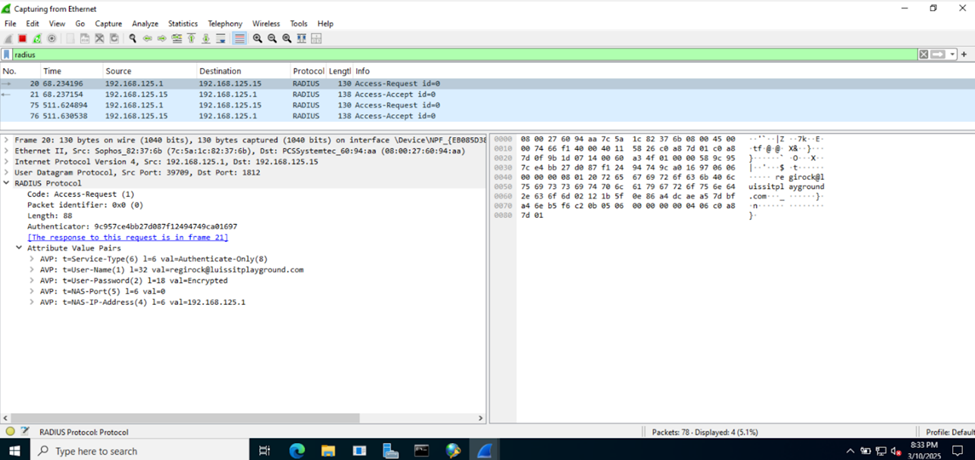
- In NPS on Windows server, network policies are used to define rules that control network access to users and devices. These policies are evaluated when a connection request is made (in this instance, the Sophos firewall will be querying the NPS server when administrators attempt to login to the Sophos firewall once RADIUS authentication is set as the primary method)
- In the context of NPS on Windows server, network policy conditions are criteria used to determine whether a network access policy should be applied to a given connection request
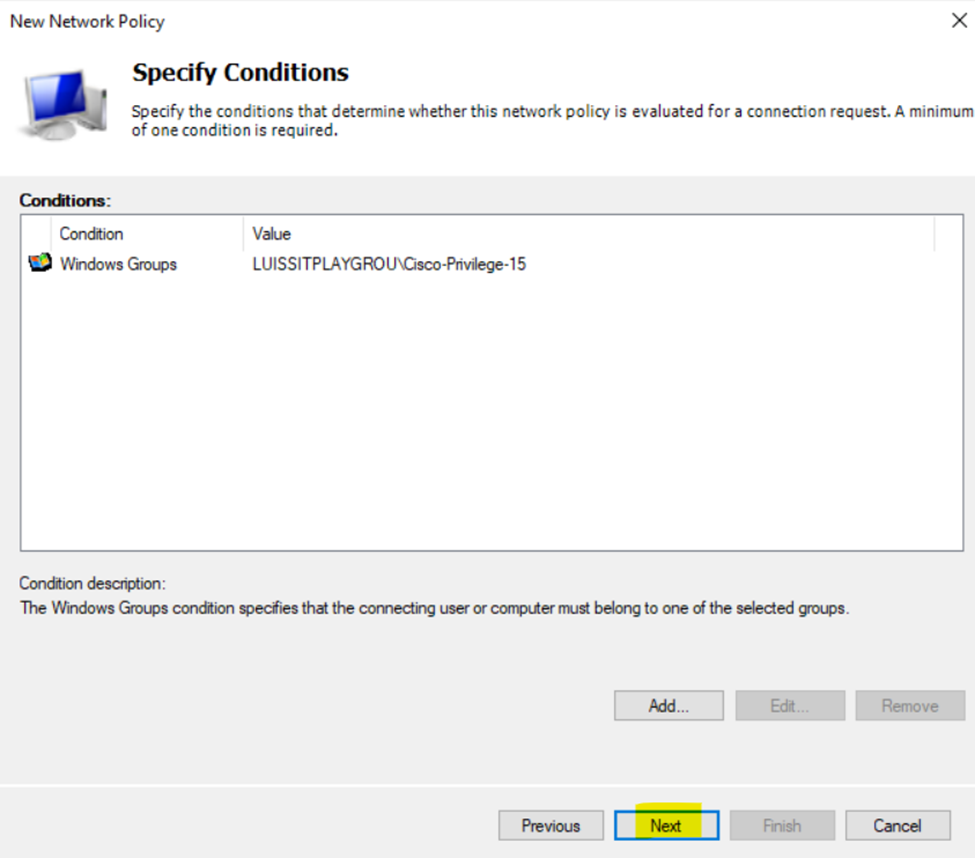
- These conditions can be based on various attributes from the connection request, such as the user's group membership (in this instance, Active Directory groups with administrator members), type of device, or time of day
Gameplan
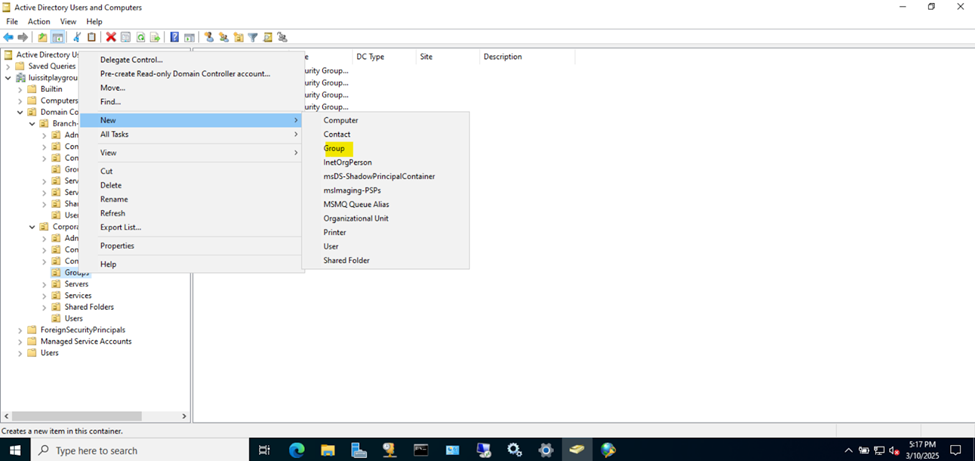
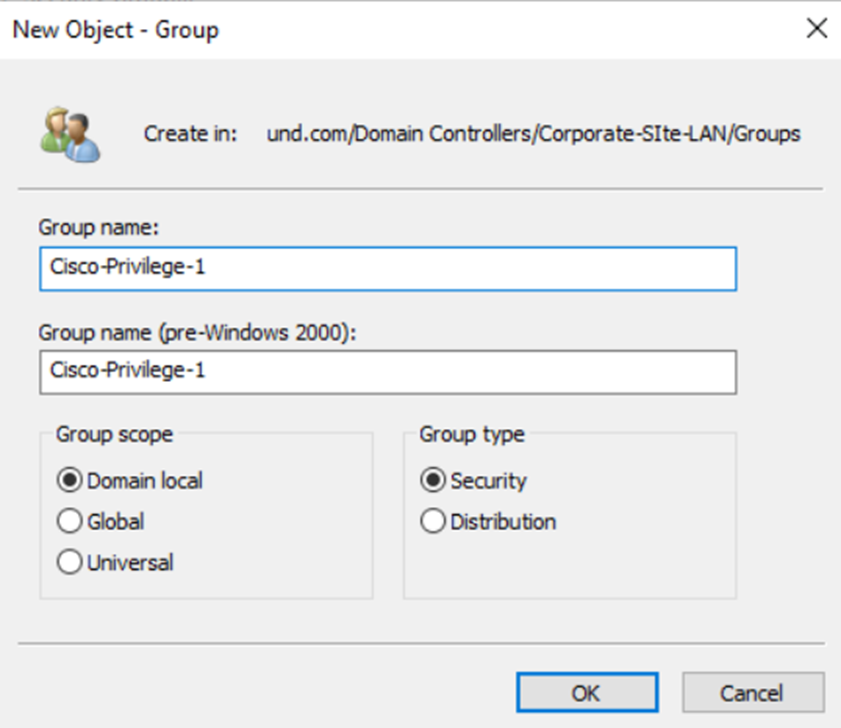
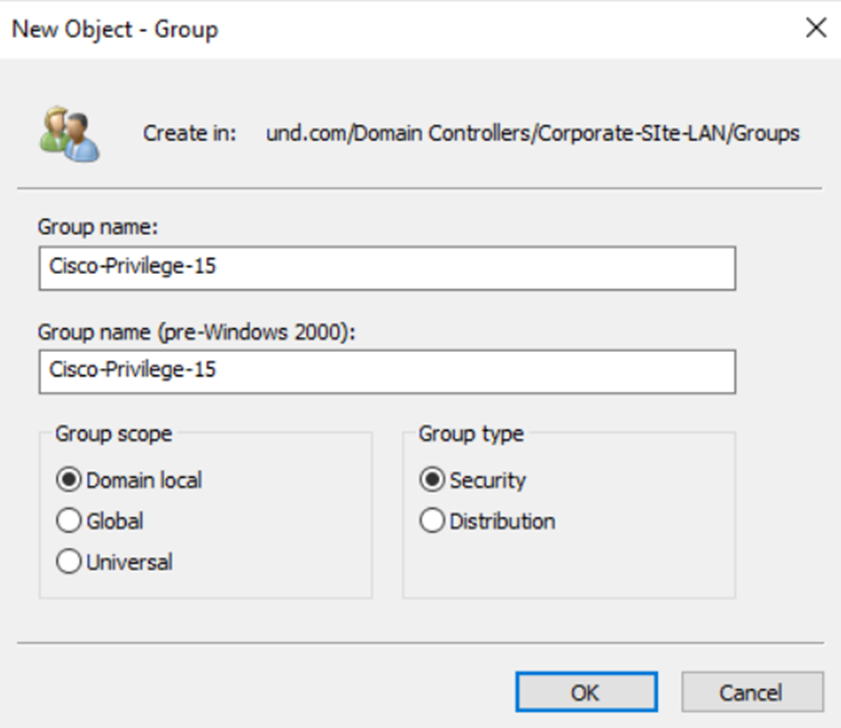
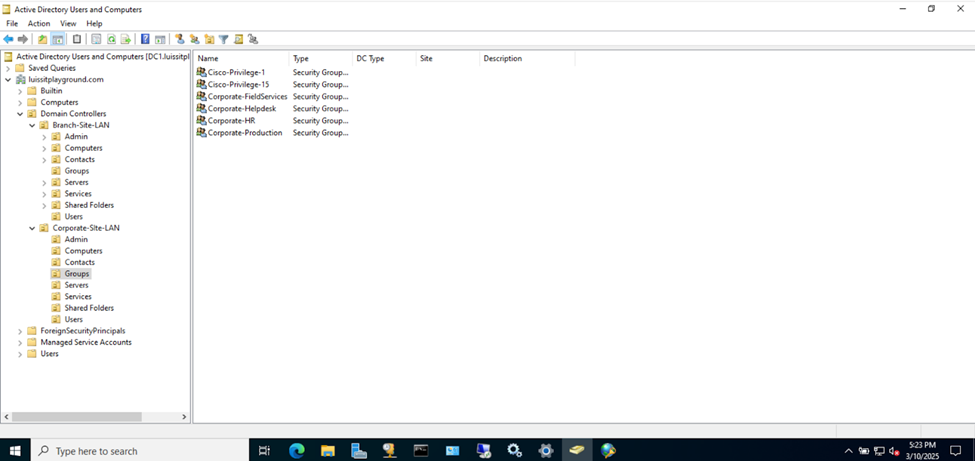
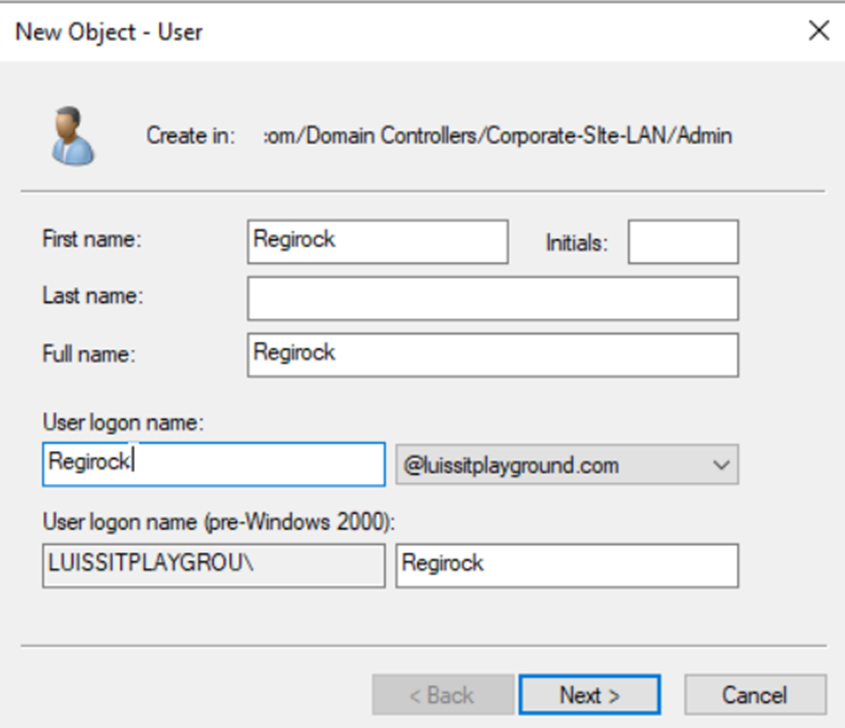
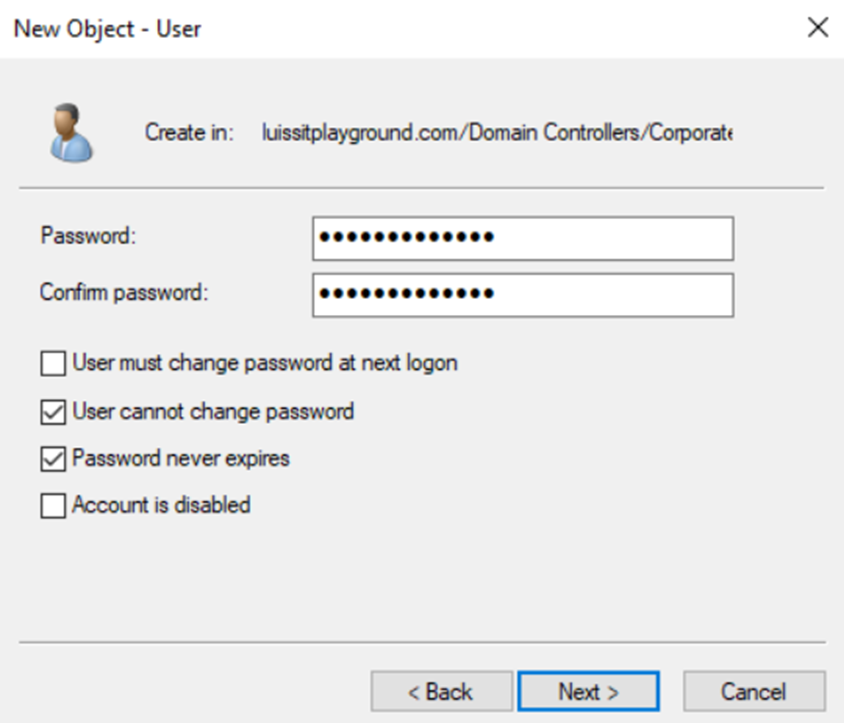
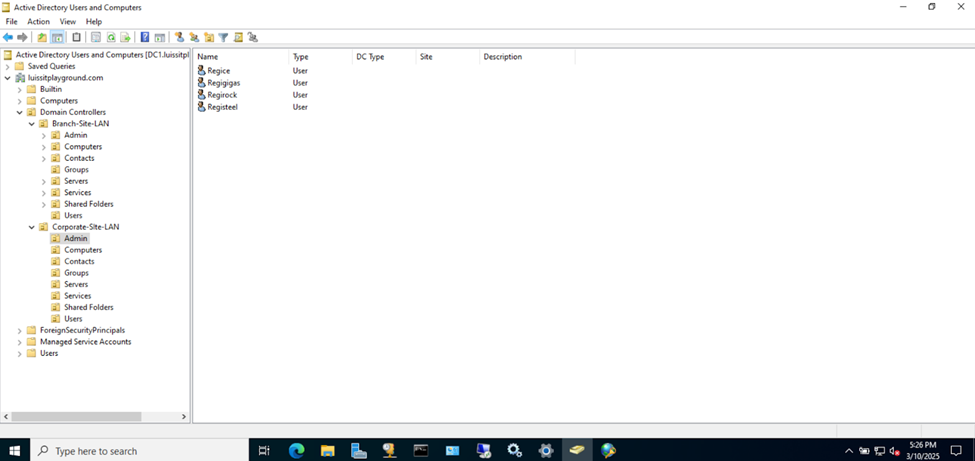
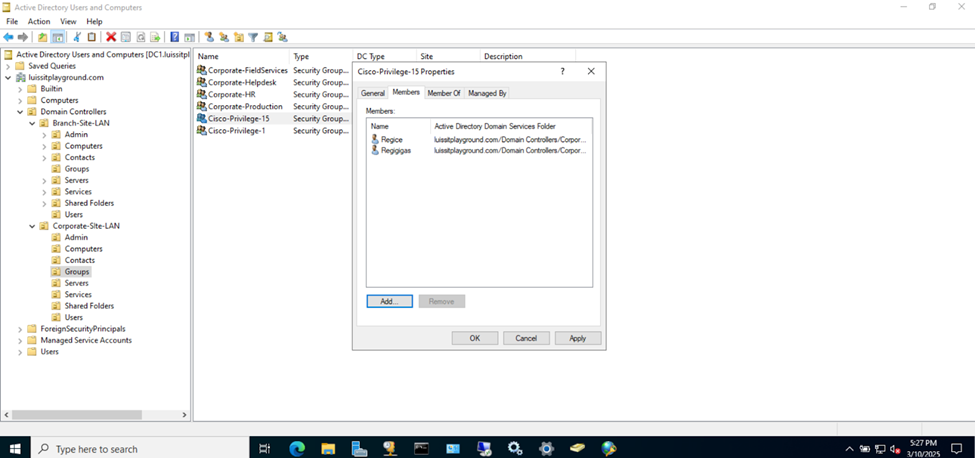
- In this lab exercise, I will be defining two security groups in Active Directory representing Cisco switch privilege levels
- In Cisco switches and routers, privilege levels define the level of access and control that users have over the device's configuration and management. Cisco devices use a system of privilege levels to control what commands a user can execute after logging into the device
- Security Groups to be defined
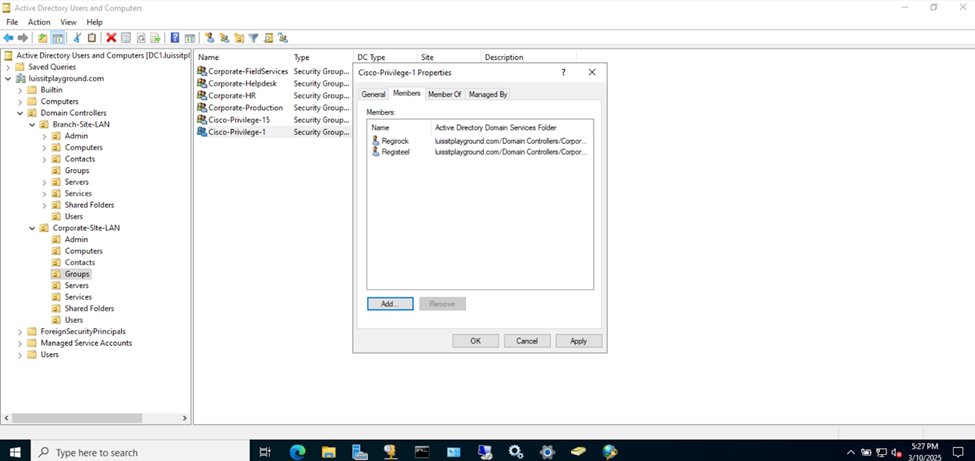
- Cisco-Privilege-1
- This level is typically used for general users who only need to monitor the switch's status or check for information without making any configuration changes
- Cisco-Privilege-15
- This is typically assigned to administrators or users who need full control over the device where most configuration tasks are done at this level
- Cisco-Privilege-1
- In a later section, I will demonstrate defining (Sophos Device Access profiles) for administrators, one profile representing a read-only role to the firewall Web admin control center and the other profile representing a full control role. With the AD groups defined, the 'Cisco-Privilege-1' group will be tied to the 'read-only' role whereas the 'Cisco-Privilege-15' group will be tied to the 'full control' role for firewall monitoring and configuration
Active Directory Groups & Users
Configuring NPS Network Policies via Windows Groups
- Resources
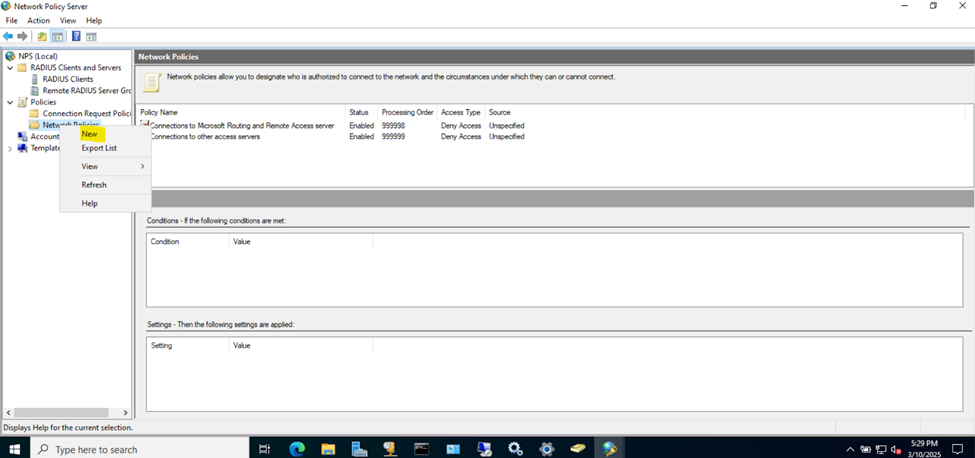
- In this demonstration, I will walk-through defining an NPS network policy for each of the two Active Directory security groups defined in the previous section
- Network Policy Conditions
- In NPS on Windows server, network policies are used to define rules that control network access to users and devices. These policies are evaluated when a connection request is made (in this instance, the Sophos firewall will be querying the NPS server when administrators attempt to login to the Sophos firewall once RADIUS authentication is set as the primary method)
- In the context of NPS on Windows server, network policy conditions are criteria used to determine whether a network access policy should be applied to a given connection request
- These conditions can be based on various attributes from the connection request, such as the user's group membership (in this instance, Active Directory groups with administrator members), type of device, or time of day
Gameplan
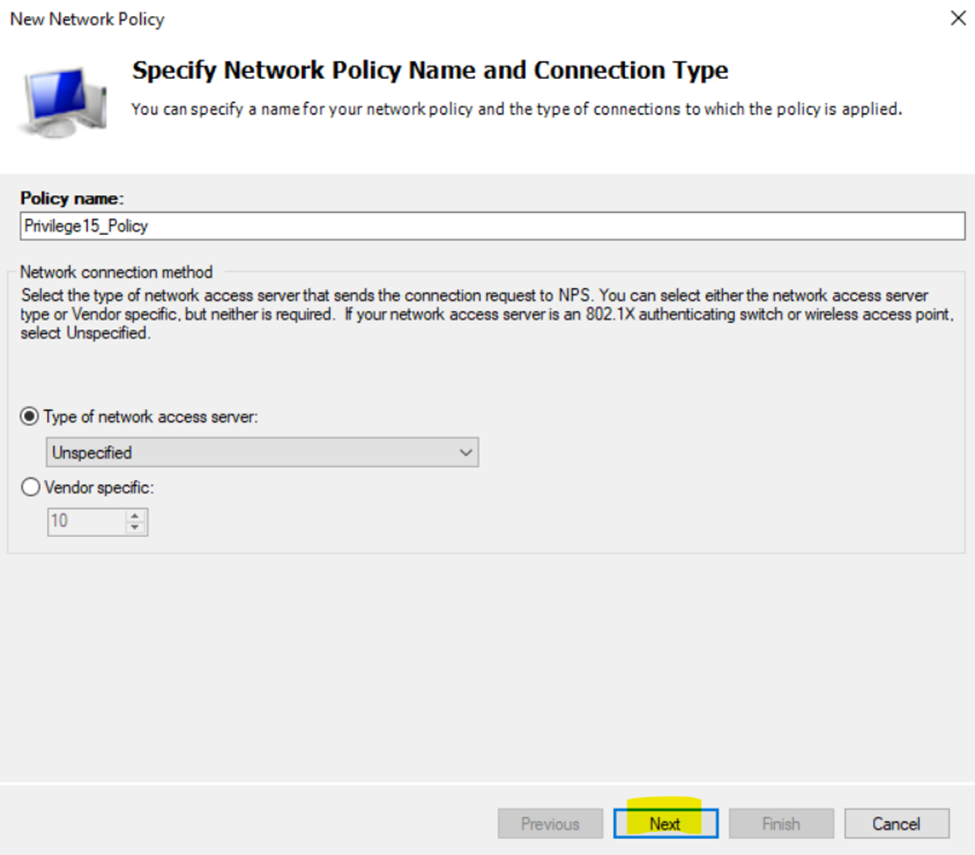
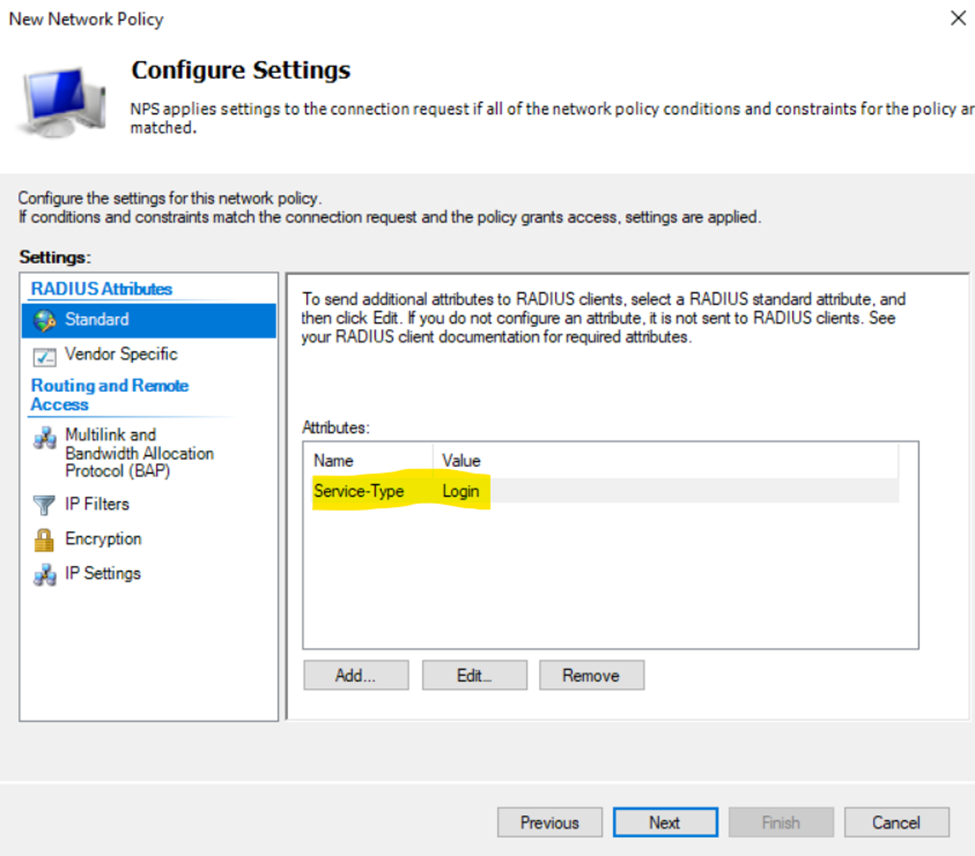
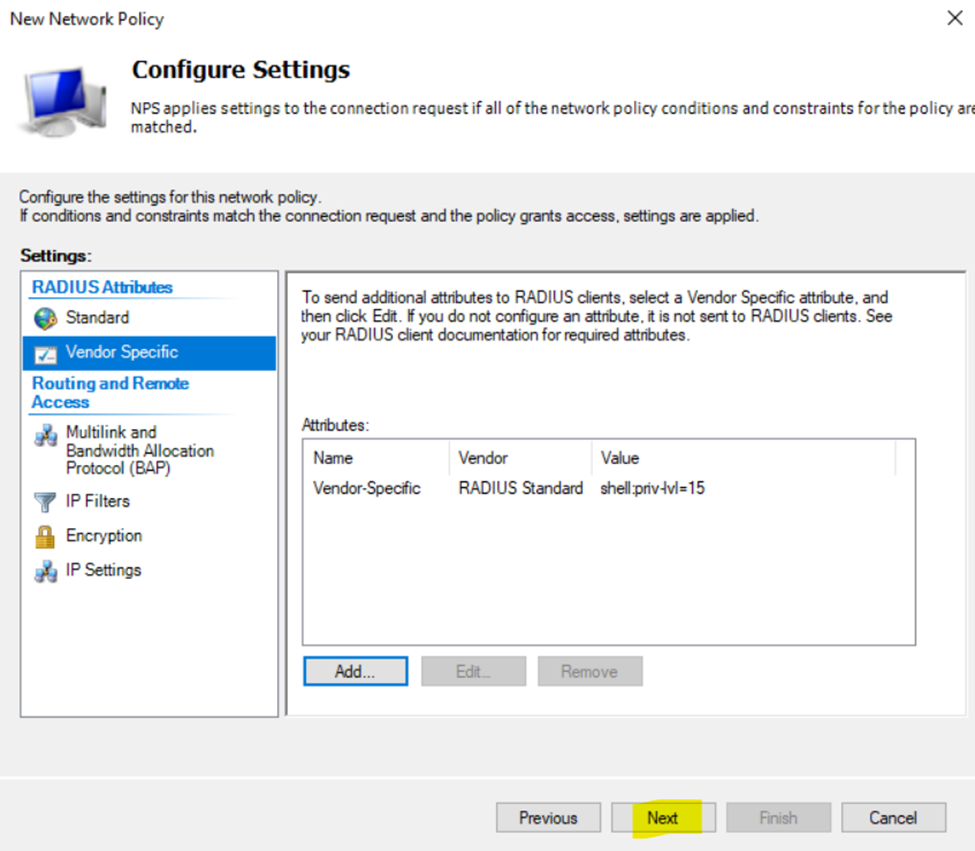
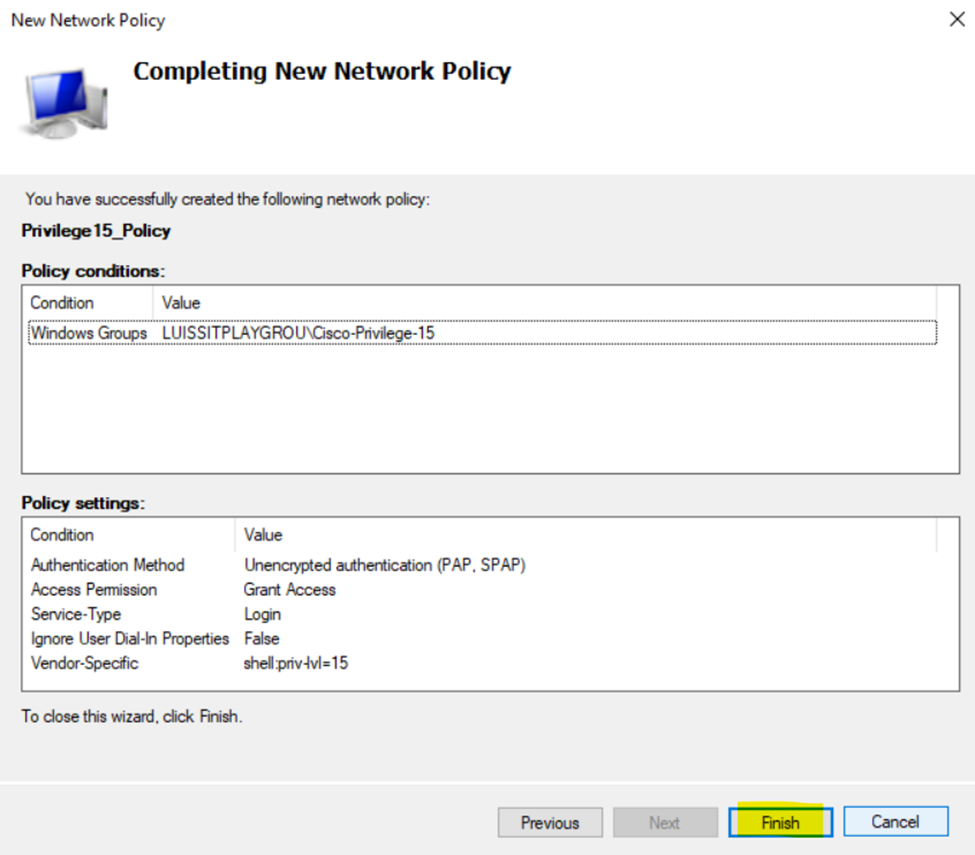
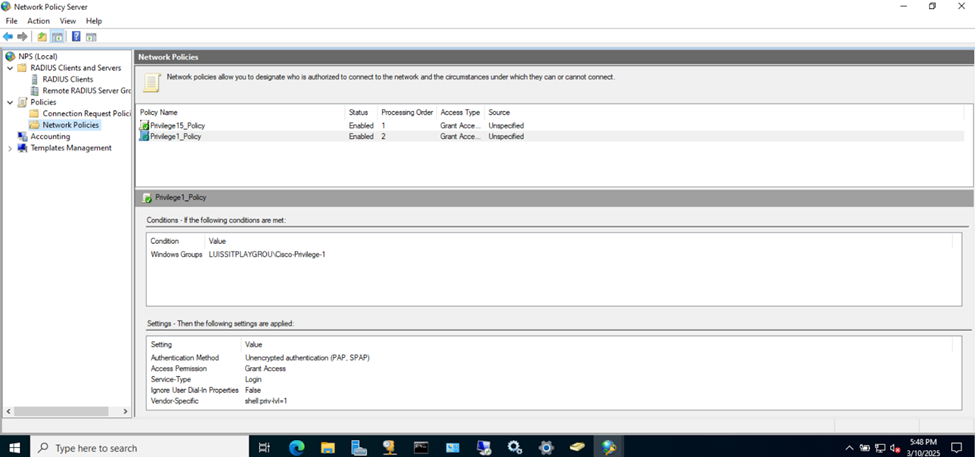
- In this lab exercise, I will be defining a 'Privilege15_Policy' and 'Privilege1_Policy' network policy and associating each policy with their respective Windows Groups (AD groups) for their network policy conditions
- In the next section, I will demonstrate configuring RADIUS on the Cisco Catalyst switches to test AAA using the Active Directory user credentials of the administrators associated with the 'Privilege15_Policy' and 'Privilege1_Policy' network policies
NPS Network Policies
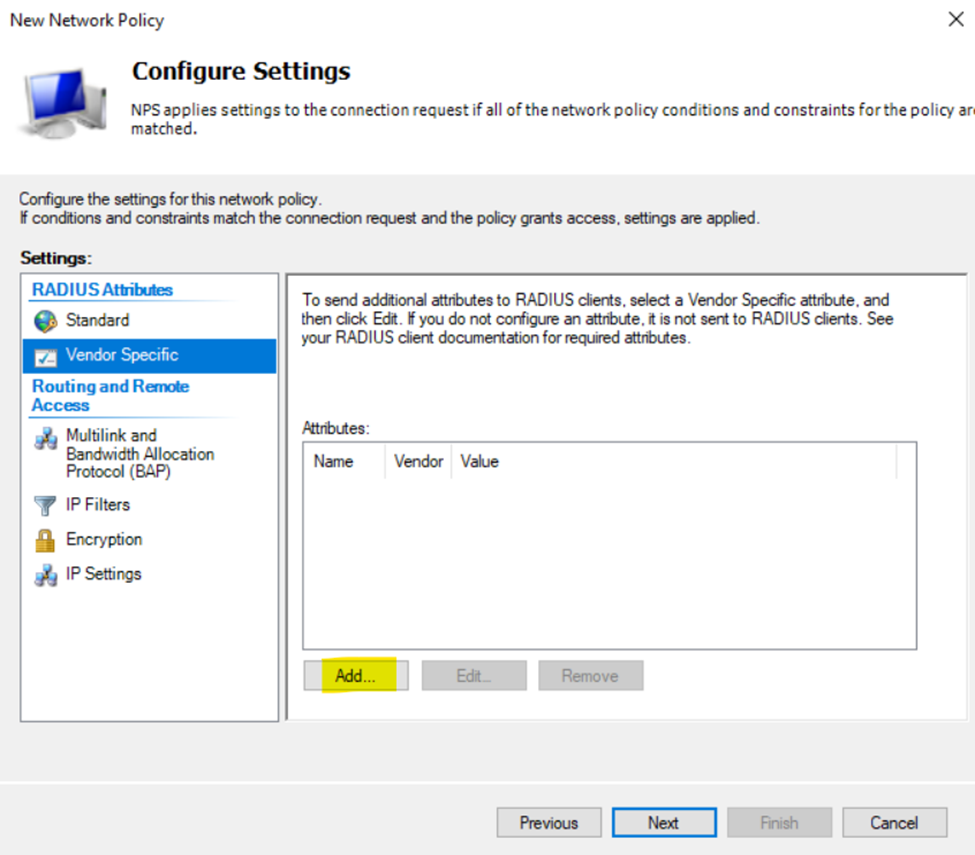
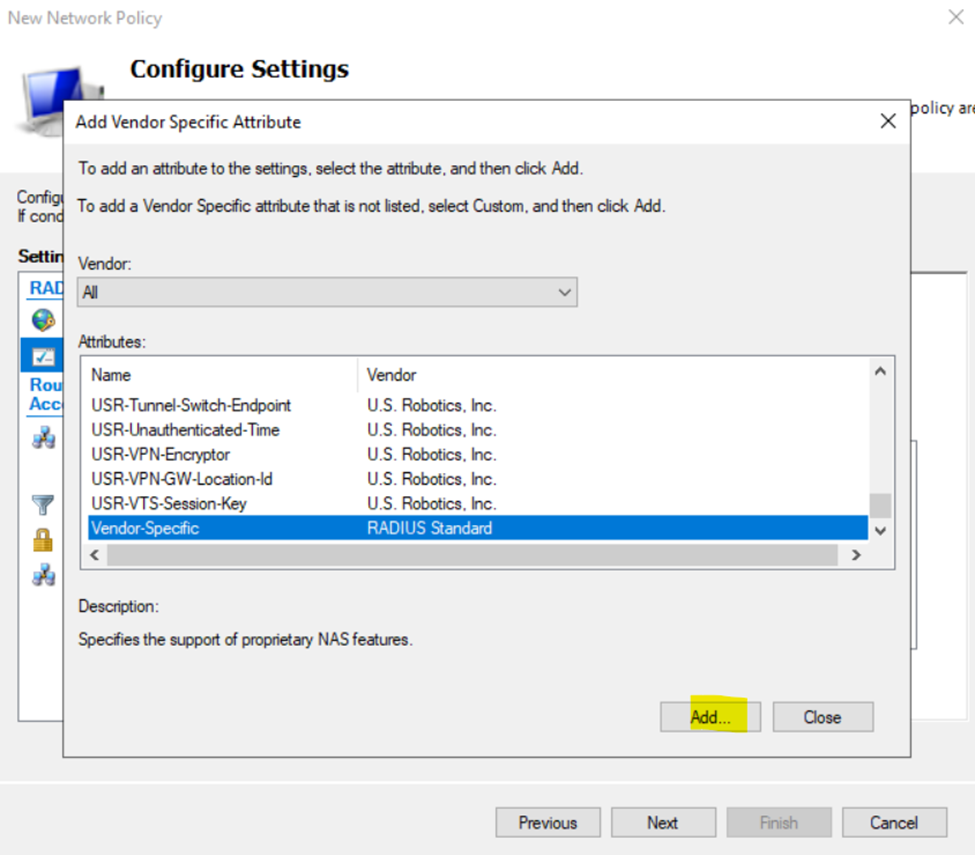
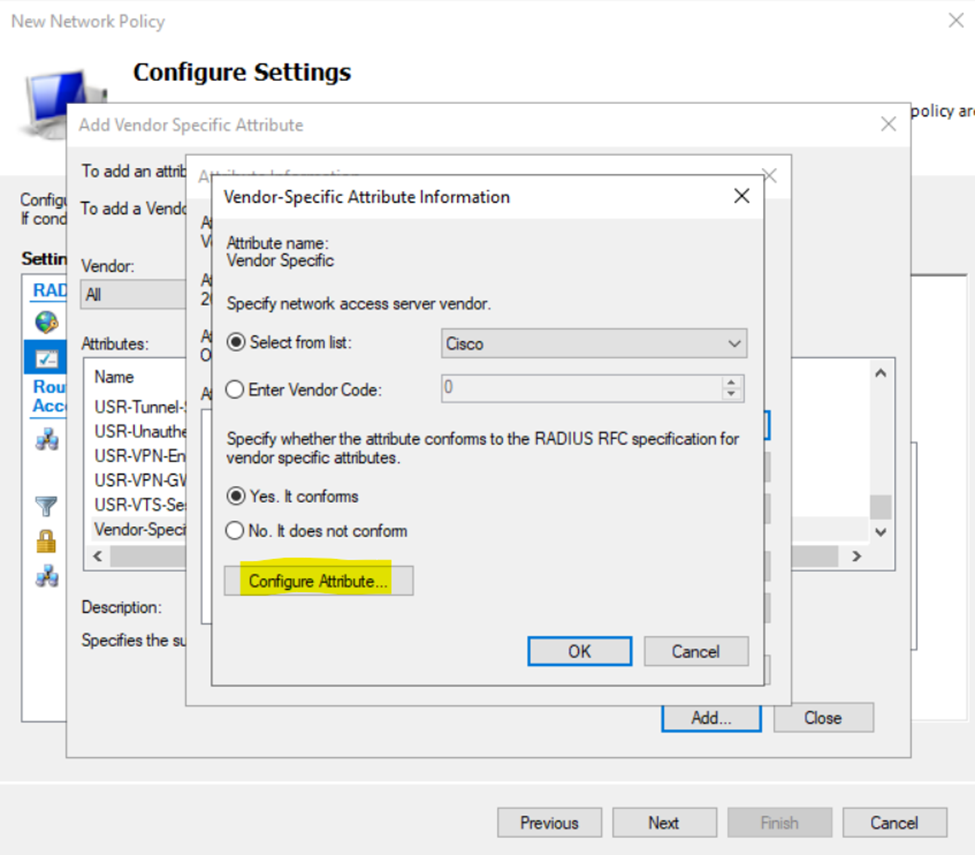
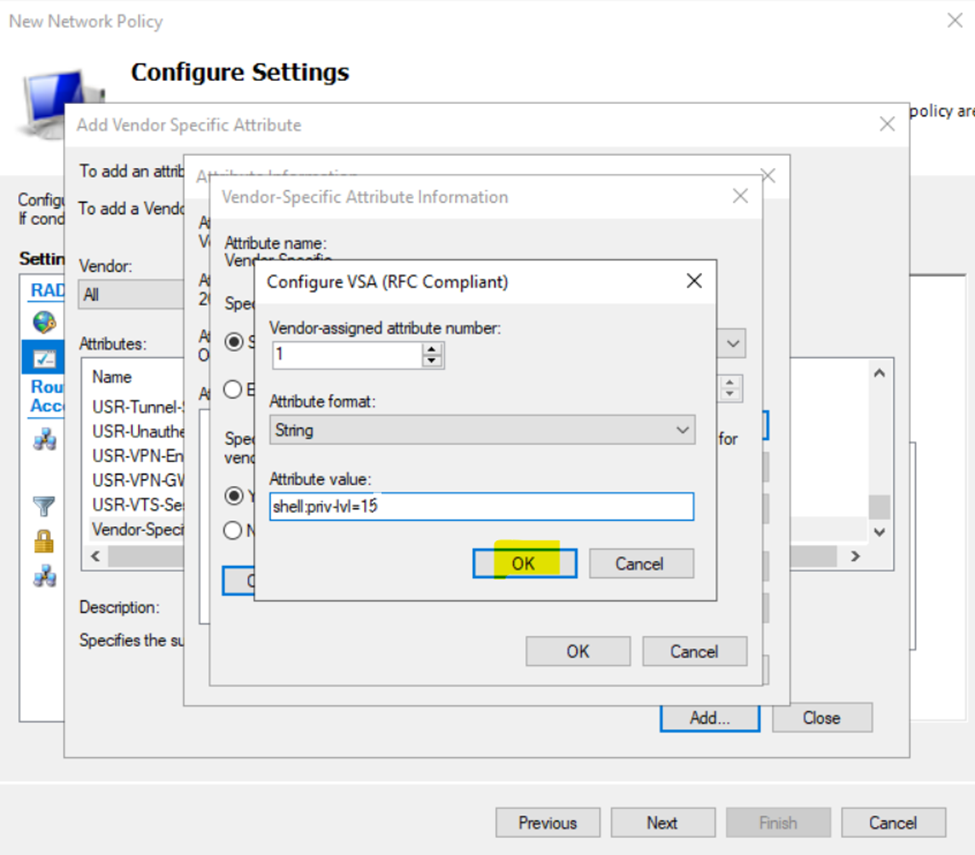
Configuring Cisco AAA
- Resources
- In this demonstration, I will walk-through configuring AAA on Cisco Catalyst switches acting as a RADIUS client
- To configure RADIUS for Cisco Catalyst switches, you'll need to configure both the RADIUS server (in this instance, NPS for windows server) and the switch itself. Upon configuring the switch, the switch will act as a RADIUS client, sending authentication, authorization, and accounting (AAA) requests to the RADIUS server
Gameplan
- In this lab exercise, I will be defining a AAA on the access and distribution Catalyst switches located in the Corporate LAN
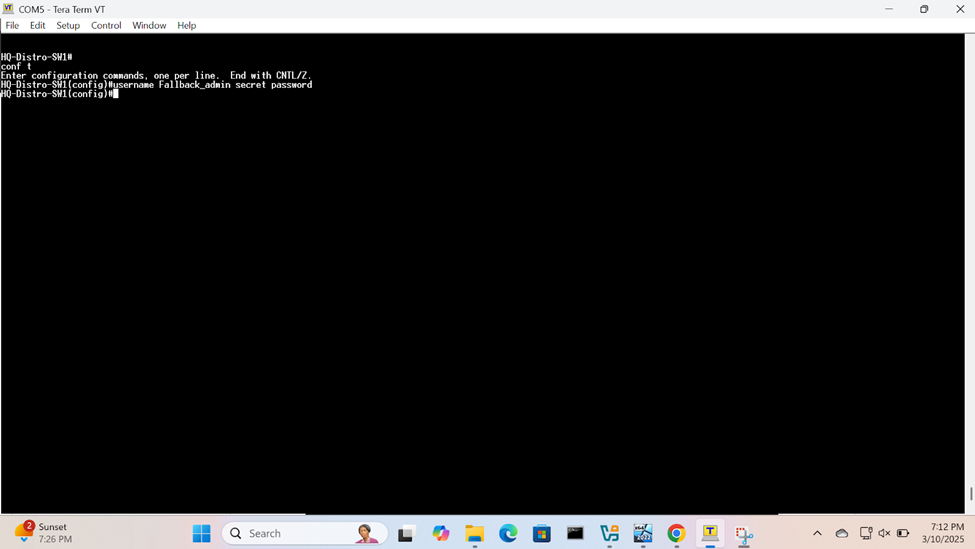
- A local user account will be defined on each switch in cases when the RADIUS server becomes unreachable or experiences failures causing the RADIUS client (switch) from successfully querying the RADIUS server for credential lookup
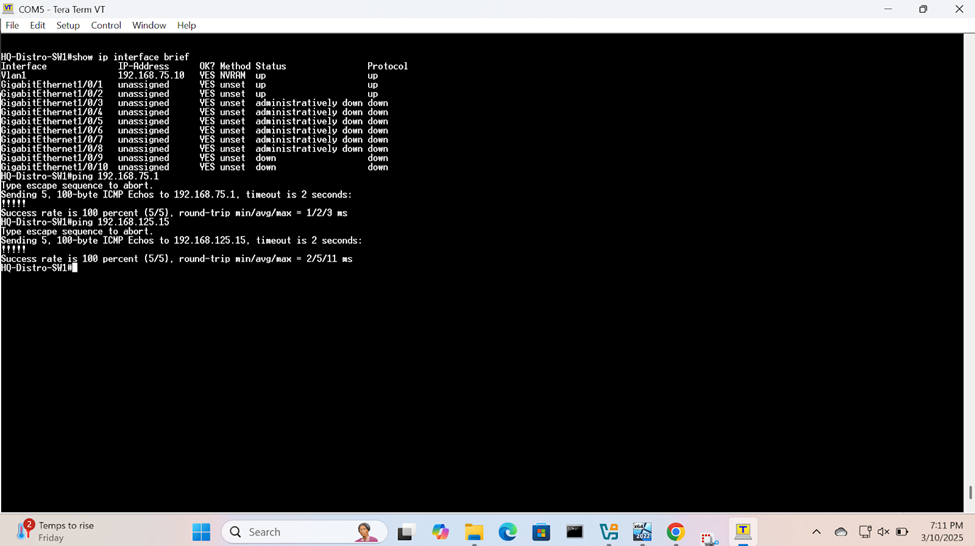
- It is best practice to test RADIUS server ICMP connectivity beforehand on the switch to ensure the switch is able to effectively able to communicate with the server
- After successful configuration, I will demonstrate verifying and testing the implementation using the Active Directory credentials of an administrator belonging to the 'Cisco-Privilege-1' and 'Cisco-Privilege-2' groups
- Overview of Switch AAA Configuration
- In the next section, I will demonstrate defining Device Access profiles on the Sophos Firewall for the Sophos RADIUS authentication implementation
Test Connectivity to RADIUS Server
Define Local User
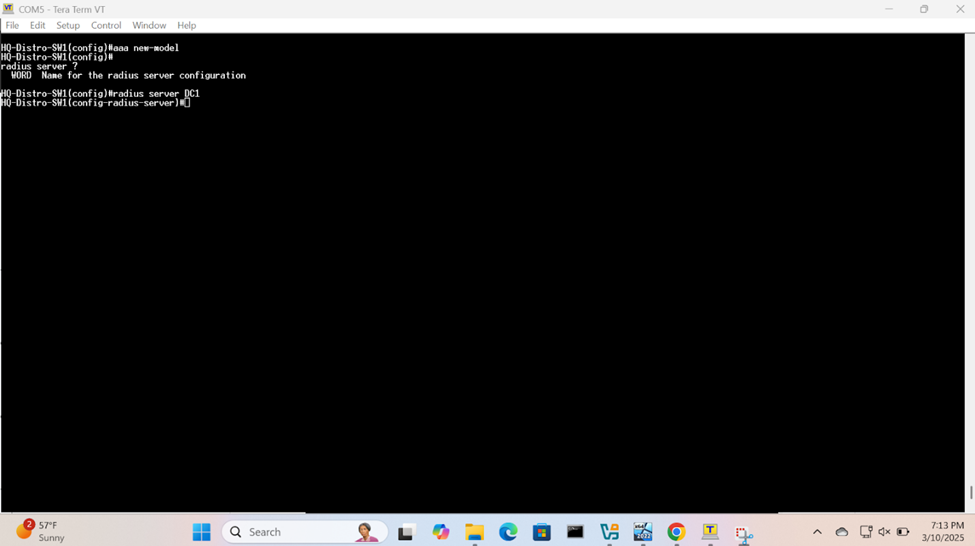
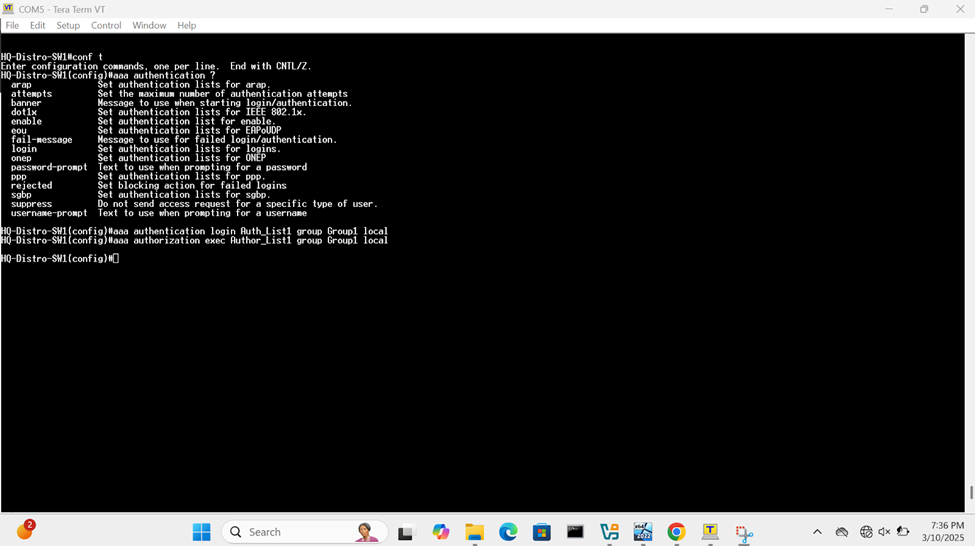
Define AAA
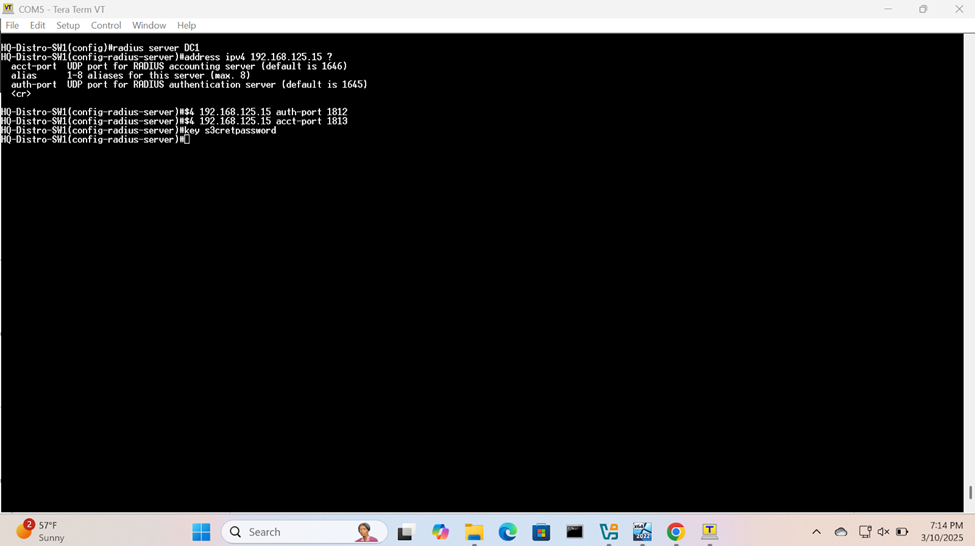
Define AAA Server Parameters
Define AAA Group Parameters
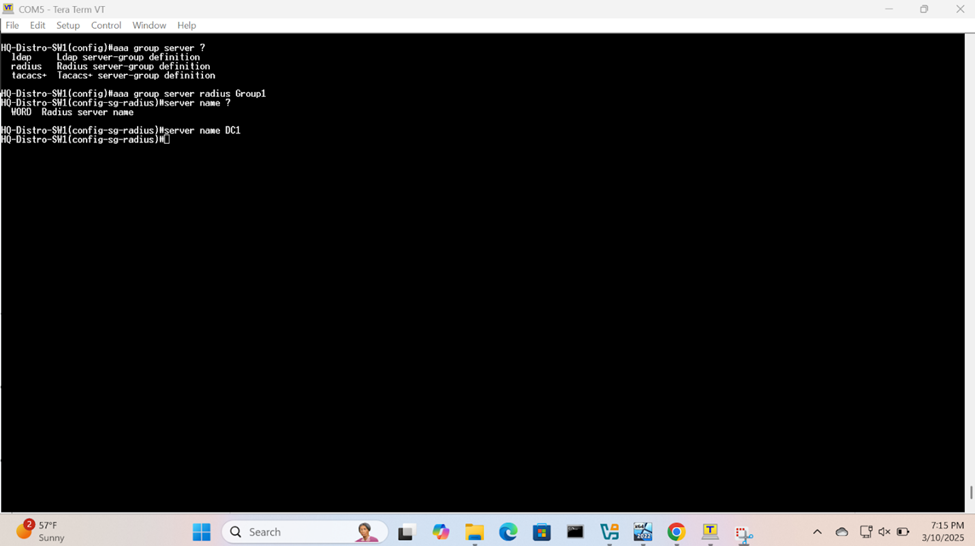
Define AAA Methods
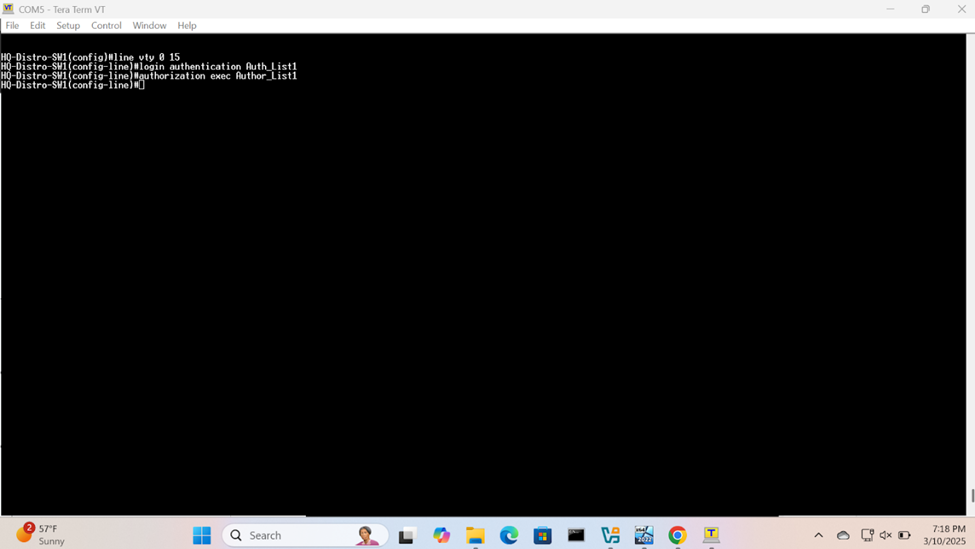
Apply AAA Methods
(Privilege-1) Test Cisco AAA with Wireshark
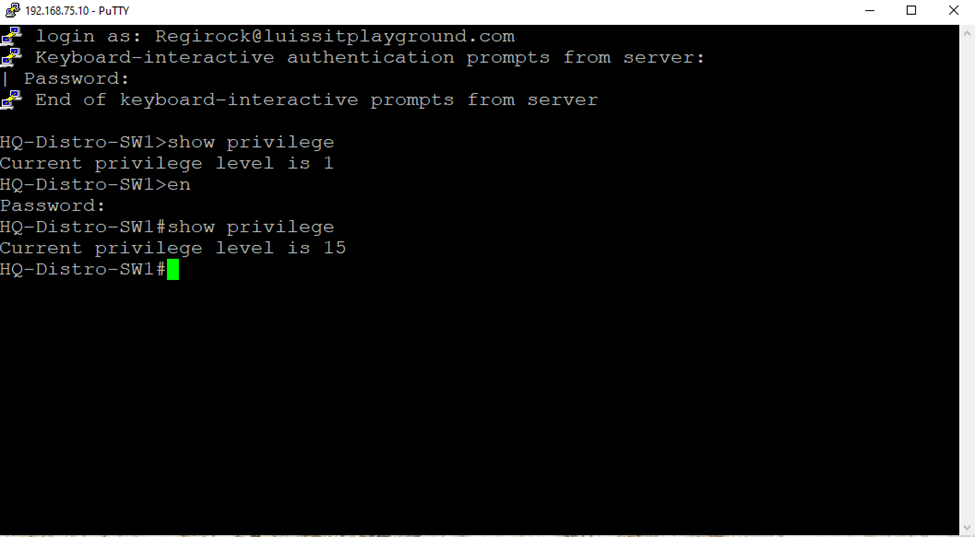
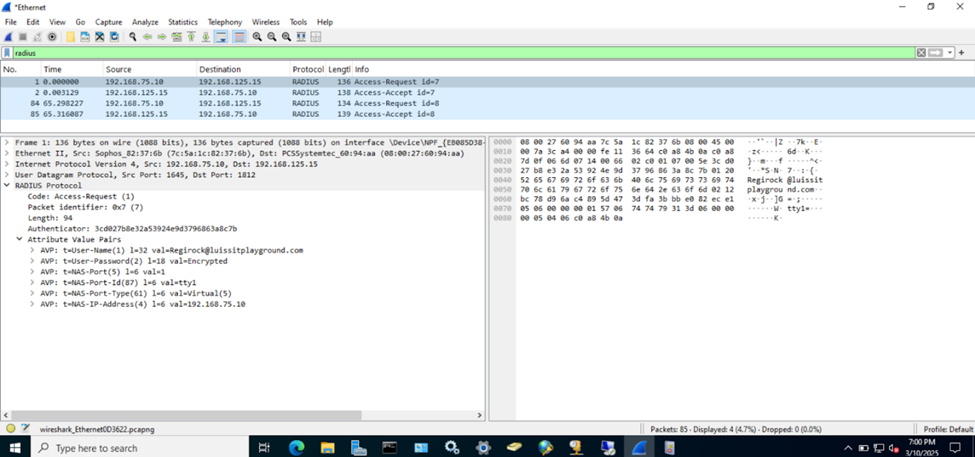
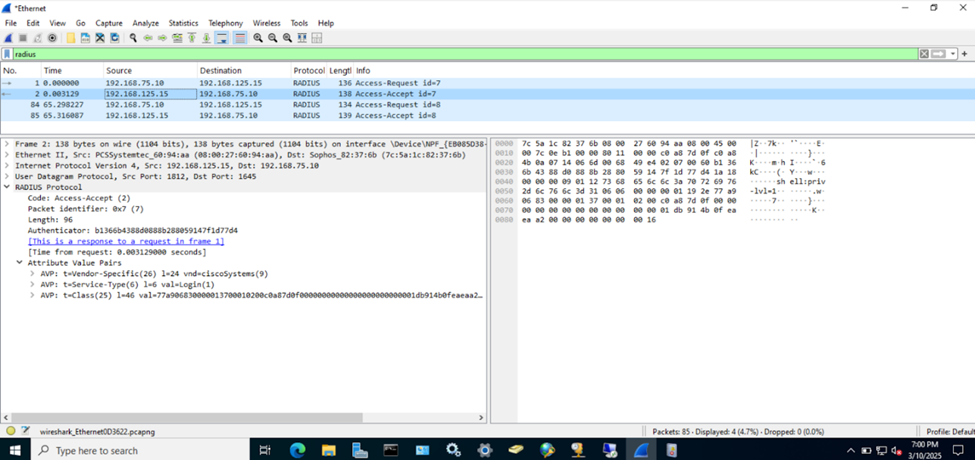
(Privilege-15) Test Cisco AAA with Wireshark

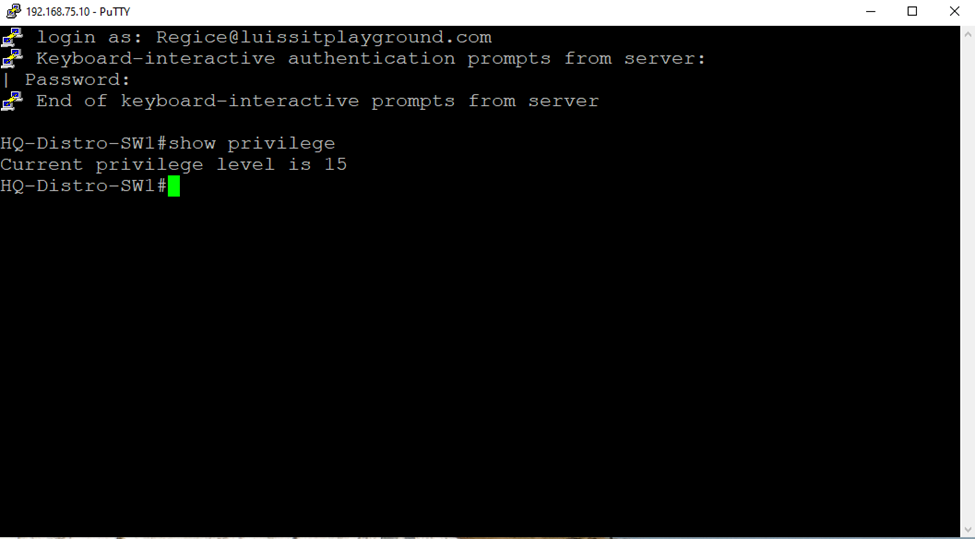
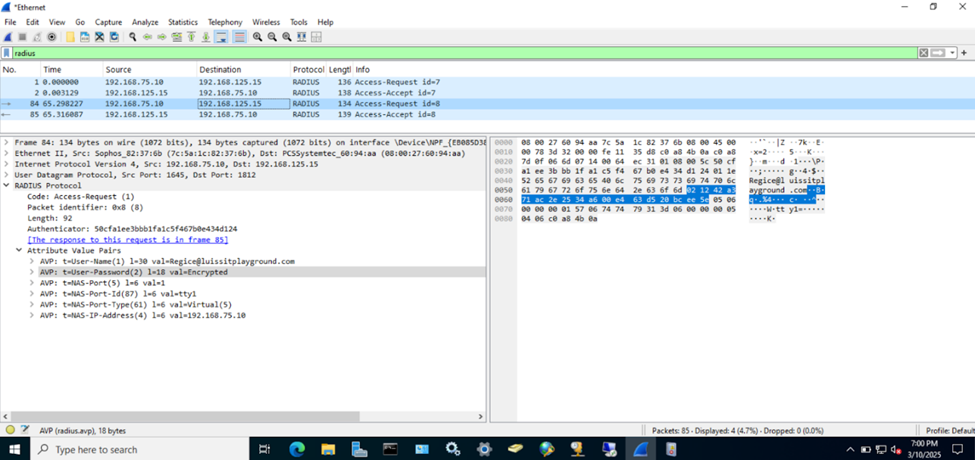
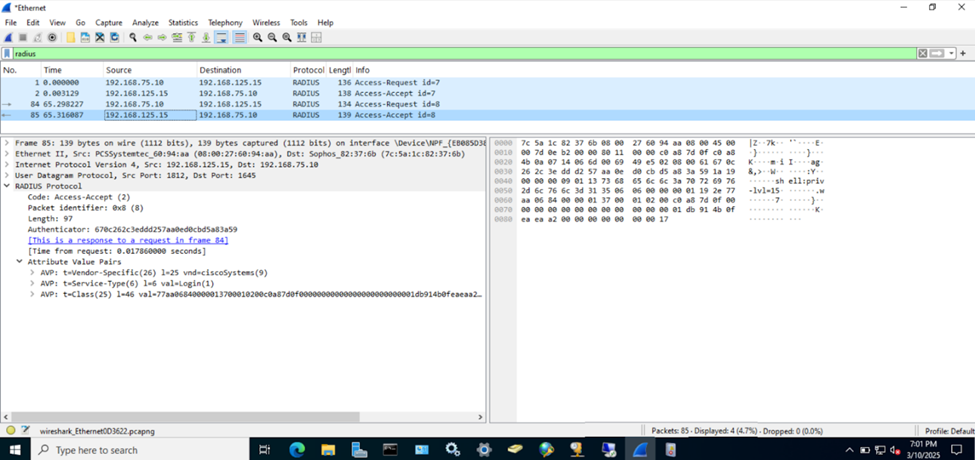
(Local User) Test Cisco AAA Failure

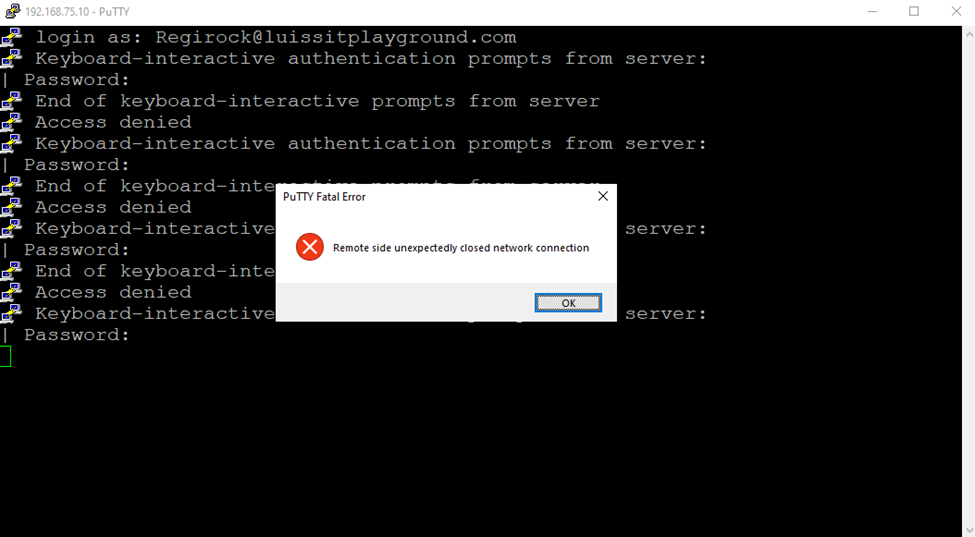
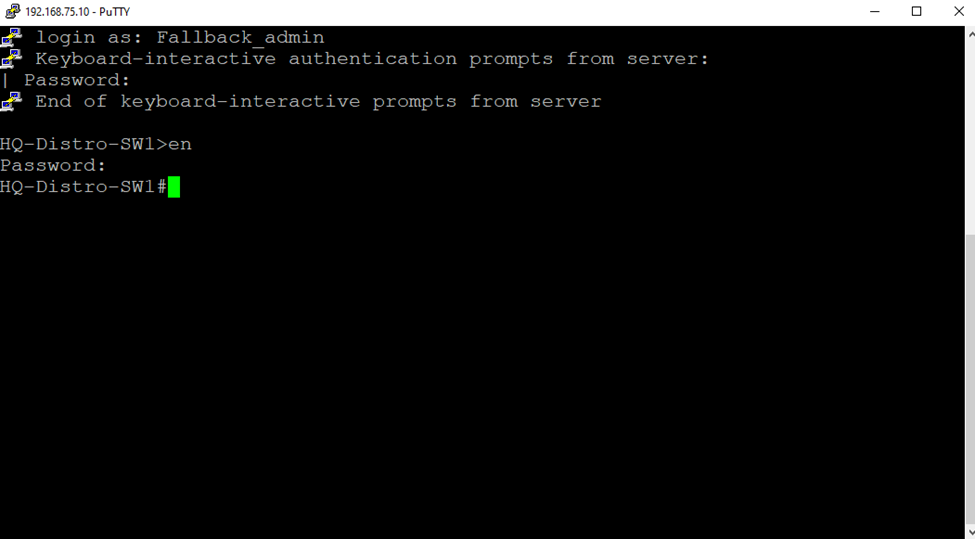
Defining Sophos Device Access Profiles
- Resources
- In this demonstration, I will walk-through defining Device Access profiles on the Sophos Firewall to distinguish the rights that will be associated with the two Active Directory groups that are used in the RADIUS NPS network policies
- Device Access Profiles
- With Sophos Device Access Profiles, you can create role-based access to the firewall for administrators
- You can create custom profiles and specify their access to the web admin console on a granular basis
- Upon defining profiles, I will demonstrate testing the RADIUS authentication implementation of the Sophos Firewall
Gameplan
- In this lab exercise, I will be defining two Device Access profiles with different roles to the web admin console of the Sophos Firewall
- The 'Network-Admins-Readonly' profile will allow 'Cisco-Privilege-1' administrators to view and monitor configurations and settings without the ability to make any changes to the firewall configuration. If a support technician needs to troubleshoot an issue, they can examine the logs or settings without having the ability to change firewall rules or policies that could cause unintended disruptions
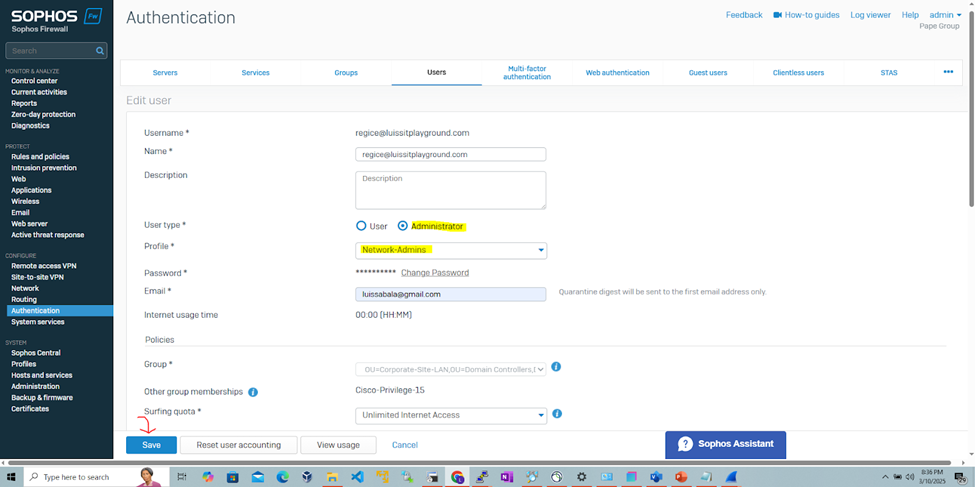
- The 'Network-Admins' profile will allow 'Cisco-Privilege-15' administrators to fully configure, manage, and monitor the firewall settings and is crucial that full control rights are assigned to only trusted and properly authorized users through means such as RADIUS
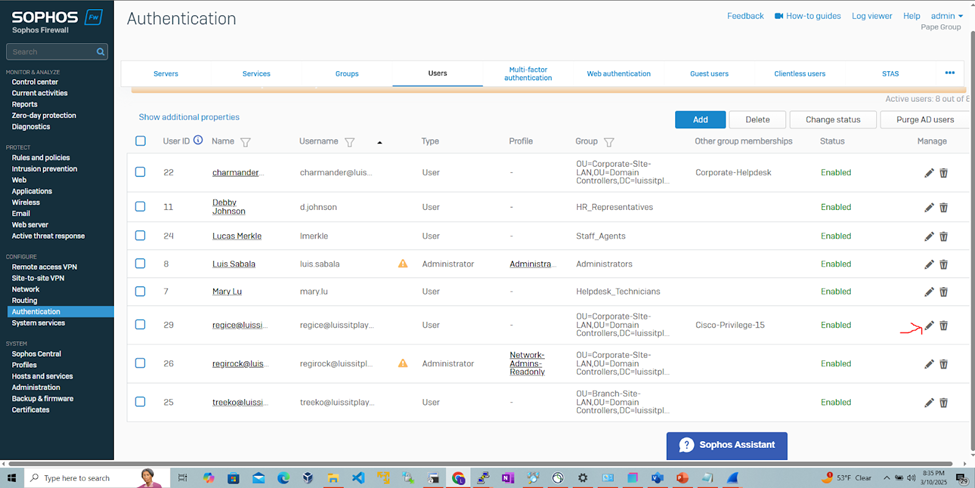
- The RADIUS server will be defined on the Sophos Firewall in which administrators 'Regirock' and 'Regice' from both Windows groups can added to the authentication users list after signing in to the Sophos Captive portal
- Once signed-in, I will demonstrate manually setting the administrator profiles of the authenticated users that specifies the roles each have to the Sophos web admin console
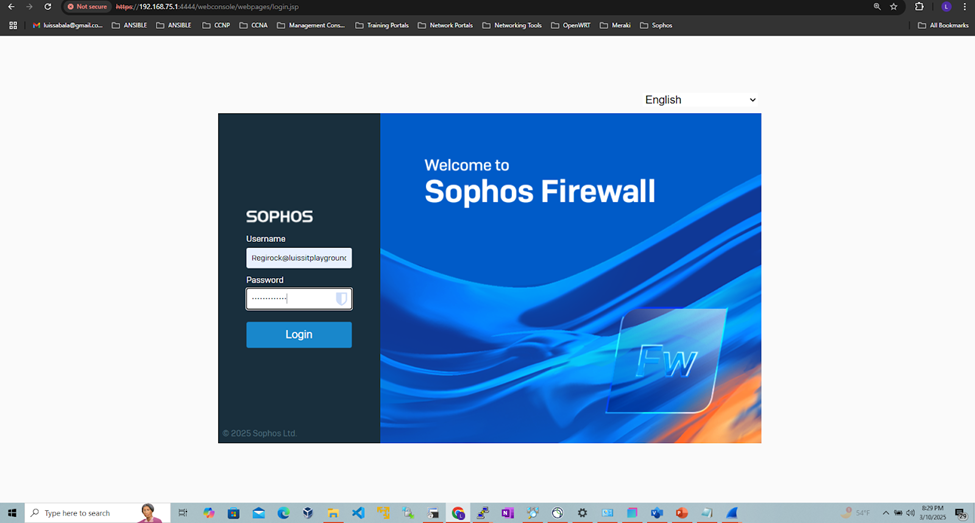
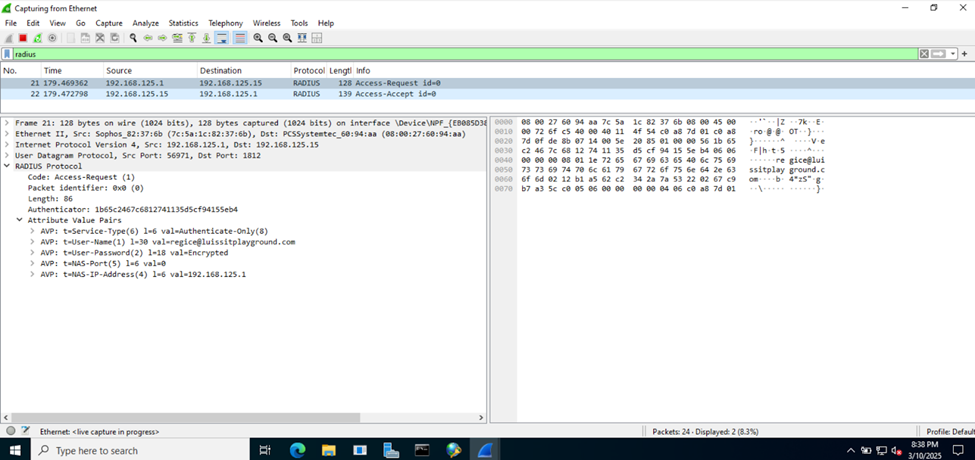
- Upon setting these profiles, RADIUS verification and rights will take place once the administrators sign in to the Sophos web admin console
- Overview of RADIUS Authentication
- Define Device Access Profiles for RADIUS Admins
- Add RADIUS Authentication Server
- Add Sophos RADIUS Client
- Set Sophos Primary Authentication Methods
- Import Active Directory Groups for RADIUS
- Captive Portal & Assigning Profiles for RADIUS
- (Privilege 1 - Read-only) RADIUS Verification
- (Privilege 15 - Full-control) RADIUS Verification
- Sophos Firewall Authentication Logs
Define Device Access Profiles for RADIUS Admins
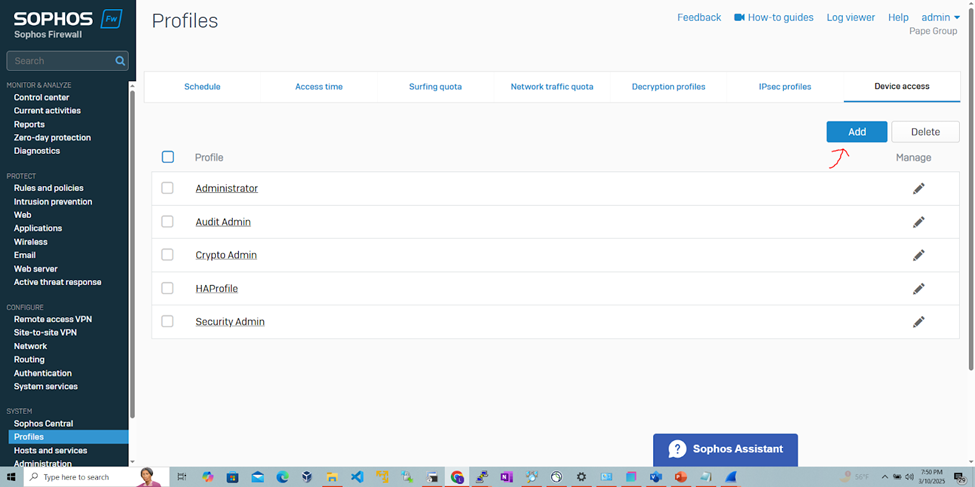
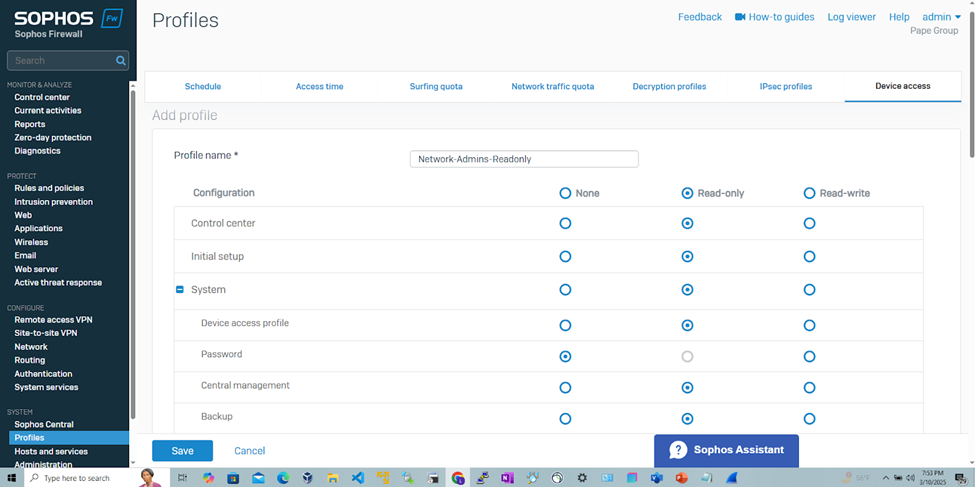
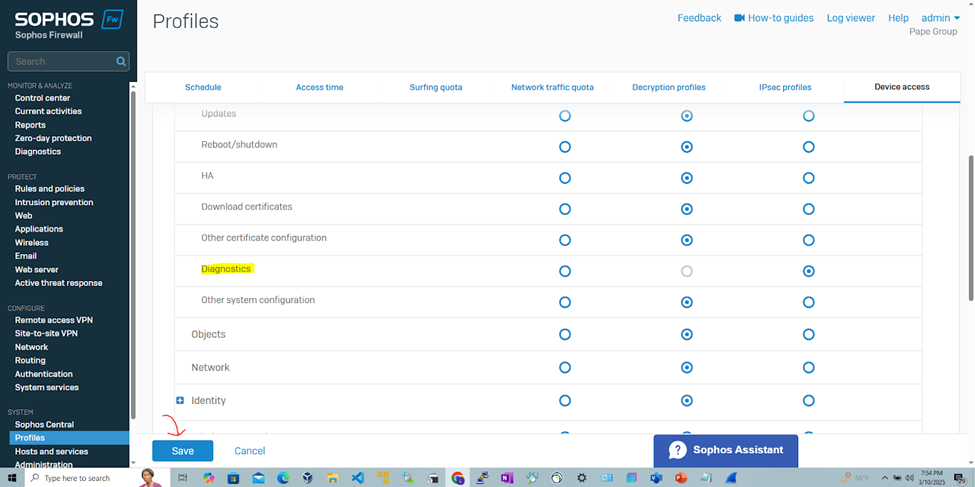
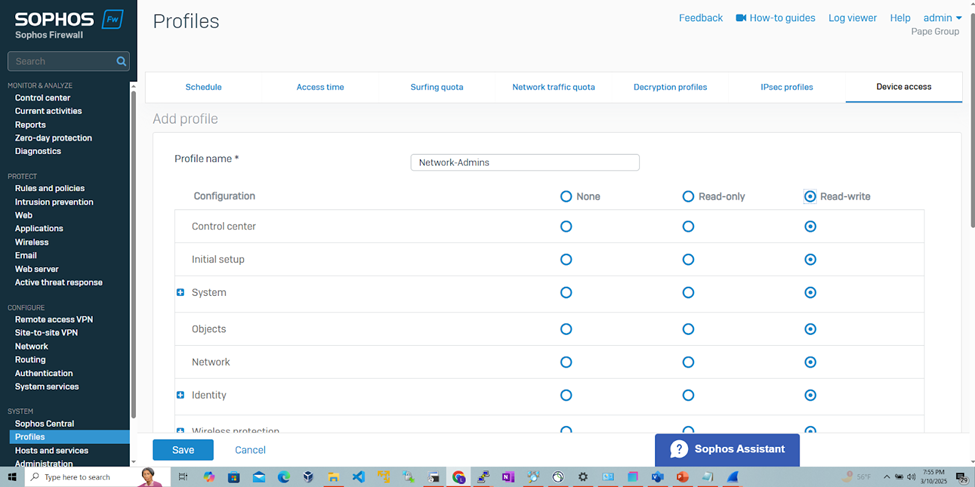
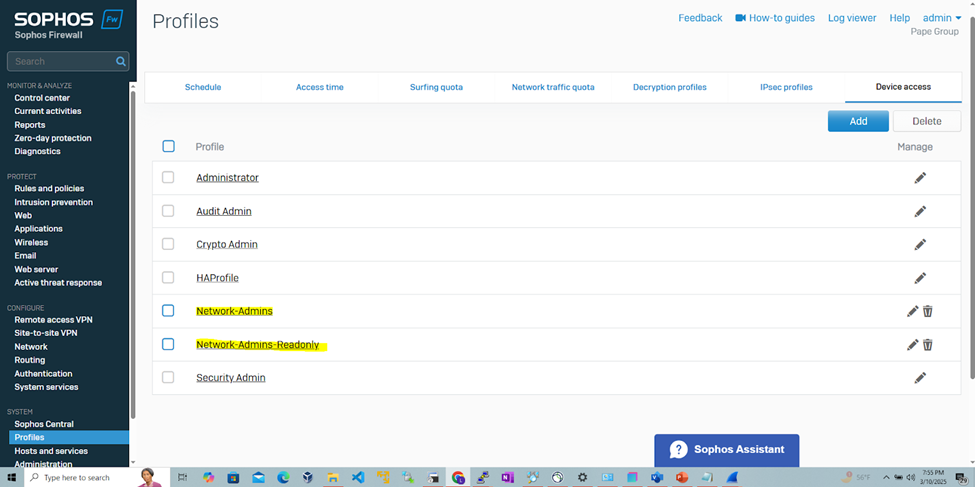
Add Sophos RADIUS Client
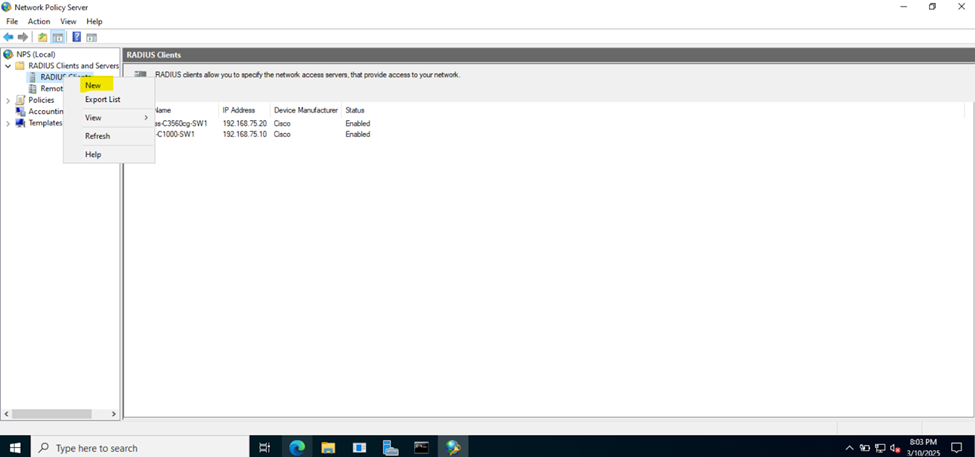
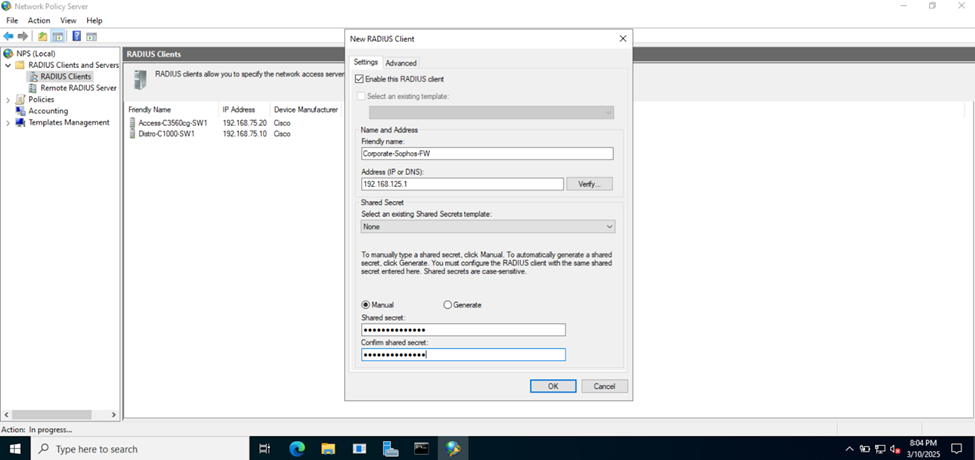
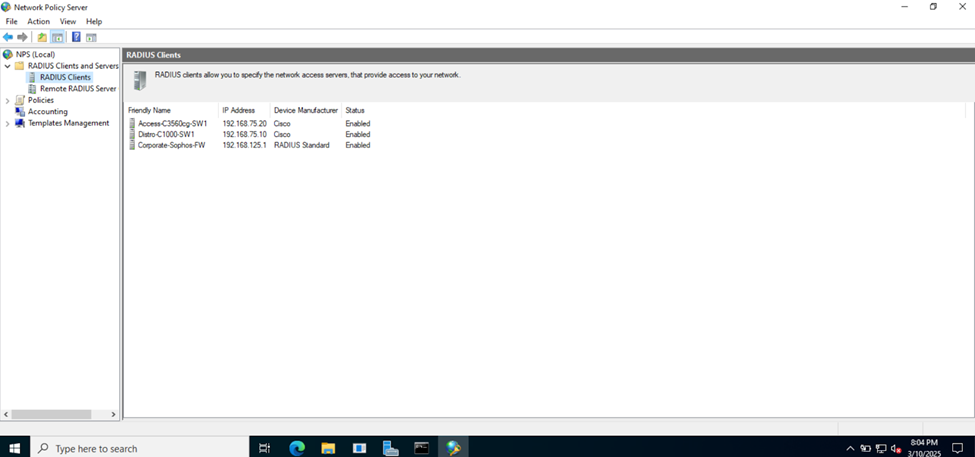
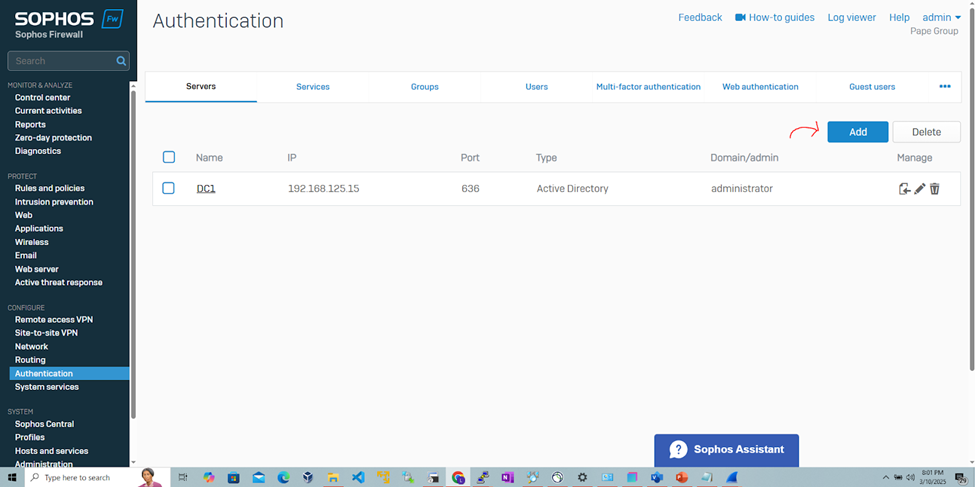
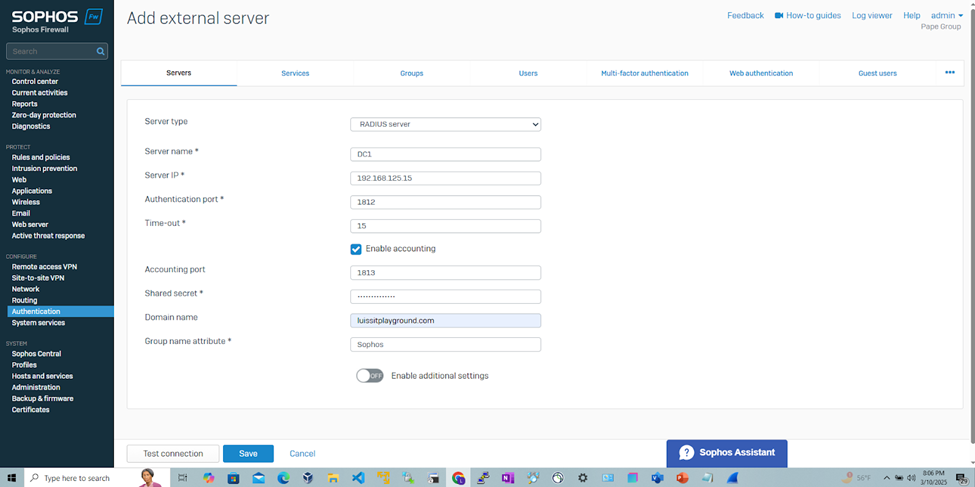
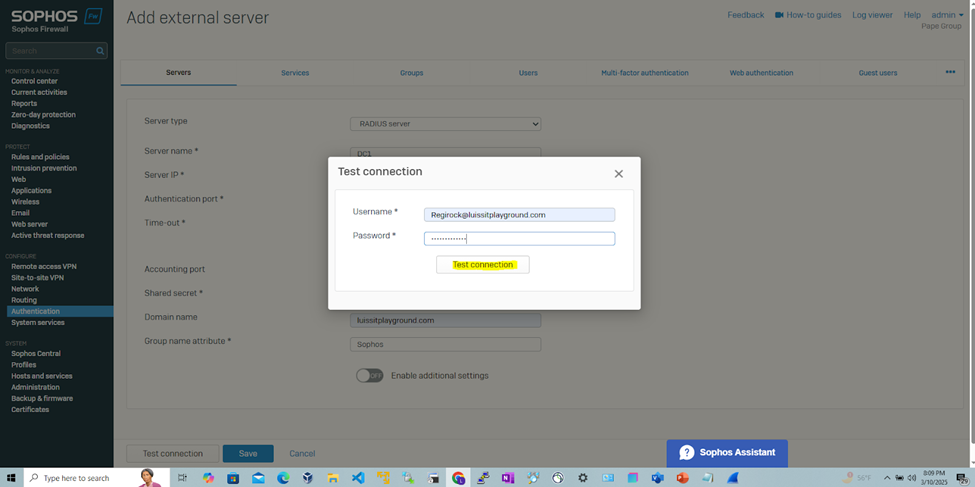
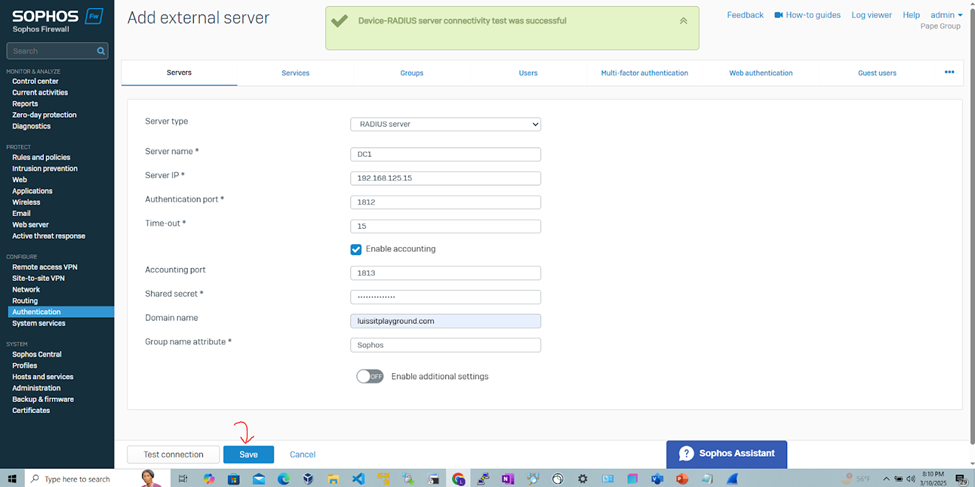
Add RADIUS Authentication Server
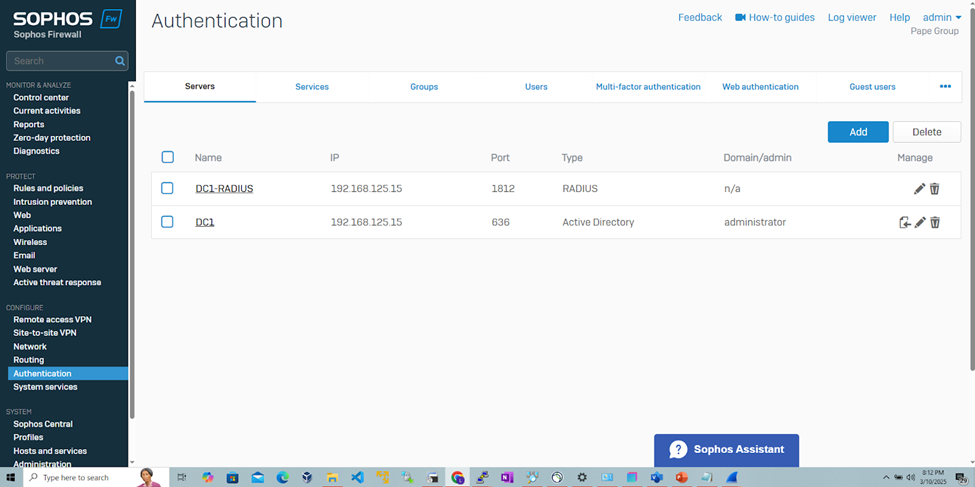
Set Sophos Primary Authentication Methods
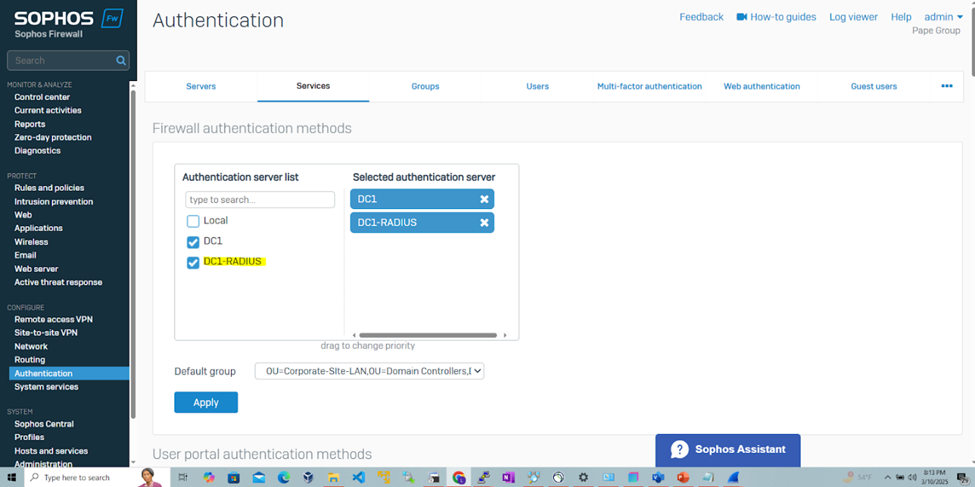
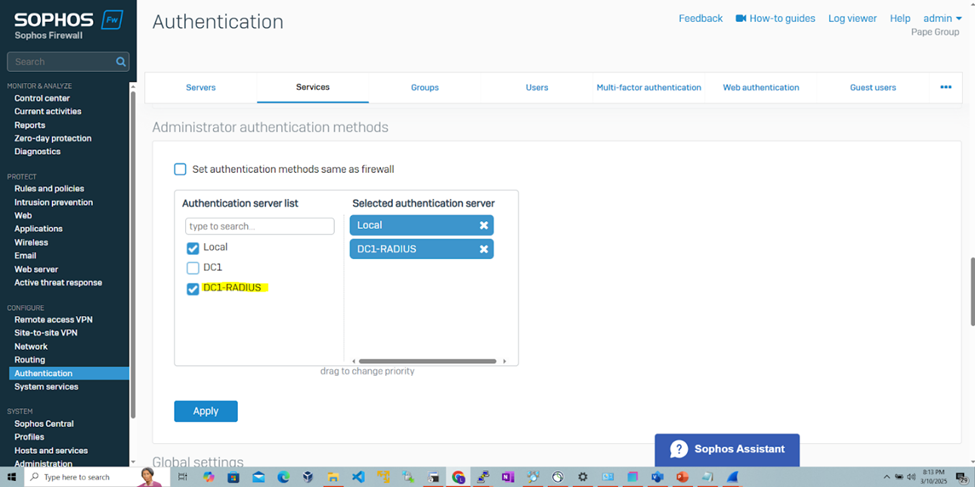
Import Active Directory Groups for RADIUS
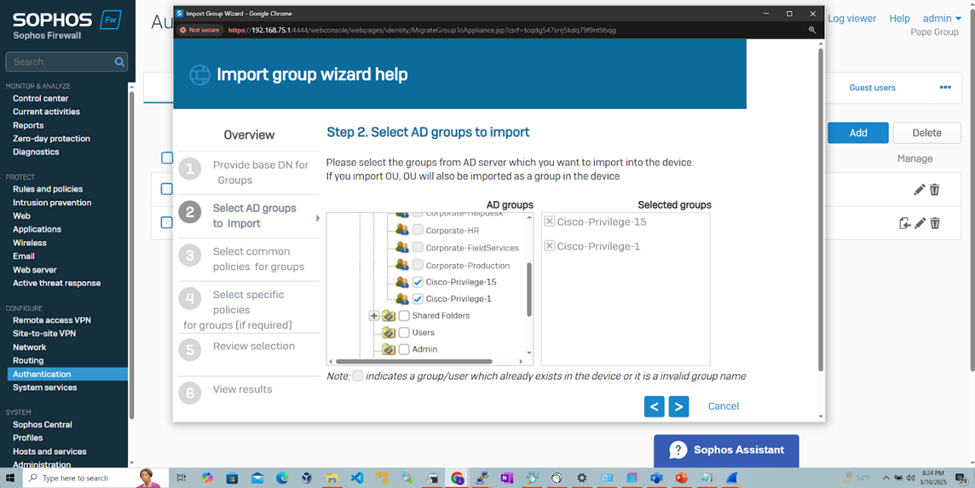
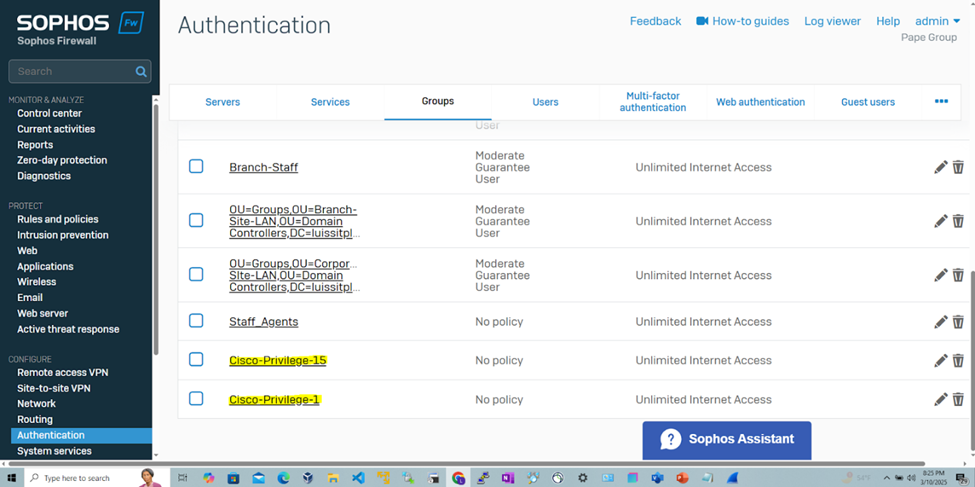
Captive Portal & Assigning Profiles for RADIUS
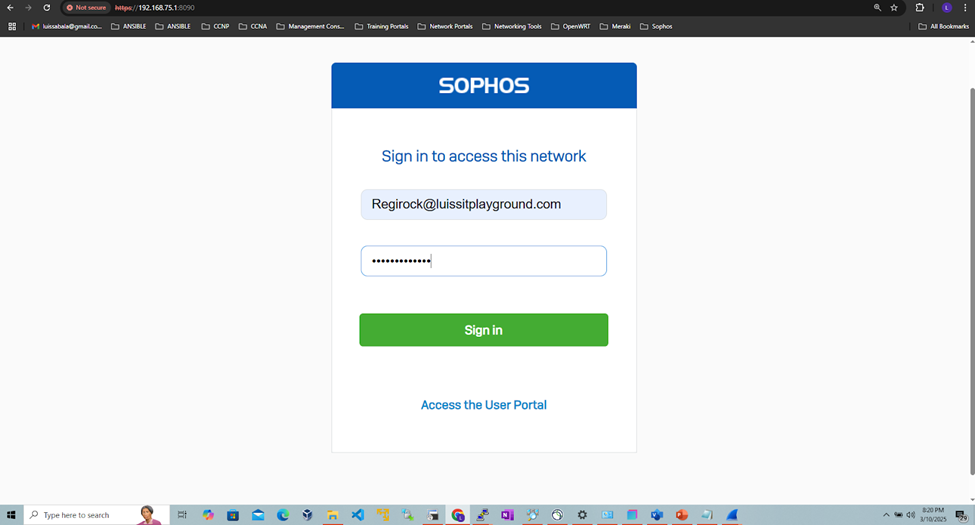
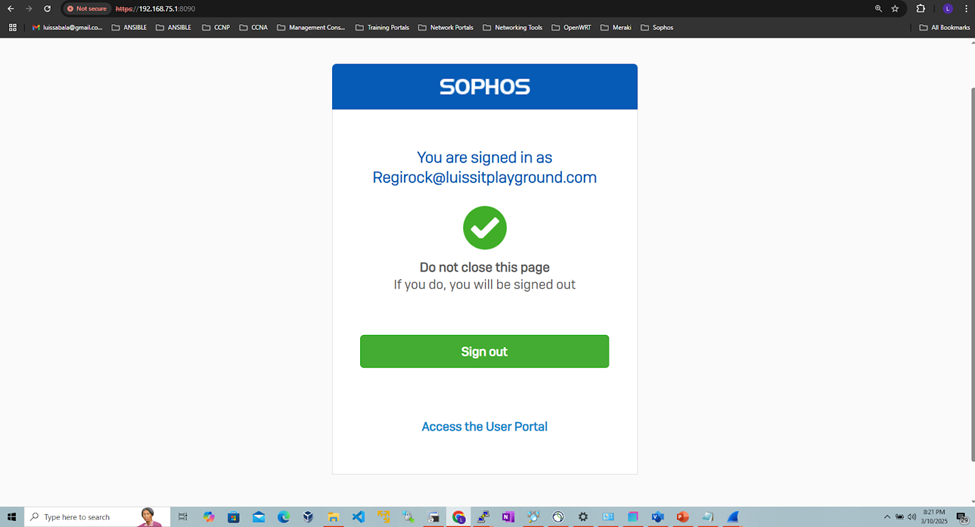
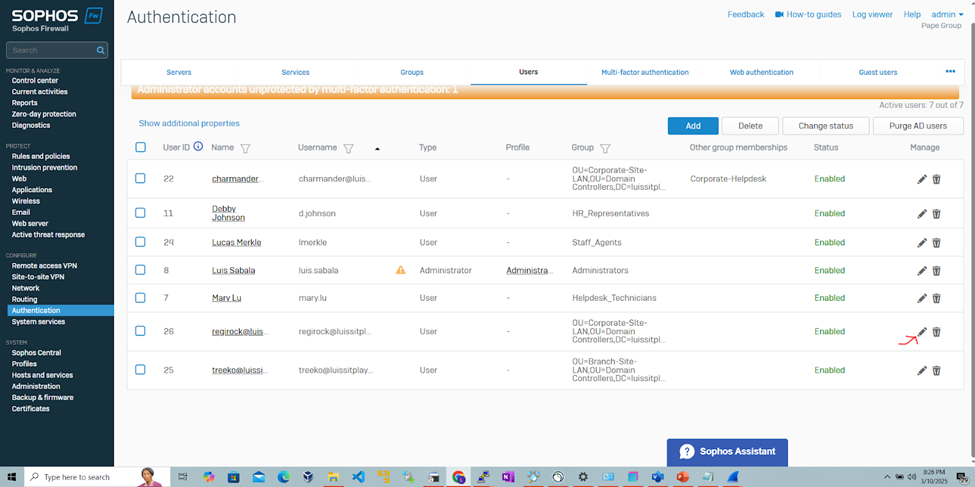
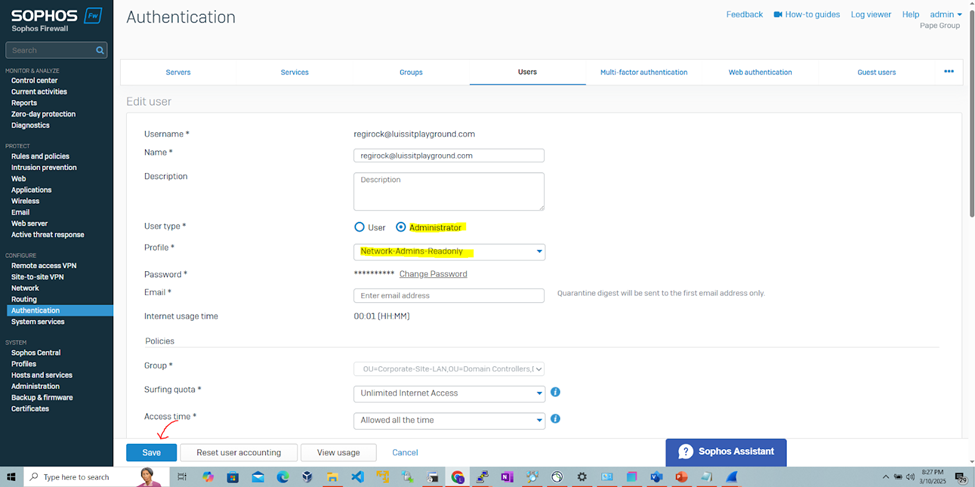
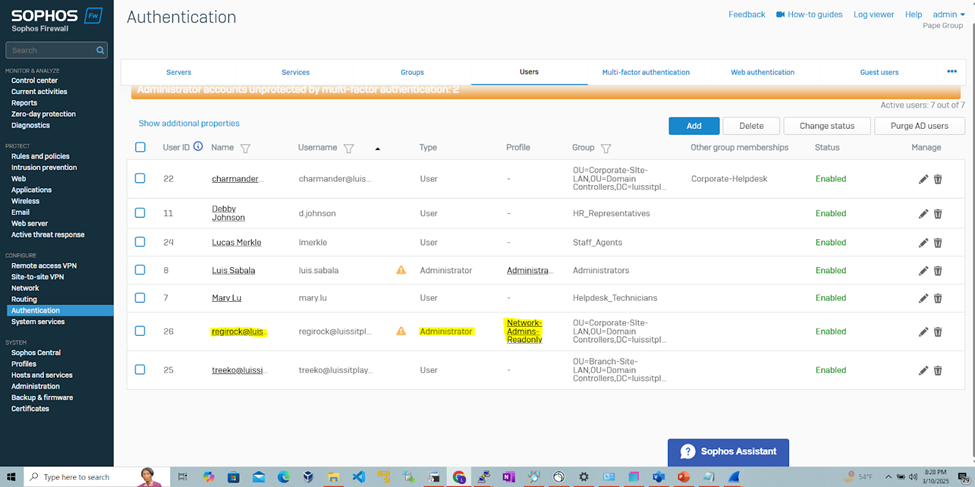
(Privilege 1- Read-Only) RADIUS Verification
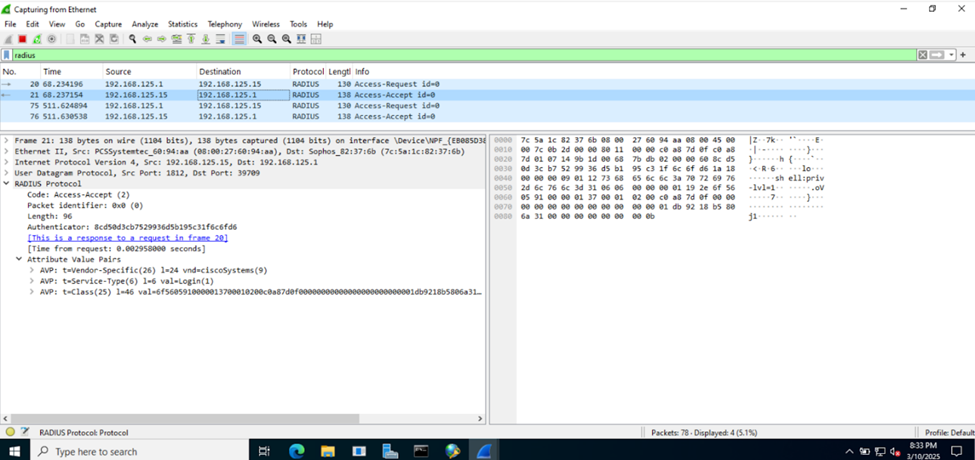
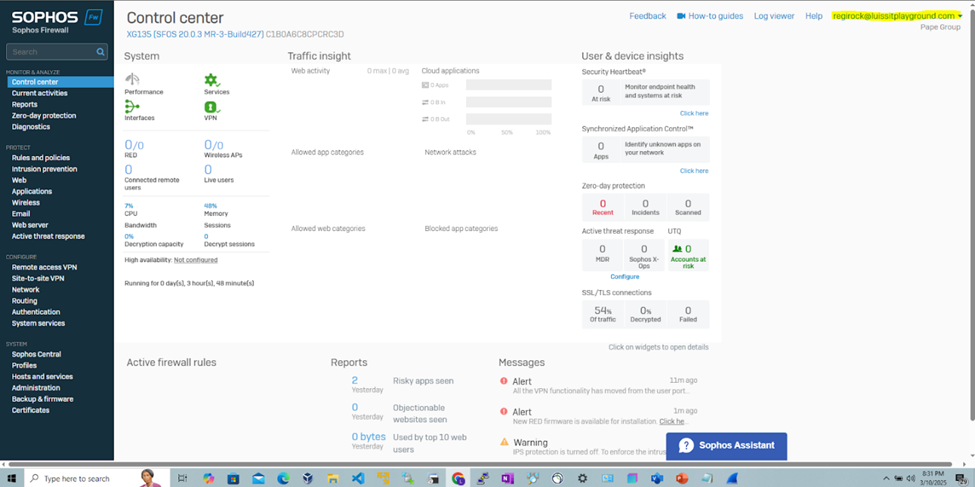
(Privilege 15 - Full-Control) RADIUS Verification
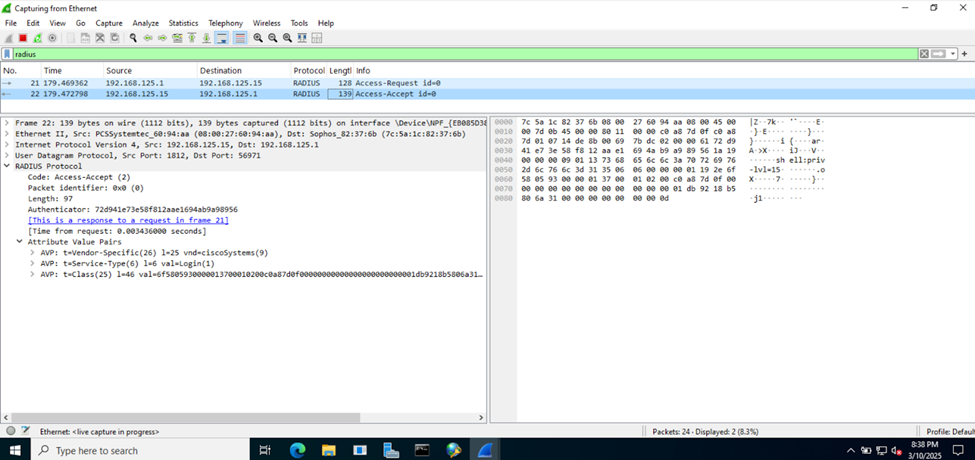

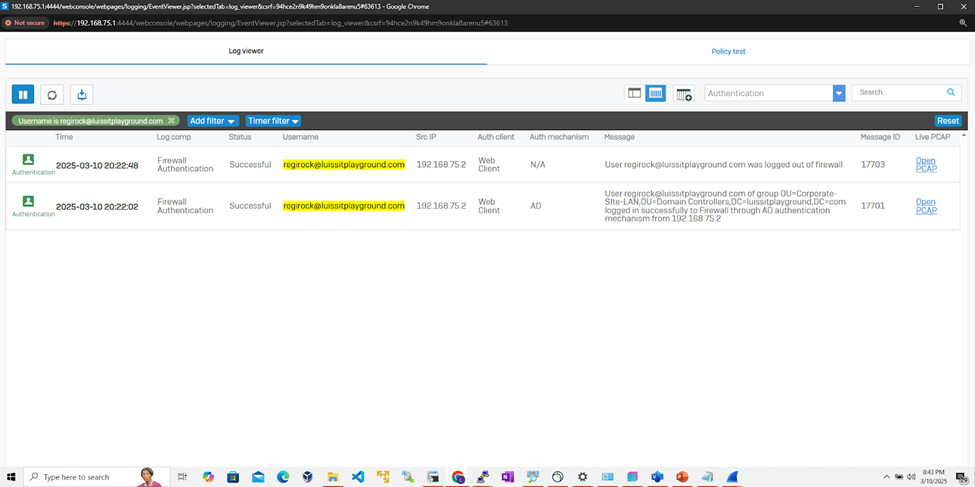
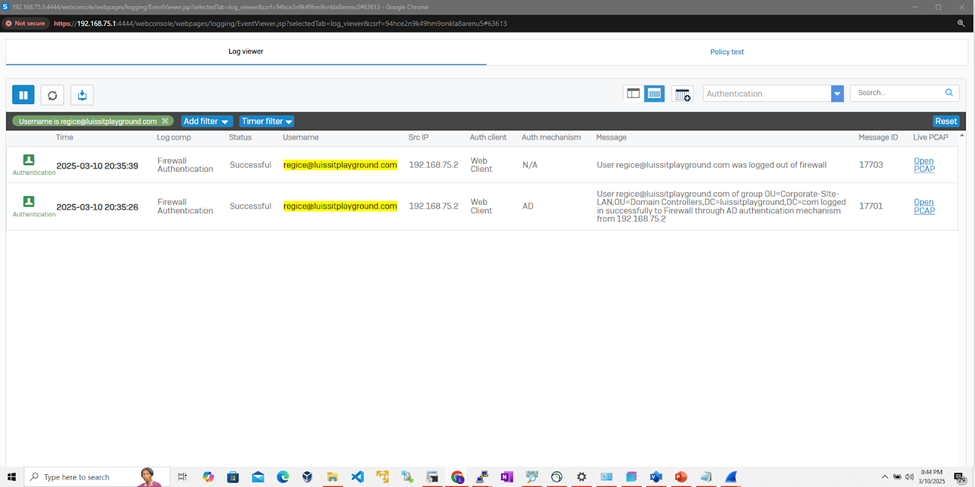
Sophos Firewall Authentication Logs